AppFlowMonitor
Dashboard > AppFlow Monitor
The AppFlow Monitor provides administrators with real-time, incoming and outgoing network data. Various views and customizable options in the AppFlow Monitor Interface assist in visualizing the traffic data by applications, users, URLs, initiators, responders, threats, VoIP, VPN, devices, or by contents.
This section contains the following subsections:
• Filter Options
• AppFlow Monitor Tabs
• AppFlow Monitor Toolbar
• Group Options
• AppFlow Monitor Status
• AppFlow Monitor Views
• Using Filtering Options
• Generating Application Visualization Report
Filter Options
The AppFlow Monitor Filter Options allows the administrator to filter out incoming, real-time data. Administrators can apply, create, and delete custom filters to customize the information they wish to view. The Filter Options apply across all the Application Flow tabs. Please refer to the Using Filtering Options.
|
Option
|
Widget
|
Description
|
|
Add to Filter
|
|
Adds current selection to filter.
At least 1 item must be selected in order to use the Filter Options. After doing so, all other tabs will update with information pertaining to the items in the filter.
|
|
Remove from Filter
|
|
Removes the current selection from the filter view by clicking on the X.
|
|
Load Filter
|
|
Loads existing filter settings.
|
|
Save
|
|
Saves the current filter settings.
|
|
Delete
|
|
Deletes the current filter settings.
|
|
AppFlow Monitor Tabs
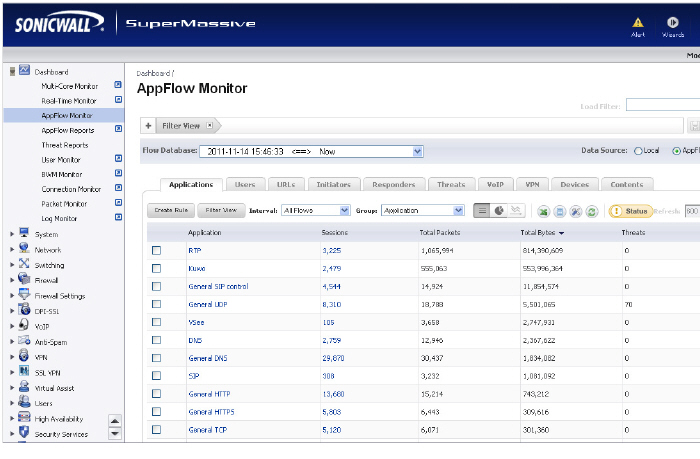
The AppFlow Monitor Tabs contains details about incoming and outgoing network traffic. Each tab provides a faceted view of the network flow. The data is organized by Applications, Users, URLs, Initiators, Responders, Threats, VoIP, VPN, Devices, and Content.
• The Applications tab displays a list of Applications currently accessing the network.
• The Users tab displays a list of Users currently connected to the network.
• The URLs tab displays a list of URLs currently accessed by Users.
• The Initiators tab displays details about current connection initiators.
• The Responders tab displays details about current connection responders.
• The Threats tab displays a list of threats encountered by the network.
• The VoIP tab displays current VoIP and media traffic.
• The VPN tab displays a list of VPN sessions connected to the network.
• The Devices tab displays a list of devices currently connected to the network.
• The Contents tab displays information about the type of traffic flowing through the network.
AppFlow Monitor Toolbar
The AppFlow Toolbar allows for customization of the AppFlow Monitor interface. The ability to create rules and add items to filters allows for more application and user control. Different views, pause and play abilities, customizable data intervals and refresh rates are also available to aid in visualizing incoming, real-time data.
|
Option
|
Widget
|
Description
|
|
Create Rule
|
|
Starts the App Control Wizard. For more information on using this wizard, refer to the Application Control.
|
|
Filter View
|
|
Adds selected items to the filter.
|
|
Interval
|
|
The span of time in which data is collected.
|
|
Group
|
|
Categorizes selections according to the available grouping options which vary depending on the tab that is selected.
Please refer to the Group Options.
|
|
List View
|
|
Provides a detailed list view of the data flow.
|
|
Pie Chart View
|
|
Provides a pie chart view of the data flow.
|
|
Flow Chart View
|
|
Provides a flow chart view of the data flow.
|
|
Export
|
|
Exports the data flow in comma separated variable (.csv) format.
|
|
Print PDF Report
|
|
Generate an Application Visualization Report. For more information, refer to the Generating Application Visualization Report.
|
|
Configuration
|
|
Allows for customization of the display by enabling or disabling columns for Applications, Sessions, Packets, Bytes, Rate, and Threats. Also allows the administrator to enable or disable commas in numeric fields.
|
|
Refresh Button
|
|
Refreshes the real-time data.
|
|
Status Update
|
|
Provides status updates about App signatures, GAV Database, Spyware Database, IPS Database, Country Database, Max Flows in Database, and CFS Status. Please refer to the AppFlow Monitor Status for more information.
A green status icon signifies that all appropriate signatures and databases are active.
A yellow status icon signifies that some or all signature databases are still being downloaded or could not be activated.
|
|
Refresh Rate
|
|
Rate at which data is refreshed.
A numeric integer between 10 and 999 must be specified.
If 300 is entered in the numeric field, that means the data flow will refresh every 300 seconds.
|
|
Pause/Play
|
|
Freezes and unfreezes the data flow. Doing so gives the administrator flexibility when analyzing real-time data.
|
|
Group Options
The Group option sorts data based on the specified group. Each tab contains different grouping options.
• The Applications tab can be grouped by:
– Application: Displays all traffic generated by individual applications.
– Category: Groups all traffic generated by an application category.
• The Users tab can be grouped by:
– User Name: Groups all traffic generated by a specific user.
– IP Address: Groups all traffic generated by a specific IP address.
– Domain Name: Groups all traffic generated by a specific domain name.
– Auth Type: Groups all traffic generated by a specific authorizing method.
• The URL tab can be grouped according to:
– URL: Displays all traffic generated by each URL.
– Domain Name: Groups all traffic generated by a domain name.
– Rating: Groups all traffic generated based on CFS rating.
• The Initiators tab can be grouped according to:
– IP Address: Groups all traffic generated by a specific IP address.
– Interface: Groups all traffic according to the firewall interface.
– Country: Groups all traffic generated by each country, based on country IP database.
– Domain Name: Groups all traffic generated by a domain name.
• The Responders tab can be grouped according to:
– IP Address: Groups all traffic by IP address.
– Interface: Groups responders by interface.
– Country: Groups responders by each country, based on country IP database.
– Domain Name: Groups responders by domain name.
• The Threats tab can be grouped according to:
– Intrusions: Displays flows in which intrusions have been identified.
– Viruses: Displays flows in which viruses have been identified.
– Spyware: Displays flows in which spyware has been identified.
– Spam: Shows all flows that fall under the category of spam.
• The VoIP tab can be grouped according to:
– Media Type: Groups VoIP flows according to media type.
– Caller ID: Groups VoIP flows according to caller ID.
• The VPN tab can be grouped according to:
– Remote IP Address: Groups VPN flows access according to the remote IP address.
– Local IP Address: Groups VPN flows access according to the local IP address.
– Name: Groups VPN flows access according to the tunnel name.
• The Devices tab can be grouped according to:
– IP Address: Groups flows by IP addresses inside the network.
– Interface: Groups flows by interfaces on the firewall.
– Name: Groups flows by device name, or MAC address.
• The Contents tab can be grouped according to:
– Email Address: Groups contents by email address.
– File Name: Groups flows by file type detected.
AppFlow Monitor Status
The AppFlow Monitor Status dialog appears when the cursor rolls over the Status button in the toolbar. The AppFlow Monitor Status provides signature updates about App Rules, App Control Advanced, GAV, IPS, Anti-Spyware, CFS, Anti-Spam, BWM, and country databases.
The option to enable or disable the flow collection is available in the Status dialog. If the Status dialog is no longer wanted, click close in the upper-right corner.
AppFlow Monitor Views
Three views are available for the AppFlow Monitor: Detailed List View, Pie Chart and Flow Chart Graph View. Each view provides the administrator a unique display of incoming, real-time data.
This section includes the following subsections:
• List View
• Graph View
List View
In the List View, each AppFlow tab is comprised of columns displaying real-time data. These columns are organized into sortable categories.
• Check Box: Allows the administrator to select the line item for creation of filters.
• Main Column: The title of the Main Column is dependent on the selected tab. For example, if the Users Tab is the selected, then the Main Column header will read “Users”. In that column, the name of the Users connected to the network are shown. Clicking on the items in this column will bring up a popup with relevant information on the item displayed.
• Sessions: Clicking on this number will bring up a table of all active sessions.
• Packets: Displays the number of data packets transferred.
• Bytes: Displays the number of bytes transferred.
• Rate (KBps): Displays the rate at which data is transferred.
• Threats: Displays the number of threats encountered by the network.
• Total: Displays the total Sessions, Packets, and Bytes sent during the duration of the current interval.
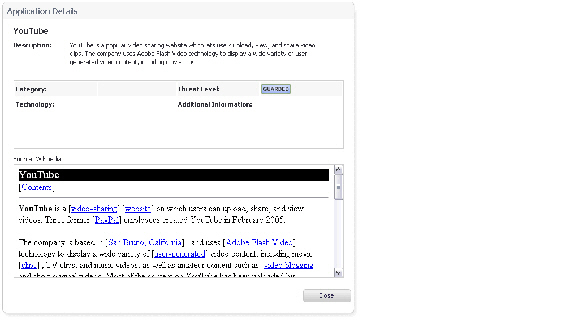
Application Details
Each item listed in the Main Column provides a link to an Application Detail dialog. A display appears when the item links are clicked. The dialog provides:
• Description of the item
• Information pertaining to the category, threat level, type of technology the item falls under, and other additional information
• Application details are particularly useful when an Administrator does not recognize the name of an Application.
Graph View
The Graph View displays the top applications and the percentage of bandwidth used. The percentage of bandwidth used is determined by taking the total amount of bandwidth used by the top applications, and dividing that total by the amount of top applications.
Using Filtering Options
Using filtering options allow administrators to reduce the amount of data seen in the AppFlow Monitor. By doing so, administrators can focus on points of interest without distraction from other applications. To use the Filtering Options, perform the following steps:
Step 1 Navigate to Dashboard > AppFlow Monitor > Applications. Select the check boxes of the applications you wish to add to the filter. In this case, Ventrilo is selected.
Step 2 Click Filter View to add Ventrilo to the filter.
Step 3 Once the application is added to the filter, only Ventrilo is visible in the Applications tab.
More information about Users, peer connectivity, and packets sent are visible in the AppFlow Monitor tabs. The Users using Ventrilo are visible in the Users tab. The IP Addresses of these users are visible in the Initiators tab. The IP Addresses of the connected peers who are sharing packets are visible in the Responders Tab.
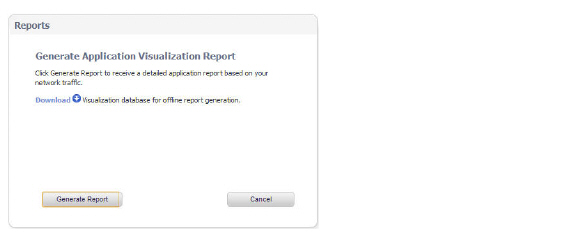
Generating Application Visualization Report
The SonicWALL Application Intelligence and Control feature allows administrators to maintain granular control of applications and users by creating bandwidth management policies based on local pre-defined categories, individual applications, or even users and groups. With the Application Visualization feature, administrators are able to view real-time graphs of applications, ingress and egress bandwidth, Websites visited, and all user activity. Administrators are able to adjust network policies based on these critical observations. The SonicWALL Application Usage and Risk Report combines the results of these two features in a downloadable report listing the following categories:
• High Risk Applications in Use
• Top URL Categories in Use
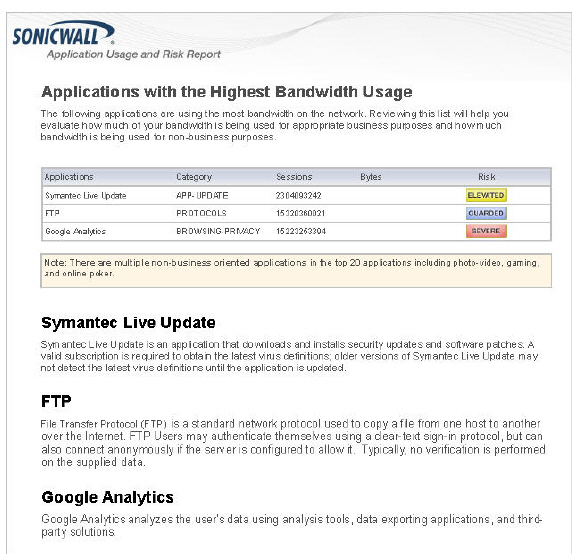
• Applications with the Highest Bandwidth Usage
• Application Usage by Category and Technology
• Top Findings of Network Characteristics
• Recommendations based on the Top Findings
Navigate to the Dashboard > App Flow Monitor page and click the download PDF report button from the AppFlow toolbar. Next, click the Generate Report button to get a dynamically generated report specific to your SonicWALL SuperMassive appliance. Note the report may take a few minutes to generate and download.
Once the report is generated, an executive summary is provided at the top of the report for a holistic overview of your network. The report contains a real-time snapshot of network traffic to guide you in implementing new bandwidth management policies. An example SonicWALL Application Usage and Risk Analysis report is provided below listing applications with the highest bandwidth usage, their application category, number of sessions, application risk level, and a detailed description of the application.