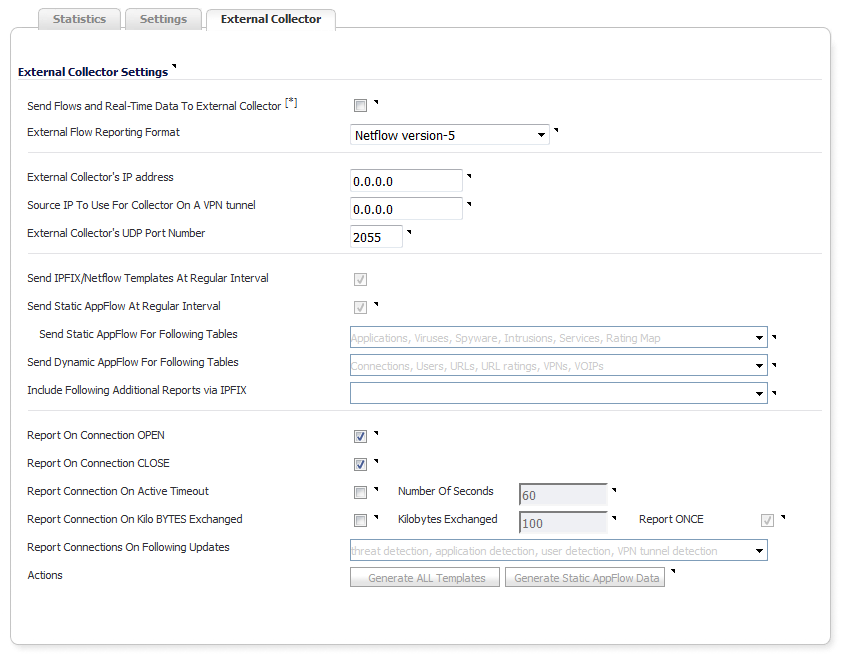
The External Collector tab provides configuration settings for AppFlow reporting to an external IPFIX collector.
|
•
|
Send Flows and Real-Time Data To External Collector—Enables the specified flows (AppFlows) data and real-time data to be reported to an external flow collector. If you enable this setting, you must select a reporting format from the External Flow Reporting Format drop-down menu.
|
|
•
|
External AppFlow Reporting Format—If the Send Flows and Real-time Data to External Collector option is selected, you must specify the flow reporting type:
|
|
•
|
NetFlow version-5 (default)
|
|
•
|
If the reporting type is set to:
|
•
|
Netflow versions 5 or 9 or IPFIX, then any third-party collector can be used to show flows reported from the device, which uses standard data types as defined in IETF. Netflow versions and IPFIX reporting types contain only connection-related flow details per the standard.
|
|
•
|
IPFIX with extensions, then only collectors that are SonicWall flow aware can be used. IPFIX with extensions reports SonicWall dynamic tables for:
|
|
NOTE: When using IPFIX with extensions, select a third-party collector that is SonicWall flow aware, such as SonicWall Scrutinizer.
|
|
•
|
External Collector’s IP Address—Specify the external collector IP address to which the device will send flows via Netflow/IPFIX. This IP address must be reachable from the SonicWall firewall for the collector to generate flow reports. If the collector is reachable via a VPN tunnel, then the source IP must be specified.
|
|
•
|
Source IP to Use for Collector on a VPN Tunnel—If the collector IP address specified in the External Collector’s IP Address setting is reachable via a VPN tunnel, then the source IP must be specified in this setting to match the correct VPN policy.
|
|
•
|
External Collector’s UDP Port Number—Specify the UDP port number on which the collector is listening for Netflow/IPFIX packets. The default port is 2055.
|
|
•
|
Send IPFIX/Netflow Templates at Regular Intervals—Enables the appliance to send Template flows at regular intervals. This option is selected by default.
|
|
•
|
Send Static AppFlow At Regular Interval—Selecting this check box enables the sending of the static AppFlows specified in the Send Static AppFlow For Following Tables drop-down menu. This setting generates IPFIX records for all static tables every hour.
|
|
This option must be selected if SonicWall Scrutinizer is used as a collector. |
|
•
|
Send Static AppFlow For Following Tables—Select the static mapping tables to be generated to a flow from the drop-down menu:
|
|
•
|
Applications (selected by default)
|
|
•
|
Viruses (selected by default)
|
|
•
|
Spyware (selected by default)
|
|
•
|
Intrusions (selected by default)
|
|
•
|
Services (selected by default)
|
|
•
|
Rating Map (selected by default)
|
For more information on static tables, refer to NetFlow Tables.
When running in IPFIX with extensions mode, SonicWall reports multiple types of data to an external device to correlate User, VPN, Application, Virus, and Spyware information. In this mode, data is both static and dynamic. Static tables are needed only once as they rarely change. Depending on the capability of the external collector, not all static tables are needed. You can select the tables needed in this drop-down menu.
|
•
|
Send Dynamic AppFlow For Following Tables—Select the dynamic mapping tables to be generated to a flow from the drop-down menu:
|
|
•
|
Connections (selected by default)
|
|
•
|
Users (selected by default)
|
|
•
|
URLs (selected by default)
|
|
•
|
URL ratings (selected by default)
|
|
•
|
VPNs (selected by default)
|
|
•
|
|
•
|
|
•
|
VoIPs (selected by default)
|
For more information on dynamic tables, refer to the NetFlow Tables.
|
In IPFIX with extensions mode, the firewall generates reports for the selected tables. As the firewall doesn’t cache this information, some of the flows not sent may create failure when correlating flows with other related data. |
|
•
|
Include Following Additional Reports via IPFIX—Select additional IPFIX reports to be generated to a flow from the drop-down menu:
|
|
•
|
Top 10 Apps – Generates the top 10 applications.
|
|
•
|
Interface Stats – Generates per-interface statistics such as interface name, interface bandwidth utilization, MAC address, link status.
|
|
•
|
Core utilization –Generates per-core utilization.
|
|
•
|
Memory utilization – Generates statuses of available memory, used memory, and memory used by the AppFlow collector.
|
By default, none are selected. Statistics are reported every 5 seconds.
When running in IPFIX with extensions mode, SonicWall can report more data that is not related to connection and flows. These tables are grouped under this section (Additional Reports). Depending on the capability of the external collector, not all additional tables are needed. In this drop-down menu, you can select tables that are needed.
|
•
|
Report On Connection OPEN—Reports flows when the connection is open. This is typically when a connection is established. All associated data related to that connection may not be available when the connection is opened. This option, however, enables flows to show up on the external collector as soon as the new connection is opened. By default, this setting is enabled.
|
|
•
|
Report On Connection CLOSED—Reports flows when the connection is closed. This is the most efficient way of reporting flows to an external collector. All associated data related to that connection are available and reported. By default, this setting is enabled.
|
|
•
|
Report Connection On Active Timeout—Reports connections based on Active Timeout sessions. If enabled, the firewall reports an active connection every active timeout period. By default, this setting is disabled.
|
|
•
|
Number of Seconds—Set the number of seconds to elapse for the Active Timeout. The range is 1 second to 999 seconds for the Active Timeout. The default setting is 60 seconds.
|
|
•
|
Report Connection On Kilo BYTES Exchanged—Reports flows based on when a specific amount of traffic, in kilobytes, is exchanged. If this setting is enabled, the firewall reports an active connection whenever the specified number of bytes of bidirectional data is exchanged on an active connection. This option is ideal for flows that are active for a long time and need to be monitored. This option is not selected by default.
|
|
•
|
Kilobytes Exchanged—Specify the amount of data, in kilobytes, transferred on a connection before reporting. The default value is 100 kilobytes.
|
|
•
|
Report ONCE—When the Report Connection On Kilo BYTES Exchanged option is enabled, the same flow is reported multiple times whenever the specified amount of data is transferred over the connection. This could cause a large amount of IPFIX packet generation on a loaded system. Enabling this option sends the report only once. By default, the setting is enabled.
|
|
•
|
Report Connections On Following Updates—Select from the drop-down menu to enable connection reporting for the following (by default, all are selected):
|
|
•
|
threat detection—Reports flows specific to threats. Upon detections of virus, intrusion, or spyware, the flow is reported again.
|
|
•
|
application detection—Reports flows specific to applications. Upon performing a deep packet inspection, the SonicWall appliance is able to detect if a flow is part of a certain application. When identified, the flow is reported again.
|
|
•
|
user detection—Reports flows specific to users. The SonicWall appliance associates flows to a user-based detection based on its login credentials. When identified, the flow is reported again.
|
|
•
|
VPN tunnel detection—Reports flows sent through the VPN tunnel. When flows sent over the VPN tunnel are identified, the flow is reported again.
|
|
•
|
Actions—Generate asynchronously templates and static flow data.
|
|
•
|
Generate ALL Templates — Click on the button to begin building templates on the IPFIX server; this will take up to two minutes to generate.
|
|
•
|
Generate Static AppFlow Data — Click on the button to begin generating a large amount of flows to the IPFIX server; this will take up to two minutes to generate.
|