|
1
|
|
2
|
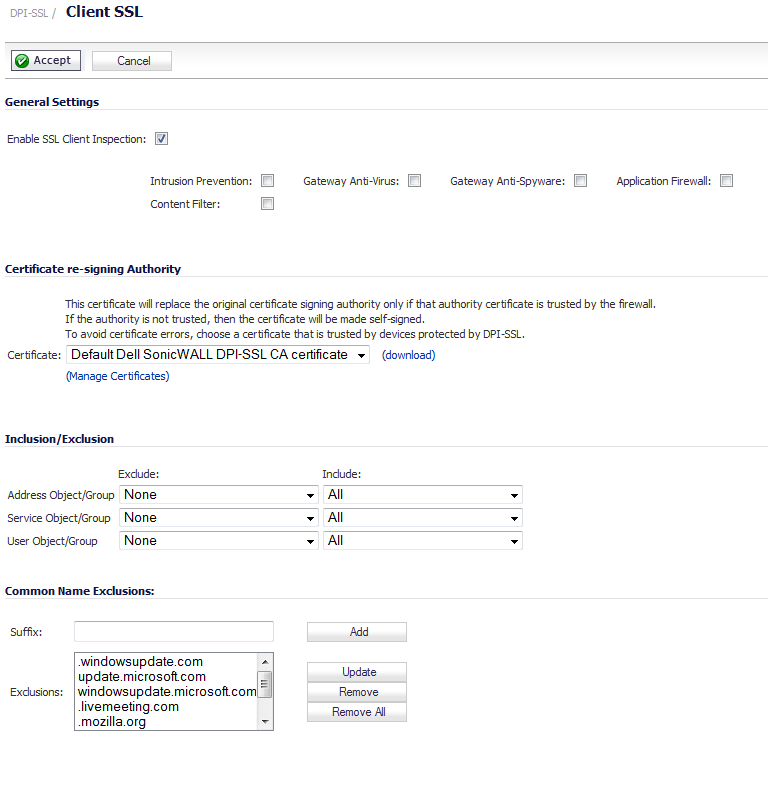
Select the Enable SSL Client Inspection checkbox. By default, this checkbox is not enabled.
|
|
4
|
Click Accept.
|
|
1
|
Navigate to the DPI-SSL > Client SSL page.
|
|
2
|
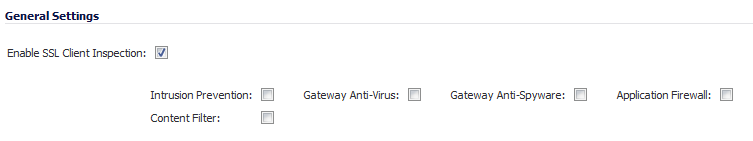
In the Certificate re-signing Authority section, select the certificate to use from the Certificate drop-down menu. By default, DPI-SSL uses the Default SonicWALL DPI-SSL CA certificate to re-sign traffic that has been inspected.
|
|
NOTE: If the certificate you want is not listed, you can import it from the System > Certificates page. See Importing Certificates . For PKCS-12-formatted certificates, see Creating PKCS-12 Formatted Certificate File .
|
|
3
|
To download the selected certificate to the firewall, click the (download) link. The Opening filename dialog appears.
|
|
a
|
Ensure the Save File checkbox is selected.
|
|
b
|
Click OK.
|
|
4
|
Click Accept.
|
|
•
|
Exclusion/Inclusion lists exclude/include specified objects and groups
|
|
•
|
Common Name Exclusions excludes specified host names
|
|
1
|
|
2
|
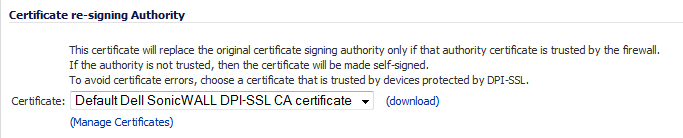
From the Address Object/Group Exclude and Include drop-down menus, select an address object or group to exclude or include from DPI-SSL inspection. By default, Exclude is set to None and Include is set to All.
|
|
TIP: The Include drop-down menu can be used to fine tune the specified exclusion list. For example, by selecting the Remote-office-California address object in the Exclude drop-down menu and the Remote-office-Oakland address object in the Include drop-down menu.
|
|
3
|
From the Service Object/Group Exclude and Include drop-down menus, select an address object or group to exclude or include from DPI-SSL inspection. By default, Exclude is set to None and Include is set to All.
|
|
4
|
From the User Object/Group Exclude and Include drop-down menus, select an address object or group to exclude or include from DPI-SSL inspection. By default, Exclude is set to None and Include is set to All.
|
|
5
|
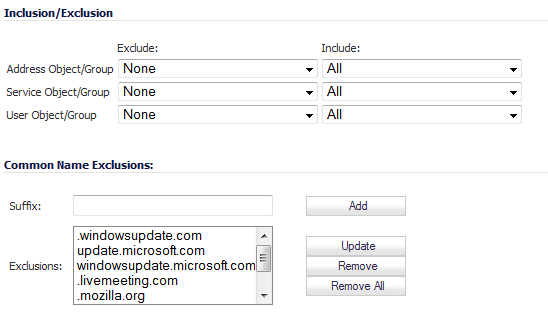
Use the Common Name Exclusions section to add domain names to the exclusion list
|
|
a
|
Enter a host name in the Suffix field.
|
|
b
|
Click the Add button.
|
|
6
|
Click Accept at the top of the page to confirm the configuration.
|
|
1
|
|
2
|
Select the Enable SSL Inspection checkbox.
|
|
3
|
|
4
|
Click Apply.
|
|
5
|
|
6
|
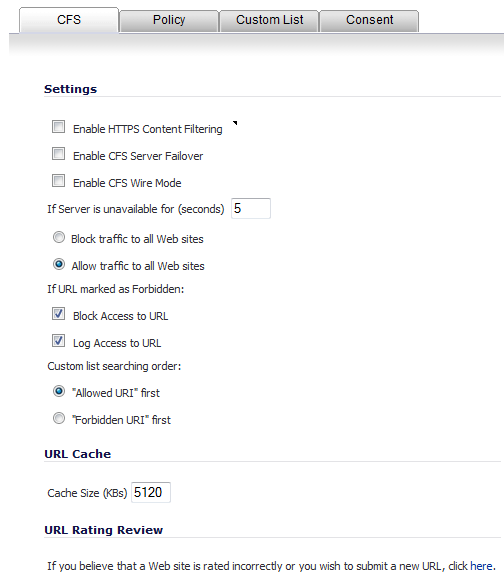
Ensure Content Filter Service is selected from the drop-down menu.
|
|
7
|
|
8
|
|
9
|
|
10
|
Click OK.
|
|
11
|
Click Accept.
|
|
1
|
|
2
|
Select the Enable SSL Client Inspection checkbox.
|
|
3
|
Select the Application Firewall checkbox.
|
|
4
|
Click Apply.
|
|
5
|
|
6
|
|
7
|
Configure an HTTP Client policy to block Microsoft Internet Explorer browser with block page as an action for the policy. For how to configure an App Rule, see Configuring an App Rules Policy .
|
|
8
|
Click Apply.
|