|
•
|
Host – An individual IP address, netmask and zone association.
|
|
•
|
MAC (original) – Media Access Control, or the unique hardware address of an Ethernet host. MAC AOs are used for:
|
|
•
|
Range – A starting and ending IP address, inclusive of all addresses in between.
|
|
•
|
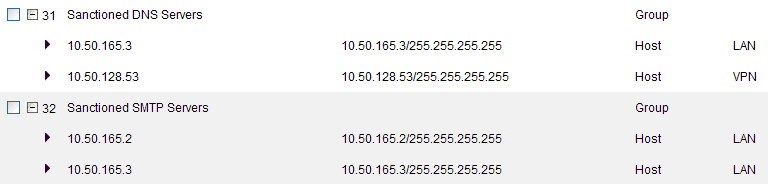
Group – A collection of Address Objects of any assortment of types. Groups may contain other Groups, Host, MAC, Range, or FQDN Address Objects.
|
|
•
|
MAC – SonicOS resolves MAC AOs to an IP address by referring to the ARP cache on the firewall.
|
|
•
|
FQDN – Fully Qualified Domain Names, such as ‘www.reallybadWebsite.com’, will be resolved to their IP address (or IP addresses) using the DNS server configured on the firewall. Wildcard entries are supported through the gleaning of responses to queries sent to the sanctioned DNS servers.
|
|
•
|
Zone Association – When defined, Host, MAC, and FQDN AOs require an explicit zone designation. In most areas of the interface (such as Access Rules) this is only used referentially. The functional application are the contextually accurate populations of Address Object drop-down lists, and the area of “VPN Access” definitions assigned to Users and Groups; when AOs are used to define VPN Access, the Access Rule auto-creation process refers to the AO’s zone to determine the correct intersection of VPN [zone] for rule placement. In other words, if the “192.168.168.200 Host” Host AO, belonging to the LAN zone was added to “VPN Access” for the “Trusted Users” User Group, the auto-created Access Rule would be assigned to the VPN LAN zone.
|
|
•
|
Management and Handling – The versatilely typed family of Address Objects can be easily used throughout the SonicOS interface, allowing for handles (e.g. from Access Rules) to be quickly defined and managed. The ability to simply add or remove members from Address Object Groups effectively enables modifications of referencing rules and policies without requiring direct manipulation.
|
|
•
|
Reusability – Objects only need to be defined once, and can then be easily referenced as many times as needed.
|
The term Dynamic Address Object (DAO) describes the underlying framework enabling MAC and FQDN AOs. By transforming AOs from static to dynamic structures Firewall > Access Rules can automatically respond to changes in the network.
|
For example, creating an FQDN AO for “*.myspace.com” will first use the DNS servers configured on the firewall to resolve “myspace.com” to 63.208.226.40, 63.208.226.41, 63.208.226.42, and 63.208.226.43 (as can be confirmed by nslookup myspace.com or equivalent). Since most DNS servers do not allow zone transfers, it is typically not possibly to automatically enumerate all the hosts in a domain. Instead, the firewall will look for DNS responses coming from sanctioned DNS servers as they traverse the firewall. So if a host behind the firewall queries an external DNS server which is also a configured/defined DNS server on the firewall, the firewall will parse the response to see if it matches the domain of any wildcard FQDN AOs.
NOTE: If the workstation, client-A, in the example above had resolved and cached vids.myspace.com before the creation of the *.myspace.com AO, vids.myspace.com would not be resolved by the firewall because the client would use its resolver’s cache rather than issuing a new DNS request. As a result, the firewall would not have the chance to learn about vids.myspace.com unless it was resolved by another host. On a Microsoft Windows workstation, the local resolver cache can be cleared using the command ipconfig /flushdns. This forces the client to resolve all FQDNs, thereby allowing the firewall to learn them as they are accessed.
|
|
|
FQDN Address Objects are resolved using the DNS servers configured on the firewall in the Network > DNS page. Since it is common for DNS entries to resolve to multiple IP addresses, the FQDN DAO resolution process will retrieve all of the addresses to which a host name resolves, up to 256 entries per AO. In addition to resolving the FQDN to its IPs, the resolution process will also associate the entry’s TTL (time to live) as configured by the DNS administrator. TTL will then be honored to ensure the FQDN information does not become stale.
|
|
|
FQDN Address Objects are resolved using the DNS servers configured on the firewall in the Network > DNS page. Since it is common for DNS entries to resolve to multiple IP addresses, the FQDN DAO resolution process will retrieve all of the addresses to which a host name resolves, up to 256 entries per AO. In addition to resolving the FQDN to its IPs, the resolution process will also associate the entry’s TTL (time to live) as configured by the DNS administrator. TTL will then be honored to ensure the FQDN information does not become stale.
|
MAC and FQDN DAOs provide extensive Access Rule construction flexibility. MAC and FQDN AOs are configured in the same fashion as static Address Objects, that is from the Network > Address Objects page. Once created, their status can be viewed by a mouse‑over of their appearance, and log events will record their addition and deletion.
|
•
|
|
•
|
The DSL home user is registering the hostname moosifer.dyndns.org with the DDNS provider DynDNS. For this session, the ISP assigned the DSL connection the address 71.35.249.153.
|
|
•
|
|
•
|
|
•
|
|
NOTE: Rather than specifying LAN Subnets as the source, a more specific source could be specified, as appropriate, so that only certain hosts are denied access to the targets.
|
It is common for dynamically configured (DHCP) network environments to work in combination with internal DNS servers for the purposes of dynamically registering internal hosts – a common example of this is Microsoft’s DHCP and DNS services. Hosts on such networks can easily be configured to dynamically update DNS records on an appropriately configured DNS server (for example, see the Microsoft Knowledgebase article How to configure DNS dynamic updates in Windows Server 2003 at http://support.microsoft.com/kb/816592/en-us).
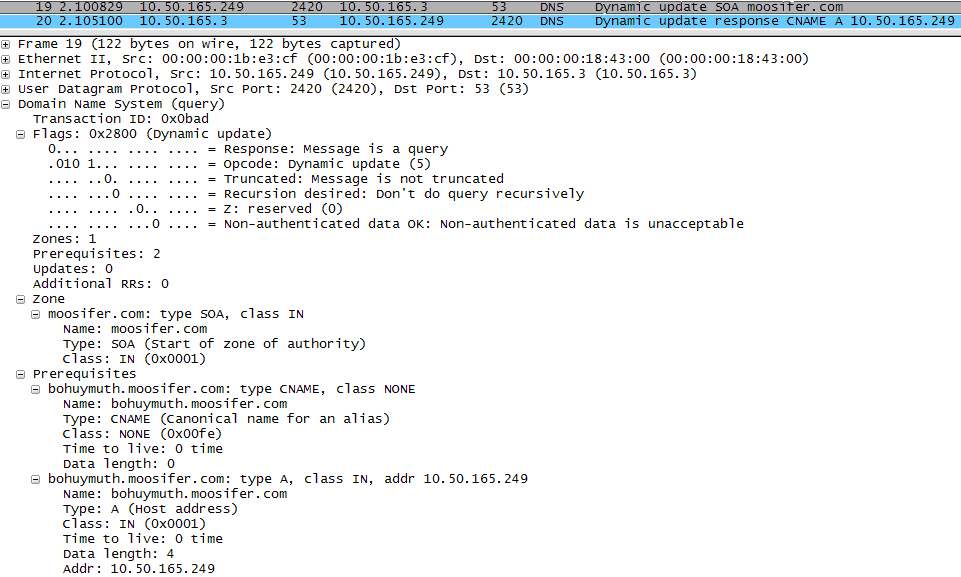
The following illustrates a packet dissection of a typical DNS dynamic update process, showing the dynamically configured host 10.50.165.249 registering its full hostname bohuymuth.moosifer.com with the (DHCP provided) DNS server 10.50.165.3:
|
•
|
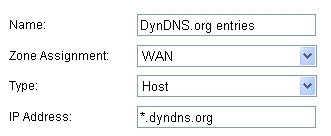
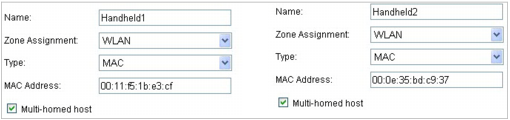
From Network > Address Objects, select Add and create the following Address Object (multi-homing optional, as needed):
|
|
•
|
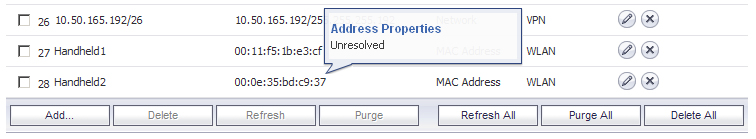
Once created, if the hosts are present in the firewall’s ARP cache, they will be resolved immediately, otherwise they will appear in an unresolved state in the Address Objects table until they are activated and are discovered through ARP:
|
|
•
|
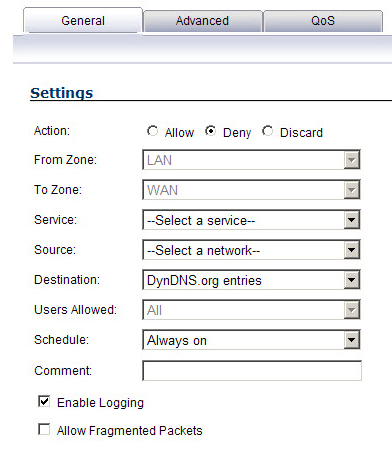
To create access rules, navigate to the Firewall > Access Rules page, click on the All Rules radio button, and scroll to the bottom of the page and click the Add button.
|
|
•
|
|
•
|
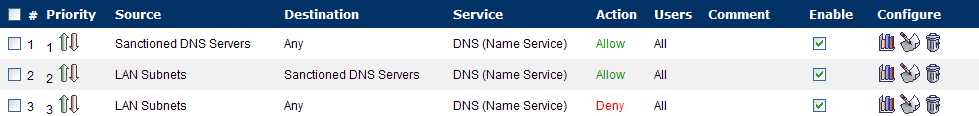
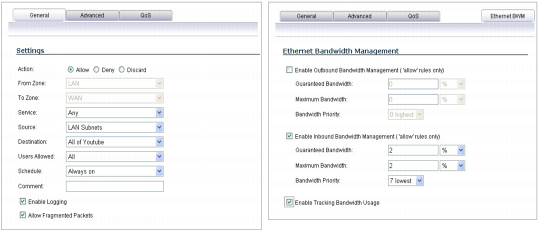
From the Firewall > Access Rules page, LAN->WAN zone intersection, add an Access Rule as follows:
|
|
NOTE: If you do not see the Bandwidth tab, you can enable bandwidth management by declaring the bandwidth on your WAN interfaces.
|
|
NOTE: The BWM icon appears within the Access Rule table, indicating that BWM is active and providing statistics. Access to all *.youtube.com hosts, using any protocol, is now be cumulatively limited to 2% of your total available bandwidth for all user sessions.
|