|
•
|
Real-Time - View logged information as it happens
|
|
•
|
Transparent - No need to halt legitimate network traffic when managing threats
|
|
•
|
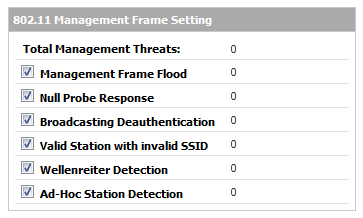
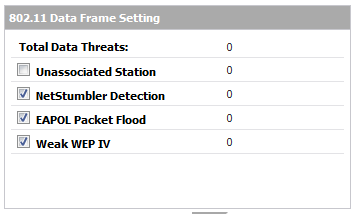
Comprehensive - Provides detection of many types of RF threats. For complete descriptions of the above types of RF Threat Detection, see Practical RF Monitoring Field Applications .
|
|
Refreshes the SonicPoint > RF Monitoring page.
|
|
|
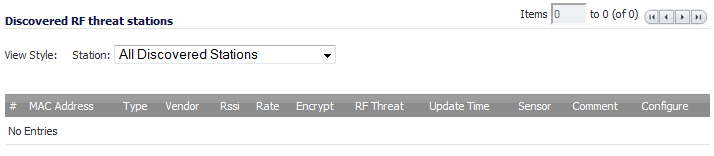
Sorts the entries by the received signal strength as reported by the SonicPoint. This entry, along with the Sensor entry, can be helpful in triangulating the actual physical position of the RF threat device.
|
|
|
Sorts the entries by the ID of the SonicPoint which recorded this threat. This entry, along with the Rssi entry, can be helpful in triangulating the actual physical position of the RF threat device.
|
|