This chapter describes how to activate, configure, and manage the Comprehensive Anti-Spam Service on a SonicWALL UTM appliance. This chapter contains the following sections:
This section provides an introduction to the Comprehensive Anti-Spam Service. This section contains the following subsections:
The Anti-Spam feature provides a quick, efficient, and effective way to add anti-spam, anti- phishing, and anti-virus capabilities to your existing SonicWALL UTM appliance.
In a typical configuration of Anti-Spam, the administrator chooses to add Anti-Spam capabilities by selecting it in the SonicOS interface and licensing it. The SonicWALL UTM appliance then uses the same advanced spam-filtering technology as the SonicWALL Email Security products to reduce the amount of junk email the organization delivers to users.
There are two primary ways inbound messages are analyzed by the Anti-Spam feature - Advanced IP Reputation Management and Cloud-based Advanced Content Management. IP Address Reputation uses the GRID Network to identify the IP addresses of known spammers, and reject any mail from those senders without even allowing a connection. GRID Network Sender IP Reputation Management checks the IP address of incoming connecting requests against a series of lists and statistics to ensure that the connection has a probability of delivering valuable email. The lists are compiled using the collaborative intelligence of the SonicWALL GRID Network. Known spammers are prevented from connecting to the SonicWALL UTM appliance, and their junk email payloads never consume system resources on the targeted systems.
Email that does not come from known spammers is analyzed based on “GRIDprints” generated by SonicWALL’s research laboratories and are based on data from millions of buiness endpoints, hundreds of millions of messages, and billions of reputation votes from the users of the GRID Network. Our Grid Network uses data from multiple SonicWALL solutions to create a collaborative intelligence network that defends against the worldwide threat landscape. GRIDprints uniquely identify messages without exposing data contained in the email message.
The Anti-Spam service determines that an email fits only one of the following threats: Spam, Likely Spam, Phishing, Likely Phishing, Virus, or Likely Virus. It uses the following precedence order when evaluating threats in email messages:
|
•
|
|
•
|
|
•
|
For example, if a message is both a virus and a spam, the message will be categorized as a virus since virus is higher in precedence than spam.
If the Anti-Spam service determines that the message is not any of the above threats, it is judged as good email and is delivered to the destination server.
Adding anti-spam protection to your SonicWALL UTM appliance increases the efficiency of your system as a whole by filtering and rejecting junk messages before users see them in their inboxes.
|
•
|
Reduced threat to the organization, because users cannot accidentally infect their
computers by clicking on virus spam
|
This section describes the Anti-Spam feature, including the SonicWALL GRID Network, and how it interacts with SonicOS as a whole. The two points of significant connection with SonicOS are Address and Service Objects. You can use the address and service objects to configure the Anti-Spam feature to function smoothly with SonicOS. For example, use the Anti-Spam Service Object to configure NAT policies to archive inbound email as well as sending it through a filter.
The Comprehensive Anti-Spam Service analyzes messages’ headers and contents, and uses collaborative GRIDprinting to block spam email.
This section describes the GRID Connection Management with Sender IP Reputation feature that is used by SonicWALL Email Security and by the Anti-Spam service in SonicOS. GRID Network Sender IP Reputation is the reputation a particular IP address has with members of the SonicWALL GRID Network. When this feature is enabled, email is not accepted from IP addresses with a bad reputation. When SonicOS will not accept a connection from a known bad IP address, mail from that IP address never reaches the email server.
GRID Network Sender IP Reputation checks the IP address of incoming connection requests against a series of lists and statistics to ensure that the connection has a probability of delivering valuable email. The lists are compiled using the collaborative intelligence of the SonicWALL GRID Network. Known spammers are prevented from connecting to the SonicWALL UTM appliance, and their junk email payloads never consume system resources on the targeted systems.
|
•
|
As much as 80 percent of junk email is blocked at the connection level, before the email is
ever accepted into your network. Fewer resources are required to maintain your level of spam protection.
|
|
•
|
|
•
|
A global network watches for spammers and helps legitimate users restore their IP
reputations if needed.
|
When a request is sent to your first-touch SonicWALL UTM appliance, the Anti-Spam service evaluates the ‘reputation’ of the requestor. The reputation is compiled from white lists of known-good senders, block lists of known spammers, and denial-of-service thresholds.
If IP Reputation is enabled, the source IP address is checked in this order:
|
If an IP address is on this list, it is allowed to pass messages through
Connection Management. The messages will be analyzed by your SonicWALL UTM appliance as usual. |
|
|
If the IP address is not in the previous lists, the SonicWALL UTM
appliance checks with the GRID Network to see if this IP address has a bad reputation. |
|
|
Connections from this IP address are deferred. A set interval must pass
before the connection is allowed.
|
|
|
If the IP address is not on the previous lists, the SonicWALL UTM
appliance checks to see if the IP address has crossed the Denial of Service threshold. If it has, the appliane uses the existing DoS settings to take action. |
Only if the IP address passes all of these tests does the SonicWALL UTM appliance allow that server to make a connection and transfer mail. If the IP address does not pass the tests, there is a message from SonicOS to the requesting server indicating that there is no SMTP server. The connection request is not accepted.
The Anti-Spam feature of SonicOS introduces new Address and Service Objects to manage a customer’s email server(s). These objects are used by the Anti-Spam Service for its NAT and Access Rule policies. Automatically-created rules are not editable and will be deleted if the Anti-Spam Service is disabled.
When enabled, the Anti-Spam service creates NAT policies and Access Rules to control and redirect email traffic. The policies and rules are visible in the Network > NAT Policies and Firewall Rules pages, but are not editable. These automatically-created policies are only available when the Anti-Spam service is enabled.
When the Anti-Spam service is licensed and activated, the Anti-Spam > Settings page shows a single checkbox to enable Anti-Spam. Selecting the checkbox invokes the Destination Mail Server Policy Wizard if there is no existing custom access rule and NAT policy for an already-deployed scenario. When you set up generated policies, the Anti-Spam service must know where the emails are routed behind the SonicWALL UTM appliance. Specifically it needs the destination mail server IP address and its zone assignment. The Destination Mail Server Policy Wizard is launched if this data cannot be found.
You will need the following information for the wizard:
|
•
|
Destination Mail Server Public IP Address
– The IP address to which external MTAs will be connecting by SMTP.
|
|
•
|
Destination Mail Server Private IP Address
– The internal IP address (behind the SonicWALL UTM appliance) of the Exchange or SMTP server.
|
|
•
|
Zone Assignment
– The zone to which the Exchange server is assigned.
|
|
•
|
Inbound Email Port
– The TCP service port number to which emails will be sent, also known as the inbound SMTP port.
|
Policies and Address Objects created by the wizard are editable and persist even if the Anti-Spam service is disabled.
This section provides an example of the type of rules and objects generated automatically as Firewall Access Rules, NAT Policies and Service Objects. These objects are not editable and will be removed if the Anti-Spam service is disabled.
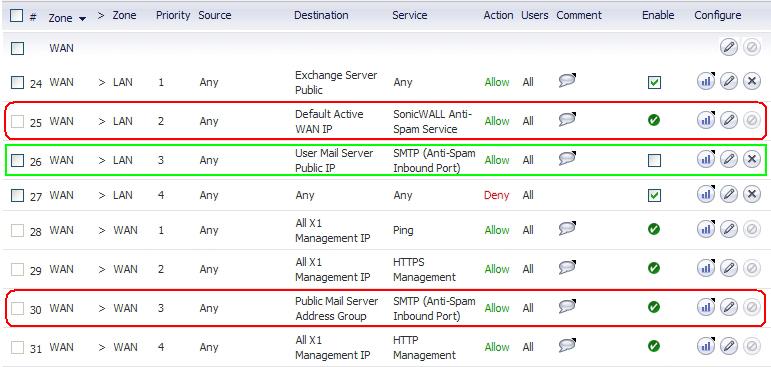
The Firewall > Access Rules page shows the generated rules used for Anti-Spam.
|
Figure 57:1
|
The rows outlined in red are the access rules generated when Anti-Spam is activated. The row outlined in green is the default rule that Anti-Spam creates if there are no existing mail server policies.
You could also create the following access rules:
|
•
|
WAN to LAN rule for processed email from Email Security Service to all the WAN IP
address using the Anti-Spam service port (default:10025)
|
The Anti-Spam Service Object is created in the Network > Services page.
|
Figure 57:2
|
This Service Object is referenced by the generated NAT policies.
|
Figure 57:3
|
The rows outlined in red are the policies generated when Anti-Spam is activated. The row outlined in green is the default policy that Anti-Spam creates if there are no existing mail server policies.
Objects created from an administrator’s interaction with the wizard can be edited and stay in the system even if the Anti-Spam service is disabled.
The following considerations apply to the auto-generation of policies:
|
•
|
A system Address Group Object called the
Public Mail Server Address Group
is created as a default for the original destination for generated policies. This group contains the Address Object, Destination Mail Server Public IP
, which takes the IP address value provided during the wizard.
|
|
•
|
In the case where a SonicWALL UTM device already has existing policies for SMTP, the
following procedures occur:
|
|
–
|
If the existing policy’s original destination is a host type Address Object, then the
generated policies use the Public Mail Server Address Group
object as their original destination.
|
|
–
|
If the existing policy’s original destination is a non-host type Address Object, the
generated policies use this non-host type Address Object as their original destination.
|
|
–
|
If there is more than one public IP address for SMTP, the administrator can manually
add Address Objects to the Public Mail Server Address Group
.
|
In the diag.html page, the Reset GRID Name Cache button can be used to clear all the entries in the GRID name cache.
The Delete Policies and Objects button can be used to remove Anti-Spam Address and Service Objects and policies that are not deleted when the service is turned off. When this button is clicked, SonicOS attempts to remove all the automatically generated objects and policies. This operation is only allowed when the Anti-Spam service is off.
|
Figure 57:4
|
The other diag.html page options relating to Anti-Spam are:
|
•
|
Disable SYN Flood Protection for Anti-Spam related connections
– SYN Flood protection by default is turned on for SMTP (25) and Anti-Spam service (10025) ports. This disables the protection.
|
|
•
|
Use GRID IP reputation check only
– When selected, this overrides the probing result and simulates the Anti-Spam service being unavailable (admin down). When an email is sent, it still goes through both the SYN FLOOD check and GRID IP check, but other email scanning is not performed.
|
The RBL Filter configuration screen was previously located under Security Services in the left navigation pane. Now find it under the Anti-Spam menu group.
The Anti-Spam service is an advanced superset of the standard SonicOS RBL Filtering. Therefore when Anti-Spam is turned on, RBL Filtering is automatically disabled.
If Anti-Spam is not enabled, you can configure the settings on the RBL Filter page.
The Anti-Spam feature is supported on all SonicWALL appliances that support SonicOS Enhanced 5.4 or higher.