|
1
|
|
2
|
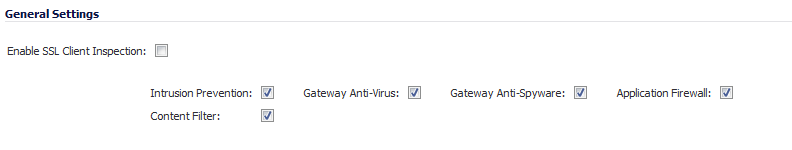
Select the Enable SSL Client Inspection checkbox. By default, this checkbox is not enabled.
|
|
4
|
Click Accept.
|
|
NOTE: For information about requesting/creating a DPI SSL Certificate Authority (CA) certificate, see the Knowledge Base article, How to request/create DPI-SSL Certificate Authority (CA) certificates for the purpose of DPI-SSL certificate resigning (SW14090) in the Dell Support Site.
|
|
1
|
|
2
|
Select the certificate to use from the Certificate drop-down menu. By default, DPI-SSL uses the Default Dell SonicWALL DPI-SSL CA certificate to re-sign traffic that has been inspected.
|
|
NOTE: If the certificate you want is not listed, you can import it from the System > Certificates page by clicking on the (Manage Certificates) link. See Importing Certificates . For PKCS-12-formatted certificates, see Creating PKCS-12 Formatted Certificate File .
|
|
3
|
To download the selected certificate to the firewall, click the (download) link. The Opening filename dialog appears.
|
|
TIP: To view available certificates, click on the (Manage Certificates) link to display the System > Certificates page
|
|
a
|
Ensure the Save File radio button is selected.
|
|
b
|
Click OK.
|
|
4
|
Click Accept.
|
|
•
|
|
•
|
Certificate with a public key (typically a file with .crt extension or the word cert as part of filename).
|
/etc/httpd/conf/ssl.key/server.key
/etc/httpd/conf/ssl.crt/server.crt
With these two files available, run the following command:
openssl pkcs12 -export -out out.p12 -inkey server.key -in server.crt
In this example, out.p12 becomes the PKCS-12-formatted certificate file, and server.key and server.crt are the PEM-formatted private key and certificate file respectively.
|
•
|
Exclusion/Inclusion lists exclude/include specified objects and groups
|
|
•
|
Common Name exclusions excludes specified host names
|
|
•
|
CFS Category-based Exclusion/Inclusion excludes or includes specified categories based on CFS categories
|
|
1
|
|
2
|
From the Address Object/Group Exclude and Include drop-down menus, select an address object or group to exclude or include from DPI-SSL inspection. By default, Exclude is set to None and Include is set to All.
|
|
TIP: The Include drop-down menu can be used to fine tune the specified exclusion list. For example, by selecting the Remote-office-California address object in the Exclude drop-down menu and the Remote-office-Oakland address object in the Include drop-down menu.
|
|
3
|
From the Service Object/Group Exclude and Include drop-down menus, select an address object or group to exclude or include from DPI-SSL inspection. By default, Exclude is set to None and Include is set to All.
|
|
4
|
From the User Object/Group Exclude and Include drop-down menus, select an address object or group to exclude or include from DPI-SSL inspection. By default, Exclude is set to None and Include is set to All.
|
|
5
|
Click Accept.
|
|
1
|
|
a
|
Enter the name in the Suffix field.
|
|
b
|
Click the Add button.
|
|
3
|
Click Accept at the top of the page to confirm the configuration.
|
|
1
|
Select the name in the Exclusions.
|
|
2
|
Click the Remove button.
|
|
3
|
Click Accept.
|
|
1
|
Navigate to the DPI-SSL > Client SSL page.
|
|
2
|
Select the Enable SSL Inspection checkbox.
|
|
3
|
|
4
|
Click Apply.
|
|
5
|
|
6
|
Ensure Content Filter Service is selected from the drop-down menu.
|
|
7
|
|
8
|
|
9
|
|
10
|
Click OK.
|
|
11
|
Click Accept.
|
To filter by application firewall rules, you need to enable them on both the DPI-SSL > Client SSL page and the App Rules > Policies page.
|
1
|
|
2
|
Select the Enable SSL Client Inspection checkbox.
|
|
3
|
Select the Application Firewall checkbox.
|
|
4
|
Click Apply.
|
|
5
|
|
6
|
|
7
|
Configure an HTTP Client policy to block Microsoft Internet Explorer browser with block page as an action for the policy. For how to configure an App Rule, see Configuring an App Rules Policy .
|
|
8
|
Click Apply.
|