|
1
|
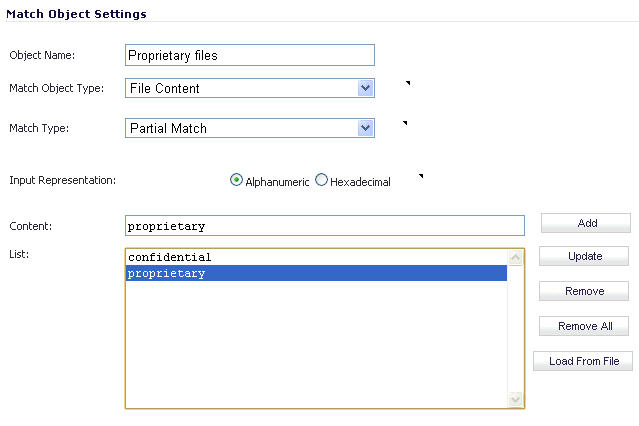
Create a match object of type File Content that matches on keywords in files.
|
Optionally, you can create a customized FTP notification action that sends a message to the client.
|
2
|
Create a policy that references this match object and action. If you prefer to simply block the file transfer and reset the connection, you can select the Reset/Drop action when you create the policy.
|
The example shown below uses a match object type of File Content with a UTF-16 encoded Chinese keyword that translates as “confidential document.”
|
3
|
Create a policy that references the match object, as shown below. This policy blocks the file transfer and resets the connection. Enable Logging is selected so that any attempt to transfer a file containing the UTF-16 encoded keyword is logged.
|
A log entry is generated after a connection Reset/Drop. An example of a log entry is shown below, including the Message stating that it is an Application Control Alert, displaying the Policy name and the Action Type of Reset/Drop.
You can use Application Control to ensure that your FTP server is read-only by blocking commands such as put, mput, rename_to, rename_from, rmdir, and mkdir. This use case shows an match object containing only the put command, but you could include all of these commands in the same match object.
|
1
|
Create a match object that matches on the put command. Because the mput command is a variation of the put command, a match object that matches on the put command will also match on the mput command.
|
|
3
|
Create a policy that references this match object and action. If you prefer to simply block the put command and reset the connection, you can select the Reset/Drop action when you create the policy.
|