The list of users read from the LDAP server can be quite long, and you will probably only want to import a small number of them. A Remove from list button is provided, along with several methods of selecting unwanted users.You can use these options to reduce the list to a manageable size and then select the users to import.
|
1
|
Navigate to the Users > Settings page.
|
|
2
|
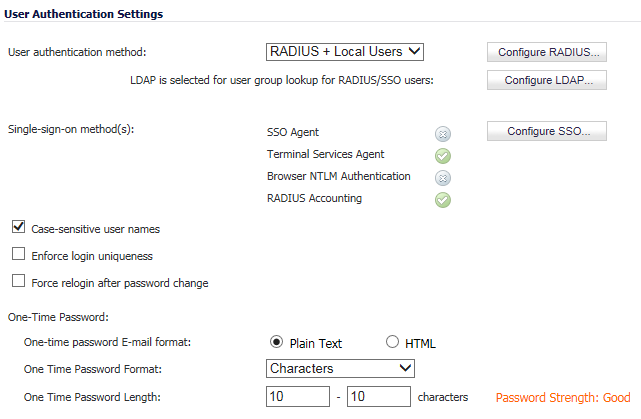
Set the User authentication method to LDAP or LDAP + Local Users. The Configure LDAP button moves up.
|
|
3
|
|
4
|
In the Settings tab, configure these server options:
|
|
a
|
Enter the name or IP address of the LDAP server in the Name or IP address field.
|
|
•
|
|
•
|
Choose a port from the Standard port choices… drop-down menu:
|
If you choose a port from the Standard port choices… drop-down menu, the port number changes to that of the specified choice.
|
c
|
Enter a maximum time to wait for each response from the LDAP server over the network in the Server timeout (seconds) field. The default is 10 seconds.
|
|
d
|
Enter a maximum time to spend on any auto operation in the Overall operation timeout (minutes) field. The default is 5 minutes.
|
|
•
|
Anonymous login (default)
|
|
•
|
Bind distinguished name (binds the distinguished name to the LDAP server
|
|
•
|
Anonymous login, go to Step 7.
|
|
•
|
|
a
|
Enter the name that is in the first component of the user’s distinguished name and not their login ID in the Login user name field. For example, John Doe may normally log in as jdoe, but you would enter John Doe in the field.
|
|
b
|
Enter the login password in the Login password field.
|
|
•
|
Bind distinguished name, the fields change.
|
|
a
|
Enter the full distinguished name (DN) to use to bind to the LDAP server in the Bind distinguished name field.
|
|
b
|
Enter the login password in the Login password field.
|
|
7
|
Select which protocol version to use from the Protocol version drop-down menu:
|
|
•
|
LDAP version 3 (default)
|
|
8
|
To enable TLS mode, ensure the Use TLS (SSL) checkbox is selected. It is enabled by default.
|
|
9
|
To allow an LDAP server to operate in both TLS and non-TLS modes on the same TCP port, select the Send LDAP ‘Start TLS’ request checkbox.
|
|
10
|
To require valid certificates from the LDAP server in TLS mode, ensure the Require valid certificate from server checkbox is selected. It is enabled by default.
|
|
11
|
Optionally, select a local certificate for TLS from the Local certificate for TLS drop-down menu. The default is None.
|
|
12
|
Click the Schema tab.
|
|
1
|
|
•
|
Microsoft Active Directory (default)
|
|
NOTE: What options are available and which are dimmed (unavailable) in the User Objects and User Group Objects sections change according to the schema you choose.
|
|
2
|
If you selected User defined schema, enter an object class in the Object class field. The default is user. These are the default values for the other schemas and cannot be changed:
|
|
•
|
|
•
|
RFC2798 InetOrgPerson – inetOrgPerson
|
|
•
|
RFC2307 Network Information Service – posixAccount
|
|
•
|
Samba SMB – sambaSAMAccount
|
|
•
|
NovelleDirectory – inetOrgPerson
|
|
3
|
If you selected User defined schema, enter a login name attribute in the Login name attribute field. The default is on. These are the default values for the other schemas and cannot be changed:
|
|
•
|
Microsoft Active Directory – sAMAccountName
|
|
•
|
|
•
|
Samba SMB – uid
|
|
•
|
|
4
|
Optionally, in the Qualified login name attribute, specify an attribute of a user object that sets an alternative login name of the user in name@domain format. This may be needed with multiple domains in particular, where the simple login name may not be unique across domains. These are the default values:
|
|
•
|
Microsoft Active Directory – userPrincipalName
|
|
•
|
|
•
|
|
NOTE: With Active Directory, this would normally be userPrincipalName for login using name@domain, but could be set to mail to enable login by email address.
|
|
5
|
If you selected User defined schema, enter a user group-membership attribute in the User group membership attribute field. There is no default. These are the default values for the other schemas and cannot be changed:
|
|
•
|
Microsoft Active Directory – memberOf
|
|
•
|
|
6
|
Optionally, specify an additional user ID group attribute in the Additional user group ID attribute field and select the Use checkbox to enable the attribute’s use. The Additional user group ID attribute, along with the Additional user group match attribute in the User Group Objects section, allow for a schema that may set additional memberships for a user in addition to those that are found via a member and/or memberOf attributes; for example, Active Directory’s group attribute.
|
If the Additional user group ID attribute is specified and its use is enabled, then when a user object is found with one or more instances of this attribute, a search for additional user groups matching those attributes will be made in the LDAP directory. If a group is found with the Additional user group match attribute set to that value, then the user is also made a member of that group.
|
NOTE: If the LDAP schema is set to Microsoft Active Directory, then the default is PrimaryGroupID and cannot be changed. To use this value, however, you must select the Use checkbox to enable the function.
With Active Directory, this value, along with the Additional user group match attribute value, gives users membership in their primary user group (typically, Domain Users). |
|
7
|
In the LDAP Import Users dialog, you can select individual users or select all users. To select all users in the list, select the Select/deselect all checkbox at the top of the list. To clear all selections, click it again.
|
|
8
|
|
•
|
To remove the users whose checkboxes you have selected, select the All selected users radio button.
|
|
•
|
To remove certain users on the basis of name, description, or location, select the Any user whose <field1> contains <field2> radio button. Select name, description, or location from the Any user whose drop-down menu and type the value to match in the contains field.
|
In this option, name refers to the user name displayed in the left column of the list, description refers to the description displayed to its right (not present for all users), and location refers to the location of the user object in the LDAP directory. The location, along with the full user name, is displayed by a mouse-over on a user name, as shown in the image above.
For example, you might want to remove accounts that are marked as “Disabled” in their descriptions. In this case, select description in the first field and type Disabled in the second field. The second field is case-sensitive, so if you typed disabled you would prune out a different set of users.
|
•
|
To remove certain users from the list on the basis of their location in the LDAP directory, select the All users <drop-down-menu1> <drop-down-menu2> radio button. From the first drop-down menu, select either at or at or under. From the second drop-down menu, select the LDAP directory location.
|
|
10
|
To undo all changes made to the list of users, click Undo. A confirmation message displays.
|
|
11
|
Click OK in the confirmation message.
|
|
12
|
When finished pruning out as many unwanted accounts as possible with the Remove from list options, use the checkboxes in the list to select the accounts to import.
|
|
13
|
Click Save selected.
|