|
•
|
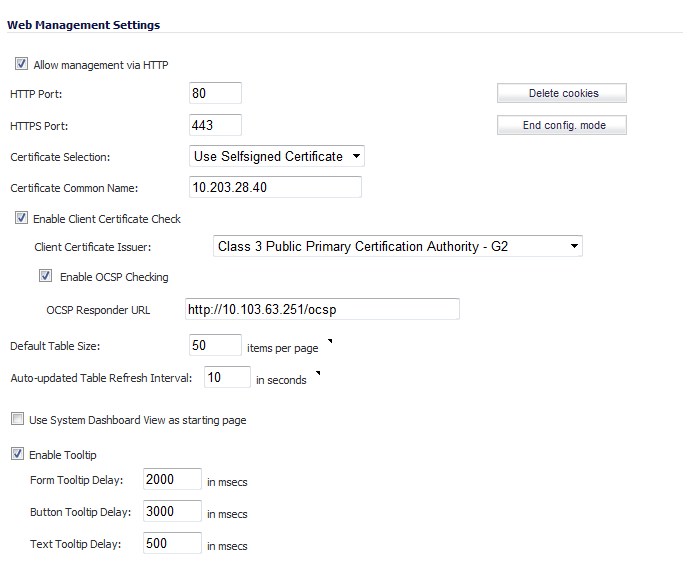
If you wish to use HTTP management, an Allow management via HTTP checkbox is available to allow you to enable/disable HTTP management globally.
The default port for HTTPS management is 443. You can add another layer of security for logging into the SonicWALL security appliance by changing the default port. To configure another port for HTTPS management, type the preferred port number into the Port field, and click Update. For example, if you configure the HTTPS Management Port to be 700, then you must log into the SonicWALL using the port number as well as the IP address, for example, <https://192.168.168.1:700> to access the SonicWALL.
The default port for HTTP is port 80, but you can configure access through another port. Type the number of the desired port in the Port field, and click Accept. However, if you configure another port for HTTP management, you must include the port number when you use the IP address to log into the SonicWALL security appliance. For example, if you configure the port to be 76, then you must type <LAN IP Address>:76 into the Web browser, i.e. <http://192.168.168.1:76>.
The Certificate Selection menu allows you to use a self-signed certificate (Use Self-signed Certificate), which allows you to continue using a certificate without downloading a new one each time you log into the SonicWALL security appliance. You can also choose Import Certificate to select an imported certificate from the System > Certificates page to use for authentication to the management interface.
The Delete Cookies button removes all browser cookies saved by the SonicWALL appliance. Deleting cookies will cause you to lose any unsaved changes made in the Management interface.
To see the Dashboard > Threat Reports page first when you login, select the Use System Dashboard View as starting page checkbox.
On the System > Administration page, under Web Management Settings, you can enable a Client Certificate Check for use with or without a Common Access Card (CAC).
A Common Access Card (CAC) is a United States Department of Defense (DoD) smart card used by military personnel and other government and non-government personnel that require highly secure access over the internet. A CAC uses PKI authentication and encryption.
The Client Certificate Check was developed for use with a CAC; however, it is useful in any scenario that requires a client certificate on an HTTPS/SSL connection. CAC support is available for client certification only on HTTPS connections.
The Enable Client Certificate Check box allows you to enable or disable client certificate checking and CAC support on the SonicWALL security appliance.
The Client Certificate Issuer drop-down menu contains a list of the Certification Authority (CA) certificate issuers that are available to sign the client certificate. If the appropriate CA is not in the list, you need to import that CA into the SonicWALL security appliance.
The Enable OCSP Checking box allows you to enable or disable the Online Certificate Status Protocol (OCSP) check for the client certificate to verify that the certificate is still valid and has not been revoked.
The OCSP Responder URL field contains the URL of the server that will verify the status of the client certificate. The OCSP Responder URL is usually embedded inside the client certificate and does not need to be entered. If the client certificate does not have an OCSP link, you can enter the URL link. The link should point to the Common Gateway Interface (CGI) on the server side which processes the OCSP checking. For example: http://10.103.63.251/ocsp
If you use the Client Certificate Check with a CAC, the client certificate is automatically installed on the browser by middleware. When you begin a management session through HTTPS, the certificate selection window is displayed asking you to confirm the certificate.
After you select the client certificate from the drop-down menu, the HTTPS/SSL connection is resumed, and the SonicWALL security appliance checks the Client Certificate Issuer to verify that the client certificate is signed by the CA. If a match is found, the administrator login page is displayed. If no match is found, the browser displays a standard browser connection fail message, such as:
Client Certificate OCSP Checking.....
If no match is found, the browser displays the following message:
OCSP Checking fail! Please contact system administrator!
|
•
|
Enable Client Certificate Check is checked, but no client certificate is installed on the browser.
|
|
•
|
Enable Client Certificate Check is checked and a client certificate is installed on the browser, but either no Client Certificate Issuer is selected or the wrong Client Certificate Issuer is selected.
|
|
•
|
Enable OSCP Checking is enabled, but either the OSCP server is not available or a network problem is preventing the SonicWALL security appliance from accessing the OSCP server.
|
To restore access to a user that is locked out, the following CLI commands are provided:
|
1
|
|
2
|
Enter the desired interval for background automatic refresh of Monitor tables (including Process Monitor, Active Connections Monitor, and Interface Traffic Statistics) in seconds in the Auto-updated Table Refresh Interval field.
|
|
3
|
Click Accept.
|
Tooltips are enabled by default. To disable Tooltips, clear the Enable Tooltip checkbox. You can configure the duration of time before Tooltips display:
|
•
|
Form Tooltip Delay - Duration in milliseconds before Tooltips display for forms (boxes where you enter text). The default is 2000 ms.
|
|
•
|
Button Tooltip Delay - Duration in milliseconds before Tooltips display for radio buttons and checkboxes. The default is 3000 ms.
|
|
•
|
Text Tooltip Delay - Duration in milliseconds before Tooltips display for UI text. The default is 500 ms.
|