 jumps to the desktop of the technician’s or customer’s computer.
jumps to the desktop of the technician’s or customer’s computer.SSL-VPN_Concepts
Concepts for Dell SonicWALL SRA
This section provides an overview of the following key concepts, with which the administrator should be familiar when using the SRA appliance and Web-based management interface:
• Browser Requirements for the SRA Administrator
• Browser Requirements for the SRA End User
• Application Offloading and HTTP(S) Bookmarks Overview
• Two-Factor Authentication Overview
• Secure Virtual Assist Overview
• Web Application Firewall Overview
Encryption enables users to encode data, making it secure from unauthorized viewers. Encryption provides a private and secure method of communication over the Internet.
A special type of encryption known as Public Key Encryption (PKE) comprises a public and a private key for encrypting and decrypting data. With public key encryption, an entity, such as a secure Web site, generates a public and a private key. A secure Web server sends a public key to a user who accesses the Web site. The public key allows the user’s Web browser to decrypt data that had been encrypted with the private key. The user’s Web browser can also transparently encrypt data using the public key and this data can only be decrypted by the secure Web server’s private key.
Public key encryption allows the user to confirm the identity of the Web site through an SSL certificate. After a user contacts the SRA appliance, the appliance sends the user its own encryption information, including an SSL certificate with a public encryption key.
The following procedure is an example of the standard steps required to establish an SSL session between a user and an SRA gateway using the SRA Web-based management interface:
1. When a user attempts to connect to the SRA appliance, the user’s Web browser sends information about the types of encryption supported by the browser to the appliance.
2. The appliance sends the user its own encryption information, including an SSL certificate with a public encryption key.
3. The Web browser validates the SSL certificate with the Certificate Authority identified by the SSL certificate.
4. The Web browser generates a pre-master encryption key, encrypts the pre-master key using the public key included with the SSL certificate and sends the encrypted pre-master key to the SRA gateway.
5. The SRA gateway uses the pre-master key to create a master key and sends the new master key to the user’s Web browser.
6. The browser and the SRA gateway use the master key and the agreed upon encryption algorithm to establish an SSL connection. From this point on, the user and the SRA gateway will encrypt and decrypt data using the same encryption key. This is called symmetric encryption.
7. Once the SSL connection is established, the SRA gateway will encrypt and send the Web browser the SRA gateway login page.
8. The user submits his user name, password, and domain name.
9. If the user’s domain name requires authentication through a RADIUS, LDAP, NT Domain, or Active Directory Server, the SRA gateway forwards the user’s information to the appropriate server for authentication.
10. Once authenticated, the user can access the SRA portal.
Internet Protocol version 6 (IPv6) is a replacement for IPv4 that is becoming more frequently used on networked devices. IPv6 is a suite of protocols and standards developed by the Internet Engineering Task Force (IETF) that provides a larger address space than IPv4, additional functionality and security, and resolves IPv4 design issues. You can use IPv6 without affecting IPv4 communications.
IPv6 supports stateful address configuration, which is used with a DHCPv6 server, and stateless address configuration, where hosts on a link automatically configure themselves with IPv6 addresses for the link, called link-local addresses.
In IPv6, source and destination addresses are 128 bits (16 bytes) in length. For reference, the 32-bit IPv4 address is represented in dotted-decimal format, divided by periods along 8-bit boundaries. The 128-bit IPv6 address is divided by colons along 16-bit boundaries, where each 16-bit block is represented as a 4-digit hexadecimal number. This is called colon-hexadecimal.
The IPv6 address, 2008:0AB1:0000:1E2A:0123:0045:EE37:C9B4 can be simplified by removing the leading zeros within each 16-bit block, as long as each block has at least one digit. When suppressing leading zeros, the address representation becomes: 2008:AB1:0:1E2A:123:45:EE37:C9B4
When addresses contain contiguous sequences of 16-bit blocks set to zeros, the sequence can be compressed to ::, a double-colon. For example, the link-local address of 2008:0:0:0:B67:89:ABCD:1234 can be compressed to 2008::B67:89:ABCD:1234. The multicast address 2008:0:0:0:0:0:0:2 can be compressed to 2008::2.
The IPv6 prefix is the part of the address that indicates the bits of the subnet prefix. Prefixes for IPv6 subnets, routes, and address ranges are written as address/prefix-length, or CIDR notation. For example, 2008:AA::/48 and 2007:BB:0:89AB::/64 are IPv6 address prefixes.
SonicOS SSL VPN supports IPv6 in the following areas:
Services
• FTP Bookmark – Define a FTP bookmark using an IPv6 address.
• Telnet Bookmark – Define a Telnet bookmark using an IPv6 address.
• SSHv1 / SSHv2 Bookmark – Define an SSHv1 or SSHv2 bookmark using an IPv6 address.
• Reverse proxy for HTTP/HTTPS Bookmark – Define an HTTP or HTTPS bookmark using an IPv6 address.
• Citrix Bookmark – Define a Citrix bookmark using an IPv6 address.
• RDP Bookmark - Define an RDP bookmark using an IPv6 address.
• VNC Bookmark - Define a VNC bookmark using an IPv6 address.
Note IPv6 is not supported for File Shares (CIFS).
Settings
• Interface Settings – Define an IPv6 address for the interface. The link-local address is displayed in a tooltip on Interfaces page.
• Route Settings – Define a static route with IPv6 destination network and gateway.
• Network Object – Define the network object using IPv6. An IPv6 address and IPv6 network can be attached to this network object.
NetExtender
When a client connects to NetExtender, it can get an IPv6 address from the SRA appliance if the client machine supports IPv6 and an IPv6 address pool is configured on the SRA. NetExtender supports IPv6 client connections from Windows systems running Vista or newer, and from Linux clients.
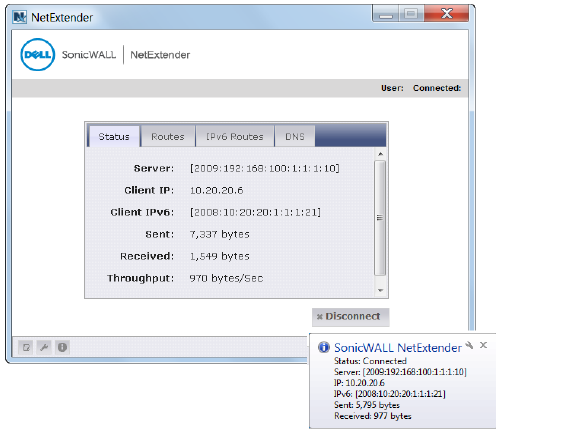
Secure Virtual Assist
Users and Technicians can request and provide support when using IPv6 addresses.
Rules
• Policy rule – User or Group Policies. Three IPv6 options in the Apply Policy To drop-down list:
– IPv6 Address
– IPv6 Address Range
– All IPv6 Address
• Login rule – Use IPv6 for address fields:
– Define Login From Defined Addresses using IPv6
– Two IPv6 options in the Source Address drop-down list: IPv6 Address / IPv6 Network
Virtual Hosts
An administrator can assign an IPv6 address to a virtual host, and can use this address to access the virtual host.
Application Offloading
An administrator can assign an IPv6 address to an application server used for application offloading, and can use this address to access the server.
Browser Requirements for the SRA Administrator
The following Web browsers are supported for the SRA Web-based management interface and the user portal, Virtual Office. Java is only required for various aspects of the SRA Virtual Office, not the management interface:
|
To configure SRA appliance using the Web-based management interface, an administrator must use a Web browser with Java, JavaScript, ActiveX, cookies, popups, and SSLv3 or TLS 1.0 enabled.
Windows XP and Internet Explorer 8 Update
Microsoft has ended support for Windows XP and IE8. Dell SonicWALL SRA clients will still continue to work, but may become more vulnerable to security risks and viruses. Dell SonicWALL will no longer provide fixes for issues exclusively affecting Windows XP and IE8. Dell SonicWALL strongly encourages Windows users to migrate to versions supported by Microsoft. For more information, refer to the Microsoft Windows website:
http://windows.microsoft.com/en-us/windows/end-support-help
Browser Requirements for the SRA End User
The following is a list of Web browser and operating system support for various SRA protocols including NetExtender and various Application Proxy elements. Minimum browser version requirements are shown for Windows, Windows Vista, Windows 7, Linux, and MacOS.
The following table provides specific browser requirements for the SSL VPN End User Interface:
|
Windows XP and Internet Explorer 8 Update
Microsoft has ended support for Windows XP and IE8. Dell SonicWALL SRA clients will still continue to work, but may become more vulnerable to security risks and viruses. Dell SonicWALL will no longer provide fixes for issues exclusively affecting Windows XP and IE8. Dell SonicWALL strongly encourages Windows users to migrate to versions supported by Microsoft. For more information, refer to the Microsoft Windows website:
http://windows.microsoft.com/en-us/windows/end-support-help
The SRA appliance provides a mechanism called Virtual Office, which is a Web-based portal interface that provides clients with easy access to internal resources in your organization. Components such as NetExtender, Secure Virtual Assist, and bookmarks to file shares and other network resources are presented to users through the Virtual Office portal. For organizations with multiple user types, the SRA appliance allows for multiple customized portals, each with its own set of shared resource bookmarks. Portals also allow for individual domain and security certificates on a per-portal basis. The components in a portal are customized when adding a portal.
File Shares
File shares provide remote users with a secure Web interface to Microsoft File Shares using the CIFS (Common Internet File System) or SMB (Server Message Block) protocols. Using a Web interface similar in style to Microsoft’s familiar Network Neighborhood or My Network Places, File Shares allow users with appropriate permissions to browse network shares, rename, delete, retrieve, and upload files, and to create bookmarks for later recall. File shares can be configured to allow restricted server path access.
Custom Portals
SRA appliances let you configure multiple portals, each with its own title, banner, login message, logo and set of available resources. Each portal also enables you to set individual Virtual Hosts/Domain Names to create a unique default portal URL. When a user logs into a portal, he or she sees a set of pre-configured links and bookmarks that are specific to that portal. You can configure whether or not NetExtender is displayed on a Virtual Office portal, and if you want NetExtender to automatically launch when users log in to the portal. The administrator configures which elements each portal displays through the Portal Settings window. For information on configuring portals, refer to Portals > Portals.
A domain in the SRA environment is a mechanism that enables authentication of users attempting to access the network being serviced by the SRA appliance. Domain types include the SRA internal LocalDomain, and the external platforms Microsoft Active Directory, NT Authentication, LDAP, and RADIUS. Often, only one domain will suffice to provide authentication to your organization, although a larger organization may require distributed domains to handle multiple nodes or collections of users attempting to access applications through the portal. For information about configuring domains, refer to Portals > Domains.
Application Offloading and HTTP(S) Bookmarks Overview
SRA appliances use HTTP(S) bookmarks and application offloading to provide access to Web-based applications running on servers within the intranet. This includes Sharepoint 2007 and the enhanced versions of commonly-used Web mail interfaces, such as Microsoft OWA Premium and Domino Web Access 8.0.1, 8.5.1, and 8.5.2. Sharepoint 2010 is supported with application offloading, but not with HTTP(S) bookmarks.
Both application offloading and HTTP(S) bookmarks use an HTTP(S) reverse proxy. A reverse proxy is a proxy server that is deployed between a remote user outside an intranet and a target Web server within the intranet. The reverse proxy intercepts and forwards packets that originate from outside the intranet. An HTTP(S) reverse proxy specifically intercepts HTTP(S) requests and responses.
Application Offloading provides secure access to both internal and publicly hosted Web applications. An application offloading host is created as a special-purpose portal with an associated virtual host acting as a proxy for the backend Web application.
Unlike HTTP(S) bookmarks, access to offloaded applications is not limited to remote users. The administrator can enforce strong authentication and access policies for specific users or groups. For instance, in an organization certain guest users may need Two-factor or Client Certificate authentication to access Outlook Web Access (OWA), but are not allowed to access OWA public folders. If authentication is enabled, multiple layers of advanced authentication features such as One Time Password, Two-factor Authentication, Client Certificate Authentication and Single Sign-On can be applied on top of each other for the offloaded host.
The offloaded application portal must be configured as a virtual host with a suitable SRA domain. It is possible to disable authentication and access policy enforcement for such an offloaded host.
Web transactions can be centrally monitored by viewing the logs. In addition, Web Application Firewall can protect offloaded application hosts from any unexpected intrusion, such as Cross-site scripting or SQL Injection.
Access to offloaded Web applications happens seamlessly as URLs in the proxied page are not rewritten in the manner used by HTTP or HTTPS bookmarks.
For configuration information, see Portals > Application Offloading and Adding or Editing User Bookmarks.
By using HTTP(S) bookmarks, users can access the full-featured versions of Sharepoint 2007, Microsoft OWA Premium, and Domino Web Access 8.0.1, 8.5.1, and 8.5.2 Web mail interfaces. These interfaces are easier to use and provide more enhanced features than their basic counterparts.
Benefits of Application Offloading
An offloaded Web application has the following advantages over configuring the Web application as an HTTP(S) bookmark in SRA:
• No URL rewriting is necessary, thereby improving throughput significantly.
• The functionality of the original Web application is retained almost completely, while an HTTP(S) bookmark is a best-effort solution.
• Application offloading extends SRA security features to publicly hosted Web sites.
Application offloading can be used in any of the following scenarios:
• To function as an SSL offloader and add HTTPS support to the offloaded Web application, using SSL acceleration of the SRA appliance.
• In conjunction with the Web Application Firewall subscription service to provide the offloaded Web application continuous protection from malicious Web attacks.
• To add strong or stacked authentication to the offloaded Web application, including Two-factor authentication, One Time Passwords and Client Certificate authentication.
• To control granular access to the offloaded Web application using global, group or user based access policies.
• To support Web applications not currently supported by HTTP/HTTPS bookmarks. Application Offloading does not require URL rewriting, thereby delivering complete application functionality without compromising throughput.
• To authenticate ActiveSync Application Offloading technology, which delivers Web applications using Virtual Hosting and Reverse Proxy. ActiveSync authentication does not require URL rewriting in order to deliver the Web applications seamlessly. As an example, the ActiveSync protocol is used by a mobile phone’s email client to synchronize with an Exchange server, as explained in ActiveSync Authentication.
Appliance Platforms
On SRA 6.0 and higher, Application Offloading and HTTP(S) bookmarks are supported on the following SRA appliances:
• SRA 4600
• SRA 4200
• SRA 1600
• SRA 1200
• SRA Virtual Appliance
HTTP Versions
HTTP(S) bookmarks and application offloading portals support both HTTP/1.0 and HTTP/1.1.
Certain performance optimization features, such as caching, compression, SSL hardware acceleration, HTTP connection persistence, TCP connection multiplexing and transfer-chunk encoding for proxies are automatically enabled depending on the usage.
Applications
Beginning in SRA 6.0, Sharepoint 2010 is supported with application offloading, but not with HTTP(S) bookmarks. The following features have been tested and verified as working well on the indicated browsers:
|
The following Web applications have been tested and verified to work with HTTP(S) bookmarks and as offloaded applications:
• Microsoft Outlook Web Access 2010
Microsoft Outlook Web Access 2007
Microsoft Outlook Web Access 2003
Note In SRA 6.0 and higher, Application Offloading supports authentication for ActiveSync. ActiveSync is a protocol used by a mobile phone’s email client to synchronize with an Exchange server. The Administrator can create an offloading portal and set the application server host to the backend Exchange server. Then, a user can use the new virtual host name in a mobile phone’s email client, and synchronize with the backend Exchange server through the SRA appliance. Before SRA 6.0, users had to disable authentication for ActiveSync offloading portals, because ActiveSync requests are different from requests sent from the browser.
Outlook Web Access is supported on the SRA 4600/4200/1600/1200 and SRA Virtual Appliance platforms.
• Windows Sharepoint 2007
Windows Sharepoint Services 3.0
Windows Sharepoint Services 2.0
The integrated client features of Sharepoint are not supported.
• Lotus Domino Web Access 8.0.1, 8.5.1, and 8.5.2
Domino Web Access is supported on the SRA 4600/4200/1600/1200 and SRA Virtual Appliance platforms.
• Novell Groupwise Web Access 7.0
• ActiveSync with Microsoft Exchange 2010
ActiveSync with Microsoft Exchange 2007
ActiveSync with Microsoft Exchange 2003
Exchange ActiveSync is supported on the following:
• Apple iPhone
• Apple iPad
• Android 2.3.x (Gingerbread), 4.0.x (ICS) and 4.1 (Jelly Bean) based phones
• Windows Mobile 6.5 based phones
• Windows Mobile 6.0 based phones
Authentication Schemes
The following authentication schemes are supported for use with application offloading and HTTP(S) bookmarks:
• Basic – Collects credentials in the form of a username and password.
• NTLM (Microsoft NT LAN Manager) – Provides automatic authentication between Active Directory aware applications.
• Forms-based authentication – Uses a Web form to collect credentials.
The following end-user requirements must be met in order to access the complete set of application offloading and HTTP(S) bookmarks features:
• Internet Explorer 8.0 or newer
• Windows 8.1, Windows 8, Windows 7, Windows XP, or Windows Server 2003 or later
When using application offloading or HTTP(S) bookmarks to access applications for Web-based clients, full feature sets are accessible to users. Application offloading and HTTP(S) bookmarks provide enhanced application support for the following software applications:
• Sharepoint Server 2007
• Sharepoint Server 2010
• Microsoft Outlook Web Access Premium
• Lotus Domino Web Access 8.0.1, 8.5.1, and 8.5.2
Note•: The maximum number of users supported is limited by the number of applications being accessed and the volume of application traffic being sent.
• Feature support varies based on your hardware and installation, see the respective sections for more detailed information about specific application support.
Tip If you are using the correct Web browser and operating system, and a supported application does not work, delete the browser session cookies, close and reopen all instances of your browser, clear the browser cache, and then try again.
Supported Application Deployment Considerations
Be aware of these installation and general feature caveats when using application offloading and HTTP(S) bookmarks with the following software applications:
• Sharepoint
– For features that rely on Windows Sharepoint Services-compatible client programs, application offloading and HTTP(S) bookmarks do not support client integration capabilities on Internet Explorer.
– Only forms-based authentication and basic authentication schemes are supported.
– Single Sign-On is supported only for basic authentication.
– Sharepoint 2010 is supported with application offloading, but not with HTTP(S) bookmarks.
• Microsoft OWA
– S/MIME support and bi-directional layout support for Arabic and Hebrew in Microsoft OWA Premium are only available using Internet Explorer 8 and later. Gzip compression supported by Microsoft OWA Premium is not supported through the reverse proxy.
• Outlook Anywhere
– SRA 4200 only with Application Offloading.
– Outlook Anywhere uses Microsoft’s MS-RPCH proprietary protocol, which may conflict with normal HTTP(S) protocol.
– Use the Generic SSL Offloading instead of HTTP or HTTPS.
Application Offloading should support any application using HTTP/HTTPS. SRA has limited support for applications using Web services and no support for non-HTTP protocols wrapped within HTTP.
The application should not contain hard-coded self-referencing URLs. If these are present, the Application Offloading proxy must rewrite the URLs. Since Web site development does not usually conform to HTML standards, the proxy can only do a best-effort translation when rewriting these URLs. Specifying hard-coded, self-referencing URLs is not recommended when developing a Web site because content developers must modify the Web pages whenever the hosting server is moved to a different IP or hostname.s
For example, if the backend application has a hard-coded IP address and scheme within URLs as follows, Application Offloading must rewrite the URL.
: <a href="http://1.1.1.1/doAction.cgi?test=foo">
This can be done by enabling the Enable URL Rewriting for self-referenced URLs setting for the Application Offloading Portal, but all the URLs may not be rewritten, depending on how the Web application has been developed. (This limitation is usually the same for other WAF/SRA vendors employing reverse proxy mode.)
External Website Bookmarks can be created for application offloading portals to achieve a single point of access for users. This allows users to automatically log into application offloading portals after logging into the main portal.
To use Cross Domain Single Sign-on (SSO), perform the following steps:
1. Create two or more portals with the same shared domain (from Virtual Host Domain name) and that need authentication. One portal should be a regular portal. These portals are also in the same SRA appliance’s domain so that a user can log in to both of them with the same credentials. Adding Portals explains how to create a portal.
2. Log into the portal and create a bookmark, as explained in Adding or Editing User Bookmarks.
3. Set the service to External Web Site, as explained in External Web Site.
4. Enable Automatically log in for the bookmark, which enables Cross Domain SSO for this bookmark.
5. Specify a Host, which is a portal with the same shared domain name.
6. Save the bookmark and launch it. The new portal is logged in automatically without any credential.
The shared domain names don’t need to be identical; a sub-domain also works. For example, one portal is a regular portal whose virtual host domain name is “www.example.com” and its shared domain name is “.example.com”. The other portal’s virtual host domain name is “intranet.eng.example.com” and the shared domain name is “.eng.example.com”. If a bookmark to xyz.eng.example.com is created in the www.example.com portal, Cross Domain SSO works because “.eng.example.com” is a sub-domain of “.example.com”.
Application Offloading now supports authentication for ActiveSync. Application Offloading technology delivers Web applications using Virtual Hosting and Reverse Proxy. Users still need to authenticate with the SRA appliance before accessing the backend Web application. However, the proxy avoids URL rewriting in order to deliver the Web applications seamlessly.
ActiveSync is a protocol used by a mobile phone’s email client to synchronize with an Exchange server. The Administrator can create an offloading portal and set the application server host to the backend Exchange server. Then, a user can use the new virtual host name in a mobile phone’s email client, and synchronize with the backend Exchange server through the SRA appliance. Before SRA 6.0, users had to disable authentication for ActiveSync offloading portals, because ActiveSync requests are different from requests sent from the browser.
Note On iPhones/iPads running versions earlier than iOS 6.1.2, initial account synchronization may fail if a calendar contains a recurring invite.
ActiveSync is managed through the Portals > Offload Web Application > Offloading > Security Settings page:
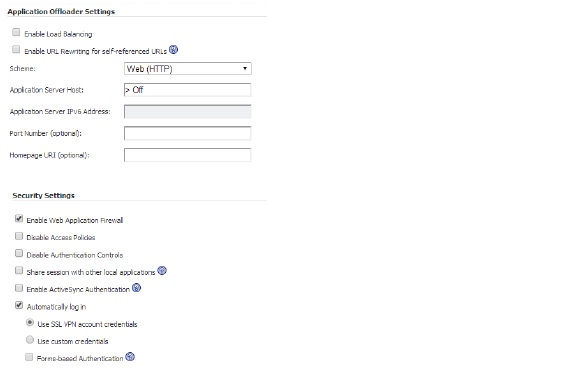
To configure ActiveSync authentication, clear the Disable Authentication Controls check box to display the authentication fields. Select the Enable ActiveSync authentication check box and then type the default domain name. The default domain name will not be used when the domain name is set in the email client’s setting.
ActiveSync Log Entries
The Log > View page is updated when a Web application is offloaded. Most mobile systems (iPhone, Android, Windows Mobile, etc.) support ActiveSync. These log entries identify when the client began to use ActiveSync through the offloading portal. The ActiveSync message identifies the device ID (ActiveSync: Device Id is…) for an ActiveSync request unless a client sets up the account and the request does not contain a device ID. The ActiveSync label is not used in log entries for anonymous users who use ActiveSync.
Note A user’s credential in the Exchange server must be the same as the one in the SRA. Many authentication types are available for each domain in the SRA. If using the Local User Database, make sure the user name and password is the same as the one for the Exchange server. Fortunately, other authentication types like Active Directory can share credentials for both the Exchange server and SRA appliance. However, authentication using authentication types that share credentials may take longer and the first ActiveSync request may time out. Once authentication succeeds, a session is created and other requests won’t need to be authenticated again.
Configuring a Portal to Check Email From an Android Device
The following example shows how to set up ActiveSync to check emails from an Android device. Be sure to replace entries shown in the examples with entries for your environment, and be careful to input the correct password. Otherwise, the account will be blocked.
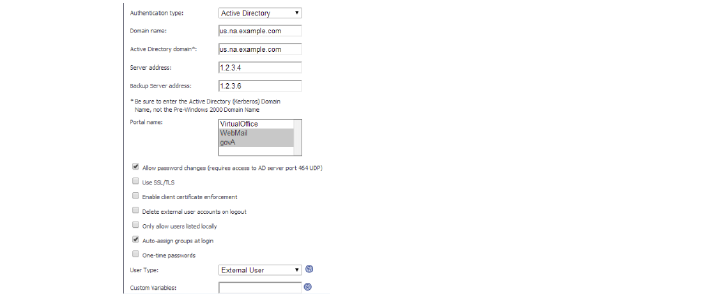
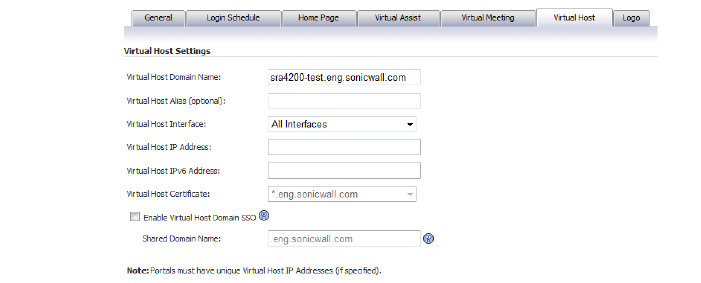
1. Create a Domain name of webmail.example.com. Set the Active Directory domain and Server address to webmail.example.com. Set the Portal name to webmail.
2. In the SRA appliance, create an offloading portal with the name webmail.
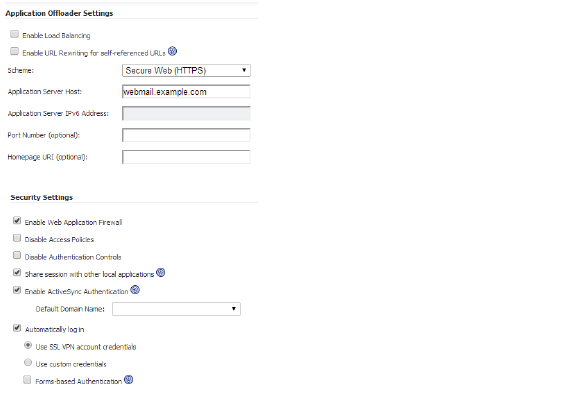
3. Set the Scheme to Secure Web (HTTPS).
4. Set the Application Server Host to your Exchange server, for example webmail.example.com.
5. Set the virtual host name, for example, webmail.example.com. The virtual host name should be resolved by the DNS server. Otherwise, modify the hosts file in the Android phone.
6. Select the Enable ActiveSync Authentication check box. Leave the default domain name blank or input webmail.example.com.
7. Turn on the Android phone, open the Email application, and type your email address and password. Click Next.
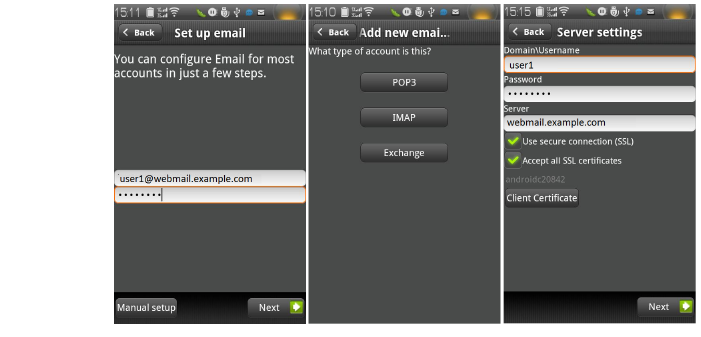
8. Choose Exchange.
9. Input your Domain\Username, Password, and Server. No domain name is displayed, so use the default domain name specified in the offloading portal’s setting. Select Accept all SSL certificates and click Next.
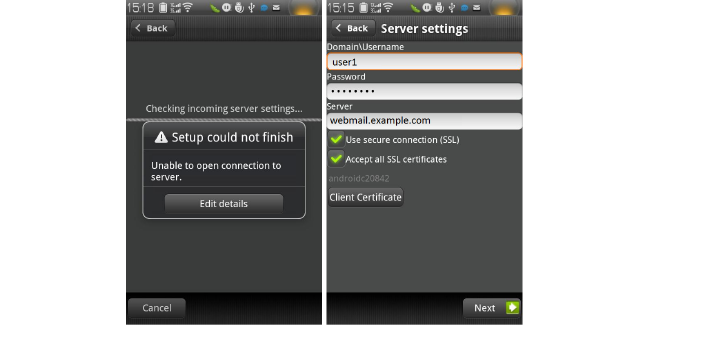
10. If the AD authentication times out, the Setup could not finish message is displayed. Wait about 20 seconds and try again. You can also check the SRA log to see if the user logged in successfully. You may not encounter this problem if the AD authentication is fast.
11. When the authentication finishes, a security warning appears. Click OK to continue, modify your account settings, and click Next.
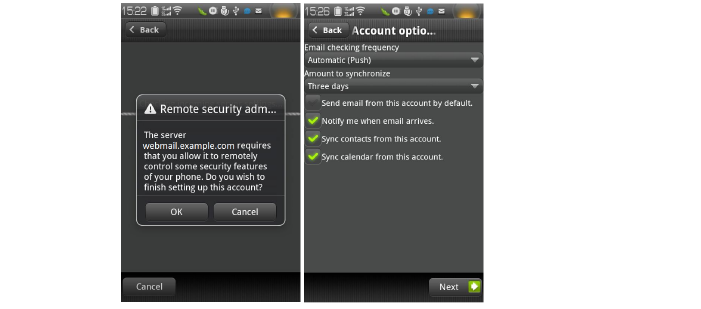
12. Try to send and receive emails, and ensure that ActiveSync entries are included in the SRA log.
Network Resources are the granular components of a trusted network that can be accessed using the SRA appliance. Network Resources can be pre-defined by the administrator and assigned to users or groups as bookmarks, or users can define and bookmark their own Network Resources.
The following sections describe types of network resources supported by the SRA appliance:
• HTTP (Web) and Secure HTTPS (Web)
• Remote Desktop Protocols and Virtual Network Computing
• Application Protocols Using RDP
• Microsoft Outlook Web Access
HTTP (Web) and Secure HTTPS (Web)
The SRA appliance provides proxy access to an HTTP or HTTPS server on the internal network, Internet, or any other network segment that can be reached by the appliance. The remote user communicates with the SRA appliance using HTTPS and requests a URL. The URL is then retrieved over HTTP by the SRA appliance. The URL is transformed as needed, and returned encrypted to the remote user.
The SRA administrator can configure Web (HTTP) or Secure Web (HTTPS) bookmarks to allow user access to Web-based resources and applications such as Microsoft OWA Premium, Windows Sharepoint 2007, Novell Groupwise Web Access 7.0, or Domino Web Access 8.0.1, 8.5.1, and 8.5.2 with HTTP(S) reverse proxy support. Reverse-proxy bookmarks also support the HTTP 1.1 protocol and connection persistence.
HTTPS bookmarks on SRA 4600/4200 appliances support keys of up to 2048 bits.
HTTP(S) caching is supported on the SRA appliance for use when it is acting as a proxy Web server deployed between a remote user and a local Web server. The proxy is allowed to cache HTTP(S) content on the SRA appliance which the internal Web server deems cacheable based on the HTTP(S) protocol specifications. For subsequent requests, the cached content is returned only after ensuring that the user is authenticated with the SRA appliance and is cleared for access by the access policies. However, SRA optimizes traffic to the backend Web server by using TCP connection multiplexing, where a single TCP connection is used for multiple user sessions to the same web server. Caching is predominantly used for static Web content like JavaScript files, style sheets, and images. The proxy can parse HTML/JavaScript/CSS documents of indefinite length. The administrator can enable or disable caching, flush cached content and set the maximum size for the cache.
Content received by the SRA appliance from the local Web server is compressed using gzip before sending it over the Internet to the remote client. Compressing content sent from the appliance saves bandwidth and results in higher throughput. Furthermore, only compressed content is cached, saving nearly 40-50% of the required memory. Note that gzip compression is not available on the local (clear text side) of the SRA appliance, or for HTTPS requests from the remote client.
A Java-based Telnet client is delivered through the remote user’s Web browser. The remote user can specify the IP address of any accessible Telnet server and the SRA appliance will make a connection to the server. Communication between the user over SSL and the server is proxied using native Telnet. The Telnet applet supports MS JVM (Microsoft Java Virtual Machine) in Internet Explorer, and requires Sun Java Runtime Environment (JRE) 1.1 or higher for other browsers.
Java-based SSH clients delivered through the remote user’s Web browser. The remote user can specify the IP address of any accessible SSH server and the SRA appliance will make a connection to the server. Communication between the user over SSL and the server is proxied using natively encrypted SSH. The SSHv1 applet supports MS JVM in Internet Explorer, and requires SUN JRE 1.1 for other browsers. SSHv2 provides stronger encryption and has other advanced features, and can only connect to a server that supports SSHv2. SSHv2 support sets the terminal type to VT100. SSHv2 requires JRE 1.6.0_10 or higher, available from http://java.sun.com.
Proxy access to an FTP server on the internal network, the Internet, or any other network segment that can be reached by the SRA appliance. The remote user communicates with the SRA appliance by HTTPS and requests a URL that is retrieved over HTTP by the SRA appliance, transformed as needed, and returned encrypted to the remote user. FTP supports 25 character sets, including four Japanese sets, two Chinese sets, and two Korean sets. The client browser and operating system must support the desired character set, and language packs may be required.
File Shares provide remote users with a secure Web interface to Microsoft File Shares using the CIFS (Common Internet File System) or the older SMB (Server Message Block) protocols. Using a Web interface similar in style to Microsoft’s familiar Network Neighborhood or My Network Places, File Shares allow users with appropriate permissions to browse network shares, rename, delete, retrieve, and upload files, and to create bookmarks for later recall. File shares can be configured to allow restricted server path access.
Remote Desktop Protocols and Virtual Network Computing
RDP Java and VNC are supported on Windows, Linux, and Mac operating systems, while RDP ActiveX is supported only on Windows. Most Microsoft workstations and servers have RDP server capabilities that can be enabled for remote access, and there are a number of freely available VNC servers that can be downloaded and installed on most operating systems. The RDP and VNC clients are automatically delivered to authorized remote users through their Web browser in the following formats:
• RDP Java – RDP Java is a Microsoft Remote Desktop Protocol that has the advantage of broad platform compatibility because it is provided in a Java client. The RDP Java client runs on Windows, Linux, and Mac computers, and supports full-screen mode. On Windows clients, SRA appliances support many advanced options. On Mac OS X 10.5 or above, RDP Java supports the Mac native RDC client.
• RDP ActiveX - RDP ActiveX is also a Microsoft Remote Desktop Protocol. The RDP ActiveX client only runs on Windows, and is not supported on Mac or Linux computers. Four advanced options are supported by SRA appliances for RDP ActiveX.
• VNC (Java) - VNC was originally developed by AT&T, but is today widely available as open source software. Any one of the many variants of VNC servers available can be installed on most any workstation or server for remote access. The VNC client to connect to those servers is delivered to remote users through the Web browser as a Java client.
RDP 6 Support
The SRA appliance supports connections with RDP 6 clients, and supports the RDP 5 feature set plus four RDP 6 features.
The SRA appliance supports connections with RDP 6.1 clients. RDC 6.1 is included with the following operating systems:
• Windows 7
• Windows Server 2008
• Windows Vista Service Pack 1 (SP1)
• Windows XP Service Pack 3 (SP3)
RDC 6.1 incorporates the following functionality in Windows Server 2008:
• Terminal Services RemoteApp
• Terminal Services EasyPrint driver
• Single Sign-On
For more information, see Adding or Editing User Bookmarks.
Note RDP 6 and RDP 7 end client systems must have the client installed on their system. The SRA appliance does not provision the mstsc client and utilizes the locally installed client for those connections.
RDP 7 Support
The SRA appliance supports connections with RDP 7 clients and supports the RDP 7 feature set. RDC 7 is available on following operating systems:
• Windows 8
• Windows 8.1
• Windows 7
• Windows Vista SP2
• Windows Vista SP1
• Windows XP SP3
Application Protocols Using RDP
Applications protocols are RDP sessions that provide access to a specific application rather than to an entire desktop. This allows defined access to an individual application, such as CRM or accounting software. When the application is closed, the session closes. The following RDP formats can be used as applications protocols:
RDP Java – Uses the Java-based RDP client to connect to the terminal server, and to automatically invoke an application at the specified path (for example, C:\programfiles\microsoft office\office11\winword.exe)
RDP ActiveX – Uses the ActiveX-based RDP client to connect to the terminal server, and to automatically invoke an application at the specified path (for example, C:\programfiles\wireshark\wireshark.exe).
Application Support for SSO, User Policies, Bookmarks
The following table provides a list of application-specific support for Single Sign-On (SSO), global/group/user policies, and bookmark Single Sign-On control policies.
|
Application Support
Beginning with version 5.5, SRA includes reverse proxy application support for all versions of OWA 2010, 2007, and 2003.
Microsoft OWA Premium mode is a Web client for Microsoft Outlook 2003/2007/2010 that simulates the Microsoft Outlook interface and provides more features than basic OWA. Microsoft OWA Premium includes features such as spell check, creation and modification of server-side rules, Web beacon blocking, support for tasks, auto-signature support, and address book enhancements. SRA HTTP(S) reverse proxy supports Microsoft OWA Premium.
Microsoft OWA Premium includes the following features:
• Access to email, calendar, and tasks
• New Outlook look-and-feel, including right-click functionality
• Ability to mark an email as unread
• Server-side spelling checker (limited to six languages)
• Forms-based authentication (session time-out)
• S/MIME support
Note S/MIME support for Microsoft OWA Premium is only available on Internet Explorer 8 or higher.
• Two-line view
• Context menus
• Improved keyboard shortcuts
• Ability to forward meeting requests
• Notifications on navigation pane
• Ability to add to contacts
• Ability to pick names from address book
• Ability to set maximum number of messages displayed in views
• Support for bi-directional layout for Arabic and Hebrew
Note Bi-directional layout support for Arabic and Hebrew for Microsoft OWA Premium is only available on Internet Explorer or higher.
• Option to set message status “mark as read” when using the reading pane
• Public folders display in their own browser window
• Access to GAL property sheets within an email message or meeting request
• Message sensitivity settings on information bar
• Attendee reminder option for meeting request
• Ability to launch the calendar in its own window
• User interface to set common server-side rules
• Outlook style Quick Flags
• Support for message signatures
• Search folders (must be created in Outlook online mode)
• Deferred search for new messages after delete
• Attachment blocking
• Web beacon blocking to make it more difficult for senders of spam to confirm email addresses
• Protection of private information when a user clicks a hyperlink in the body of an email message
The SRA reverse proxy application support for Windows Sharepoint 2007, Windows Sharepoint Services 3.0, and Windows Sharepoint Services 2.0 includes the following features:
• Site Templates
• Wiki Sites
• Blogs
• RSS Feeds
• Project Manager
• Mobile Access to Content
• My Site
• Search Center
• Document Center
• Document Translation Management
• Web Content Management
• Workflows
• Report Center
For features that rely on Windows Sharepoint Services-compatible client programs, SRA 5.5 Reverse Proxy does not support the client integration capabilities of Sharepoint.
Single sign-on is supported only for basic authentication.
Only forms-based authentication and basic authentication schemes are supported
The SRA appliance reverse proxy application supports for Domino Web Access 8.0.1, 8.5.1, and 8.5.2 includes the following features:
| ||||||||||||||||||||||||||||||||||||
Citrix is a remote access, application sharing service, similar to RDP. It enables users to remotely access files and applications on a central computer over a secure connection. The Citrix applet requires SUN JRE 1.6.0_10 or higher.
The Citrix Receiver clients for ActiveX and Java are supported, as well as the earlier XenApp and ICA clients. In previous versions of Citrix, the Citrix ICA Client was renamed as the Citrix XenApp plugin.
SRA appliances support client computers running the Citrix “Receiver for Windows 3.0” ActiveX client, the Citrix “Receiver for Java 10.1” Java client, Citrix XenApp plugin version 12.0.3 or earlier (including earlier versions of ICA Client) and Citrix Java client version 10.0 or earlier. The minimum working version of the Citrix ICA Client for Vista is 10.0.
SonicOS SRA 5.5 and higher supports Citrix XenApp Server 6.5, XenApp Server 6.0, XenApp Server 5.0, and XenApp Server 4.5.
SRA appliances running SRA 5.0 or higher support Simple Network Management Protocol (SNMP), which will report remote access statistics. SNMP support facilitates network management for administrators, allowing them to leverage standardized reporting tools.
The administrator can configure DNS on the SRA appliance to enable it to resolve host names with IP addresses. The SRA Web-based management interface allows the administrator to configure a hostname, DNS server addresses, and WINS server addresses.
Configuring a default network route allows your SRA appliance to reach remote IP networks through the designated default gateway. The gateway will typically be the upstream firewall to which the SRA appliance is connected. In addition to default routes, it also possible to configure specific static routes to hosts and networks as a preferred path, rather than using the default gateway.
This section provides an overview to the NetExtender feature. This section contains the following subsections:
• Benefits
Dell SonicWALL NetExtender is a transparent software application for Windows, Mac, and Linux users that enables remote users to securely connect to the remote network. With NetExtender, remote users can securely run any application on the remote network. Users can upload and download files, mount network drives, and access resources as if they were on the local network. The NetExtender connection uses a Point-to-Point Protocol (PPP) connection.
In SRA 5.5 and higher, NetExtender capabilities include the Dell SonicWALL Mobile Connect app for Apple iPhone, iPad, and iPod Touch. Mobile Connect enables secure, mobile connections to private networks protected by Dell SonicWALL security appliances. For information about installing and using Dell SonicWALL Mobile Connect, see the Dell SonicWALL Mobile Connect User’s Guide.
NetExtender provides remote users with full access to your protected internal network. The experience is virtually identical to that of using a traditional IPSec VPN client, but NetExtender does not require any manual client installation. Instead, the NetExtender Windows client is automatically installed on a remote user’s PC by an ActiveX control when using the Internet Explorer browser, or with the XPCOM plugin when using Firefox. On Linux or MacOS systems, supported browsers use Java controls to automatically install NetExtender from the Virtual Office portal.
The NetExtender Windows client also has a custom-dialer that allows it to be launched from the Windows Network Connections menu. This custom-dialer allows NetExtender to be connected before the Windows domain login. The NetExtender Windows client also supports a single active connection, and displays real-time throughput and data compression ratios in the client.
After installation, NetExtender automatically launches and connects a virtual adapter for SSL-secure NetExtender point-to-point access to permitted hosts and subnets on the internal network.
The following sections describe advanced NetExtender concepts:
• NetExtender with External Authentication Methods
• Point to Point Server IP Address
SRA appliances provide a stand-alone NetExtender application. NetExtender is a browser-installed lightweight application that provides comprehensive remote access without requiring users to manually download and install the application. The first time a user launches NetExtender, the NetExtender stand-alone client is automatically installed on the user’s PC or Mac. The installer creates a profile based on the user’s login information. The installer window then closes and automatically launches NetExtender. If the user has a legacy version of NetExtender installed, the installer will first uninstall the old NetExtender and install the new version.
Once the NetExtender stand-alone client has been installed, Windows users can launch NetExtender from their PC’s Start > Programs menu and configure NetExtender to launch when Windows boots.
NetExtender can establish a VPN session before the user logs into the Windows domain. Users with Windows XP or earlier versions can click the Logon using dial-up connection on the Windows login screen and select NetExtender from the list of dialup connections. For Windows Vista or later, users can click Switch User on the Windows login screen and click the blue computer icon that appears at the right bottom of the screen to view the dialup connection list, and then can select NetExtender to connect.
Mac users can launch NetExtender from their system Applications folder, or drag the icon to the dock for quick access. On Linux systems, the installer creates a desktop shortcut in
/usr/share/NetExtender. This can be dragged to the shortcut bar in environments like Gnome and KDE.
NetExtender is compatible with the following Dell SonicWALL appliances:
• SRA 4600/1600
• SRA 4200/1200
• SRA Virtual Appliance
• NSA and TZ series (with SRA license)
NetExtender is also backward compatible with older SSL-VPN 2000/4000 appliances for connectivity.
NetExtender is officially supported on the following client platforms:
• Fedora 14+
• Ubuntu 11.04+
• OpenSUSE 10.3+
• Mac OS X 10.6.8+
• Android 1.6+ (rooting required)
• Windows Mobile 7.5, 7.8, and 8.0
• Windows 8.1, Windows 8, Windows XP, Windows 7, Windows Server 2003, Windows Server 2008 R2.
NetExtender may work properly on other Linux distributions, but they are not officially supported by Dell SonicWALL.
Note The Mobile Connect application is now available for iOS 4.3 or higher and Android 4.0 or higher.
Multiple range and route support for NetExtender on SRA appliances enables network administrators to easily segment groups and users without the need to configure firewall rules to govern access. This user segmentation allows for granular control of access to the network—allowing users access to necessary resources while restricting access to sensitive resources to only those who require it.
For networks that do not require segmentation, client addresses and routes can be configured globally as in the SRA 1.0 version of NetExtender. The following sections describe the new multiple range and route enhancements:
• IP Address User Segmentation
Administrators can configure separate NetExtender IP address ranges for users and groups. These settings are configured on the Users > Local Users and Users > Local Groups pages, using the NetExtender tab in the Edit User and Edit Group windows.
When configuring multiple user and group NetExtender IP address ranges, it is important to know how the SRA appliance assigns IP addresses. When assigning an IP address to a NetExtender client, the SRA appliance uses the following hierarchy of ranges:
1. An IP address from the range defined in the user’s local profile.
2. An IP address from the range defined in the group profile to which the user belongs.
3. An IP address from the global NetExtender range.
To reserve a single IP address for an individual user, the administrator can enter the same IP address in both the Client Address Range Begin and Client Address Range End fields on the NetExtender tab of the Edit Group window.
NetExtender client routes are used to allow and deny access to various network resources. Client routes can also be configured at the user and group level. NetExtender client routes are also configured on the Edit User and Edit Group windows. The segmentation of client routes is fully customizable, allowing the administrator to specify any possible permutation of user, group, and global routes (such as only group routes, only user routes, group and global routes, user, group, and global routes, etc.). This segmentation is controlled by the Add Global NetExtender Client routes and Add Group NetExtender Client routes check boxes.
NetExtender with External Authentication Methods
Networks that use an external authentication server will not configure local usernames on the SRA appliance. In such cases, when a user is successfully authenticated, a local user account is created if the Add Global NetExtender Client routes and Add Group NetExtender Client routes settings are enabled.
Point to Point Server IP Address
In SRA, the PPP server IP address is 192.0.2.1 for all connecting clients. This IP address is transparent to both the remote users connecting to the internal network and to the internal network hosts communicating with remote NetExtender clients. Because the PPP server IP address is independent from the NetExtender address pool, all IP addresses in the global NetExtender address pool will be used for NetExtender clients.
SRA appliances provide users with the ability to run batch file scripts when NetExtender connects and disconnects. The scripts can be used to map or disconnect network drives and printers, launch applications, or open files or Web sites. NetExtender Connection Scripts can support any valid batch file commands.
Tunnel All mode routes all traffic to and from the remote user over the SRA NetExtender tunnel—including traffic destined for the remote user’s local network. This is accomplished by adding the following routes to the remote client’s route table:
|
NetExtender also adds routes for the local networks of all connected Network Connections. These routes are configured with higher metrics than any existing routes to force traffic destined for the local network over the SRA tunnel instead. For example, if a remote user is has the IP address 10.0.67.64 on the 10.0.*.* network, the route 10.0.0.0/255.255.0.0 is added to route traffic through the SRA tunnel.
Tunnel All mode can be configured at the global, group, and user levels.
SRA appliances support NetExtender sessions using proxy configurations. Currently, only HTTPS proxy is supported. When launching NetExtender from the Web portal, if your browser is already configured for proxy access, NetExtender automatically inherits the proxy settings. The proxy settings can also be manually configured in the NetExtender client preferences. NetExtender can automatically detect proxy settings for proxy servers that support the Web Proxy Auto Discovery (WPAD) Protocol.
NetExtender provides three options for configuring proxy settings:
• Automatically detect settings - To use this setting, the proxy server must support Web Proxy Auto Discovery Protocol (WPAD)), which can push the proxy settings script to the client automatically.
• Use automatic configuration script - If you know the location of the proxy settings script, you can select this option and provide the URL of the script.
• Use proxy server - You can use this option to specify the IP address and port of the proxy server. Optionally, you can enter an IP address or domain in the BypassProxy field to allow direct connections to those addresses and bypass the proxy server. If required, you can enter a user name and password for the proxy server. If the proxy server requires a username and password, but you do not specify them, a NetExtender pop-up window will prompt you to enter them when you first connect.
When NetExtender connects using proxy settings, it establishes an HTTPS connection to the proxy server instead of connecting to the SRA server directly. The proxy server then forwards traffic to the SRA server. All traffic is encrypted by SSL with the certificate negotiated by NetExtender, of which the proxy server has no knowledge. The connecting process is identical for proxy and non-proxy users.
Two-Factor Authentication Overview
Two-factor authentication is an authentication method that requires two independent pieces of information to establish identity and privileges. Two-factor authentication is stronger and more rigorous than traditional password authentication that only requires one factor (the user’s password).
Dell SonicWALL’s implementation of two-factor authentication partners with two of the leaders in advanced user authentication: RSA and VASCO.
Beginning in SRA 5.5, two RADIUS servers can be used for two-factor authentication, allowing users to be authenticated through the Web portal or with an SRA client such as NetExtender or Secure Virtual Assist.
Note Single sign-on (SSO) in SRA appliances do not support two-factor authentication.
See the following sections:
• Benefits of Two-Factor Authentication
• How Does Two-Factor Authentication Work?
• Supported Two-Factor Authentication Providers
Benefits of Two-Factor Authentication
Two-factor authentication offers the following benefits:
• Greatly enhances security by requiring two independent pieces of information for authentication.
• Reduces the risk posed by weak user passwords that are easily cracked.
• Minimizes the time administrators spend training and supporting users by providing a strong authentication process that is simple, intuitive, and automated.
How Does Two-Factor Authentication Work?
Two-factor authentication requires the use of a third-party authentication service, or two separate RADIUS authentication servers.
With two-factor authentication, users must enter a valid temporary passcode to gain access. A passcode consists of the following:
• The user’s personal identification number (PIN)
• A temporary token code or password
When two RADIUS servers are used, the second stage PIN or password can be sent to the user via SMS or email. NetExtender login and Secure Virtual Assist both provide extra challenge(s) for entering it.
When a third-party authentication service is used, it consists of two components:
• An authentication server on which the administrator configures user names, assigns tokens, and manages authentication-related tasks.
• Physical tokens that the administrator gives to users which display temporary token codes.
Users receive the temporary token codes from their RSA or VASCO token cards. The token cards display a new temporary token code every minute. When the RSA or VASCO server authenticates the user, it verifies that the token code timestamp is current. If the PIN is correct and the token code is correct and current, the user is authenticated.
Because user authentication requires these two factors, the dual RADIUS servers solution, the RSA SecureID solution, and the VASCO DIGIPASS solution offers stronger security than traditional passwords (single-factor authentication).
Supported Two-Factor Authentication Providers
RSA
RSA is an algorithm for public-key cryptography. RSA utilizes RSA SecurID tokens to authenticate through an RSA Authentication Manager server. RSA is not supported on all hardware platforms and is supported via RADIUS only.
VASCO
VASCO is a public company that provides user authentication products. VASCO utilizes Digipass tokens to authenticate through a VASCO IdentiKey server. VASCO is supported on all SRA platforms.
VASCO Data Security delivers reliable authentication through the use of One Time Password technology. VASCO IdentiKey combined with Dell SonicWALL SRA and firewall VPN appliances creates an open-market approach delivered through VASCO IdentiKey technology.
VASCO IdentiKey allows users to utilize the VASCO DIGIPASS concept that uses One Time Passwords that are assigned for time segments that provide easy and secure SRA remote access. The One Time Password within the authentication request is verified on the VASCO IdentiKey. After verification, a RADIUS access-accept message is sent to the SRA server for authentication.
Two-Factor Authentication Login Processes
This section provides examples of the two-factor authentication login prompts when using Web login and NetExtender.
With Web login, the Username and Password fields are used to enter the first-stage credentials.
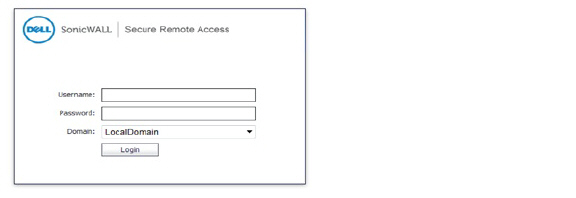
When prompting the user to input the challenge code, the message “Please enter the M.ID PIN:” is the reply message from the RADIUS server in this example; different RADIUS servers may have different reply message formats.

Some RADIUS servers may require the user to respond to several challenges to complete the authentication. In this example, the M.ID server asks the user to supply two challenges. The following passcode can be received through email or cellphone (if SMS is configured).
When using two-factor authentication with the NetExtender Windows client, the login process through the client is very similar to logging in through the Web page. Initially, the Username and Password fields are used to enter the first-stage credentials.
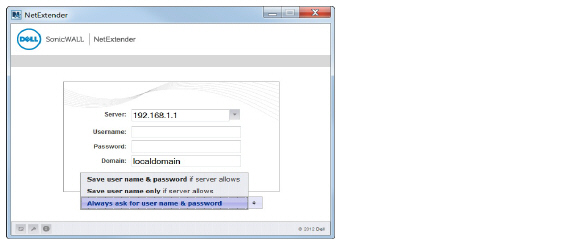
This is followed by the PIN challenge.

Last, the Passcode challenge is displayed.

This section provides an introduction to the One Time Password feature. This section contains the following topics:
• Benefits of One Time Passwords
• How Does the SRA One Time Password Feature Work?
• Configuring One Time Passwords for SMS-Capable Phones
• Verifying Administrator One Time Password Configuration
The SRA One Time Password feature adds a second layer of login security to the standard username and password. A one-time password is a randomly generated, single-use password. The SRA One Time Password feature is a two-factor authentication scheme that utilizes one-time passwords in addition to standard user name and password credentials, providing additional security for Dell SonicWALL SRA users.
The SRA One Time Password feature requires users to first submit the correct SRA login credentials. After following the standard login procedure, the SRA generates a one-time password, which is sent to the user at a pre-defined email address. The user must login to that email account to retrieve the one-time password and type it into the SRA login screen when prompted, before the one-time password expires.
Benefits of One Time Passwords
The SRA One Time Password feature provides more security than single, static passwords alone. Using a one-time password in addition to regular login credentials effectively adds a second layer of authentication. Users must be able to access the email address defined by the SRA administrator before completing the SRA One Time Password login process. Each one-time password is single-use and expires after a set time period, requiring that a new one-time password be generated after each successful login, cancelled or failed login attempt, or login attempt that has timed out, thus reducing the likelihood of a one-time password being compromised.
How Does the SRA One Time Password Feature Work?
The SRA administrator can enable the One Time Password feature on a per-user or per-domain basis. To enable the One Time Password feature on a per-user basis, the administrator must edit the user settings in the SRA management interface. The administrator must also enter an external email address for each user who is enabled for One Time Passwords. For users of Active Directory and LDAP, the administrator can enable the One Time Password feature on a per-domain basis.
Enabling the One Time Password feature on a per-domain basis overrides individual “enabled” or “disabled” One Time Password settings. Enabling the One Time Password feature for domains does not override manually entered email addresses, which take precedence over those auto-configured by a domain policy and over AD/LDAP settings.
In order to use the SRA One Time Password feature, the administrator must configure valid mail server settings in the Log > Settings page of the SRA management interface. The administrator can configure the One Time Password feature on a per-user or per-domain basis, and can configure timeout policies for users.
If the email addresses to which you want to deliver your SRA One Time Passwords are in an external domain (such as SMS addresses or external webmail addresses), you will need to configure your SMTP server to allow relaying from the SRA appliance to the external domain.
For information about how to configure Microsoft Exchange to support SRA One Time Password, see the Dell SonicWALL SRA One Time Password Feature Module, available online at:
http://www.sonicwall.com/us/Support.html
For users enabled for the One Time Password feature either on a per-user or per-domain basis, the login process begins with entering standard user name and password credentials in the SRA interface. After login, users receive a message that a temporary password will be sent to a pre-defined email account. The user must login to the external email account and retrieve the one-time password, then type or paste it into the appropriate field in the SRA login interface. Any user requests prior to entering the correct one-time password will re-direct the user to the login page.
The one-time password is automatically deleted after a successful login and can also be deleted by the user by clicking the Cancel button in the SRA interface, or will be automatically deleted if the user fails to login within that user’s timeout policy period.
Configuring One Time Passwords for SMS-Capable Phones
SRA One Time Passwords can be configured to be sent via email directly to SMS-capable phones. Contact your cell phone service provider for further information about enabling SMS (Short Message Service).
Below is a list of SMS email formats for selected major carriers, where 4085551212 represents a 10-digit telephone number and area code.
• Verizon: 4085551212@vtext.com
• Sprint: 4085551212@messaging.sprintpcs.com
• AT&T PCS: 4085551212@text.att.net
• Cingular: 4085551212@mobile.mycingular.com
• T-Mobile: 4085551212@tmomail.net
• Nextel: 4085551212@messaging.nextel.com
• Virgin Mobile: 4085551212@vmobl.com
• Qwest: 4085551212@qwestmp.com
These SMS email formats are for reference only. These email formats are subject to change and may vary. You may need additional service or information from your provider before using SMS. Contact the SMS provider directly to verify these formats and for further information on SMS services, options, and capabilities.
To configure the SRA appliance to send one-time passwords to an SMS email address, follow the procedure described in Editing User Settings, and enter the user’s SMS address in the E-mail address field.
Verifying Administrator One Time Password Configuration
To verify that an individual user account has been enabled to use the One Time Password feature, login to the SRA Virtual Office user interface using the credentials for that account.
If you are able to successfully login to Virtual Office, you have correctly used the One Time Password feature.
If you cannot login using One Time Password, verify the following:
• Are you able to login without being prompted to check your email for One-time Password? The user account has not been enabled to use the One-time Password feature.
• Is the email address correct? If the email address for the user account has been entered incorrectly, login to the management interface to correct the email address.
• Is there no email with a one-time password? Wait a few minutes and refresh your email inbox. Check your spam filter. If there is no email after several minutes, try to login again to generate a new one-time password.
• Have you accurately typed the one-time password in the correct field? Re-type or copy and paste the one-time password within the time allotted by the user’s timeout policy as set in the Log > Settings page.
This section provides an introduction to the End Point Control feature. This section contains the following topics:
• Benefits of End Point Control
• How Does End Point Control Work?
• Configuring End Point Control
In traditional VPN solutions, accessing your network from an untrusted site like an employee-owned computer or a kiosk at an airport or hotel increases the risk to your network resources. The SRA appliance includesprovides secure access from any Web-enabled system, including devices in untrusted environments.
The SRA appliance supports End Point Control (EPC), which provides the following benefits:
• Verifies that the user’s environment is secure before establishing a connection.
• Protects sensitive data and
• Ensures that your network is not compromised when accessed from devices in untrusted environments.
• Protects the network from threats originating from client devices participating in the SRA.
How Does End Point Control Work?
The SRA appliance provides end point security controls by performing host integrity checking and security protection mechanisms before a tunnel session is begun. Host integrity checks help ensure that the client system is in compliance with your organization’s security policy. SonicWALL end point security controls are tightly integrated with access control to analyze the Windows client system and apply access controls based on the results.
End Point Control is supported on iOS and Android mobile devices using Mobile Connect, allowing device profiles to be created for these mobile devices. This provides security protection from threats against client devices and protection to the SSL VPN from threats originating from client devices participating in the SSL VPN. For more information on Mobile Connect, refer to the Mobile Connect User Guides.
Perform the following tasks to configure EPC:
1. Image the appliance with 7.5 firmware, as explained in the Dell SonicWALL SRA Getting Started Guide.
2. Configure Device Profiles that allow or deny user authentication based on various global, group, or user attributes. See End Point Control > Device Profiles.
3. Add and configure groups and users to allow or deny End Point Control profiles. See Edit EPC Settings.
4. Configure users to inherit their group profiles. See Edit EPC Settings.
5. Enable End Point Control. See End Point Control > Settings.
6. Connect to NetExtender and monitor the End Point Control log. See End Point Control > Log.
Secure Virtual Assist Overview
This section provides an introduction to the Secure Virtual Assist feature. This section contains the following topics:
• What is Secure Virtual Assist?
• Benefits of Secure Virtual Assist
• How Does Secure Virtual Assist Work?
• Launching a Secure Virtual Assist Technician Session
• Performing Secure Virtual Assist Technician Tasks
• Enabling a System for Secure Virtual Access
What is Secure Virtual Assist?
Secure Virtual Assist is an easy to use tool that allows SRA users to remotely support customers by taking control of their computers while the customer observes. Providing support to customers is traditionally a costly and time consuming aspect of business. Secure Virtual Assist creates a simple to deploy, easy to use remote support solution.
Benefits of Secure Virtual Assist
Secure Virtual Assist provides the following benefits:
• Simplified and effective customer support - Support staff can use Secure Virtual Assist to directly access customers computers to troubleshoot and fix problems. This eliminates the need for customers to try to explain their problems and their computer’s behavior over the phone.
• Time and cost savings - Secure Virtual Assist eliminates the need for support staff to visit customers to troubleshoot problems and reduces the average time-to-resolution of support calls.
• Educational tool - Trainers and support staff can use Secure Virtual Assist to remotely show customers how to use programs and tools.
• Seamless integration with existing authentication system - Ensures that the customers are who they say they are. Alternatively, the local database of the SRA appliance and tokenless two-factor authentication can be utilized.
• Secure connections - 256-bit AES SSL encryption of the data by the SRA appliance provides a secure environment for the data and assists in the effort to be compliant with regulations like Sarbanes-Oxley and HIPAA.
• Greater flexibility for remote access - Using the Secure Virtual Access functionality, support staff can access their personal systems located outside the LAN of the SRA appliance.
How Does Secure Virtual Assist Work?
The following sections describe how the Secure Virtual Assist feature works:
Secure Virtual Assist is a lightweight, thin client that installs automatically using Java from the SRA Virtual Office without requiring the installation of any external software. For computers that do not support Java, Secure Virtual Assist can be manually installed by downloading an executable file from the Virtual Office.
For basic screen sharing support, administrative privileges are not required to run Secure Virtual Assist. For full installation of the client, administrative rights may be necessary, but full installation is not necessary to use the service.
When a user requests service as a customer, Secure Virtual Assist should not be run while connected to the system via RDP for Windows 7 and Windows Vista platforms. Secure Virtual Assist runs as a service for proper access to the customer’s system, so correct permissions cannot be set if it is run from an RDP connection.
There are two sides to a Secure Virtual Assist session: the customer view and the technician view. The customer is the person requesting assistance on their computer. The technician is the person providing assistance. A Secure Virtual Assist session consists of the following sequence of events:
1. The technician launches Secure Virtual Assist from the SRA Virtual Office.
2. The technician monitors the Assistance Queue for customers requesting assistance.
3. The customer requests assistance by one of the following methods:
– Logs into the SRA Virtual Office and clicks on the Secure Virtual Assist link.
– Receives an email invitation from the technician and clicks on the link to launch Secure Virtual Assist.
– Navigate directly to the URL of the Secure Virtual Assist home page that is provided by the technician.
4. The Secure Virtual Assist application installs and runs on the customer’s browser.
5. The customer appears in the Secure Virtual Assist Assistance Queue.
6. The technician clicks on the customer’s name and launches a Secure Virtual Assist session.
7. The customer clicks on a warning pop-up window that gives the technician control over the customer’s computer.
8. The technician’s Secure Virtual Assist window now displays the customer’s entire display. The technician has complete control of the customer computer’s mouse and keyboard. The customer sees all of the actions that the technician performs.
9. If at anytime the customer wants to end the session, they can take control and click on the End Virtual Assist button in the bottom right corner of the screen.
10.When the session ends, the customer resumes sole control of the computer.
Secure Virtual Assist includes a Remote File Transfer feature that enables the technician to transfer files directly to and from the customer’s computer. The technician launches the File Transfer process by clicking a button in the Virtual Assist taskbar in the top left corner of the Secure Virtual Assist window. The File Transfer feature supports the upload and download of multiple files.
Secure Virtual Assist includes a chat feature that allows the technician and customer to communicate using an instant message-style chat function. Either the technician or the customer can initiate a chat session by clicking on the Chat button in the Secure Virtual Assist taskbar.
From the technician view of Secure Virtual Assist, technicians can send email invitations to customers that contain a direct URL link to initiate a Secure Virtual Assist session. The technician can optionally include a unique message to the customer. When the customer clicks on the email link to Secure Virtual Assist, only the technician who sent the invitation can assist that customer.
Secure Virtual Access, as part of the larger Secure Virtual Assist feature, allows technicians to gain access to systems outside the LAN of the SRA appliance, such as their personal systems. After downloading and installing a client from the portal page for Secure Virtual Access mode, the personal system will appear only on that technician’s Secure Virtual Assist support queue, within the SRA management interface. While Secure Virtual Access must be enabled per-portal, this functionality provides greater remote access flexibility for support technicians.
Installing and using Secure Virtual Access requires administrative privileges.
Launching a Secure Virtual Assist Technician Session
To launch a Secure Virtual Assist session as a technician, perform the following steps.
1. Log in to the SRA Virtual Office. If you are already logged in to the SRA customer interface, click on the Virtual Office button.
2. Click on the Virtual Assist button.

3. If the Virtual Assist plug-in is installed, the Virtual Assist window is displayed automatically. See 9. on page 51.
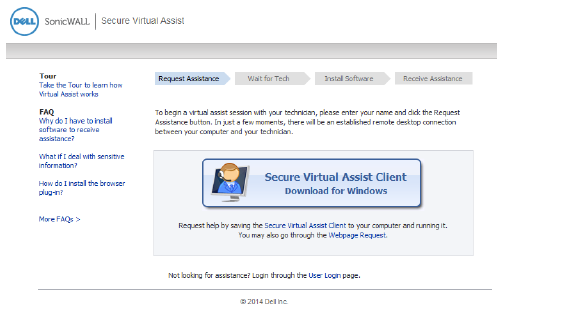
4. If the Virtual Assist plug-in is not installed, the File Download window displays, and Secure Virtual Assist attempts to automatically install. Click Run to launch the program directly, or click Save to save the installer file to your computer, and then manually launch it.
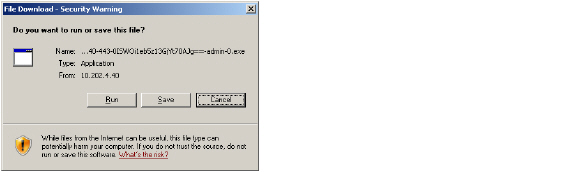
When downloading through IPv6, the File Download window displays IPv6 information.
5. When you launch the installer, you may see an additional warning message. Click Run.
6. A pop-up window asks if you would like to install Secure Virtual Assist as a standalone client. Click Yes to save the application. A shortcut will be added to your desktop and a link to the application will be added to the program list on your Start Menu. Click No to launch Secure Virtual Assist without saving the application for future use.

7. If you clicked Yes to save the application, you will be prompted to select a location to save the file. Select an appropriate location, such as C:\Program Files\SonicWALL.
8. When Secure Virtual Assist launches for the first time, you may see a security warning pop-up window. De-select the Always ask before opening this file check box to avoid this window in the future. Click Run.
9. The Secure Virtual Assist standalone application launches.
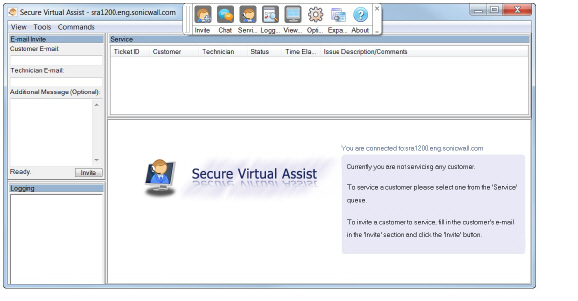
10. The technician is now ready to assist customers.
Performing Secure Virtual Assist Technician Tasks
To get started, the technician logs into the SRA appliance and launches the Secure Virtual Assist application.
Note Each technician can only assist one customer at a time.
Once the technician has launched the Secure Virtual Assist application, the technician can assist customers by performing the following tasks:
• Using the Secure Virtual Assist Taskbar
• Controlling the Secure Virtual Assist Display
To invite a customer to a Secure Virtual Assist session by email:
1. To invite a customer to Secure Virtual Assist, use the email invitation form on the left of the Secure Virtual Assist window.
Note Customers who launch Secure Virtual Assist from an email invitation can only be assisted by the technician who sent the invitation. Customers who manually launch Secure Virtual Assist can be assisted by any technician.
2. Enter the customer’s email address in the Customer E-mail field.
3. Optionally, enter Technician E-mail to use a different return email address than the default technician email.
4. Optionally, enter an Additional Message to the customer.
5. Click Invite. The customer will receive an email with an HTML link to launch Secure Virtual Assist.
6. Customers requesting assistance will appear in the Assistance Queue, and the duration of time they have been waiting will be displayed.
1. A pop-up window in the lower right task bar alerts the technician when a customer is in the assistance queue.
2. Double-click on a customer’s user name to begin assisting the customer.
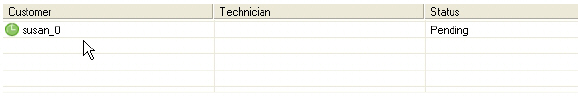
3. The customer’s entire desktop is displayed in the bottom right window of the Secure Virtual Assist application.
The technician now has complete control of the customer’s keyboard and mouse. The customer can see all of the actions that the technician performs.
During a Secure Virtual Assist session, the customer is not locked out of their computer. Both the technician and customer can control the computer, although this may cause confusion and consternation if they both attempt “to drive” at the same time.
The customer has a small tool bar in the bottom right of their screen, with three options.
The customer has the following options during a Secure Virtual Assist session, each enabled after clicking the corresponding button.
• Active - Toggles to the View Only mode, where the technician can view the customer’s computer but cannot control the computer.
• Chat - Initiates a chat window with the technician.
• End Virtual Assist - Terminates the session.
Using the Secure Virtual Assist Taskbar
The Technician’s view of Secure Virtual Assist includes a taskbar with a number of options.
In Windows, the taskbar contains the following buttons:
• Refresh - Refreshes the display of the customer’s computer.
• File Transfer - Launches a window to transfer files to and from the customer’s computer. see Using the Secure Virtual Assist File Transfer for more information.
• Chat - Launches the chat window to communicate with the customer. The technician can also use the dedicated chat window in the bottom left window of the Secure Virtual Assist application.
• System Info -Displays detailed information about the customer’s computer.
• Reboot Customer - Reboot the customer’s computer. Unless you have Requested full control, the customer will be warned about and given the opportunity to deny the reboot.
• Switch Screen - Switches to a second monitor if the customer’s computer has more than one monitor configured.
In MacOS, the taskbar contains the following buttons:
• Refresh - Refreshes the display of the customer’s computer.
• Auto Scale - Adjusts the screen to fit the window size.
• Full Screen - Adjusts the screen to fill the entire window.
• System Info -Displays detailed information about the customer’s computer similar to that shown for a Windows computer.
• Reboot - Reboot the customer’s computer. Unless you have Requested full control, the customer will be warned about and given the opportunity to deny the reboot.
• Chat - Launches the text chat window to communicate with the customer. The technician can also use the dedicated chat window in the bottom left window of the Secure Virtual Assist application.
• File Transfer - Launches a window to transfer files to and from the customer’s computer. see Using the Secure Virtual Assist File Transfer for more information.
• Hide Toolbar - Hides the taskbar from view.
• Gray Color - Displays everything in grey monochrome
Controlling the Secure Virtual Assist Display
• Full Screen - Hides all of the Secure Virtual Assist toolbars and displays the customer’s desktop on the technician’s entire screen with the Secure Virtual Assist taskbar in the top left corner.
If the Secure Virtual Assist taskbar doesn’t display, move your mouse to the top middle of the screen. Right-click on the taskbar and click Restore to exit full-screen mode.
• Auto Scaling - Zooms the display to fill the entire Secure Virtual Assist window.
• Zoom - Zooms the display to one of several presets or allows you enter a specific value.
• True Size - Zooms to 100%.
• Side Bar - Toggles the display of the side bar with the email invitation and chat windows.
• Top Bar - Toggles the display of the top bar with the customer queue and toolbar.
• All Bars - Displays both the side bar and top bar.
• No Bar - Hides both the side bar and top bar.
Note A number of these options can be configured from the pull-down menus at the top of the Secure Virtual Assist application.
Technicians can request full control of a customer’s desktop, allowing them to reboot the system, delete files, or over-write files on the customer’s computer without the customer being repeatedly prompted for permission. Select Request Full Control under the Commands menu to issue a request that will appear on the customer’s desktop.
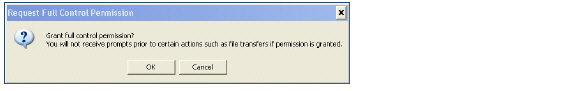
Using the Secure Virtual Assist File Transfer
The File Transfer window is used to transfer files to and from the customer’s computer. The file directory of the technician’s computer is shown on the left and the customer’s computer on the right.
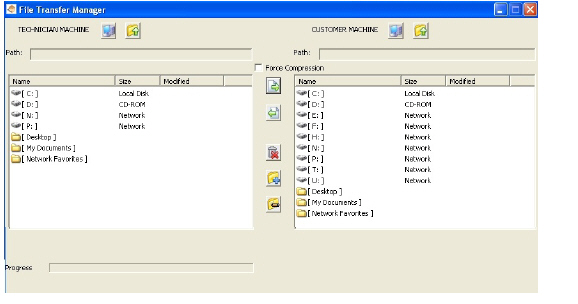
The File Transfer window functions in much the same manner as Windows Explorer or an FTP program. Navigate the File Transfer window by double-clicking on folders and selecting files. The File Transfer window includes the following controls:
• Desktop  jumps to the desktop of the technician’s or customer’s computer.
jumps to the desktop of the technician’s or customer’s computer.
• Up  navigates up one directory on either the technician’s or customer’s computer.
navigates up one directory on either the technician’s or customer’s computer.
• Download  transfers the selected file or files from the technician’s computer to the customer’s computer.
transfers the selected file or files from the technician’s computer to the customer’s computer.
• Upload  transfers the selected file or files from the customer’s computer to the technician’s computer.
transfers the selected file or files from the customer’s computer to the technician’s computer.
• Delete  deletes the selected file or files.
deletes the selected file or files.
Note When deleting or over-writing files, the customer is warned and must give the technician permission unless the technician has elected Request Full Control and the customer has confirmed.
• New folder  creates a new folder in the selected directory.
creates a new folder in the selected directory.
• Rename  renames the selected file or directory.
renames the selected file or directory.
When a file is transferring, the transfer progress is displayed at the bottom of the File Transfer window. Click the Exit button to cancel a transfer in progress.
Note File Transfer supports the transfer of single or multiple files. It does not currently support the transfer of directories. To select multiple files, hold down the Ctrl button while clicking on the files.
Enabling a System for Secure Virtual Access
If Secure Virtual Access has been enabled on the Virtual Assist tab on the Portals > Portals page of the management interface, users should see a link on the portal to set-up a system for Secure Virtual Access. To enable Secure Virtual Access within the SRA management interface, see Configuring Per-Portal Virtual Assist Settings.
To configure Secure Virtual Access on a system:
1. Login to the portal through the system you wish to configure for Secure Virtual Access and click the Virtual Access link.

2. A file should download with parameters to install the VASAC.exe file that will provide the needed client for Secure Virtual Access mode. Save and run the file.
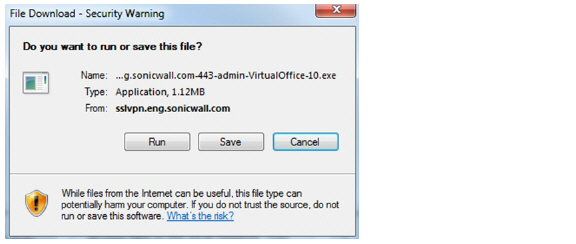
Note Running the file directly from this dialog box may not work on some systems. Save the file to the system and then run the application.
3. Fill in the necessary information in the provided fields to configure the system in Secure Virtual Access mode and click OK.
• Server: This should be the name or IP address of the appliance the technician normally accesses the Virtual Office from outside the management interface (Do not include “https://”).
• Portal: The name of the portal the technician would normally login to.
• Computer Name: This is an identifier for the system to help differentiate between other systems that may be waiting for support in the queue.
• Password: This is a password the technician must enter prior to accessing the system through the support queue.
4. After installation, the VASAC client should be left running in the desktop tray.
This system’s identifier name should now appear in the technician’s support queue displayed on the Secure Virtual Assist > Status page within the management interface.Upon double-clicking the system listing, the technician will be prompted to provide the password established during system set-up to gain Secure Virtual Access to the system.
Ending Secure Virtual Access Mode
Disconnecting from a Secure Virtual Access session will place the system back in the support queue for later access by the technician. From the personal system-side, the user/technician may uninstall or terminate the application from the tray option icons.
An administrator can forcibly remove a system from the queue. If this occurs, the Secure Virtual Access system should no longer attempt to connect to the support queue and should display an error message.
Note For tasks and information on using Secure Virtual Assist as an end-user, refer to the Dell SonicWALL SRA User’s Guide.
Secure Virtual Meeting Overview
This section provides an introduction to the Secure Virtual Meeting feature. This section contains the following topics:
• What is Secure Virtual Assist?
• Benefits of Secure Virtual Assist
• How Does Secure Virtual Assist Work?
• Launching a Secure Virtual Assist Technician Session
• Performing Secure Virtual Assist Technician Tasks
• Enabling a System for Secure Virtual Access
What is Secure Virtual Meeting?
Secure Virtual Meeting is a for the SRA 4200 and Virtual Appliance. Secure Virtual Meeting allows multiple users to view a desktop and interactively participate in a meeting from virtually anywhere with an Internet connection. Secure Virtual Meeting is similar to the one-to-one desktop sharing provided by Virtual Assist except multiple users can share a desktop.
Benefits of Secure Virtual Meeting
Secure Virtual Meeting provides the following benefits:
• Secure connections - 256-bit AES SSL encryption of the data by the SonicWALL SRA appliance provides a secure environment for the data and assists in the effort to be compliant with regulations like Sarbanes-Oxley and HIPAA.
• Time and cost savings - Secure Virtual Meeting eliminates the need to visit customer sites and reduces the average time-to-resolution of support calls.
• Educational tool - Trainers and support staff can use Secure Virtual Meeting to remotely show customers how to use programs and tools.
• Configurable environment with multiple functions - Meeting parameters can be configured for specific meetings, in addition to meeting configurations that apply to all virtual meetings.
• Meeting functions - Meeting attendees may perform several functions, such as polling meeting attendees, text chatting, and switching who shares their desktop or controls the meeting.
User Roles
Secure Virtual Meeting has several user roles:
• Coordinator (Owner of the meeting) - The Coordinator must be a SonicWALL SRA user on the appliance. The Coordinator schedules, sets up, and controls the meeting. In addition, the Coordinator has the sole power to promote a Participant to the Assistant.
• Assistant (Coordinator-designated Assistant) - The Coordinator selects an Assistant from the list of available Participants and assigns the Assistant privileges. When the Coordinator exits the meeting, the Assistant automatically becomes the Coordinator. A meeting may have multiple Assistants, each with the same or a different set of privileges. An Assistant need not be a user of the SSL-VPN appliance. Possible Assistant privileges are:
– Start/End Meeting
– Set Host
– Open Polling
– Set/Unset View Only
– Invite Participants
– Kick out Participants
– Reschedule Meeting
• Host - The Host is a Participant who shares their desktop with all Participants in the meeting. When a meeting begins, the Host’s desktop is shown to all Participants. The Host can be changed by the Coordinator during the meeting by selecting any available Participant. If a Host is not explicitly set when the meeting starts, the Coordinator becomes the Host. Only one Participant is designated as the Host at any one time.
Only the Host can control the Host System, unless the Host grants permission when a Participant requests control. The Host may also give control to any Participant by selecting the Participant from the Meeting Members list. Only one Participant can control the Host System at any one time. When a Participant takes control of the Host System, he loses control as soon as the Host moves his mouse pointer on the screen. The meeting control permission state is visible to all Participants while in the lobby.
• Participant (User with credentials to join the meeting) - A Participant must enter a meeting code before they can join a meeting. The code required to join the meeting is determined by the Coordinator prior to the meeting. After joining a meeting, the Participant can view the shared desktop and chat with another attendee privately or type a message in the Chat window that is visible to all attendees. A Participant becomes the Assistant if selected by the Coordinator or by an Assistant who has the required privilege.
• View-only Participant (User with limited meeting capabilities) - The Coordinator may designate any Participant as a View-only Participant. A View-only Participant cannot be assigned any privileges nor become an Assistant or Host.
Roles are switched before or during a meeting. A Coordinator or Assistant with necessary privileges can change the roles of any Participant during the meeting. A Participant wishing to become the Host must request permission from the Coordinator.
How Does a Secure Virtual Meeting Work?
The following sections describe how Secure Virtual Meeting works,
Configuring Secure Virtual Meeting
Secure Virtual Meeting configuration and management tasks are performed via the AMC console and consists of the following:
• Status
• Settings
• Log
• Licensing
These tasks are explained in detail in Secure Virtual Meeting chapter of the SRA Administrator’s Guide and the Secure Virtual Meeting Feature Module.
The Virtual Meeting Coordinator performs the following tasks:
|
The following functions can be performed from the lobby by clicking buttons:
 Clicking the Start Meeting button starts the meeting. Only the Coordinator and Assistant can start a meeting.
Clicking the Start Meeting button starts the meeting. Only the Coordinator and Assistant can start a meeting.
 Clicking the Stop Meeting button stops the meeting. Only the Coordinator and Assistant can end the meeting.
Clicking the Stop Meeting button stops the meeting. Only the Coordinator and Assistant can end the meeting.
 Clicking the Polling button opens the polling window where you can load, edit, and start a poll for Participants currently in the meeting. Only the Coordinator and Assistant can initiate polling.
Clicking the Polling button opens the polling window where you can load, edit, and start a poll for Participants currently in the meeting. Only the Coordinator and Assistant can initiate polling.
 Clicking the Invite button sends an email invitation to Participants. Only the Coordinator and Assistant can invite Participants.
Clicking the Invite button sends an email invitation to Participants. Only the Coordinator and Assistant can invite Participants.
 Clicking the Reschedule Meeting button reschedules the meeting start and end times. Only the Coordinator and Assistant can reschedule a meeting.
Clicking the Reschedule Meeting button reschedules the meeting start and end times. Only the Coordinator and Assistant can reschedule a meeting.
 Clicking the Request Host button informs the Host that you want to become the Host and share your desktop. Only Participants who are not currently the Host can request to become the Host.
Clicking the Request Host button informs the Host that you want to become the Host and share your desktop. Only Participants who are not currently the Host can request to become the Host.
 Clicking the Quit button exits the meeting and return to the meeting selection window. Anyone in the meeting can quit the meeting.
Clicking the Quit button exits the meeting and return to the meeting selection window. Anyone in the meeting can quit the meeting.
 Clicking the Start Sharing button shares the Host desktop with all Participants in the meeting. Sharing is only available during a meeting.
Clicking the Start Sharing button shares the Host desktop with all Participants in the meeting. Sharing is only available during a meeting.
 Clicking the Stop Sharing button stops sharing the Host System desktop. Only the Host can stop sharing and only while in the sharing state (after Start Sharing has been selected).
Clicking the Stop Sharing button stops sharing the Host System desktop. Only the Host can stop sharing and only while in the sharing state (after Start Sharing has been selected).
 Clicking the Request Control button requests that the Host give you control of the keyboard and mouse. Only Participants who aren’t the Host can request control.
Clicking the Request Control button requests that the Host give you control of the keyboard and mouse. Only Participants who aren’t the Host can request control.
Using the Control Menu during a Meeting
The Control Menu is available at the top of a shared desktop when the Host shares the desktop during an active meeting.
 The Invite button is available for the Coordinator or Assistants with invite permission. It opens the invite dialog if the lobby is not open.
The Invite button is available for the Coordinator or Assistants with invite permission. It opens the invite dialog if the lobby is not open.
 The Polling button is available for the Coordinator or Assistants with polling permission. It opens the polling dialog.
The Polling button is available for the Coordinator or Assistants with polling permission. It opens the polling dialog.
 The Chat button is available for all Participants, including View-only Participants. It opens a chat dialog if the lobby is not open.
The Chat button is available for all Participants, including View-only Participants. It opens a chat dialog if the lobby is not open.
 The Lobby button is available for all meeting members, including View-only Participants. If the lobby is hidden during a meeting, it displays the lobby window when the Host is sharing the screen.
The Lobby button is available for all meeting members, including View-only Participants. If the lobby is hidden during a meeting, it displays the lobby window when the Host is sharing the screen.
 The Options button opens the Meeting Settings window and is available for all Participants.
The Options button opens the Meeting Settings window and is available for all Participants.
 The Viewer button is available for all Participants except the Host. It toggles the window between the Participant’s window and the Host’s desktop.
The Viewer button is available for all Participants except the Host. It toggles the window between the Participant’s window and the Host’s desktop.
 The About button opens the About dialog, which identifies the Secure Virtual Meeting client and version. The About button is available for all meeting members, including View-only Participants.
The About button opens the About dialog, which identifies the Secure Virtual Meeting client and version. The About button is available for all meeting members, including View-only Participants.
Participants can be designated as View-only Participants or regular Participants. View-only Participants enter and exit meetings like other Participants, but cannot perform most functions. However, they can be kicked out of meetings like other regular Participants. Regular Participants can also:
• Respond to polls
• Text chat
• Request control of the Host keyboard and mouse
• Request to become the Host and share the Participant’s desktop
• Become the Assistant
• Become a View-only Assistant
Web Application Firewall Overview
This section provides an introduction to the Web Application Firewall feature. This section contains the following topics:
• What is Web Application Firewall?
• Benefits of Web Application Firewall
• How Does Web Application Firewall Work?
What is Web Application Firewall?
Web Application Firewall is subscription-based software that runs on the Dell SonicWALL SRA appliance and protects Web applications running on servers behind the SRA. Web Application Firewall also provides real-time protection for resources such as HTTP(S) bookmarks, Citrix bookmarks, offloaded Web applications, and the SRA management interface and user portal that run on the Dell SonicWALL SRA appliance itself.
Web Application Firewall provides real-time protection against a whole suite of Web attacks such as Cross-site scripting, SQL Injection, OS Command Injection, and many more. The top ten vulnerabilities for Web applications are tracked by OWASP, an open source community that focuses its efforts on improving the security of Web applications. Dell SonicWALL SRA Web Application Firewall protects against these top ten, defined in 2007 as follows:
Table 9 OWASP Top Ten Vulnerabilities
|
Slowloris Protection
In addition to the top ten threats listed above, Web Application Firewall protects against Slowloris HTTP Denial of Service attacks. This means that Web Application Firewall also protects all the backend Web servers against this attack. Many Web servers, including Apache, are vulnerable to Slowloris. Slowloris is especially effective against Web servers that use threaded processes and limit the amount of threading allowed.
Slowloris is a stealthy, slow-acting attack that sends partial HTTP requests at regular intervals to hold connections open to the Web server. It gradually ties up all the sockets, consuming sockets as they are freed up when other connections are closed. Slowloris can send different host headers, and can send GET, HEAD, and POST requests. The string of partial requests makes Slowloris comparable to a SYN flood, except that it uses HTTP rather than TCP. Only the targeted Web server is affected, while other services and ports on the same server are still available. When the attack is terminated, the Web server can return to normal within as little as 5 seconds, making Slowloris useful for causing a brief downtime or distraction while other attacks are initiated. Once the attack stops or the session is closed, the Web server logs may show several hundred 400 errors.
For more information about how Web Application Firewall protects against the OWASP top ten and Slowloris types of attacks, see How Does Web Application Firewall Work?.
Offloaded Web Application Protection
Web Application Firewall can also protect an offloaded Web application, which is a special purpose portal created to provide seamless access to a Web application running on a server behind the SRA appliance. The portal must be configured as a virtual host. It is possible to disable authentication and access policy enforcement for such an offloaded host. If authentication is enabled, a suitable domain needs to be associated with this portal and all Dell SonicWALL advanced authentication features such as One Time Password, Two-factor Authentication, and Single Sign-On apply to the offloaded host.
Application Profiling
Starting in SRA 5.5, Application Profiling (Phase 1) allows the administrator to generate custom rules in an automated manner based on a trusted set of inputs. This is a highly effective method of providing security to Web applications because it develops a profile of what inputs are acceptable by the application. Everything else is denied, providing positive security enforcement. This results in fewer false positives than generic signatures, which adopt a negative security model. When the administrator places the device in learning mode in a staging environment, the SRA appliance learns valid inputs for each URL accessed by the trusted users. At any point during or after the learning process, the custom rules can be generated based on the “learned” profiles.
Rate Limiting for Custom Rules
Starting in SRA 5.5, it is possible to track the rate at which a custom rule, or rule chain, is being matched. This is extremely useful to block dictionary attacks or brute force attacks. The action for the rule chain is triggered only if the rule chain is matched as many times as configured.
Cookie Tampering Protection
Cookie Tampering Protection is an important item in the Payment Card Industry Data Security Standard (PCI DSS) section 6.6 requirements and part of the Web Application Firewall evaluation criteria that offers strict security for cookies set by the backend Web servers. Various techniques such as encryption and message digest are used to prevent cookie tampering. See Configuring Cookie Tampering Protection Settings for additional information.
Credit Card and Social Security Number Protection
Credit Card/SSN protection is a Data Loss Prevention technique that ensures that sensitive information, such as credit card numbers and Social Security numbers are not leaked within Web pages. Once such leakage is detected, the administrator can choose to mask these numbers partially or wholly, present a configurable error page, or simply log the event. See Configuring Information Disclosure Protection for additional information.
Web Site Cloaking
Web Site Cloaking prevents guessing the Web server implementation and exploiting its vulnerabilities. See Configuring Web Site Cloaking for additional information.
PDF Reporting for WAF Monitoring and PCI DSS 6.5 and 6.6 Compliance
Starting in SRA 5.5, PDF reporting is introduced for Web Application Firewall Monitoring and PCI DSS 6.5 and 6.6 Compliance. You can generate the reports on the Web Application Firewall > Status page. The timeline for generating the data published in the reports is configurable on the Web Application Firewall > Monitoring page.
Benefits of Web Application Firewall
Web Application Firewall is secure and can be used in various areas, including financial services, healthcare, application service providers, and e-commerce. Dell SonicWALL SRA uses SSL encryption to encrypt data between the Web Application Firewall and the client. Dell SonicWALL SRA also satisfies OWASP cryptographic storage requirements by encrypting keys and passwords wherever necessary.
Companies using Web Application Firewall can reduce the development cost required to create secure applications and also cut out the huge turnaround time involved in deploying a newly found vulnerability fix in every Web application by signing up for Web Application Firewall signature updates.
Resources accessed over Application Offloaded portals and HTTP(S) bookmarks can be vulnerable due to a variety of reasons ranging from badly designed architecture to programming errors. Web Application Firewall provides an effective way to prevent a hacker from exploiting these vulnerabilities by providing real-time protection to Web applications deployed behind the Dell SonicWALL SRA appliance.
Deploying Web Application Firewall at the SRA appliance lets network administrators use application offloading even when it exposes Web applications needing security to internal and remote users. Application offloading avoids URL rewriting, which improves the proxy performance and functionality.
There are several benefits of integrating Web Application Firewall with Dell SonicWALL SRA appliances. Firstly, identity-based policy controls are core to Web Application Firewall and this is easily achievable using SSL VPN technology. Secondly, there are lower latencies due to the existing hardware-based SSL offloading. Most importantly, SRA appliances run Web applications and must be protected from such attacks.
As small businesses adopt hosted services to facilitate supplier collaboration, inventory management, online sales, and customer account management, they face the same strict compliance requirements as large enterprises. Web Application Firewall on a Dell SonicWALL SRA appliance provides a convenient, cost-effective solution.
Web Application Firewall is easy to configure in the Dell SonicWALL SRA management interface. The administrator can configure Web Application Firewall settings globally, by attack priority, and on a per-signature basis. Once custom configuration settings or exclusions are in place, you can disable Web Application Firewall without losing the configuration, allowing you to perform maintenance or testing and then easily re-enable it.
How Does Web Application Firewall Work?
To use the Web Application Firewall feature, the administrator must first license the software or start a free trial. Web Application Firewall must then be enabled on the Web Application Firewall > Settings page of the Dell SonicWALL SRA management interface.Web Application Firewall can be configured to log or block detected attacks arriving from the Internet.
The following sections describe how Web Application Firewall and SRA appliances prevent attacks such as Slowloris or those listed in the OWASP top ten, how Web Application Firewall protects against information disclosure, and how other features work:
• How are Signatures Used to Prevent Attacks?
• How is Cross-Site Request Forgery Prevented?
• How is Information Disclosure Prevented?
• How are Broken Authentication Attacks Prevented?
• How are Insecure Storage and Communications Prevented?
• How is Access to Restricted URLs Prevented?
• How are Slowloris Attacks Prevented?
• What Type of PCI Compliance Reports Are Available?
• How Does Cookie Tampering Protection Work?
• How Does Application Profiling Work?
• How Does Rate Limiting for Custom Rules Work?
How are Signatures Used to Prevent Attacks?
For Cross Site Scripting, Injection Flaws, Malicious File Execution, and Insecure Direct Object Reference vulnerabilities, the Web Application Firewall feature uses a black list of signatures that are known to make Web applications vulnerable. New updates to these signatures are periodically downloaded from a Dell SonicWALL signature database server, providing protection from recently introduced attacks.
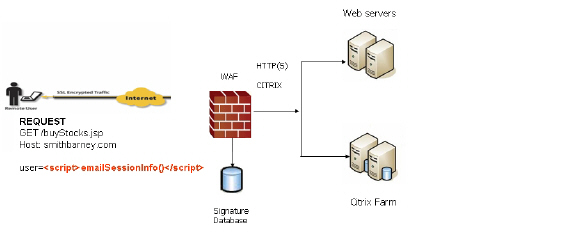
When input arrives from the Internet, Web Application Firewall inspects HTTP/HTTPS request headers, cookies, POST data, query strings, response headers, and content. It compares the input to both a black list and a white list of signatures. If pattern matching succeeds for any signature, the event is logged and/or the input is blocked if so configured. If blocked, an error page is returned to the client and access to the resource is prevented. If blocked, an error page is returned to the client and access to the resource is prevented. The threat details are not exposed in the URL of the error page. If configured for detection only, the attack is logged but the client can still access the resource. If no signature is matched, the request is forwarded to the Web server for handling.
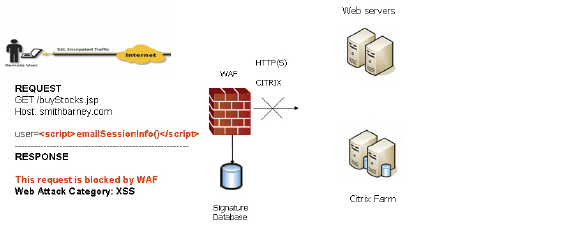
The Web Application Firewall process is outlined in the following flowchart.
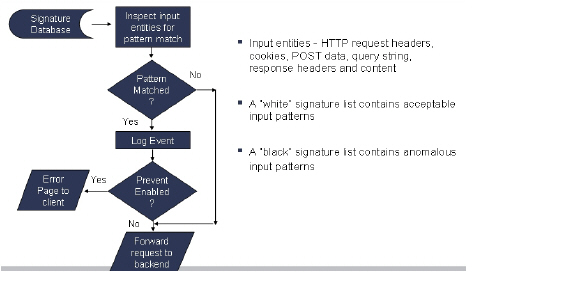
In the case of a blocked request, the following error page is returned to the client:
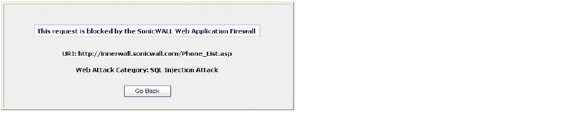
This page is customizable under Web Application Firewall > Settings in the SRA management interface. Some administrators may want to customize the HTML contents of this page. Others may not want to present a user friendly page for security reasons. Instead, they may prefer the option to present an HTTP error code such as 404 (Not found) or 403 (Access Denied).
How is Cross-Site Request Forgery Prevented?
CSRF attacks are not detected with signature matching. Using this vulnerability, a hacker disguised as the victim can gain unauthorized access to application even without stealing the session cookie of a user. While a victim user is authenticated to a Web site under attack, the user may unwittingly load a malicious Web page from a different site within the same browser process context, for instance, by launching it in a new tab part of the same browser window. If this malicious page makes a hidden request to the victim Web server, the session cookies in the browser memory are made part of this request making this an authenticated request. The Web server serves the requested Web page as it assumes that the request was a result of a user action on its site. To maximize the benefits, typically, hackers targets actionable requests, such as data updates to carry out this attack.
To prevent CSRF attacks, every HTTP request within a browser session needs to carry a token based on the user session. To ensure that every request carries this token, the Web Application Firewall feature rewrites all URLs contained in a Web page similarly to how they are rewritten by the Reverse Proxy for HTTP(S) Bookmarks feature. If CSRF protection is enabled, this is also performed for Application Offloading.
CSRF protection is provided for anonymous mode as well. If CSRF protection is enabled, then an idle timeout set to the global idle timeout is enforced for anonymous access. If the session times out, an error message is displayed, forcing the user to revisit the site in a new window. If authentication is enforced for the portal, then the user is redirected to the login page for the portal.
How is Information Disclosure Prevented?
Web Application Firewall prevents Information Disclosure and Improper Error Handling by providing a way for the administrator to configure text containing confidential and sensitive information so that no Web site accessed through the Web Application Firewall reveals this text. These text strings are entered on the Web Application Firewall > Settings page.
Beside the ability to pattern match custom text, signatures pertaining to information disclosure are also used to prevent these types of attacks.
Beginning in SRA 5.5, Web Application Firewall protects against inadvertent disclosure of credit card and Social Security numbers (SSN) in HTML Web pages.
Note Only text or HTML pages, and only the first 512K bytes are inspected for credit card or SSN disclosure.
Web Application Firewall can identify credit card and SSN numbers in various formats. For example, a SSN can be specified as XXX XX XXXX or XXX-XX-XXXX. Web Application Firewall attempts to eliminate false-positives by filtering out formats that do not conform to the credit card or SSN specification. For example, credit cards follow the Luhn’s algorithm to determine if an n-digit number could be a credit card number or not.
The administrator can set an appropriate action, such as detect (log), prevent, or just mask the digits that can reveal the user identity. Masking can be done fully or partially, and you can select any of the following characters for masking: #, *, -, x, X, ., !, $, and ?. The resulting masked number is similar to the appearance of credit card numbers printed on an invoice.
How are Broken Authentication Attacks Prevented?
The requirement for Broken Authentication and Session Management requires Web Application Firewall to support strong session management to enhance the authorization requirements for Web sites. Dell SonicWALL SRA already has strong authentication capabilities with the ability to support One Time Password, Two-factor Authentication, Single Sign-On, and client certificate authentication.
For Session Management, Web Application Firewall pops up a session logout dialog box when the user portal is launched or when a user logs into an application offloaded portal. This feature is enabled by default when Web Application Firewall is licensed and can be disabled from the Web Application Firewall > Settings page.
How are Insecure Storage and Communications Prevented?
Insecure Cryptographic Storage and Insecure Communications are prevented by encrypting keys and passwords wherever necessary, and by using SSL encryption to encrypt data between the Web Application Firewall and the client. Dell SonicWALL SRA also supports HTTPS with the backend Web server.
How is Access to Restricted URLs Prevented?
Dell SonicWALL SRA supports access policies based on host, subnet, protocol, URL path, and port to allow or deny access to Web sites. These policies can be configured globally or for users and groups.
How are Slowloris Attacks Prevented?
Slowloris attacks can be prevented if there is an upstream device, such as a Dell SonicWALL SRA security appliance, that limits, buffers, or proxies HTTP requests. Web Application Firewall uses a rate-limiter to thwart Slowloris HTTP Denial of Service attacks.
What Type of PCI Compliance Reports Are Available?
Payment Card Industry Data Security Standard (PCI DSS) 6.5 (Version 2.0) and PCI DSS 6.6 (Version 1.2) are covered in PCI reporting. The administrator can configure Web Application Firewall to satisfy these PCI requirements.
You can generate and download the PCI report file on the Web Application Firewall > Status page.
Note This is not an official PCI Compliance report. It is for your self-assessment only.
In the report cover, the following information is displayed:
• The model, serial number, and firmware version of the appliance
• The user name of the person who downloaded the report, displayed as the author of the report
• Time when the report was generated
An example is shown below:
Two tables are dynamically generated in the PCI compliance report to display the status of each PCI requirement. The format of the table is shown in the example below:
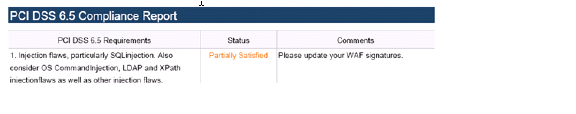
The first column describes the PCI requirement.
The second column displays the status of the PCI requirement under current Web Application Firewall settings. There are 4 possible values for the status, distinguished by color.
• Satisfied (Green)
• Partially Satisfied (Orange)
• Unsatisfied (Red)
• Unable to determine (Black)
The third column provides comments and details explaining the status rating. If the status is Satisfied, no comments are provided.
How Does Cookie Tampering Protection Work?
SRA appliances protect important server-side cookies from tampering.
There are two kinds of cookies:
Server-Side Cookies – These cookies are generated by backend Web servers. They are important and have to be protected. They have optional attributes like Path, Domain, Secure, and HttpOnly.
Client-Side Cookies – These cookies are created by client side scripts in user browsers. They are not safe, and can be easily tampered with.
This feature is found on the Web Application Firewall > Settings page.
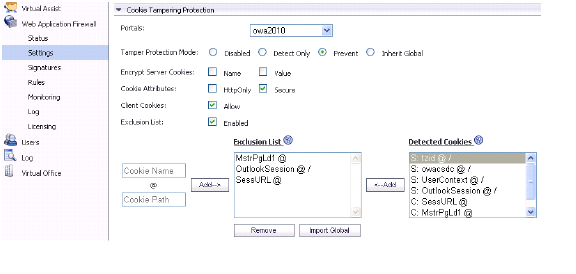
This page contains the following options:
Portals – A list of all application offloading portals. Each portal will have its own setting. The item Global is the default setting for all portals.
Tamper Protection Mode – Three modes are available:
• Prevent – Strip all the tampered cookies and log them.
• Detect only – Log the tampered cookies only.
• Inherit Global – Use the global setting for this portal.
Encrypt Server Cookies – Choose to encrypt name and value separately. This affects client-side script behavior because it makes cookie names or values unreadable. Only server-side cookies are encrypted by these options.
Cookie Attributes – The attributes HttpOnly and Secure are appended to server-side cookies if they are enabled.
The attribute HttpOnly prevents the client-side scripts from accessing the cookies, which is important in mitigating attacks such as Cross Site Scripting and session hijacking. The attribute Secure ensures that the cookies are transported only in HTTPS connections. Both together add a strong layer of security for the server-side cookies.
Note By default, the attribute Secure is always appended to an HTTP connection even if Cookie Tampering Protection is disabled. This behavior is a configurable option, and can be turned off.
Allow Client Cookies – The Allow Client Cookies option is enabled by default. In Strict mode, the Allow Client Cookies option is disabled. When disabled, client-side cookies are not allowed to be sent to the backend systems. This option does not affect server-side cookies.
Exclusion List – If the Exclusion List is enabled and contains a cookie, the cookie is passed as usual and is not protected. You can exclude server-side cookies and client-side cookies.
Exclusion list items are case sensitive, and in the format ‘CookieName@CookiePath’. Cookies with the same name and different paths are treated as different cookies. ‘CookiePath’ can be left empty to represent any path.
Import Global – Application Offloading portals can import the Global exclusion list.
How Does Application Profiling Work?
The administrator can configure application profiling on the Web Application Firewall > Rules page. Application profiling is performed independently for each portal and can profile multiple applications simultaneously.
After selecting the portal, you can select the type of application content that you want to profile. You can choose HTML/XML, Javascript, CSS, or All, which includes all content types such as images, HTML, and CSS. HTML/XML content is the most important from a security standpoint, because it typically covers the more sensitive Web transactions. This content type is selected by default.
Then the SRA appliance is placed in learning mode by clicking on the Begin Profiling button (the button then changes to End Profiling). The profiling should be done while trusted users are using applications in an appropriate way. The SRA records inputs and stores them as URL profiles. The URL profiles are listed as a tree structure on the Web Application Firewall > Rules page in the Application Profiling section.
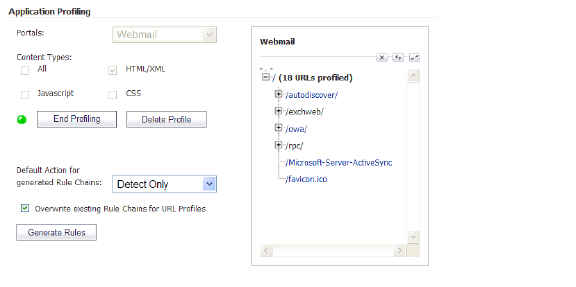
Only the URLs presented as hyperlinks are accessible URLs on the backend server. You can click on the hyperlink to edit the learned values for that URL if the values are not accurate. You can then generate rules to use the modified URL profile.
The SRA learns the following HTTP Parameters:
• Response Status Code
• Post Data Length – The Post Data Length is estimated by learning the value in the Content-Length header. The maximum size is set to the power of two that is closest to and higher than this value. This accommodates the amount of memory that may have been allocated by the backend application. For example, for a Content Length of 65, the next power of two greater than 65 is 128. This is the limit configured in the URL profile. If the administrator determines that this is not accurate, the value can be modified appropriately.
• Request Parameters – This is the list of parameters that a particular URL can accept.
When an adequate amount of input has been learned, you can click the End Profiling button and are ready to generate the rules from the learned input. You can set one of the following as a default action for the generated rule chains:
• Disabled – The generated rules will be disabled rather than active.
• Detect Only – Content triggering the generated rule will be detected and logged.
• Prevent – Content triggering the generated rule will be blocked and logged.
If a rule chain has already been generated from a URL profile in the past, then the rule chain will be overwritten only if the Overwrite existing Rule Chains for URL Profiles check box is selected. When you click the Generate Rules button, the rules are generated from the URL profiles. If a URL profile has been modified, those changes are incorporated.
How Does Rate Limiting for Custom Rules Work?
The administrator can configure rate limiting when adding or editing a rule chain from the Web Application Firewall > Rules page. When rate limiting is enabled for a rule chain, the action for the rule chain is triggered only when the number of matches within a configured time period is above the configured threshold.
This type of protection is useful in preventing Brute Force and Dictionary attacks. An example rule chain with a Rule Chain ID of 15002 is available in the management interface for administrators to use as reference.
The associated fields are exposed when the Enable Hit Counters check box is selected at the bottom of the New Rule Chain or Edit Rule Chain screen.

Once a rule chain is matched, Web Application Firewall keeps an internal counter to track how many times the rule chain is matched. The Max Allowed Hits field contains the number of matches that must occur before the rule chain action is triggered. If the rule chain is not matched for the number of seconds configured in the Reset Hit Counter Period field, then the counter is reset to zero.
Rate limiting can be enforced per remote IP address or per user session or both. The Track Per Remote Address check box enables rate limiting based on the attacker’s remote IP address.
The Track Per Session check box enables rate limiting based on the attacker’s browser session. This method sets a cookie for each browser session. Tracking by user session is not as effective as tracking by remote IP if the attacker initiates a new user session for each attack.
The Track Per Remote Address option uses the remote address as seen by the SRA appliance. In the case where the attack uses multiple clients from behind a firewall that is configured with NAT, the different clients effectively send packets with the same source IP address and will be counted together.