For a SonicPoint overview, see SonicPoint > SonicPoints.
|
1
|
Navigate to SonicPoint > SonicPoints page.
|
|
2
|
To add a new SonicPoint N profile, click the Add SonicPoint N Profile button in the SonicPoint N Provisioning Profiles table. To edit an existing profile, select the profile and click the Configure icon in the same line as the profile you want to edit. The Add/Edit SonicPoint N Profile dialog displays.
|
You configure the SonicPoint N through options on these tabs:
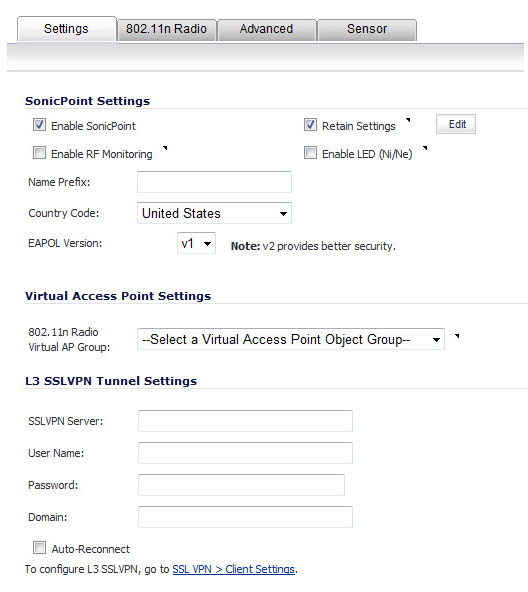
The Settings tab has these sections:
|
1
|
Check Enable SonicPoint to enable each SonicPoint N automatically when it is provisioned with this profile. This option is selected by default.
|
|
2
|
Optionally, check Retain Settings to have the SonicPoint Ns provisioned by this profile retain customized settings until system restart or reboot. This option is not selected by default.
|
If you select this option, the Edit button becomes active. To specify the settings to retain:
|
a
|
|
•
|
Click the Retain All Settings check box; all the other options become dimmed.
|
|
c
|
Click OK.
|
|
3
|
Optionally, check the Enable RF Monitoring check box to enable wireless RF Threat Real Time Monitoring and Management. This option is not selected by default.
|
|
4
|
Optionally, check the Enable LED (Ni/Ne) check box to turn SonicPoint N LEDs on/off. This option is not selected by default.
|
|
5
|
Enter a prefix for the names of all SonicPoint Ns connected to this zone in the Name Prefix field. This prefix assists in identifying SonicPoint N on a zone. When each SonicPoint N is provisioned, it is given a name that consists of the name prefix and a unique number, for example: SonicPoint N 126008.
|
|
6
|
Select the country where you are operating the SonicPoint Ns from the Country Code drop-down menu. The country code determines which regulatory domain the radio operation falls under.
|
|
7
|
From the EAPOL Version drop-down menu, select the version of EAPoL (Extensible Authentication Protocol over LAN) to use: v1 or v2. The default is v1, but v2 provides better security.
|
|
1
|
Optionally, select an 802.11n Virtual Access Point (VAP) group to assign these SonicPoint Ns to a VAP from the 802.11n Radio Virtual AP Group drop-down menu. This drop-down menu allows you to create a new VAP group.
|
|
1
|
In the SSL VPN Server field, enter the IP address of the SSL VPN server.
|
|
2
|
In the User Name field, enter the User Name of the SSL VPN server.
|
|
3
|
In the Password field, enter the Password for the SSL VPN server.
|
|
4
|
In the Domain field, enter the domain that the SSL VPN server is located in.
|
|
5
|
Click the Auto-Reconnect check box for the SonicPoint to auto-reconnect to the SSL VPN server.
|
|
NOTE: The sections and options displayed on the 802.11n Radio tab change depending on whether you selected a VAP group in the 802.11n Radio Virtual AP Group drop-down menu on the Settings tab and the mode you select in the Mode drop-down menu.
|
|
1
|
Click the 802.11n Radio tab.
|
|
1
|
Check the Enable Radio box to automatically enable the 802.11n radio bands on all SonicPoints provisioned with this profile. This option is selected by default.
|
|
•
|
From the Enable Radio drop-down menu, select a schedule for when the 802.11n radio is on or create a new schedule; default is Always on. You can create a new schedule by selecting Create new schedule.
|
|
2
|
Select your preferred radio mode from the Mode drop-down menu. The wireless security appliance supports the following modes:
|
|
•
|
2.4GHz 802.11n Only—Allows only 802.11n clients access to your wireless network. 802.11a/b/g clients are unable to connect under this restricted radio mode.
|
|
•
|
2.4GHz 802.11n/g/b Mixed—Supports 802.11b, 802.11g, and 802.11n clients simultaneously. If your wireless network comprises multiple types of clients, select this mode. This is the default.
|
|
TIP: For 802.11n clients only, for optimal throughput speed solely, SonicWall recommends the 802.11n Only radio mode. Use the 802.11n/b/g Mixed radio mode for multiple wireless client authentication compatibility.
|
|
•
|
2.4GHz 802.11g Only—If your wireless network consists only of 802.11g clients, you may select this mode for increased 802.11g performance. You may also select this mode if you wish to prevent 802.11b clients from associating.
|
|
•
|
5GHz 802.11n Only—Allows only 802.11n clients access to your wireless network. 802.11a/b/g clients are unable to connect under this restricted radio mode.
|
|
•
|
5GHz 802.11n/a Mixed—Supports 802.11n and 802.11a clients simultaneously. If your wireless network comprises both types of clients, select this mode.
|
|
•
|
5GHz 802.11a Only—Select this mode if only 802.11a clients access your wireless network.
|
|
NOTE: The available 801.11n Radio Settings options change depending on the mode selected. If the wireless radio is configured for a mode that:
|
|
3
|
If you selected a mode that supports 802.11a, optionally check the Enable DFS Channels checkbox. The Enable Dynamic Frequency Selection (DFS) option allows wireless devices to share spectrum with existing radar systems in the 5 GHz band.
|
|
4
|
In the SSID field, enter a recognizable string for the SSID of each SonicPoint using this profile. This is the name that will appear in clients’ lists of available wireless connections.
|
|
•
|
|
•
|
Auto - Allows the appliance to automatically detect and set the optimal channel for wireless operation based on signal strength and integrity. This is the default setting. Use Auto unless you have a specific reason to use or avoid specific channels.
|
|
7
|
For 802.11n only: from the Radio Band drop-down menu, select the band for the 802.11n radio:
|
|
•
|
Auto - Allows the appliance to automatically detect and set the optimal channel for wireless operation based on signal strength and integrity. Both the Primary Channel and Secondary Channel are set to Auto also. This is the default setting.
|
|
•
|
Standard - 20 MHz Channel—Specifies that the 802.11n radio will use only the standard 20 MHz channel. When this option is selected, the Standard Channel drop-down menu is displayed instead of the Primary Channel and Secondary Channel options.
|
|
•
|
Standard Channel—This drop-down menu only displays when the 20 MHz channel is selected. By default, this is set to Auto, which allows the appliance to set the optimal channel based on signal strength and integrity.
|
Optionally, you can select a single channel within the range of your regulatory domain. Selecting a specific a channel can also help with avoiding interference with other wireless networks in the area. The available channels are the same as for 802.11g in Step 5.
|
•
|
Wide - 40 MHz Channel—Specifies that the 802.11n radio will use only the wide 40 MHz channel. When this option is selected, the Primary Channel and Secondary Channel drop-down menus are active:
|
|
•
|
Primary Channel—By default this is set to Auto. Optionally, you can specify a specific primary channel. The available channels are the same as for 802.11a in Step 5.
|
|
•
|
Secondary Channel—The configuration of this drop-down menu is controlled by your selection for the primary channel:
|
|
•
|
|
8
|
Enable Short Guard Interval—Specifies the short guard interval of 400ns (as opposed to the standard guard interval of 800ns).
|
The 802.11n standard specifies two guard intervals: 400ns (short) and 800ns (long).
|
9
|
Enable Aggregation—Enables 802.11n frame aggregation, which combines multiple data frames in a single transmission to reduce overhead and increase throughput.
|
Ensure the wireless client also can support aggregation to avoid compatibility issues.
|
TIP: The Enable Short Guard Interval and Enable Aggregation options can slightly improve throughput. They both function best in optimum network conditions where users have strong signals with little interference. In networks that experience less than optimum conditions (for example, interference, weak signals), these options may introduce transmission errors that eliminate any efficiency gains in throughput.
|
|
10
|
The Enable MIMO option enables/disables MIMO (multiple-input multiple output). Enabling this option increases 802.11n throughput by using multiple-input/multiple-output antennas. This option is enabled by default for all 802.11n modes and is dimmed to ensure it is not disabled. The option is activated and selected by default if 5GHZ 802.11a Only or 2.4GHz 802.11g Only mode is selected. Ensure the wireless client also can support these antennas to avoid compatibility issues. If the 802.11a or 502.11g client cannot support these antennas, disable the option by deselecting it.
|
|
NOTE: If a VAP was selected in the 802.11n Radio Virtual AP Group drop-down menu on the Settings tab, this section is not available. Instead, the Virtual Access Point Encryption Settings section is displayed. Go to Virtual Access Point Encryption Settings Section.
The options change depending on the authentication type you select. |
|
1
|
Select the method of authentication for your wireless network from the Authentication Type drop-down menu:
|
|
•
|
WEP - Open System – All options are dimmed; go to ACL Enforcement section.
|
|
NOTE: For WEP - Both (Open System & Shared Key) and WEP - Shared Key, go to WEP Configuration section.
|
|
•
|
|
•
|
WEP (Wired Equivalent Privacy) is a standard for Wi-Fi wireless network security.
|
1
|
Select the size of the encryption key from the WEP Key Mode drop-down menu:
|
|
•
|
None – default for WEP - Both (Open System & Shared Key). If selected, the rest of the options in this section remain dimmed; go to ACL Enforcement section
|
|
•
|
|
•
|
|
•
|
152 bit (default for WEP - Shared Key)
|
|
2
|
From the Default Key drop-down menu, select the default key, which will be tried first when trying to authenticate a user:
|
|
•
|
Key 1 (default)
|
|
•
|
|
•
|
|
•
|
|
3
|
From the Key Entry drop-down menu, select whether the key is:
|
|
•
|
Alphanumeric (default)
|
|
4
|
In the Key 1 - Key 4 fields, enter up to four possible WEP encryptions keys to be used when transferring encrypted wireless traffic. Enter the most likely to be used in the field you selected as the default key.
|
|
•
|
Key 1: First static WEP key associated with the key index.
|
|
•
|
Key 2: Second static WEP key associated with the key index.
|
|
•
|
Key 3: Third static WEP key associated with the key index.
|
|
•
|
Key 4: Fourth static WEP key associated with the key index.
|
|
1
|
From the Cipher Type drop-down menu, select the cipher to encrypt your wireless data.
|
|
•
|
AES (newer, more secure; default): AES (Advanced Encryption Standard) is a set of ciphers designed to prevent attacks on wireless networks. AES is available in block ciphers of either 128, 192 or 256 bits depending on the hardware you intend to use with it. In the networking field, AES is considered to be among the most secure of all commonly installed encryption packages.
|
|
•
|
TKIP (older, more compatible): TKIP (Temporary Key Integrity Protocol) is not actually a cipher, but a set of security algorithms meant to improve the overall safety of WEP (wired equivalent privacy networks). WEP is widely known to have a host of serious security vulnerabilities. TKIP adds a few extra layers of protection to WEP.
|
|
•
|
Auto: the appliance chooses the cipher type automatically.
|
|
2
|
In the Group Key Interval field, enter the time period for which a Group Key is valid, that is, the time interval before the encryption key is changed automatically for added security. The default value is 86400 seconds (24 hours). Setting too low of a value can cause connection issues.
|
|
4
|
For PSK authentication types only, enter a passphrase in the Passphrase field. This is the shared passphrase your network users must enter to gain network access when they connect with PSK-based authentication.
|
|
NOTE: This option will be displayed only if you selected WPA-PSK, WPA2-PSK, or WPA2‑AUTO‑PSK for your authentication type.
|
|
NOTE: This section displays only if you selected WPA-EAP, WPA2-EAP, or WPA2-AUTO-EAP for your authentication type.
|
|
1
|
Click the Configure button in the Radius Server Settings section. The SonicPoint Radius Server Settings dialog displays.
|
|
2
|
In the Radius Server Retries field, enter the number retries allowed for the Radius server.
|
|
3
|
In the Retry Interval (seconds) field enter the time, in seconds, between retries.
|
|
NOTE: This section displays only if a VAP was selected from the 802.11n Radio Virtual AP Group drop-down menu in the Virtual Access Point Settings section of the Settings tab.
|
|
1
|
|
2
|
From the Key Entry Method radio buttons, select whether the key is:
|
|
•
|
Alphanumeric (default)
|
|
3
|
From the Default Key radio buttons, select the default key, which will be tried first when trying to authenticate a user:
|
|
•
|
Key 1 (default)
|
|
•
|
|
•
|
|
•
|
|
4
|
In the Key 1 - Key 4 fields, enter up to four possible WEP encryptions keys to be used when transferring encrypted wireless traffic. Enter the most likely to be used in the field you selected as the default key.
|
|
•
|
Key 1: First static WEP key associated with the key index.
|
|
•
|
Key 2: Second static WEP key associated with the key index.
|
|
•
|
Key 3: Third static WEP key associated with the key index.
|
|
•
|
Key 4: Fourth static WEP key associated with the key index.
|
|
5
|
From the Key Type drop-down menus, select the size of each key:
|
|
•
|
None (default)
|
|
•
|
|
•
|
|
•
|
|
1
|
Select Enable Mac Filter List to enforce Access Control by allowing or denying traffic from specific devices.
|
|
2
|
From the Allow List drop-down menu, select a MAC address group to automatically allow traffic from all devices with a MAC address in the group.
|
|
•
|
Create new Mac Address Object Group… – the Add Address Object Group dialog displays
|
|
3
|
From the Deny List drop-down menu, select a MAC address group to automatically deny traffic from all devices with a MAC address in the group.
|
|
4
|
Select Enable MIC Failure ACL Blacklist to detect WPA TKIP MIC failure floods and automatically place the problematic wireless station(s) into a blacklist to stop the attack. As wireless clients generate the TKIP countermeasures, they will also be automatically moved into blacklist, so the other wireless stations within the same wireless LAN network will not be affected.
|
|
NOTE: It is recommended that the Allow List be set to All MAC Addresses and the Deny List be set to Default SonicPoint ACL Deny Group.
|
|
5
|
Enter the maximum number of MIC failures per minute in the MIC Failure Frequency Threshold field; default is 3.
|
|
NOTE: If a VAP was selected in the 802.11n Radio Virtual AP Group drop-down menu on the Settings tab, this section is not available. Go to Advanced Tab.
|
|
1
|
Select Enable Remote MAC Access Control to enforce 802.11n wireless access control based on MAC-based authentication policy in a remote Radius server.
|
|
2
|
In the Advanced tab, configure the performance settings for the 802.11n radio. For most 802.11n advanced options, the default settings give optimum performance.
|
1
|
Select Hide SSID in Beacon to have the SSID send null SSID beacons in place of advertising the wireless SSID name. Sending null SSID beacons forces wireless clients to know the SSID before connecting. By default, this option is unchecked.
|
|
2
|
From the Schedule IDS Scan drop-down menu, select a schedule for the IDS (Intrusion Detection Service) scan. Select a time when there are fewer demands on the wireless network to minimize the inconvenience of dropped wireless connections. You can create your own schedule by selecting Create new schedule or disable the feature by selecting Disabled, the default.
|
|
3
|
From the Data Rate drop-down menu, select the speed at which the data is transmitted and received. Best (default) automatically selects the best rate available in your area given interference and other factors. Or you can manually select a data rate, from a minimum of 1 Mbps to a maximum of 54 Mbps.
|
|
4
|
From the Transmit Power drop-down menu, select the transmission power. Transmission power effects the range of the SonicPoint.
|
|
•
|
Full Power (default)
|
|
•
|
|
5
|
From the Antenna Diversity drop-down menu, select the method that determines which antenna the SonicPoint uses to send and receive data.
|
|
•
|
Best: This is the default setting. When Best is selected, the SonicPoint automatically selects the antenna with the strongest, clearest signal. In most cases, Best is the optimal setting.
|
|
•
|
1: Select 1 to restrict the SonicPoint to use antenna 1 only. Facing the rear of the SonicPoint, antenna 1 is on the left, closest to the power supply.
|
|
•
|
2: Select 2 to restrict the SonicPoint to use antenna 2 only. Facing the rear of the SonicPoint, antenna 2 is on the right, closest to the console port.
|
|
6
|
In the Beacon Interval (milliseconds) field, enter the number of milliseconds between sending wireless SSID beacons. The minimum interval is 100 milliseconds, the maximum is 1000 milliseconds, and the default is 100 milliseconds.
|
|
7
|
In the DTIM Interval field, enter the DTIM interval in milliseconds. The minimum number of frames is 1, the maximum is 255, and the default is 1.
|
|
8
|
In the Fragmentation Threshold (bytes) field, enter the number of bytes of fragmented data you want the network to allow. Fragment wireless frames to increase reliability and throughput in areas with RF interference or poor wireless coverage. Lower threshold numbers produce more fragments. The minimum threshold is 256 bytes, the maximum is 2346 bytes, and the default is 2346 bytes.
|
|
9
|
In the RTS Threshold (bytes) field, enter the threshold for a packet size, in bytes, at which a request to send (RTS) will be sent before packet transmission. Sending an RTS ensures that wireless collisions do not take place in situations where clients are in range of the same access point, but may not be in range of each other. The minimum threshold is 256 bytes, the maximum is 2346 bytes, and the default is 2346 byes.
|
|
10
|
In the Maximum Client Associations field, enter the maximum number of clients you want each SonicPoint using this profile to support on this radio at one time. The minimum number of clients is 1, the maximum number is 128, and the default number is 32.
|
|
11
|
In the Station Inactivity Timeout (seconds) field, enter the maximum length of wireless client inactivity before Access Points age out the wireless client, in seconds. The minimum period is 60 seconds, the maximum is 36000 seconds, and the default is 300 seconds.
|
|
12
|
From the Preamble Length drop-down menu, select the length of the preamble--the initial wireless communication sent when associating with a wireless host: Long (default) or Short.
|
|
13
|
From the Protection Mode drop-down menu, select the CTS or RTS protection: None (default), Always, or Auto.
|
|
14
|
From the Protection Rate drop-down menu, select the speed for the CTS or RTS protection:
|
|
•
|
1 Mbps (default)
|
|
•
|
|
•
|
|
•
|
|
15
|
From the Protection Type drop-down menu, select the type of protection, CTS-only (default) or RTS‑CTS.
|
|
16
|
From the WMM (Wi-Fi Multimedia) drop-down menu, select whether a WMM profile is to be associated with this profile:
|
|
•
|
Disabled (default)
|
|
•
|
Create new WMM profile. If you select Create new WMM profile, the Add Wlan WMM Profile dialog displays. For information about configuring a WMM profile, see Configuring Wi-Fi Multimedia Parameters.
|
|
17
|
Select Enable Short Slot Time to allow clients to disassociate and reassociate more quickly. Specifying this option increases throughput on the 802.11n/g wireless band by shortening the time an access point waits before relaying packets to the LAN. By default, this option is not selected.
|
|
18
|
Select Does not allow Only 802.11b Clients to Connect if you are using Turbo G mode and, therefore, are not allowing 802.11b clients to connect. Specifying this option limits wireless connections to 802.11g clients only. By default, this option is not selected.
|
In the Sensor tab, you enable or disable Wireless Intrusion Detection and Prevention (WIDP) mode.
|
1
|
Select Enable WIDF sensor to have the SonicPoint N operate as a dedicated WIDP sensor.
|
|
2
|
From the drop-down menu, select the schedule for when the SonicPoint N operates as a WIDP sensor or select Create new schedule… to specify a different time; default is Always on.
|