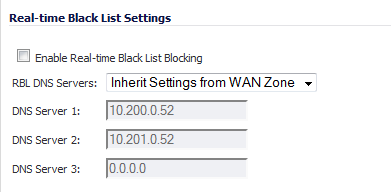
When Enable Real-time Black List Blocking is enabled in the Real-time Black List Settings section on the RBL Filter page, inbound connections from hosts on the WAN or outbound connections to hosts on the WAN are checked against each enabled RBL service with a DNS request to the DNS servers configured under RBL DNS Servers.
The RBL DNS Servers menu allows you to specify the DNS servers. You can choose Inherit Settings from WAN Zone or Specify DNS Servers Manually. If you select Specify DNS Servers Manually, enter the DNS server addresses in the DNS Server fields.
When you have finished, click Accept.
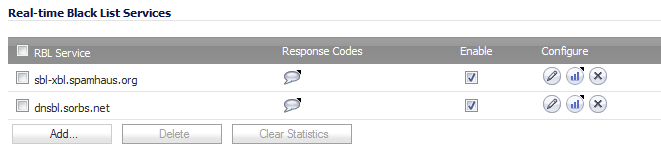
You can add additional RBL services in the Real-time Black List Services section.
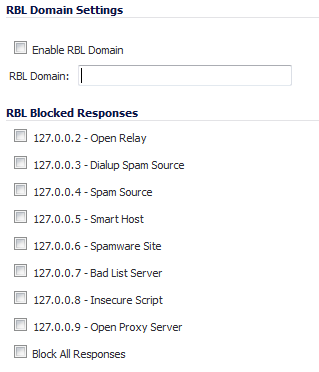
To add an RBL service, click the Add button. In the Add RBL Domain window, you specify the RBL domain to be queried, enable it for use, and specify its expected response codes. Most RBL services list the responses they provide on their Web site, although selecting Block All Responses is generally acceptable.
Statistics are maintained for each RBL Service in the RBL Service table, and can be viewed with a mouseover of the (statistics) icon to the right on the service entry.
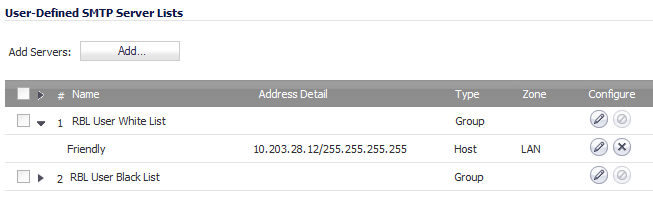
The User Defined SMTP Server Lists section allows for Address Objects to be used to construct a white-list (explicit allow) or black-list (explicit deny) of SMTP servers. Entries in this list will bypass the RBL querying procedure.
|
1
|
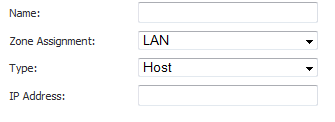
Create an Address Object for the server using the Add Servers: Add… button. the Add Address Object window appears.
|
|
3
|
Click OK. The Address Object will be added to the RBL User White List in the User-Defined SMTP Server Lists table.
|
|
4
|
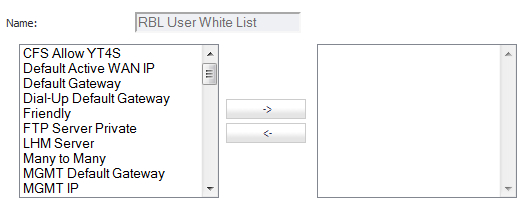
Click the edit icon in the Configure column of the RBL User White List row. The Edit Address Object window displays.
|
|
6
|
Click OK.
|
|
1
|
Click the Edit icon in the Configure column of the RBL User Black List row. The Edit Address Object window displays.
|
|
3
|
Click OK.
|
The System > Diagnostics page also provides a Real-time Black List Lookup feature that allows for SMTP IP addresses (or RBL services, or DNS servers) to be specifically tested.