Configuring SSO is a process that includes installing and configuring the SonicWALL SSO Agent and/or the SonicWALL Terminal Services Agent (TSA), and configuring a firewall running SonicOS to use the SSO Agent or TSA. For an introduction to SonicWALL SSO, see Single Sign-On Overview .
|
•
|
|
•
|
To install the SonicWALL SSO Agent, see the procedure in the Dell SonicWALL Directory Services Connector Administration Guide. You can download this guide from mysonicwall.com.
SonicWALL TSA is available for download without charge from MySonicWALL.
|
2
|
|
3
|
Select Terminal Services Agent in the Software Type drop-down menu. The available versions of TSA are displayed.
|
|
6
|
On the Welcome page, click Next to continue.
|
|
7
|
The License Agreement displays. Select I accept the terms in the License Agreement and click Next to continue.
|
|
8
|
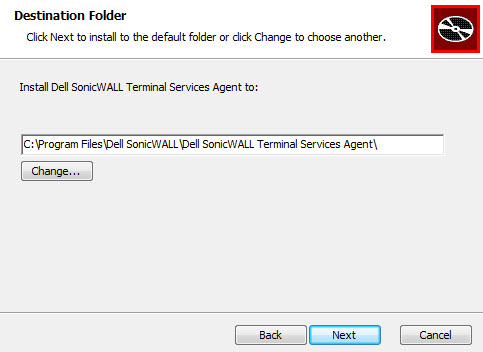
On the Destination Folder window, select the destination folder. To use the default folder, C:\Program Files\SonicWALL\SonicWALL Terminal Services Agent\, click Next. To specify a custom location, click Change, select the folder, and click Next.
|
|
•
|
Use TDI based Windows driver - required on Windows 2003 servers
|
|
•
|
Use WFP based Windows driver - recommended for Windows 2008 R2 and later
|
|
10
|
On the Ready to install SonicWALL Terminal Services Agent window, click Install to start the installation.
|
|
11
|
|
12
|
When installation is complete, click Close to exit the installer.
|
|
13
|
You must restart your system before starting the SonicWALL Terminal Services Agent. To restart immediately, click Yes in the dialog box. To restart later, click No.
|
|
1
|
Launch the SonicWALL Configuration Tool by double-clicking the desktop shortcut or by navigating to Start > All Programs > SonicWALL > SonicWALL Directory Connector > SonicWALL Configuration Tool.
|
|
NOTE: If the IP address for a default firewall was not configured, or if it was configured incorrectly, a pop up will display. Click Yes to use the default IP address (192.168.168.168) or click No to use the current configuration.
|
If you clicked Yes, the message Successfully restored the old configuration will display. Click OK.
If you clicked No, or if you clicked Yes but the default configuration is incorrect, the message SonicWALL SSO Agent service is not running. Please check the configuration and start the service. will display. Click OK.
If the message SonicWALL SSO Agent service is not running. Please check the configuration and start the service displays, the SSO Agent service will be disabled by default. To enable the service, expand the SonicWALL Directory Connector Configuration Tool in the left navigation panel by clicking the + icon, highlight the SonicWALL SSO Agent underneath it, and click the Start icon.
|
2
|
In the left-hand navigation panel, expand the SonicWALL Directory Connector Configuration Tool by clicking the + icon. Right click the SonicWALL SSO Agent and select Properties.
|
|
3
|
From the Logging Level drop-down menu, select the level of events to be logged in the Windows Event Log. The default logging level is 1. Select one of the following levels:
|
|
•
|
Logging Level 0 - Only critical events are logged.
|
|
•
|
Logging Level 1 - Critical and significantly severe events are logged.
|
|
•
|
Logging Level 2 - All requests from the appliance are logged, using the debug level of severity.
|
|
4
|
In the Refresh Time field, enter the frequency, in seconds, that the SSO Agent will refresh user log in status. The default is 60 seconds.
|
|
5
|
From the Query Source drop-down menu, select the protocol that the SSO Agent will use to communicate with workstations, either NETAPI or WMI.
|
|
6
|
In the Configuration File field, enter the path for the configuration file. The default path is C:\Program Files\SonicWALL\DCON\SSO\CIAConfig.xml.
|
|
7
|
Click Accept.
|
|
8
|
Click OK.
|
|
2
|
Expand the SonicWALL Directory Connector and SonicWALL SSO Agent trees in the left column by clicking the + button. Right click SonicWALL Appliance and select Add.
|
|
3
|
Enter the appliance IP address for your Dell SonicWALL network security appliance in the Appliance IP field. Enter the port for the same appliance in the Appliance Port field. The default port is 2258. Give your appliance a friendly name in the Friendly Name field. Enter a shared key in the Shared Key field or click Generate Key to generate a shared key.
|
Your appliance displays in the left-hand navigation panel under the Dell SonicWALL Appliance tree.
You can edit all settings on firewalls previously added in SonicWALL SSO Agent, including IP address, port number, friendly name, and shared key. To edit a firewall in SonicWALL SSO Agent, select the appliance from the left-hand navigation panel and click the Edit icon above the left-hand navigation panel. You can also click the Edit tab at the bottom of the right-hand dialog.
To delete a firewall you previously added in SonicWALL SSO Agent, select the appliance from the left-hand navigation panel and click the Delete icon above the left-hand navigation panel.
You can start, stop, and pause SonicWALL SSO Agent services to firewalls. To pause services for an appliance, select the appliance from the left-hand navigation panel and click the Pause icon. To stop services for an appliance, select the appliance from the left-hand navigation panel and click the Stop icon. To resume services, click the Start icon.
|
1
|
|
2
|
|
3
|
Type the communication port into the Appliance Port field. The default port is 2259, but a custom port can be used instead. This port must be open on the Windows Server system.
|
|
4
|
Type the encryption key into the Shared Secret field. Select the Show Secret checkbox to view the characters and verify correctness. The same shared secret must be configured on the firewall.
|
|
5
|
In most cases, type 0.0.0.0 into the Bind IP field. However, if the terminal server has multiple network interfaces (multi-homed) and you want the agent to send notifications to the firewall(s) on a specific one, then enter the interface's IP address here. In that case, enter the same IP address that is configured on the firewall for the agent.
|
|
6
|
In the Timeout drop-down list, select the number of seconds that the agent will wait for a reply from the appliance before retrying the notification. The range is 5 to 10 seconds, and the default is 5 seconds.
|
|
7
|
In the Retries drop-down list, select the number of times the agent will retry sending a notification to the appliance when it does not receive a reply. The range is 3 to 10 retries, and the default is 5.
|
|
8
|
To enable full details in log messages, select the Enable Verbose Log checkbox. Do this only to provide extra, detailed information in a trouble shooting report. Avoid leaving this enabled at other times because it may impact performance.
|
|
9
|
Click Apply. A dialog box indicates that the SonicWALL TSA service has restarted with the new settings.
|
|
1
|
|
2
|
Click the Reports tab.
|
|
•
|
Save it as a text file, click Save As.
|
|
4
|
When finished, click Close.
|
|
1
|
|
2
|
Click the About tab.
|
|
3
|
Click Close.
|
|
•
|
|
•
|
The Maximum requests to send at a time setting is available on the Advanced tab of the SSO agent configuration.
This setting controls the maximum number of requests that can be sent from the appliance to the agent at the same time. The agent processes multiple requests concurrently, spawning a separate thread in the PC to handle each. Sending too many requests at a time can overload the PC on which the agent is running. If the number of requests to send exceeds the maximum, then some are placed on an internal “ring buffer” queue (see Using the Single Sign-On Statistics in the TSR and Viewing SSO Mouseover Statistics and Tooltips ). Requests waiting on the ring buffer for too long could lead to slow response times in SSO authentication.
The SSO Configuration page provides mouseover statistics about each agent, and mouseover tooltips for many fields. On the Settings tab, a green LED-style icon next to an agent indicates that the agent is up and running. A red LED icon indicates that the agent is down.
To view the statistics for a particular agent, hover your mouse pointer over the Statistics icon to the right of the SSO agent. This also works for individual TSAs on the Terminal Services tab.
To view the statistics for all SSO activity on the appliance, hover your mouse pointer over the Statistics icon at the bottom of the table, in the same row as the Add button.
To close the statistics display, click close.
To clear all the displayed values, click Click to reset.
A rich set of SSO performance and error statistics is included in the trouble shooting report (TSR). These can be used to gauge how well SSO is performing in your installation. Download the TSR on the System > Diagnostics page and search for the title “SSO operation statistics”. The following are the counters to look at in particular:
|
1
|
Under SSO ring buffer statistics, look at Ring buffer overflows and Maximum time spent on ring. If the latter approaches or exceeds the polling rate, or if any ring buffer overflows are shown, then requests are not being sent to the agent quickly enough. Also, if the Current requests waiting on ring is constantly increasing, that would indicate the same. This means that the Maximum requests to send at a time value should be increased to send requests faster. However, that will increase the load on the agent, and if the agent cannot handle the additional load, then problems will result, in which case it may be necessary to consider moving the agent to a more powerful PC or adding additional agents.
|
|
2
|
Under SSO operation statistics, look at Failed user id attempts with time outs and Failed user id attempts with other errors. These should be zero or close to it – significant failures shown here indicate a problem with the agent, possibly because it cannot keep up with the number of user authentications being attempted.
|
|
3
|
Also under SSO operation statistics, look at the Total users polled in periodic polling, User polling failures with time outs, and User polling failures with other errors. Seeing some timeouts and errors here is acceptable and probably to be expected, and occasional polling failures will not cause problems. However, the error rate should be low (an error rate of about 0.1% or less should be acceptable). Again, a high failure rate here would indicate a problem with the agent, as above.
|
|
4
|
Under SSO agent statistics, look at the Avg user ID request time and Avg poll per-user resp time. These should be in the region of a few seconds or less – something longer indicates possible problems on the network. Note, however, that errors caused by attempting to authenticate traffic from non-Windows PCs via SSO (which can take a significantly long time) can skew the Avg user ID request time value, so if this is high but Avg poll per-user resp time looks correct, that would indicate the agent is probably experiencing large numbers of errors, likely due to attempting to authenticate non-Windows devices – see below, Step 6.
|
|
5
|
If using multiple agents, then also under SSO agent statistics look at the error and timeout rates reported for the different agents, and also their response times. Significant differences between agents could indicate a problem specific to one agent that could be addressed by upgrading or changing settings for that agent in particular.
|
|
•
|
If using Content Filtering, select that address object with the Bypass the Single Sign On process for traffic from setting on the Enforcement tab of the SSO configuration dialog.
|
|
•
|
To identify the IP addresses concerned, look in the TSR and search for “IP addresses held from SSO attempts”. This lists SSO failures in the preceding period set by the Hold time after failure setting.
To limit the rate of errors due to this you can also extend the Hold time after failure setting on the Users tab.
If the above statistics indicate a possible problem with the agent, a good next step would be to run Windows Task Manager on the PC on which the agent is running and look at the CPU usage on the Performance tab, plus the CPU usage by the “CIAService.exe” process on the Processes tab. If the latter is using a large percentage of the CPU time and the CPU usage is spiking close to 100%, this is an indication that the agent is getting overloaded. To try to reduce the loading you can decrease the Maximum requests to send at a time setting; see Using the Single Sign-On Statistics in the TSR above, Step 1.
|
•
|
Consider reducing the polling rate configured on the Users tab by increasing the poll time. This will reduce the load on the agent, at the cost of detecting logouts less quickly. Note that in an environment with shared PCs, it is probably best to keep the poll interval as short as possible to avoid problems that could result from not detecting logouts when different users use the same PC, such as the initial traffic from the second user of a PC possibly being logged as sent by the previous user.
|
Enabling SonicWALL SSO affects policies on the Firewall > Access Rules page of the SonicOS management interface. Rules set under Firewall > Access Rules are checked against the user group memberships returned from a SSO LDAP query, and are applied automatically.
When a SonicWALL SSO agent or TSA is configured in the SonicOS management interface, a Firewall access rule and corresponding NAT policy are created to allow the replies from the agent into the LAN. These rules use either a SonicWALL SSO Agents or SonicWALL Terminal Services Agents address group object, which has a member address object for each configured agent. The member address objects are automatically added to and deleted from the group object as agents are added or deleted. The member address objects are also updated automatically as an agent’s IP address changes, including when an IP address is resolved via DNS (where an agent is given by DNS name).
If SonicWALL SSO agents or TSAs are configured in different zones, the Firewall access rule and NAT policy are added to each applicable zone. The same SonicWALL SSO Agents or SonicWALL Terminal Services Agents address group is used in each zone.
Samba is a software package used by Linux/Unix or Mac machines to give their users access to resources in a Windows domain (via Samba’s smbclient utility) and/or to give Windows domain users access to resources on the Linux or Mac machine (via a Samba server).
|
•
|
To use SonicWALL SSO with Linux/Mac users, the SonicWALL SSO Agent must be configured to use NetAPI rather than WMI to get the user login information from the user's machine.
|
These and other configuration details are described in the Using Single Sign-on with Samba technote.
SonicWALL SSO is supported by Samba 3.5 or newer.
To avoid these problems, the Don't invoke Single Sign On to Authenticate Users checkbox is available when configuring Firewall access rules by clicking Add on the Firewall > Access Rules page (with View Style set to All Rules).
This checkbox is visible only when SonicWALL SSO is enabled and when the Users Allowed field on the Add Rule dialog is not set to All. If this checkbox is selected, SSO is not attempted for traffic that matches the rule, and unauthenticated HTTP connections that match it are directed straight to the login page. Typically, the Source field would be set to an address object containing the IP addresses of Mac and Linux systems.
|
NOTE: Do not select the Don't invoke Single Sign On to Authenticate Users option for use with devices that are allowed to bypass the user authentication process entirely. Any devices that may be affected by an access rule when this option is enabled must be capable of logging in manually. A separate access rule should be added for such devices, with Users Allowed set to All.
|
Firewall access rules provide the administrator with the ability to control user access. Rules set under Firewall > Access Rules are checked against the user group memberships returned from a SSO LDAP query, and are applied automatically. Access rules are network management tools that allow you to define inbound and outbound access policy, configure user authentication, and enable remote management of the firewall. The SonicOS Firewall > Access Rules page provides a sortable access rule management interface.
For detailed information about access rules, see Firewall > Access Rules .
|
•
|
HTTP login from a terminal server is allowed only for the built-in admin account and other user accounts with administrator privileges. An attempt to log in with a non-administrative account will fail with the error, Not allowed from this location.
|
|
•
|
On successful HTTP login, an administrative user is taken straight to the management interface. The small User Login Status page is not displayed.
|
|
•
|
Only one user at a time can manage the appliance from a given terminal server. If two users attempt to do so simultaneously, the most recently logged in user takes precedence, and the other user will see the error, This is not the browser most recently used to log in.
|
|
•
|
On a failure to identify a user due to communication problems with the TSA, an HTTP browser session is not redirected to the Web login page (as happens on a failure in the SSO case). Instead, it goes to a new page with the message, The destination that you were trying to reach is temporarily unavailable due to network problems.
|
This section provides information to help you manage SSO on your firewall:
The Users > Status page displays Active User Sessions on the firewall. The table lists User Name, IP Address, Session Time, Time Remaining, Inactivity Remaining, Settings, and Logout. For users authenticated using SonicWALL SSO Agent, the message Auth. by SSO Agent displays. To logout a user, click the Delete icon next to the user’s entry.
|
NOTE: Changes in a user’s settings, configured under Users > Settings, is not reflected during that user’s current session; you must manually log the user out for changes to take effect. The user is transparently logged in again, with the changes reflected.
|
The Users > Settings page provides configuration options for user session settings, global user settings, and acceptable use policy settings, in addition to SSO and other user login settings.
The Enable login session limit and corresponding Login session limit (minutes) settings under User Session Settings apply to users logged in using SSO. SSO users are logged out according to session limit settings, but will be automatically and transparently logged back in when they send further traffic.
Changes applied in the Users > Settings page during an active SSO session are not reflected during that session.
The Packet Monitor feature available on System > Packet Monitor provides two checkboxes to enable capture of decrypted messages to and from the SSO agent, and decrypted LDAP over TLS (LDAPS) messages.
|
1
|
Click the Configuration button in the System > Packet Monitor page. The Packet Monitor Configuration dialog displays.
|
|
2
|
Click the Advanced Monitor Filter tab.
|
|
3
|
Select the Monitor intermediate Packets checkbox.
|
|
4
|
Select the Monitor intermediate decrypted Single Sign On agent messages checkbox.
|
|
5
|
Click OK.
|
The packets are marked with (sso) in the ingress/egress interface field. They have dummy Ethernet, TCP, and IP headers, so some values in these fields may not be correct.
Captured SSO messages are displayed fully decoded on the System > Packet Monitor page in the Captured Packets table and the Packet Detail and Hex Dump sections.
|
1
|
|
2
|
Click the Advanced Monitor Filter tab
|
|
3
|
Select the Monitor intermediate Packets checkbox.
|
|
4
|
Select the Monitor intermediate decrypted LDAP over TLS packets checkbox.
|
|
5
|
Click OK.
|
The packets are marked with (ldp) in the ingress/egress interface field. They have dummy Ethernet, TCP, and IP headers, so some values in these fields may not be correct. The LDAP server port is set to 389 so an external capture analysis program (such as Wireshark) knows to decode these packets as LDAP. Passwords in captured LDAP bind requests are masked. The LDAP messages are not decoded in the Packet Monitor display, but the capture can be exported and displayed in WireShark to view them decoded.