|
•
|
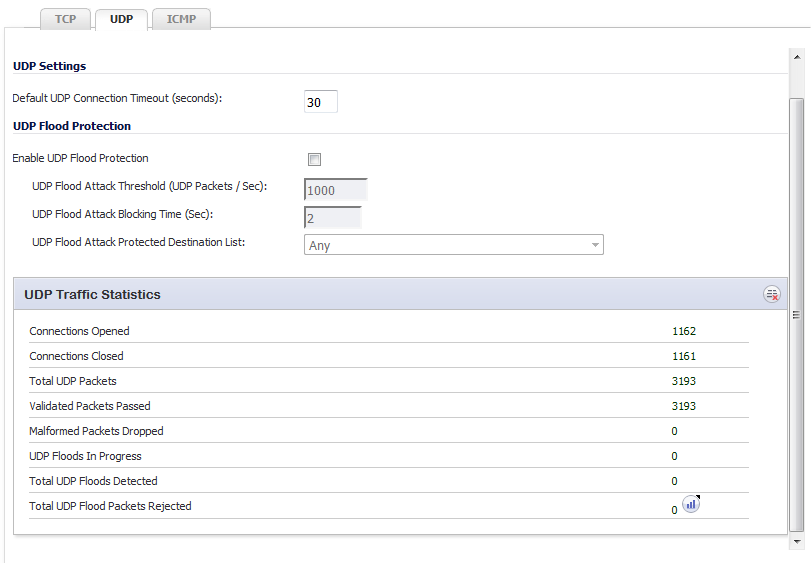
Default UDP Connection Timeout (seconds) - The number of seconds of idle time you want to allow before UDP connections time out. This value is overridden by the UDP Connection timeout you set for individual rules.
|
The following settings configure UDP Flood Protection:
|
•
|
Enable UDP Flood Protection – Enables UDP Flood Protection. This option is not selected by default.
|
|
NOTE: Enable UDP Flood Protection must be enabled to activate the other UDP Flood Protection options.
|
|
•
|
UDP Flood Attack Threshold (UDP Packets / Sec) – The maximum number of UDP packets allowed per second to be sent to a host, range, or subnet that triggers UDP Flood Protection. Exceeding this threshold triggers ICMP Flood Protection.The minimum value is 50, the maximum value is 1000000, and the default value is 1000.
|
|
•
|
UDP Flood Attack Blocking Time (Sec) – After the appliance detects the rate of UDP packets exceeding the attack threshold for this duration of time, UDP Flood Protection is activated and the appliance begins dropping subsequent UDP packets. The minimum time is 1 second, the maximum time is 120 seconds, and the default time is 2 seconds.
|
|
•
|
UDP Flood Attack Protected Destination List – The destination address object or address group that will be protected from UDP Flood Attack. The default value is Any.
|
|
TIP: Select Any to apply the Attack Threshold to the sum of UDP packets passing through the firewall.
|
The UDP Traffic Statistics table provides statistics as shown in Table 73. To clear and restart the statistics displayed by a table, click the Clear Stats icon for the table.