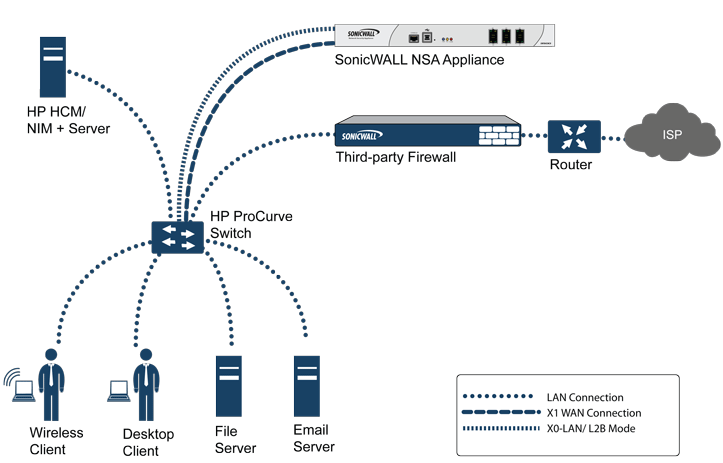
This section provides an example topology that uses SonicWall IPS Sniffer Mode in a Hewlitt Packard ProCurve switching environment. See Sample IPS Sniffer Mode Topology. This scenario relies on the ability of HP’s ProCurve Manager Plus (PCM+) and HP Network Immunity Manager (NIM) server software packages to throttle or close ports from which threats are emanating.
Sample IPS Sniffer Mode Topology
In this deployment the WAN interface and zone are configured for the internal network’s addressing scheme and attached to the internal network. The X2 port is Layer 2 bridged to the LAN port – but it won’t be attached to anything. The X0 LAN port is configured to a second, specially programmed port on the HP ProCurve switch. This special port is set for mirror mode – it forwards all the internal user and server ports to the “sniff” port on the SonicWall. This allows the SonicWall to analyze the entire internal network’s traffic, and if any traffic triggers the firewall signatures it will immediately trap out to the PCM+/NIM server via the X1 WAN interface, which then can take action on the specific port from which the threat is emanating.
To configure this deployment, navigate to the Network > Interfaces page and click on the configure icon for the X2 interface. On the X2 Settings page, set the IP Assignment to ‘Layer 2 Bridged Mode’ and set the Bridged To: interface to ‘X0’. Select the check box for Only sniff traffic on the bridge-pair. Click OK to save and activate the change.
Next, go to the Network > Interfaces page and click on the configure icon for the X1 WAN interface. On the X1 Settings page, assign it a unique IP address for the internal LAN segment of your network – this may sound wrong, but this will actually be the interface from which you manage the appliance, and it is also the interface from which the appliance sends its SNMP traps as well as the interface from which it gets firewall signature updates. Click OK.