|
•
|
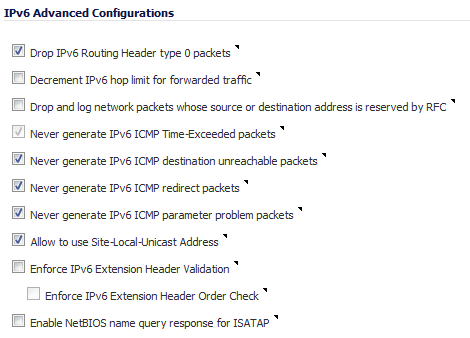
Drop IPv6 Routing Header type 0 packets – Select this to prevent a potential DoS attack that exploits IPv6 Routing Header type 0 (RH0) packets. When this setting is enabled, RH0 packets are dropped unless their destination is the Dell SonicWALL security appliance and their Segments Left value is 0. Segments Left specifies the number of route segments remaining before reaching the final destination. Enabled by default. For more information, see http://tools.ietf.org/html/rfc5095.
|
|
•
|
Decrement IPv6 hop limit for forwarded traffic – Similar to IPv4 TTL, when selected, the packet is dropped when the hop limit has been decremented to 0. Disabled by default.
|
|
•
|
Drop and log network packets whose source or destination address is reserved by RFC – Select this option to reject and log network packets that have a source or destination address of the network packet defined as an address reserved for future definition and use as specified in RFC 4921 for IPv6. Disabled by default.
|
|
•
|
Never generate IPv6 ICMP Time-Exceeded packets – By default, the SonicWALL appliance generates IPv6 ICMP Time-Exceeded Packets that report when the appliance drops packets due to the hop limit decrementing to 0. Select this option to disable this function; the SonicWALL appliance will not generate these packets. This option is selected by default.
|
|
•
|
Never generate IPv6 ICMP destination unreachable packets – By default, the SonicWALL appliance generates IPv6 ICMP destination unreachable packets. Select this option to disable this function; the SonicWALL appliance will not generate these packets. This option is selected by default.
|
|
•
|
Never generate IPv6 ICMP redirect packets – By default, the SonicWALL appliance generates redirect packets. Select this option to disable this function; the SonicWALL appliance will not generate redirect packets. This option is selected by default.
|
|
•
|
Never generate IPv6 ICMP parameter problem packets – By default, the SonicWALL appliance generates IPv6 ICMP parameter problem packets. Select this option to disable this function; the SonicWALL appliance will not generate these packets. This option is selected by default.
|
|
•
|
Allow to use Site-Local-Unicast Address – By default, the SonicWALL appliance allows Site-Local Unicast (SLU) address and this checkbox is selected. As currently defined, SLU addresses are ambiguous and can present multiple sites. The use of SLU addresses may adversely affect network security through leaks, ambiguity, and potential misrouting. To avoid the issue, deselect the checkbox to prevent he appliance from using SLU addresses.
|
|
•
|
Enforce IPv6 Extension Header Validation – Select this option if you want the SonicWALL appliance to check the validity of IPv6 extension headers. By default, this option is disabled.
|
When both this option and the Decrement IPv6 hop limit for forwarded traffic option are selected, the Enforce IPv6 Extension Header Order Check option becomes available. (You may need to refresh the page.)
|
•
|
Enforce IPv6 Extension Header Order Check – Select this option to have the SonicWALL appliance check the order of IPv6 Extension Headers. By default, this option is disabled.
|
|
•
|
Enable NetBIOS name query response for ISATAP – Select this option if you want the SonicWALL appliance to generate a NetBIOS name in response to a broadcast ISATAP query. By default, this option is disabled.
|