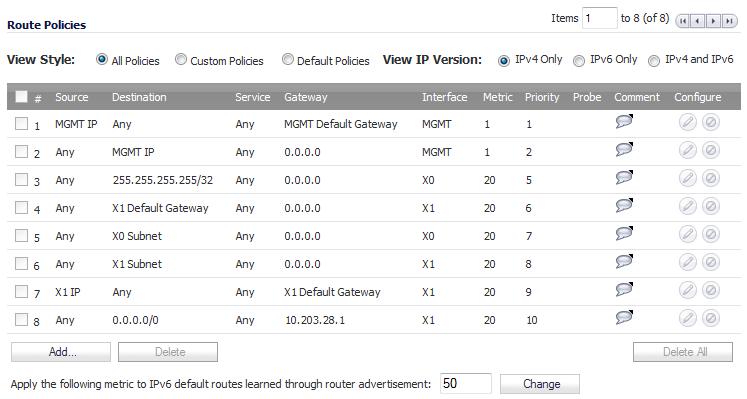
You can change the view your route policies in the Route Policies table by selecting one of the view settings in the View Style menu.
All Policies displays all the routing policies including Custom Policies and Default Policies. Initially, only the Default Policies are displayed in the Route Policies table when you select All Policies from the View Style menu.
The Route Policies table provides easy pagination for viewing a large number of routing policies. You can navigate a large number of routing policies listed in the Route Policies table by using the navigation control bar located at the top right of the Route Policies table. Navigation control bar includes four buttons. The far left button displays the first page of the table. The far right button displays the last page. The inside left and right arrow buttons moved the previous or next page respectively.
You can enter the policy number (the number listed before the policy name in the # Name column) in the Items field to move to a specific routing policy. The default table configuration displays 50 entries per page. You can change this default number of entries for tables on the System > Administration page.
In SonicOS, a static route is configured through a basic route policy.
|
1
|
Scroll to the bottom of the Network > Routing page.
|
|
2
|
|
3
|
From the Source drop-down menu, select the source address object for the static route, or select Create new address object to dynamically create a new address object. The default is Any.
|
|
4
|
|
5
|
From the Service drop-down menu, select a service object. For a generic static route that allows all traffic types, simply select Any (the default).
|
|
6
|
From the Gateway drop-down menu, select the gateway address object to be used for the route. The default is 0.0.0.0.
|
|
7
|
From the Interface drop-down menu, select the interface to be used for the route.
|
|
8
|
Enter the Metric for the route. The default metric for static routes is one (1). For more information on metrics, see Policy Based Routing .
|
|
9
|
(Optional) Enter a Comment for the route. This field allows you to enter a descriptive comment for the new static route policy.
|
|
10
|
(Optional) Select the Disable route when the interface is disconnected checkbox to have the route automatically disabled when the interface is disconnected. This option is selected by default.
|
|
11
|
(Optional) The Allow VPN path to take precedence option allows you to create a backup route for a VPN tunnel. This option is not selected by default.
|
By default, static routes have a metric of 1 and take precedence over VPN traffic. The Allow VPN path to take precedence option gives precedence over the route to VPN traffic to the same destination address object. This results in the following behavior when a VPN tunnel:
|
•
|
Is active: static routes matching the destination address object of the VPN tunnel are automatically disabled if the Allow VPN path to take precedence option is enabled. All traffic is routed over the VPN tunnel to the destination address object.
|
|
•
|
Goes down: static routes matching the destination address object of the VPN tunnel are automatically enabled. All traffic to the destination address object is routed over the static routes.
|
|
12
|
To permit WAN acceleration, select the Permit Acceleration checkbox. This option is not selected by default.
|
|
13
|
The Probe, Disable route when probe succeeds, and Probe default state is UP options configure Probe-Enabled Policy Based Routing. See Probe-Enabled Policy Based Routing Configuration for information on their configuration.
|
|
14
|
Click OK to add the route.
|
|
1
|
In the Add Route Policy dialog, configure the static route as described in Static Route Configuration .
|
|
2
|
In the Probe drop-down menu, select the appropriate Network Monitor object or select Create New Network Monitor object… to dynamically create a new object. For more information, see Network > Network Monitor . The default is None.
|
|
3
|
Typical configurations do not check the Disable route when probe succeeds checkbox, because typically administrators want to disable a route when a probe to the route’s destination fails. This option gives you added flexibility for defining routes and probes.
|
|
4
|
Select the Probe default state is UP to have the route consider the probe to be successful (that is, in the UP state) when the attached Network Monitor policy is in the UNKNOWN state. This is useful to control the probe-based behavior when a unit of a High Availability pair transitions from IDLE to ACTIVE, because this transition sets all Network Monitor policy states to UNKNOWN.
|
|
5
|
The following example walks you through creating a route policy for two simultaneously active WAN interfaces. For this example, a secondary WAN interface needs to be setup on the X3 interface and configured with the settings from your ISP. Next, configure the security appliance for load balancing by checking the Enable Load Balancing on the Network > WAN Failover & LB page. For this example, choose Per Connection Round-Robin as the load balancing method in the Network > WAN Failover & LB page. Click Accept to save your changes on the Network > WAN Failover & LB page.
|
1
|
|
NOTE: Do not enable the Allow VPN path to take precedence option for these routing policies. The Allow VPN path to take precedence option gives precedence over the route to VPN traffic to the same destination address object. This option is used for configuring static routes as backups to VPN tunnels. See Static Route Configuration for more information.
|
|
2
|
Create a routing policy that directs all LAN Subnet sources to Any destinations for HTTP service out of the X1 Default Gateway via the X1 interface :
|
|
a
|
Select these settings from the Source, Destination, Service, Gateway and Interface drop-down menus respectively.
|
|
b
|
|
c
|
|
3
|
Click OK.
|
|
4
|
Create a second routing policy that directs all LAN Subnet sources to Any destinations for Telnet service out of the X3 Default Gateway via the X3 interface:
|
|
a
|
Selecting these settings from the Source, Destination, Service, Gateway and Interface drop-down menus respectively.
|
|
b
|
|
c
|
|
5
|
Click OK.
|
|
1
|
Access the public Web sites http://www.whatismyip.com and http://whatismyip.everdot.org. Both sites display the primary WAN interface’s IP address and not the secondary WAN interface.
|
|
1
|
When logged in, issue the who command. It displays the IP address (or resolved FQDN) of the WAN IP address of the secondary WAN interface and not the primary WAN interface.
|