The SonicWall TSA can be installed on any Windows Server machine with Terminal Services or Citrix installed. The server must belong to a Windows domain that can communicate with the SonicWall security appliance directly using the IP address or using a path, such as VPN. See How SonicWall Terminal Services Agent Works.
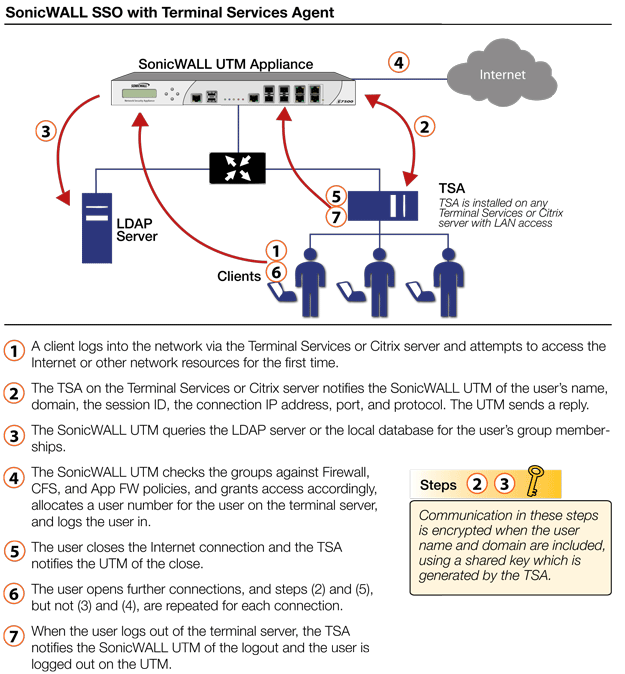
How SonicWall Terminal Services Agent Works
For installation instructions for the SonicWall TSA, refer to the Installing the SonicWall Terminal Services Agent.
To accommodate large installations with thousands of users, SonicWall network security appliances are configurable for operation with multiple terminal services agents (one per terminal server). The number of agents supported depends on the model, as shown in Multiple TSA Support per Model.
The SonicWall network security appliance has the Allow limited access for non-domain users setting for optionally giving limited access to non-domain users (those logged into their local machine and not into the domain), and this works for terminal services users as it does for other SSO users.
If your network includes non-Windows devices or Windows computers with personal firewalls running, check the box next to Probe user for and select the radio button for either NetAPI or WMI depending on which is configured for the SSO Agent. This causes the SonicWall network security appliance to probe for a response on the NetAPI/WMI port before requesting that the SSO Agent identify a user. If no response occurs, these devices will fail SSO immediately. Such devices do not respond to, or may block, the Windows networking messages used by the SSO Agent to identify a user.
To control handling of these non-user connections, an Allow Terminal Server non-user traffic to bypass user authentication in access rules check box is available in the TSA configuration on the appliance. When selected, these connections are allowed. If this check box is not selected, then the services are treated as local users and can be given access by selecting the Allow limited access for non-domain users setting and creating user accounts on the appliance with the corresponding service names.