The X-Forwarded-For HTTP header field was originally introduced by the Squid proxy server, but has now become a de facto standard and is in the process of being standardized by the IETF. It is inserted in the HTTP request sent to the web server from the proxy server and gives the originating IP address of the client from which it received the web request.
Where a connection passes through a chain of proxy servers, X-Forwarded-For can give a comma-separated list of IP addresses with the first being the furthest downstream (that is, the user).
SonicOS can read the user’s IP address from the X-Forwarded-For field when it is present, and to identify the user can use that rather than the actual source IP address of the HTTP request (the latter being the proxy server in this case).
For security reasons, the proxy servers must be specified by the administrator manually.
A hacker could generate HTTP requests with X-Forwarded-For set to anything, and use that to masquerade as a different more privileged user. Hence the appliance must not blindly accept that the given IP address is valid for the user just because an X-Forwarded-For header field is present. Therefore, X-Forwarded-For is ignored unless the HTTP request has come from a known proxy server. For this purpose, a list of the proxy servers is configurable in the SonicOS management interface.
Since a proxy server can pass on X-Forwarded-For IP addresses in a list for purposes of proxy server chaining, the same vulnerability would exist if a proxy server were to pass on a spoofed IP addresses from an X-Forwarded-For field inserted by a hacker. SonicOS has no control over this and so we must rely on the proxy server being properly configured to prevent it.
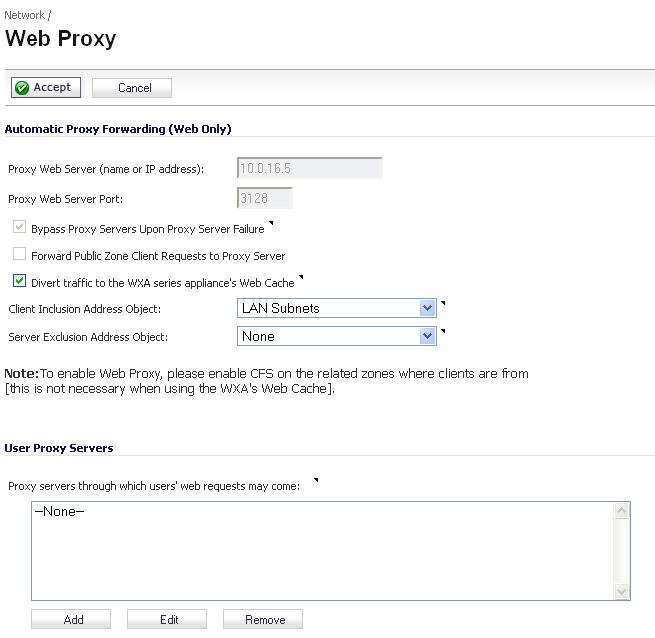
A Web proxy server intercepts HTTP requests and determines if it has stored copies of the requested Web pages. If it does not, the proxy completes the request to the server on the Internet, returning the requested information to the user and also saving it locally for future requests. Setting up a Web proxy server on a network can be cumbersome, because each computer on the network must be configured to direct Web requests to the server.
If you have a proxy server on your network, instead of configuring each computer’s Web browser to point to the proxy server, you can move the server to the WAN or DMZ and enable Web Proxy Forwarding using the settings on the Network > Web Proxy page. The firewall automatically forwards all Web proxy requests to the proxy server without requiring all the computers on the network to be configured.
The following graphic shows the Network > Web Proxy page.