Unassigned switch ports on the SonicWall NSA 2400MX appliance can function as VLAN trunk ports.
You can enable or disable VLANs on the trunk ports, allowing the existing VLANs on the SonicWall NSA 2400MX appliance to be bridged to respective VLANs on another switch connected via the trunk port. The SonicWall NSA 2400MX appliance supports 802.1Q encapsulation on the trunk ports. A maximum of 25 VLANs can be enabled on each trunk port.
The VLAN trunking feature provides the following functions:
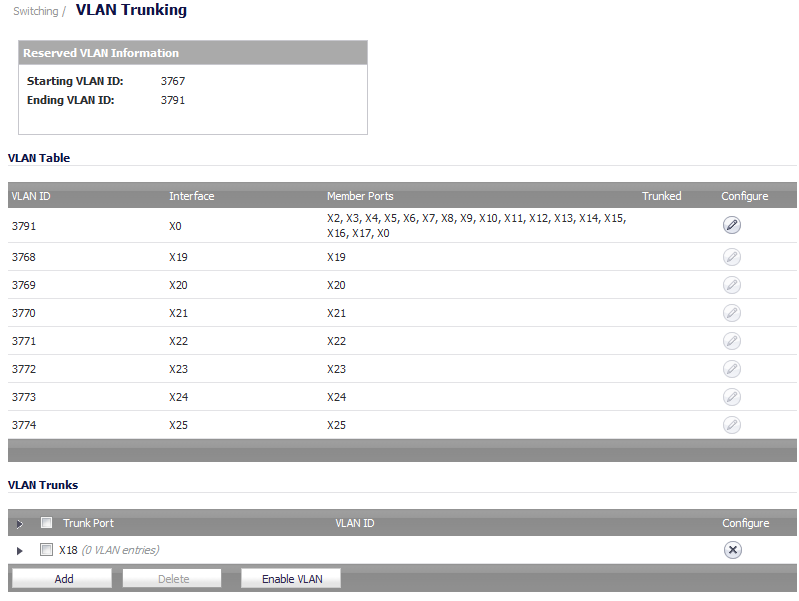
The allowed VLAN ID range is 1-4094. Some VLAN IDs are reserved for PortShield use. The reserved range is displayed in the Switching > VLAN Trunking page. You can mark certain PortShield groups as Trunked. When the PortShield group is dismantled, the associated VLAN is automatically disabled on the trunk ports.
VLANs can exist locally in the form of PortShield groups or can be totally remote VLANs. Below, the Network > PortShield page shows a PortShield group with X14 as the PortShield interface and X15, X16, and X17 as members of the PortShield group. X20 and X21 are VLAN trunk ports.
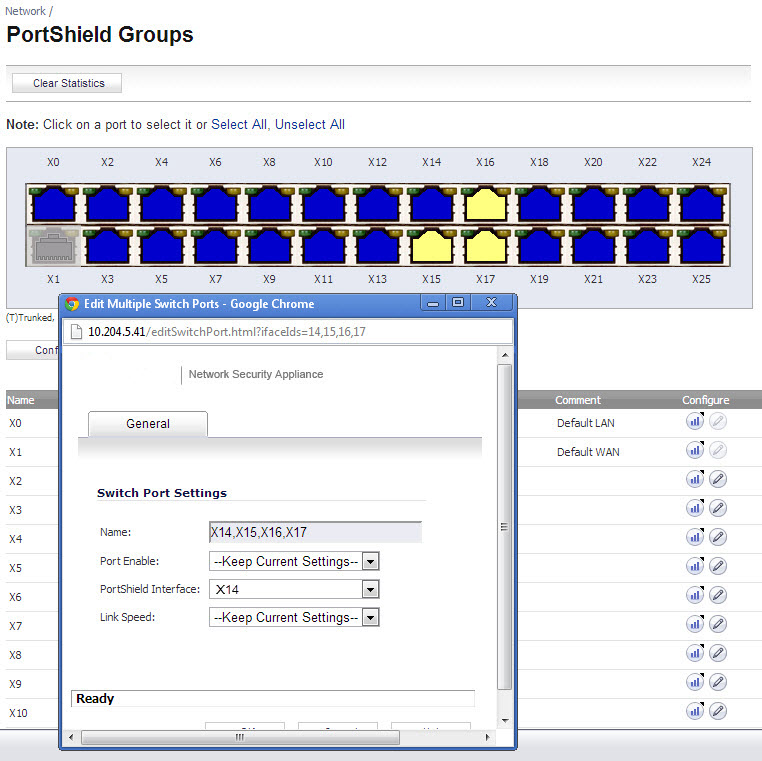
You can change the VLAN ID of PortShield groups on the SonicWall NSA 2400MX appliance. This allows easy integration with existing VLAN numbering.
Unlike traditional Layer 2 switches, the SonicWall NSA 2400MX appliance does not allow changing port VLAN membership in an ad-hoc manner. VLAN membership of a port must be configured via PortShield configuration in the SonicOS management interface. For more information about configuring PortShield groups, see Network > PortShield Groups.
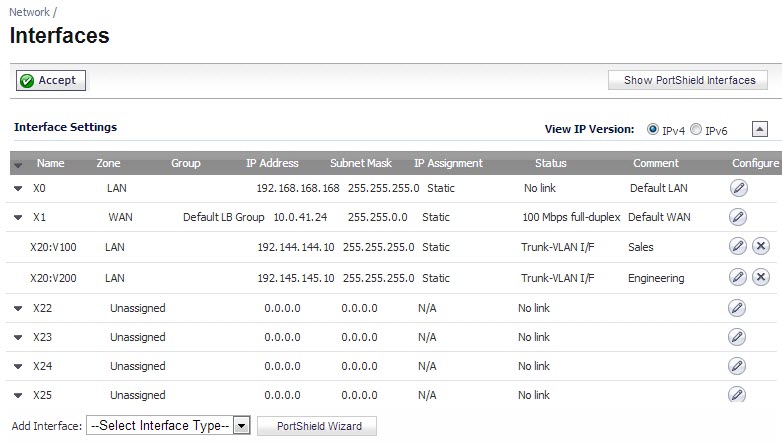
A virtual interface (called the VLAN Trunk Interface) is automatically created for remote VLANs. When the same remote VLAN is enabled on another trunk port, no new interface is created. All packets with the same VLAN tag ingressing on different trunk ports are handled by the same virtual interface. This is a key difference between VLAN sub-interfaces and VLAN trunk interfaces.
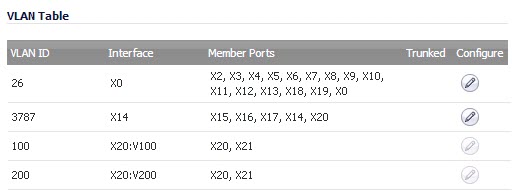
The Name column on the Network > Interfaces page displays the VLAN Trunk Interfaces for the VLAN trunks on which VLAN IDs 100 and 200 are enabled.
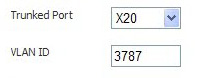
You can enable any VLAN, local or remote, on a VLAN trunk to allow bridging to respective VLANs on another switch. For example, local VLAN 3787, created from a PortShield group, can be enabled on the VLAN trunk for port X20, which also has two remote VLANs enabled on it.
The VLAN Table on the Switching > VLAN Trunking page displays the trunk port, X20, as a member of local VLAN 3787 after the VLAN is enabled on the VLAN trunk.
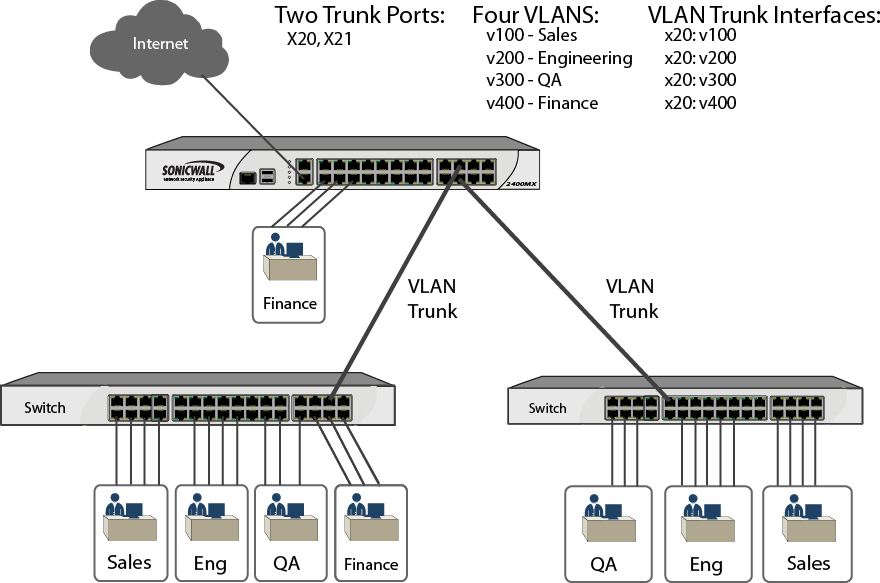
Sample VLAN Trunk Topology illustrates a VLAN trunk with two trunk ports, bridging the Sales, Engineering, QA, and Finance VLANs through the NSA 2400MX. Each remote VLAN was enabled on VLAN trunk port X20 initially, causing the creation of four virtual VLAN trunk interfaces. When these VLANs were also enabled on trunk port X21, no new virtual interfaces were created.
Sample VLAN Trunk Topology
VLAN trunking interoperates with Rapid Spanning Tree Protocol (RSTP), Link Aggregation and Port Mirroring features. A VLAN trunk port can be mirrored, but cannot act as a mirror port itself. You cannot enable Static port security on the VLAN trunk port.
Ports configured as VLAN trunks cannot be used for any other function and are reserved for use in Layer 2 only. For example, you cannot configure an IP Address for the trunk ports.
When a Trunk VLAN interface has been configured on a particular trunk port, that trunk port cannot be deleted until the VLAN interface is removed, even though the VLAN is enabled on multiple trunk ports. This is an implementation limitation and will be addressed in a future release.
