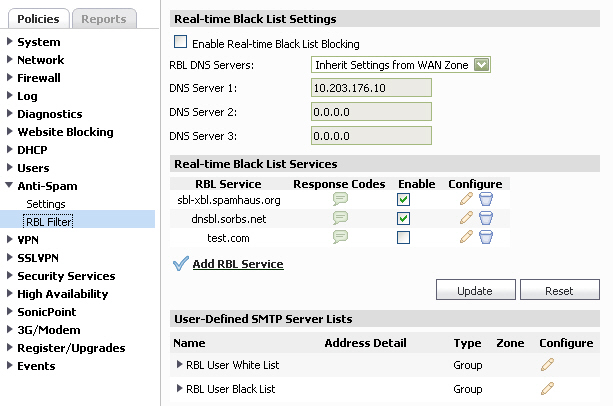
The Policies > Anti-Spam > RBL Filter page only allows configuration of Real-Time Black List filtering if the Anti-Spam Service is not enabled.
SMTP Real-Time Black List (RBL) is a mechanism for publishing the IP addresses of SMTP spammers use. There are a number of organizations that compile this information both for free: http://www.spamhaus.org, and for profit: http://www.mail-abuse.com. A well-maintained list of RBL services and their efficacy can be found at:
http://www.sdsc.edu/~jeff/spam/cbc.html
http://www.sdsc.edu/~jeff/spam/cbc.html
When Enable Real-time Black List Blocking is enabled on the Anti-Spam > RBL Filter page, inbound connections from hosts on the WAN, or outbound connections to hosts on the WAN are checked against each enabled RBL service with a DNS request to the DNS servers configured under RBL DNS Servers.
The RBL DNS Servers menu allows you to specify the DNS servers. You can choose Inherit Settings from WAN Zone or Specify DNS Servers Manually. If you select Specify DNS Servers Manually, enter the DNS server addresses in the DNS Server fields.