The SSL VPN > Server Settings page is used to configure details of the SonicWALL security appliance’s behavior as an SSL VPN server.
The following options can be configured on the SSL VPN > Server Settings page.
|
•
|
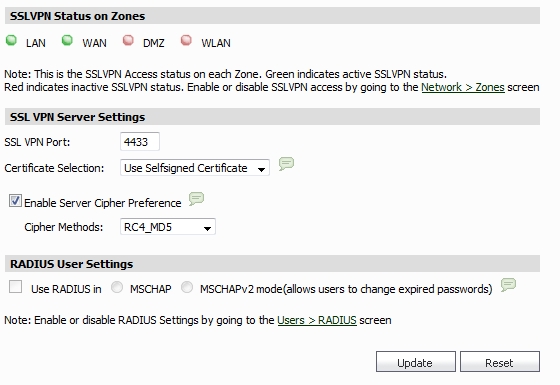
SSL VPN Status on Zones: This displays the SSL VPN Access status on each Zone. Green indicates active SSL VPN status, while red indicates inactive SSL VPN status. To enable or disable SSL VPN access on a zone, click on the Network > Zones link to jump to the Edit Zone window.
|
|
•
|
SSL VPN Port: Set the SSL VPN port for the appliance. The default is 4433.
|
|
•
|
Certificate Selection: Select the certificate that is used to authenticate SSL VPN users. All imported local certificates are available to be selected in the pull-down menu. To manage certificates, go to the System > Certificates page.
|
|
•
|
Enable Server Cipher Preference: Select to configure a preferred cipher method. The available ciphers are RC4_MD5, 3DES_SHA1, and AES256_SHA1.
|
|
•
|
RADIUS User Settings: This option is only available when either RADIUS or LDAP is configured to authenticate SSL VPN users. Select Use RADIUS in to have RADIUS use MSCHAP (or MSCHAPv2) mode. Enabling MSCHAP-mode RADIUS allows users to change expired passwords at login time.
|
 .
.