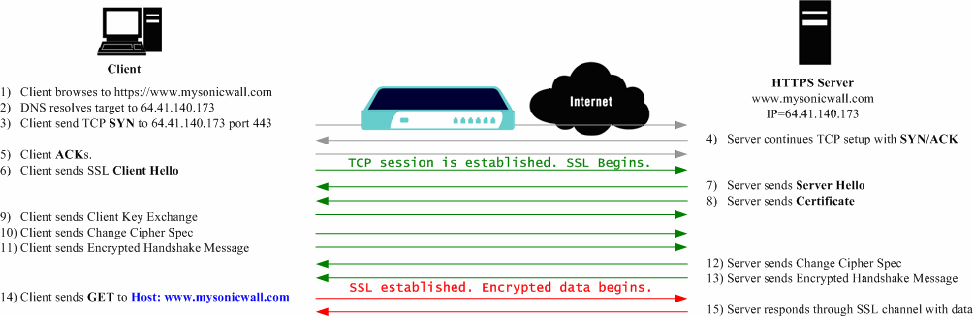
An effect of the security provided by SSL is the obscuration of all payload, including the URL (Uniform Resource Locator, for example, https://www.mysonicwall.com) being requested by a client when establishing an HTTPS session. This is because of the fact that HTTP is transported within the encrypted SSL when using HTTPS. It is not until the SSL session is established (step 14) that the actual target resource (www.mysonicwall.com) is requested by the client, but because the SSL session is already established, no inspection of the session data by the SonicWALL firewall appliance or any other intermediate device is possible. As a result, URL based content filtering systems cannot consider the request to determine permissibility in any way other than by IP address.
For more information about SSL Control, see the SonicOS Enhanced 4.0 Administrator’s Guide.
|
2
|
|
3
|
Under General Settings, select Enable SSL Control to enable SSL Control for the selected group or appliance.
|
|
•
|
Log the event—If an SSL policy violation, as defined within the Configuration section below, is detected, the event is logged, but the SSL connection is allowed to continue.
|
|
•
|
Block the connection and log the event—In the event of a policy violation, the connection is blocked and the event is logged.
|
|
•
|
Enable Blacklist—Controls detection of the entries in the blacklist, as configured in the Custom Lists section below.
|
|
•
|
Enable Whitelist—Controls detection of the entries in the whitelist, as configured in the Custom Lists section below. Whitelisted entries take precedence over all other SSL control settings.
|
|
•
|
Detect Expired Certificates—Controls detection of certificates whose start date is before the current system time, or whose end date is beyond the current system time. Date validation depends on the SonicWALL’s System Time. Make sure your System Time is set correctly, preferably synchronized with NTP, on the System > Time page.
|
|
•
|
Detect SSLv2—Controls detection of SSLv2 exchanges. SSLv2 is known to be susceptible to cipher downgrade attacks because it does not do integrity checking on the handshake. Best practices recommend using SSLv3 or TLS instead of SSLv2.
|
|
•
|
Detect Self-Signed Certificates—Controls the detection of certificates where both the issuer and the subject have the same common name.
|
|
•
|
Detect Certificate signed by an Untrusted CA—Controls the detection of certificates where the issuer’s certificate is not in the SonicWALL’s System > Certificates trusted store.
|
|
•
|
Detect Weak Ciphers(< 64bits)—Controls the detection of SSL sessions negotiated with symmetric ciphers less than 64 bits, commonly indicating export cipher usage.
|
|
a
|
|
b
|
|
7
|