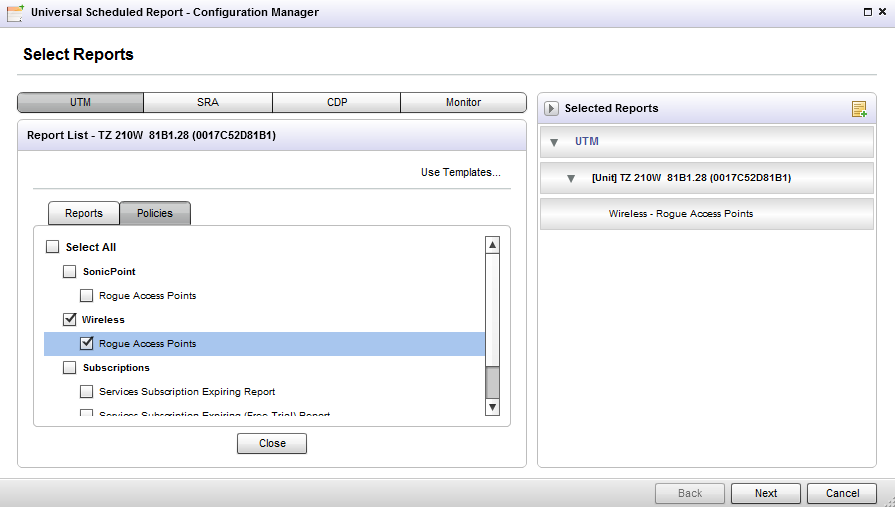
To schedule a Rogue Access Point report, click the Schedule Rouge Access Point Report link located at the bottom of the Wireless > IDS page. This redirects you to the Universal Scheduled Reports > Configuration Manager page, where you can schedule the Rogue Access point report in the Policies tab. Rouge Access Point reporting is not supported at Global level, only Group and Unit levels. Refer to Using the Universal Scheduled Reports Application for details on configuring Universal Scheduled Reports.