To use single sign-on, your SonicWall security appliance must be configured to use either SonicWall SSO Agent or Browser NTLM authentication only as the SSO method.
The following procedure describes how to configure your SonicWall security appliance to use Browser NTLM authentication only. Perform the following steps:
|
1
|
Log in to your SonicWall security appliance and navigate to Users > Settings.
|
In the Single-sign-on method drop-down menu, select Browser NTLM authentication only.
|
2
|
|
3
|
Click the Settings tab. Configuration on the Settings tab is the same as the configuration for the NTLM tab when SonicWall SSO Agent is selected as the Single-sign-on method. Refer to Step 32 in the procedure in Configuring Your SonicWall Security Appliance for SonicWall SSO Agent for detailed configuration instructions for this page.
|
|
4
|
|
5
|
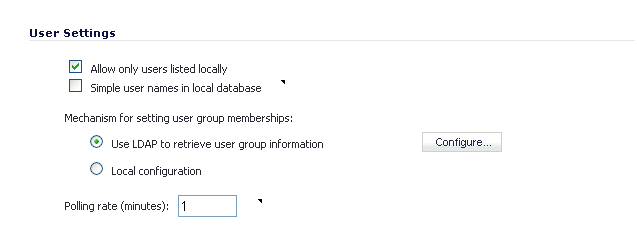
Check the box next to Allow only users listed locally to allow only users listed locally on the appliance to be authenticated.
|
|
6
|
Check the box next to Simple user names in local database to use simple user names. When selected, the domain component of a user name will be ignored. User names returned from the authentication agent typically include a domain component, for example, domain1/user1. If this box is not checked, user names in the local database must match exactly the full names returned from the agent, including the domain component.
|
|
7
|
To use LDAP to retrieve user information, select the Use LDAP to retrieve user group information radio button. Click Configure to configure the LDAP settings. The LDAP Configuration page displays. For configuration information for this page, refer to Advanced LDAP Configuration.
|
|
8
|
To use locally configured user group settings, select the Local configuration radio button.
|
|
9
|
In the Polling rate (minutes) field, enter a polling interval, in minutes. The security appliance will poll the workstation running SSO Agent once every interval to verify that users are still logged on. The default is 1.
|
|
10
|
Configuration on the Enforcement, Terminal Services, and Test tabs is the same as for those tabs when SonicWall SSO Agent is selected as the Single-sign-on method. Refer to the procedure in Configuring Your SonicWall Security Appliance for SonicWall SSO Agent for detailed configuration instructions for these pages.
|
When LDAP is selected in the Authentication method for login field, RADIUS configuration is still required when using NTLM authentication. NTLM authentication requires MSCHAP, which is provided by RADIUS but not by LDAP.
The Configure button next to RADIUS may also be required for CHAP/NTLM is enabled when LDAP authentication is selected on the Users > Settings page.
To configure RADIUS settings, click the Configure button and follow the instructions in the Configuring RADIUS Authentication.
In Microsoft Windows 7 and Vista, Internet Explorer uses the NTLMv2 variant of NTLM by default. The NTLMv2 variant cannot be authenticated via RADIUS in the same way as NTLM. To use browser NTLM authentication as the SSO method with these versions of Windows, the Windows machines must be configured to use NTLMv2 Session Security instead of NTLMv2. NTLMv2 Session Security is a variant that is designed to be compatible with RADIUS/MSCHAPv2. This configuration is performed using Windows Group Policy.
|
1
|
To open Windows Group Policy, open the Control Panel and select Administrative Tools.
|
|
2
|
Select Local Security Policy to open the Local Security Policy window.
|
|
3
|
|
4
|
Edit the Network Security: LAN Manager authentication level setting and select one of the following:
|