|
•
|
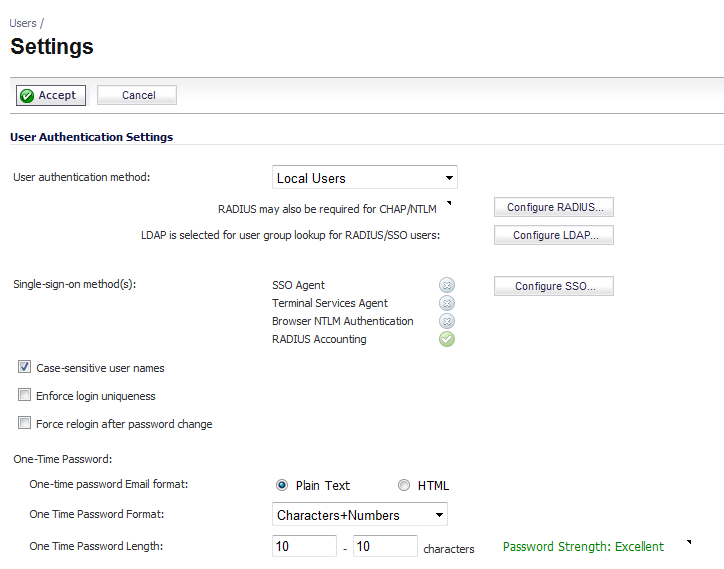
In the User authentication method drop-down list, select the type of user account management your network uses:
|
|
•
|
Select Local Users to configure users in the local database in the SonicWall appliance using the Users > Local Users and Users > Local Groups pages.
|
For information about using the local database for authentication, see Using Local Users and Groups for Authentication.
For detailed configuration instructions, see the following sections:
|
•
|
Select RADIUS if you have more than 1,000 users or want to add an extra layer of security for authenticating the user to the SonicWall. If you select RADIUS for user authentication, users must log into the SonicWall using HTTPS in order to encrypt the password sent to the SonicWall. If a user attempts to log into the SonicWall using HTTP, the browser is automatically redirected to HTTPS.
|
For information about using a RADIUS database for authentication, see Using RADIUS for Authentication.
For detailed configuration instructions, see Configuring RADIUS Authentication
|
•
|
Select RADIUS + Local Users if you want to use both RADIUS and the SonicWall local user database for authentication.
|
|
•
|
Select LDAP if you use a Lightweight Directory Access Protocol (LDAP) server, Microsoft Active Directory (AD) server, or Novell eDirectory to maintain all your user account data.
|
For information about using an LDAP database for authentication, see Using LDAP/Active Directory/eDirectory Authentication.
For detailed configuration instructions, see Configuring LDAP Integration in SonicOS
|
•
|
Select LDAP + Local Users if you want to use both LDAP and the SonicWall local user database for authentication.
|
|
•
|
In the Single-sign-on method list, select one of the following:
|
|
•
|
Select SSO Agent if you are using Active Directory for authentication and the SonicWall SSO Agent is installed on a computer in the same domain.
|
|
•
|
Select Terminal Services Agent if you are using Terminal Services and the SonicWall Terminal Services Agent (TSA) is installed on a terminal server in the same domain.
|
|
•
|
Select Browser NTLM authentication if you want to authenticate Web users without using the SonicWall SSO Agent or TSA. Users are identified as soon as they send HTTP traffic. NTLM requires RADIUS to be configured (in addition to LDAP, if using LDAP), for access to MSCHAP authentication. If LDAP is selected above, a separate Configure button for RADIUS appears here when NTLM is selected.
|
|
•
|
Select RADIUS Accounting if you want a network access server (NAS) to send user login session accounting messages to an accounting server.
|
For detailed SSO configuration instructions, see Configuring Single Sign-On.
For Browser NTLM authentication configuration, see Configuring Your SonicWall Appliance for Browser NTLM Authentication.
|
•
|
Select Case-sensitive user names to enable matching based on capitalization of user account names.
|
|
•
|
Select Enforce login uniqueness to prevent the same user name from being used to log into the network from more than one location at a time. This setting applies to both local users and RADIUS/LDAP users. However, the login uniqueness setting does not apply to the default administrator with the username admin.
|
|
•
|
Select Force relogin after password change to force the user to login immediately after changing the password.
|
|
•
|
In the One-Time Password section, select the following:
|
|
•
|
Select either Plain text or HTML for One-time password Email format, depending on your preference if you are using One-Time Password authentication.
|
|
•
|
Select one of the following for One-time password format:
|
|
•
|
|
•
|