|
•
|
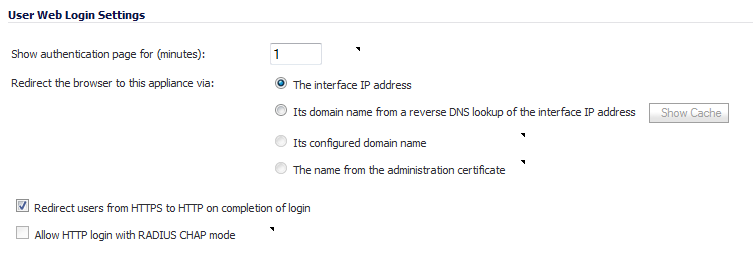
In the Show user authentication page for field, enter the number of minutes that a user has to log in before the login page times out. If it times out, a message displays saying they must click before attempting to log in again.
|
|
•
|
SonicOS provides options under Redirect the browser to this appliance via: that allow you to enable redirecting to a domain name as well as to an IP address.
|
Options are available to redirect to the following:
|
•
|
The interface IP address – This option redirects the user to the IP address of the interface to which his computer or local network is connected. This operates the same as in previous releases.
|
|
•
|
Its domain name from a reverse DNS lookup of the interface IP address – This option causes the appliance to determine the Fully Qualified Domain Name of the interface IP address, and redirect the user to that domain name. For this to work, Reverse DNS must be enabled for the domain in the DNS server.
|
Click on the Show Cache button to display the Interface Host Names Reverse DNS Cache table, which lists Interface, IP Address, DNS Name, and TTL (secs).
|
•
|
Its configured domain name – This option redirects the user to the domain name that is configured on the System > Administration page. The firewall’s domain name must be configured there before this redirect can work, and in each zone that users will be logging in from, it must be a valid domain name that resolves to an interface IP address. Possible zones include LAN, WLAN, WAN, etc.
|
|
•
|
The name from the administration certificate – This option redirects the user to the domain name (common name) in the certificate that was imported. The certificate must be imported on the System > Administration page before this redirect can work, and as above it must be a valid domain name in each zone that users will be logging in from.
|
|
•
|
Select Redirect users from HTTPS to HTTP on completion of login if you want users to be connected to the network through your SonicWall appliance via HTTP after logging in via HTTPS. If you have a large number of users logging in via HTTPS, you may want to redirect them to HTTP, because HTTPS consumes more system resources than HTTP. If you deselect this option, you will see a warning dialog.
|
|
•
|
Select Allow HTTP login with RADIUS CHAP mode to have a CHAP challenge be issued when a RADIUS user attempts to log in using HTTP. This allows for a secure connection without using HTTPS, preventing the browser from sending the password in clear text over HTTP. Be sure to check that the RADIUS server supports this option.
|