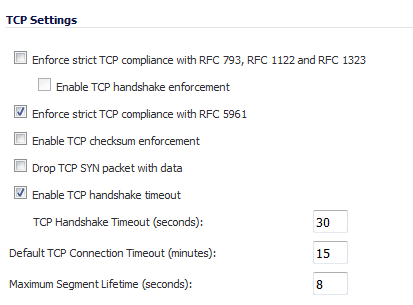
The TCP Settings section allows you to:
|
•
|
Enforce strict TCP compliance with RFC 793 and RFC 1122 – Select to ensure strict compliance with several TCP timeout rules. This setting maximizes TCP security, but it may cause problems with the Window Scaling feature for Windows Vista users. When this option is selected, the Enable TCP handshake enforcement option becomes active.
|
|
•
|
Enable TCP handshake enforcement – Require a successful three-way TCP handshake for all TCP connections.
|
|
•
|
Enforce strict TCP compliance with RFC 5961 – Select to ensure compliance with IETF RFC 5961. RFC 5961 protects against vulnerability CVE-2004-0230 by stopping spoofed off-path TCP packet injection attacks. This option is selected by default.
|
|
CAUTION: For maximum security, all client devices are recommended to be updated to comply with RFC 5961. It is not recommended to disable this option; to do so should be done with caution and only if legacy client devices have not been updated to follow RFC 5961 and RST floods are occurring.
|
|
•
|
Enable TCP checksum enforcement – If an invalid TCP checksum is calculated, the packet is dropped.
|
|
•
|
Default TCP Connection Timeout – The default time assigned to Access Rules for TCP traffic. If a TCP session is active for a period in excess of this setting, the TCP connection is cleared by the SonicWall. The default value is 5 minutes, the minimum value is 1 minute, and the maximum value is 999 minutes.
|
|
•
|
Maximum Segment Lifetime (seconds) – Determines the number of seconds that any TCP packet is valid before it expires. The minium value is 1 second, the maximum value is 60 seconds, and the default value is 8 seconds.
|