Rogue Access Points have emerged as one of the most serious and insidious threats to wireless security. In general terms, an access point is considered rogue when it has not been authorized for use on a network. The convenience, affordability and availability of non-secure access points, and the ease with which they can be added to a network creates an easy environment for introducing rogue access points. Specifically, the real threat emerges in a number of different ways, including unintentional and unwitting connections to the rogue device, transmission of sensitive data over non-secure channels, and unwanted access to LAN resources. So while this doesn't represent a deficiency in the security of a specific wireless device, it is a weakness to the overall security of wireless networks.
Intrusion Detection Services (IDS) greatly increase the security capabilities of the SonicWall security appliance because it enables the appliance to recognize and take countermeasures against the most common types of illicit wireless activity. IDS reports on all access points the SonicWall security appliance can find by scanning the 802.11a/b/g/n/ac/af radio bands on the SonicPoints.
The SonicPoint > IDS page reports on all access points detected by the SonicWall security appliance and its associated SonicPoints, and provides the ability to authorize legitimate access points.
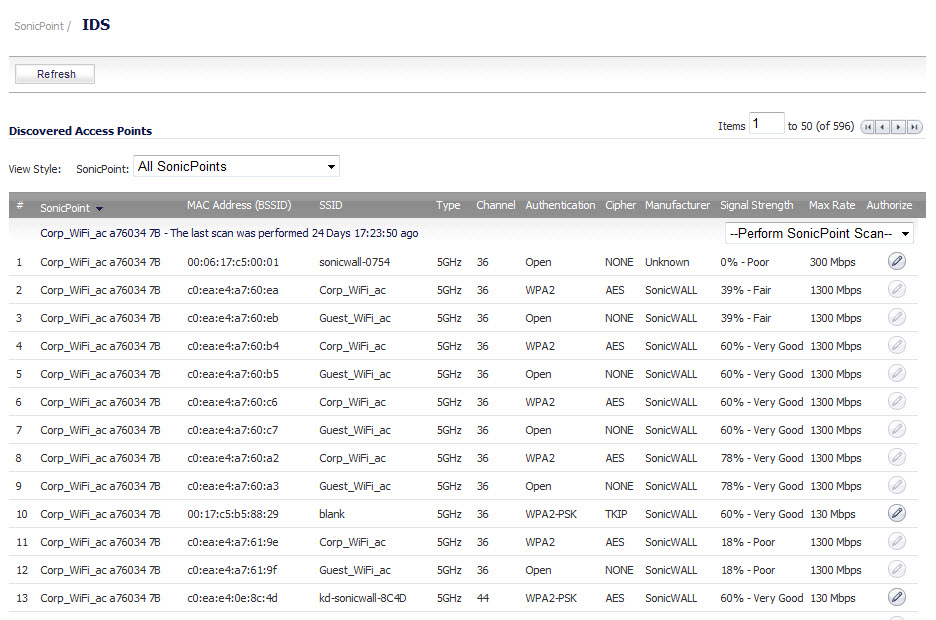
The table below describes the entities that are displayed on the SonicPoint > IDS page.
