SonicOS also provides Single Sign-On (SSO) capability. SSO can be used in conjunction with LDAP.
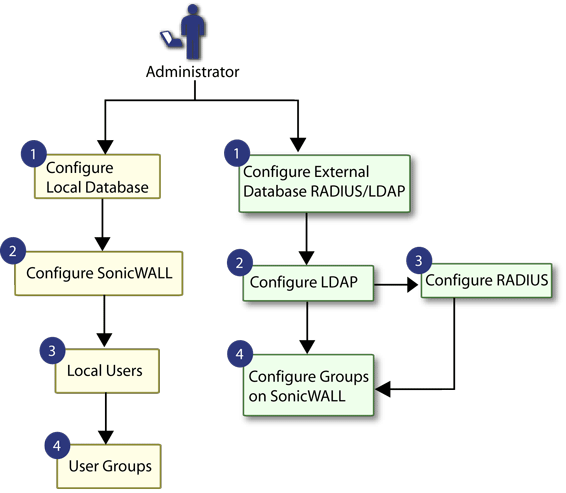
Figure 36 shows an overview of user management.
Figure 36. User management topology
The Dell SonicWALL network security appliance provides a local database for storing user and group information. You can configure the firewall to use this local database to authenticate users and control their access to the network; see Figure 37. The local database is a good choice over LDAP or RADIUS when the number of users accessing the network is relatively small. Creating entries for dozens of users and groups takes time, although once the entries are in place they are not difficult to maintain.
Figure 37. User management: Using local users and groups for authentication
The number of users supported by the local database on the SM 9800 is:
To apply Content Filtering Service (CFS) policies to users, the users must be members of local groups and the CFS policies are then applied to the groups. To use CFS, you cannot use LDAP or RADIUS without combining that method with local authentication. When using the combined authentication method to use CFS policies, the local group names must be an exact match with the LDAP or RADIUS group names. When using the LDAP + Local Users authentication method, you can import the groups from the LDAP server into the local database on the firewall. This greatly simplifies the creation of matching groups, to which CFS policies can then be applied.
|
•
|
Group membership - Users can belong to one or more local groups. By default, all users belong to the groups Everyone and Trusted Users. You can remove these group memberships for a user and can add memberships in other groups.
|
|
•
|
VPN access - You can configure the networks that are accessible to a VPN client started by a user. When configuring VPN access settings, you can select from a list of networks. The networks are designated by their Address Group or Address Object names.
|
You can also add or edit local groups. The configurable settings for groups include the following:
|
•
|
Group settings - For administrator groups, you can configure SonicOS to allow login to the management interface without activating the login status popup dialog.
|
|
•
|
Group members - Groups have members that can be local users or other local groups.
|
|
•
|
VPN access - VPN access for groups is configured in the same way as VPN access for users. You can configure the networks that are accessible to a VPN client started by a member of this group. When configuring VPN access settings, you can select from a list of networks. The networks are designated by their Address Group or Address Object names.
|
|
•
|
CFS policy - You can apply a content filtering (CFS) policy to group members. The CFS policy setting is only available if the firewall is currently licensed for Premium Content Filtering Service.
|
Remote Authentication Dial In User Service (RADIUS) is a protocol used by Dell SonicWALL network security appliances to authenticate users who are attempting to access the network; see Figure 38. The RADIUS server contains a database with user information and checks a user’s credentials using authentication schemes such as Password Authentication Protocol (PAP), Challenge-handshake authentication protocol (CHAP), Microsoft CHAP (MSCHAP), or MSCHAPv2.
Figure 38. User management: Using RADIUS for authentication
Microsoft Active Directory also works with Dell SonicWALL Single Sign-On and the Dell SonicWALL SSO Agent. For more information, see Single Sign-On Overview .
The following terms are useful when working with LDAP and its variants:
|
•
|
Schema – The schema is the set of rules or the structure that defines the types of data that can be stored in a directory, and how that data can be stored. Data is stored in the form of entries.
|
|
•
|
Active Directory (AD) – The Microsoft directory service, commonly used with Windows-based networking. Microsoft Active Directory is compatible with LDAP.
|
|
•
|
eDirectory – The Novell directory service, used for Novell NetWare-based networking. Novell eDirectory has an LDAP gateway that can be used for management.
|
|
•
|
Entry – The data that is stored in the LDAP directory. Entries are stored in attribute/value (or name/value) pairs, where the attributes are defined by object classes. A sample entry would be cn=john where cn (common name) is the attribute and john is the value.
|
|
•
|
Object class – Object classes define the type of entries that an LDAP directory may contain. A sample object class, as used by AD, would be user or group.
|
Microsoft Active Directory’s Classes can be browsed at http://msdn.microsoft.com/library/.
|
•
|
Object - In LDAP terminology, the entries in a directory are referred to as objects. For the purposes of the SonicOS implementation of the LDAP client, the critical objects are User and Group objects. Different implementations of LDAP can refer to these object classes in different fashions, for example, Active Directory refers to the user object as user and the group object as group, while RFC2798 refers to the user object as inetOrgPerson and the group object as groupOfNames.
|
|
•
|
Attribute - A data item stored in an object in an LDAP directory. Object can have required attributes or allowed attributes. For example, the dc attribute is a required attribute of the dcObject (domain component) object.
|
|
•
|
dn - A “distinguished name,” which is a globally unique name for a user or other object. It is made up of a number of components, usually starting with a common name (cn) component and ending with a domain specified as two or more domain components (dc). For example, cn=john,cn=users,dc=domain,dc=com.
|
|
•
|
cn – The “common name” attribute is a required component of many object classes throughout LDAP.
|
|
•
|
ou – The “organizational unit” attribute is a required component of most LDAP schema implementations.
|
|
•
|
dc – The “domain component” attribute is commonly found at the root of a distinguished name and is commonly a required attribute.
|
|
•
|
TLS – Transport Layer Security is the IETF standardized version of SSL (Secure Sockets Layer). TLS 1.1 and 1.2 are supported.
|
SonicOS provides support for directory servers running the following protocols:
LDAP User Group names that are copied to the Security Appliance include the domain name in the format: name@domain.com. This ensures that user group names from various domains are unique.
The following features and restrictions apply to mirrored LDAP User Groups:
|
•
|
Integrating your firewall with an LDAP directory service requires configuring your LDAP server for certificate management, installing the correct certificate on your firewall, and configuring the firewall to use the information from the LDAP Server. For an introduction to LDAP, see Using LDAP/Active Directory/eDirectory Authentication .
The following procedures describe how to perform these tasks in an Active Directory environment:
|
1
|
Navigate to Start > Settings > Control Panel > Add/Remove Programs
|
|
2
|
Select Add/Remove Windows Components
|
|
3
|
Select Certificate Services
|
|
4
|
Select Enterprise Root CA when prompted.
|
|
5
|
|
6
|
Launch the Domain Security Policy application: Navigate to Start > Run and run the command: dompol.msc.
|
|
7
|
Open Security Settings > Public Key Policies.
|
|
8
|
Right click Automatic Certificate Request Settings.
|
|
9
|
Select New > Automatic Certificate Request.
|
|
10
|
Step through the wizard, and select Domain Controller from the list.
|
|
1
|
|
2
|
Right click on the CA you created, and select properties.
|
|
3
|
|
4
|
|
5
|
Step through the wizard, and select the Base-64 Encoded X.509 (.cer) format.
|
|
1
|
Browse to System > CA Certificates.
|
|
2
|
Select Add new CA certificate. Browse to and select the certificate file you just exported.
|
|
3
|
Click the Import certificate button.
|
You can set any local group, including default local groups (except for the Everyone group and the Trusted Users group) as a group with members that are set by their location in the LDAP directory tree.
When a user is a member of any local groups that are configured for LDAP location:
SonicWALL SSO is configured in the Users > Settings page of the SonicOS management interface. SSO is separate from the Authentication method for login settings, which can be used at the same time for authentication of VPN/L2TP client users or administrative users.
Other benefits of SonicWALL SSO include:
|
•
|
Ease of use — Users only need to sign in once to gain automatic access to multiple resources.
|
|
•
|
Improved user experience — Windows domain credentials can be used to authenticate a user for any traffic type without logging into the appliance using a Web browser.
|
|
•
|
Transparency to users — Users are not required to re-enter user name and password for authentication.
|
|
•
|
Secure communication — Shared key encryption for data transmission protection.
|
|
•
|
Installation — SonicWALL SSO Agent can be installed on any Windows server on the LAN, and TSA can be installed on any terminal server.
|
|
•
|
Multiple SSO Agents — Up to 8 agents are supported to provide capacity for large installations
|
|
•
|
Multiple TSAs — Multiple terminal services agents (one per terminal server) are supported. The number depends on the model of the SonicWALL network security appliance and ranges from 8 to 512.
|
|
•
|
Browser NTLM authentication — SonicWALL SSO can authenticate users sending HTTP traffic without using the SSO Agent.
|
|
•
|
Mac and Linux support — With Samba 3.5 and higher, SonicWALL SSO is supported for Mac and Linux users.
|
|
•
|
Per-zone enforcement — SonicWALL SSO can be triggered for traffic from any zone even when not automatically initiated by firewall access rules or security services policies, providing user identification in event logging or AppFlow Monitoring.
|
The SSO Agent is compatible with all versions of SonicOS that support SonicWALL SSO.
The following requirements must be met in order to run the SSO Agent:
The following requirements must be met in order to run the TSA:
SonicWALL SSO requires minimal administrator configuration and is transparent to the user.
SSO is triggered in the following situations:
|
•
|
NTLM Authentication is currently available for HTTP; it is not available for use with HTTPS traffic.
To use this method with Linux or Mac clients as well as Windows clients, you can also enable SSO to probe the client for either NetAPI or WMI, depending on which is configured for the SSO Agent.This causes the firewall to probe for a response on the NetAPI/WMI port before requesting that the SSO Agent identify a user. If no response occurs, these devices fail SSO immediately. For a:
The SSO Agent can be installed on any workstation with a Windows domain that can communicate with clients and the firewall directly using the IP address or using a path, such as VPN. For installation instructions for the SSO Agent, refer to Installing the SonicWALL SSO Agent .
|
•
|
User login denied - not allowed by policy rule – The user has been identified and does not belong to any user groups allowed by the policy blocking the user’s traffic.
|
|
•
|
User login denied - not found locally – The user has not been found locally, and Allow only users listed locally is selected in the firewall.
|
|
•
|
User login denied - SSO Agent agent timeout – Attempts to contact the SSO Agent have timed out.
|
|
•
|
User login denied - SSO Agent configuration error – The SSO Agent is not properly configured to allow access for this user.
|
|
•
|
User login denied - SSO Agent communication problem – There is a problem communicating with the workstation running the SSO Agent.
|
|
•
|
User login denied - SSO Agent agent name resolution failed – The SSO Agent is unable to resolve the user name.
|
|
•
|
SSO Agent returned user name too long – The user name is too long.
|
|
•
|
SSO Agent returned domain name too long – The domain name is too long.
|
|
NOTE: The notes field of log messages specific to the SSO Agent will contain the text <domain/user-name>, authentication by SSO Agent.
|
For installation instructions for the TSA, refer to Installing the SonicWALL Terminal Services Agent .
The firewall has the Allow limited access for non-domain users setting for optionally giving limited access to non-domain users (users logged into their local machine and not into the domain), and this works for terminal services users as it does for other SSO users.
If your network includes non-Windows devices or Windows computers with personal firewalls running, check the box next to Probe user for and select the radio button for either NetAPI or WMI depending on which is configured for the SSO Agent. This causes the firewall to probe for a response on the NetAPI/WMI port before requesting that the SSO Agent identify a user. If no response occurs, these devices will fail SSO immediately. Such devices do not respond to, or may block, the Windows networking messages used by the SSO Agent to identify a user.
To control handling of these non-user connections, an Allow Terminal Server non-user traffic to bypass user authentication in access rules checkbox is available in the TSA configuration on the appliance. When selected, these connections are allowed. If this checkbox is not selected, then the services are treated as local users and can be given access by selecting the Allow limited access for non-domain users setting and creating user accounts on the appliance with the corresponding service names.
The following settings on the Users tab of the SSO configuration apply when configuring NTLM authentication:
If the user name does not match a local user account, the user will not be logged in. The Allow limited access for non-domain users option does not apply for users authenticated via NTLM.
|
•
|
Internet Explorer (9.0 or above) – Uses the user’s domain credentials and authenticates transparently if the website that it is logging into the firewall (the Dell SonicWALL appliance) is in the local intranet, according to the Security tab in its Internet Options. This requires adding the firewall to the list of websites in the Local Intranet zone in the Internet Options.
|
|
•
|
Google Chrome – Behaves the same as Internet Explorer, including requiring that the firewall is added to the list of websites in the Local Intranet zone in the Internet Options.
|
|
•
|
Firefox – Uses the user’s domain credentials and authenticates transparently if the website that it is logging into the firewall is listed in the network.automatic-ntlm-auth.trusted-uris entry in its configuration (accessed by entering about:config in the Firefox address bar).
|
|
•
|
Safari – Although Safari does support NTLM, it does not currently support fully transparent logon using the user’s domain credentials.
|
|
•
|
Browsers on Non-PC Platforms – Non-PC platforms, such as Linux and Mac, can access resources in a Windows domain through Samba, but do not have the concept of “logging the PC into the domain” as Windows PCs do. Hence, browsers on these platforms do not have access to the user’s domain credentials and cannot use them for NTLM.
|
|
NOTE: When NTLM is enabled for Single Sign-On enforcement, an HTTP/HTTPS access rule with Trusted Users as Users Allowed must be added to the LAN to WAN rules in the Firewall > Access Rules page. This rule will trigger an NTLM authentication request to the user. Without the access rule, other configurations such as restrictive Content Filter policies might block the user from Internet access and prevent the authentication request.
|
RADIUS accounting uses two types of accounting messages:
An Accounting-Request can send one of three request types specified by the Status-Type attribute:
|
•
|
Start—sent when a user logs in.
|
|
•
|
Stop—sent when a user logs out.
|
|
•
|
Interim-Update—sent periodically during a user login session.
|
The following attributes, that are relevant to SSO, are sent in Accounting-Requests:
|
•
|
|
•
|
User-Name—The user’s login name. The format is not specified by the RFC and can be a simple login name or a string with various values such as login name, domain, or distinguished name (DN).
|
|
•
|
Framed-IP-Address—The user's IP address. If NAT is used, this must be the user’s internal IP address.
|
|
•
|
Calling-Station-Id—A string representation of the user's IP address, used by some appliances such as Dell SMA.
|
|
•
|
Proxy-State—A pass-though state used for forwarding requests to another RADIUS accounting server.
|
|
•
|
|
•
|
Send the user’s IP address in either the Framed-IP-Address or Calling-Station-Id attribute in both Start and Stop messages.
|
|
NOTE: In the case of a remote access server using NAT to translate a user’s external public IP address, the attribute must provide the internal IP address that is used on the internal network, and it must be a unique IP address for the user. If both attributes are being used, the Framed-IP-Address attribute must use the internal IP address, and the Calling-Station-Id attribute should use the external IP address.
|
The user’s login name should be sent in the User-Name attribute of Start messages and Interim-Update messages. The user’s login name can also be sent in the User-Name attribute of Stop messages, but is not required. The User-Name attribute must contain the user’s account name and may include the domain also, or it must contain the user’s distinguished name (DN).
In RADIUS accounting, these attributes are used to contain the user's IPv6 address:
Currently, all these IPv6 attributes are ignored.
Some devices pass the IPv6 address as text in the Calling-Station-ID attribute.
The Calling-Station-ID is also ignored if it does not contain a valid IPv4 address.
This section provides an introduction to the Multiple Administrators Support feature.
|
•
|
SonicOS provides support for multiple concurrent administrators. This feature allows for multiple users to log-in with full administrator privileges. In addition to using the default admin user name, additional administrator user names can be created.
Multiple Administrators Support provides the following benefits:
|
•
|
Improved productivity - Allowing multiple administrators to access a firewall simultaneously eliminates “auto logout,” a situation that occurs when two administrators require access to the appliance at the same time and one is automatically forced out of the system.
|
|
•
|
Reduced configuration risk – The new read-only mode allows users to view the current configuration and status of a firewall without the risk of making unintentional changes to the configuration.
|
The following sections describe how the Multiple Administrators Support feature works:
|
•
|
Configuration mode - Administrator has full privileges to edit the configuration. If no administrator is already logged into the appliance, this is the default behavior for administrators with full and limited administrator privileges (but not read-only administrators).
|
|
•
|
Read-only mode - Administrator cannot make any changes to the configuration, but can view the entire management UI and perform monitoring actions.
|
Only administrators that are members of the SonicWALL Read-Only Admins user group are given read-only access, and it is the only configuration mode they can access.
|
•
|
Non-configuration mode - Administrator can view the same information as members of the read-only group and they can also initiate management actions that do not have the potential to cause configuration conflicts.
|
Only administrators that are members of the SonicWALL Administrators user group can access non-configuration mode. This mode can be entered when another administrator is already in configuration mode and the new administrator chooses not to preempt the existing administrator. By default, when an administrator is preempted out of configuration mode, he or she is converted to non-configuration mode. On the System > Administration page, this behavior can be modified so that the original administrator is logged out.
Table 93 provides a summary of the access rights available to the configuration modes. Access rights for limited administrators are included also, but note that this table does not include all functions available to limited administrators.
|
Full admin in non‑config mode |
||||
The Multiple Administrators Support feature supports two new default user groups:
|
•
|
SonicWALL Administrators - Members of this group have full administrator access to edit the configuration.
|
|
•
|
SonicWALL Read-Only Admins - Members of this group have read-only access to view the full management interface, but they cannot edit the configuration and they cannot switch to full configuration mode.
|
|
•
|
If members of the SonicWALL Administrators user group are also included in the Limited Administrators or SonicWALL Read-Only Admins user groups, the members have full administrator rights.
|
|
•
|
If members of the Limited Administrators user group are included in the SonicWALL Read-Only Admins user group, the members have limited administrator rights.
|
|
1
|
The admin user and SonicWALL Global Management System (GMS) both have the highest priority and can preempt any users.
|
|
2
|
A user that is a member of the SonicWALL Administrators user group can preempt any users except for the admin and SonicWALL GMS.
|
|
3
|
A user that is a member of the Limited Administrators user group can only preempt other members of the Limited Administrators group.
|