The following are sample topologies depicting common deployments. Inline Layer 2 Bridge Mode represents the addition of a SonicWall security appliance to provide firewall services in a network where an existing firewall is in place. Perimeter Security represents the addition of a SonicWall security appliance in pure L2 Bridge mode to an existing network, where the SonicWall is placed near the perimeter of the network. Internal Security represents the full integration of a SonicWall security appliance in mixed-mode, where it provides simultaneous L2 bridging, WLAN services, and NATed WAN access. Layer 2 Bridge Mode with High Availability represents the mixed-mode scenario where the SonicWall HA pair provide high availability along with L2 bridging. Layer 2 Bridge Mode with SSL VPN represents the scenario where a SonicWall SSL VPN Series appliance is deployed in conjunction with L2 Bridge mode.
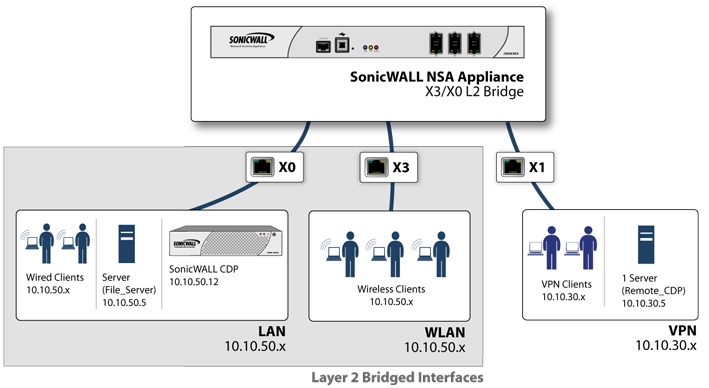
In wireless mode, after bridging the wireless (WLAN) interface to a LAN or DMZ zone, the WLAN zone becomes the secondary bridged interface, allowing wireless clients to share the same subnet and DHCP pool as their wired counterparts. See Wireless Layer 2 Bridge Topology.
Wireless Layer 2 Bridge Topology
|
1
|
Navigate to the Network > Interfaces page in the SonicOS management interface.
|
|
2
|
Click the Configure icon for the wireless interface you wish to bridge. The Edit Interface dialog displays.
|
|
3
|
|
4
|
Select the Interface which the WLAN should be Bridged To. In this instance, the X0 (default LAN zone) is chosen.
|
|
5
|
HP’s ProCurve Manager Plus (PCM+) and HP Network Immunity Manager (NIM) server software packages can be used to manage the switches as well as some aspects of the SonicWall network security appliance. See Inline Layer 2 Bridge Topology.
Inline Layer 2 Bridge Topology
|
1
|
Navigate to the Network > Interfaces page.
|
|
2
|
|
3
|
On the X0 Settings dialog, set the:
|
|
•
|
IP Assignment to Layer 2 Bridged Mode.
|
|
•
|
Bridged To: interface to X1.
|
|
4
|
|
5
|
Click OK to save and activate the change.
|
Perimeter Security Topology depicts a network where the SonicWall is added to the perimeter for the purpose of providing security services (the network may or may not have an existing firewall between the SonicWall and the router).
In this scenario, everything below the SonicWall (the Primary Bridge Interface segment) will generally be considered as having a lower level of trust than everything to the left of the SonicWall (the Secondary Bridge Interface segment). For that reason, it would be appropriate to use X1 (Primary WAN) as the Primary Bridge Interface.
Traffic from hosts connected to the Secondary Bridge Interface (LAN) would be permitted outbound through the SonicWall to their gateways (VLAN interfaces on the L3 switch and then through the router), while traffic from the Primary Bridge Interface (WAN) would, by default, not be permitted inbound.
If there were public servers, for example, a mail and Web server, on the Secondary Bridge Interface (LAN) segment, an Access Rule allowing WAN->LAN traffic for the appropriate IP addresses and services could be added to allow inbound traffic to those servers.
Internal Security Topology depicts a network where the SonicWall will act as the perimeter security device and secure wireless platform. Simultaneously, it will provide L2 Bridge security between the workstation and server segments of the network without having to readdress any of the workstation or servers.
Since both interfaces of the Bridge-Pair are assigned to a Trusted (LAN) zone, the following apply:
|
a
|
The DHCP server would be in the DMZ. DHCP requests from the Workstations would pass through the L2 Bridge to the DHCP server (192.168.0.100), but the DHCP offers from the server would be dropped by the default DMZ->LAN Deny Access Rule. An Access Rule would have to be added, or the default modified, to allow this traffic from the DMZ to the LAN.
|
For detailed instructions on configuring interfaces in Layer 2 Bridge Mode, see Configuring Layer 2 Bridge Mode.
This method is appropriate in networks where both High Availability and Layer 2 Bridge Mode are desired. This example is for SonicWall NSA series appliances, and assumes the use of switches with VLANs configured. See Layer 2 Bridge with High Availability Topology.
Layer 2 Bridge with High Availability Topology
On the Firewall > Access Rules page, click the Configure icon for the intersection of WAN to LAN traffic. Click the Configure icon next to the default rule that implicitly blocks uninitiated traffic from the WAN to the LAN.
In the Edit Rule dialog, select Allow for the Action setting, and then click OK.
In this scenario the WAN interface is used for the following:
On the Network > Interfaces page of the SonicOS management interface, click the Configure icon for the WAN interface, and then assign it an address that can access the Internet so that the appliance can obtain signature updates and communicate with NTP.
The gateway and internal/external DNS address settings will match those of your SSL VPN appliance:
|
•
|
IP address: This must match the address for the internal interface on the SSL VPN appliance.
|
|
•
|
Subnet Mask, Default Gateway, and DNS Server(s): Make these addresses match your SSL VPN appliance settings.
|
For the Management setting, select the HTTPS and Ping check boxes. Click OK to save and activate the changes.
To configure the LAN interface settings, navigate to the Network > Interfaces page and click the Configure icon for the LAN interface.
For the IP Assignment setting, select Layer 2 Bridged Mode. For the Bridged to setting, select X1.
If you also need to pass VLAN tagged traffic, supported on SonicWall NSA series appliances, click the VLAN Filtering tab and add all of the VLANs that will need to be passed.
Click OK to save and activate the change. You may be automatically disconnected from the firewall’s management interface. You can now disconnect your management laptop or desktop from the firewall’s X0 interface and power the firewall off before physically connecting it to your network.
If your SSL VPN appliance is in two-port mode behind a third-party firewall, it is dual-homed.
Make sure that all security services for the SonicWall network security appliance are enabled. See Licensing Services and Activating Firewall Services on Each Zone.
SonicWall Content Filtering Service must be disabled before the device is deployed in conjunction with a SonicWall SMA 1000 Series SSL VPN appliance. On the Network > Zones page, click Configure next to the LAN (X0) zone, clear the Enforce Content Filtering Service check box and then click OK.
If you have not yet changed the administrative password on the SonicWall network security appliance, you can do so on the System > Administration page.
To test access to your network from an external client, connect to the SSL VPN appliance and log in. Once connected, attempt to access to your internal network resources. If there are any problems, review your configuration and see Configuring the Common Settings for L2 Bridge Mode Deployments.