CDP_Appendix
SonicWALL CDP Appendix
Help Overview
Help , a function within the Web Management Interface, redirects the administrator to online SonicWALL CDP help content.
To view the help content, click the
Help
button ![]() in the Web Management Interface toolbar.
in the Web Management Interface toolbar.
Troubleshooting SonicWALL CDP
This section contains troubleshooting information for the SonicWALL CDP. This section contains the following subsections:
Appliance Troubleshooting
This section contains troubleshooting that relates to the SonicWALL CDP appliance.
Symptom: Cannot connect to CDP Appliance
|
|
|
Verify that your workstation/server has network level connectivity to the CDP appliance by attempting to ping the CDP appliance at its configured address. |
|
|
|
Select CDP Manual Connection |
|
|
|
Ensure that an agent firewall is not blocking the CDP Agent User Interface from connecting to the SonicWALL CDP appliance. |
Enable firewall exceptions for Lasso.Client.exe, CDPAutoUpdate.exe and CDPAgent.exe.
Software Troubleshooting
This section contains troubleshooting that relates to the SonicWALL CDP software.
Symptom: Agent will not update
|
|
|
Updates to the agent and appliance are downloaded and installed automatically in a process that is transparent to the user. |
|
|
|
Verify the current version of your product by navigating to the to the System tab in the SonicWALL CDP Agent User Interface. |
Configuring SonicWALL CDP to Use a Public Server Instead of Windows Workgroups
Administrators using a Windows Workgroup may notice that their computer can access the network, but the CDP device cannot. This is because the CDP appliance is not compatible with Windows Workgroups.
Since certain networks demand that you join a Workgroup, the CDP administrator may not be able to upgrade the firmware.
As a solution, the administrator must configure the CDP device with a public server, rather than a private server.
To use a public server you need to configure the CDP Web management interface network settings. To do this, complete the following steps:
|
|
On your Windows machine, navigate to Network Connections . |
|
|
Right-click Local Area Connections . |
|
|
Select Properties . |
|
|
Select TCP/IP Properties . |
|
|
Click OK in each dialog box. |
Symptom: Cannot open Web Management Interface
The Web Management Interface and the Agent User Interface cannot be open simultaneously on the same PC.
Backup and Recovery Troubleshooting
This section contains troubleshooting that relates to the SonicWALL CDP backup and recovery process. See the following:
Symptom: Initial backup seems slow
|
|
|
Because SonicWALL CDP performs file compression and intelligent file management, the initial backup of files and folders may take some time depending on folder volume and size. |
|
|
|
For example, if you are trying to backup 100,000 files averaging 200 KB, it could take up to 24 hours to complete. |
Symptom: Files do not appear to be backing up
|
|
|
By default, SonicWALL CDP uses the System account to access to the folders that are selected for backup. |
|
|
|
The System account will need to be added to the security settings of any directory that you want to backup. |
Symptom: Applications are not available when adding a backup policy
The SonicWALL CDP Agent uses a discovery process to find applications available for backup. The Volume Shadow Copy service and VSS Writer service must not be disabled for the discovery process to work.
Volume Shadow Copy Service
To ensure that the SonicWALL CDP Agent can discover available applications, including Outlook, Outlook Express, System State and Active Directory, Exchange Infostore, Exchange User Mailbox, SQL Server, and Sharepoint, verify that the Volume Shadow Copy service is not disabled.
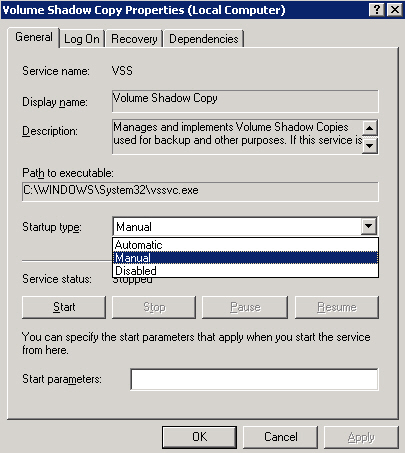
To view and configure the startup method for the Volume Shadow Copy service, perform the following steps:
|
|
Open the Windows Services window by selecting Start > Administrative Tools > Services . |
|
|
If it is Disabled , right-click it and select Properties . |
|
|
In the Volume Shadow Copy Properties window, select Manual from the Startup type drop-down list. |
|
|
Click OK . |
VSS Writer Service
By default on Windows Server 2003 SBS, the VSS Writer service is disabled. To ensure that the SonicWALL CDP Agent can discover Microsoft Exchange and SQL applications, the VSS Writer service must be enabled.
To enable the VSS Writer service, perform the following steps:
|
|
Select Start > Run , type regedit , and then click OK . |
|
|
Double-click the Disable Exchange Writer value. |
|
|
In the Value data text box, change the value from 1 to 0 , and then click OK . |
|
|
Quit the Registry Editor. |
|
|
Open the Windows Services window by selecting Start > Administrative Tools > Services . |
Symptom: A Permission Denied error is seen when restoring User Mailboxes
|
|
|
Verify that you are logged in as “cdpadmin” to the system on which you are trying to restore the user mailboxes. Logging in as “Administrator” and then accessing the Exchange User Mailbox application with “cdpadmin” privileges does not work. |
Recovery when RAID Fails
If you are using the SonicWALL CDP 5040 or 6080 appliances, your data will be protected by the additional failover protection of a RAID system in the event that a drive goes down.
SonicWALL CDP 5040 and 6080 appliances have RAID 5, which involves three or more disks, with block-level data striping with distributed parity across the drive set.
This section contains the following subsections:
If One Disk Fails While Using SonicWALL CDP 5040 / 6080
If one disk fails while using the SonicWALL CDP 5040 or 6080:
|
|
|
Contact SonicWALL Technical Support . Though your system will remain operational, it is necessary to correct the disk failure. |
If Two Disks Fail While Using SonicWALL CDP 5040 / 6080
If two disks fail while using the SonicWALL CDP 5040 or 6080:
Contact SonicWALL Technical Support . Your system will no longer be operational.
Configuring SonicOS Security Services for SonicWALL CDP
When using SonicWALL CDP in conjunction with a SonicWALL firewall appliance, it is necessary to add the CDP appliance to the Security Services exclusion lists.
To configure the Security Services firewall exception list for CDP, perform the following tasks:
Clearing the Enforce Host Tag Search for CFS Setting
To clear the Enforce Host Tag Search for CFS setting, perform the following steps:
|
|
In your browser, navigate to the unlinked Diag page for the SonicWALL network security
appliance, available at: https://<firewall IP address>/diag.html |
|
|
In the left pane, click on the Internal Settings button. |
|
|
Under Security Services Settings in the right pane, clear the Enforce Host Tag Search for CFS checkbox. |
|
|
Click Accept at the top of the page. |
|
|
Click the Close button to return to the SonicOS management interface. |
Setting up Security Services for SonicWALL CDP
This section describes the steps needed when adding a SonicWALL CDP appliance to your network when you are running SonicOS Security Services. To prevent the Security Services from blocking access to your SonicWALL CDP appliance, you must configure SonicOS Security Services with exclusions for the IP address of the appliance.
To configure SonicOS Security Services with exclusions for the SonicWALL CDP appliance, perform the following steps:
|
|
Navigate to the Security Services > Content Filter page. |
|
|
Under CFS Exclusion List , select the Enable CFS Exclusion List checkbox. |
|
|
Click the Add button and add the SonicWALL CDP IP address to the list. |
|
|
Click OK in the Add dialog box, then click Apply on the Content Filter page. |
|
|
Navigate to the Security Services > Client AV Enforcement page. |
|
|
Under Administration , click Configure . |
|
|
In the AV Config View window, under Client Anti-Virus Enforcement , select the Exclude specified address ranges from Client Anti-Virus enforcement radio button. |
|
|
Click the Add button and add the SonicWALL CDP IP address to the list. |
|
|
Click OK in the Add dialog box and Config View window, then click Apply on the Client AV Enforcement page. |
|
|
Navigate to the Security Services > Gateway Anti-Virus page. |
|
|
Under Gateway AV Settings , select the Enable HTTP Byte-Range requests with Gateway AV checkbox. |
|
|
Under Gateway Anti-Virus Global Settings , click the Configure Gateway AV Settings button. |
|
|
In the Gateway AV Config View window, under Gateway AV Exclusion List , select the Enable Gateway AV Exclusion List checkbox. |
|
|
Click the Add button and add the SonicWALL CDP IP address to the list. |
|
|
Click OK in the Add dialog box and Config View window, then click Apply on the Gateway Anti-Virus page. |
|
|
Navigate to the Security Services > Intrusion Prevention page. |
|
|
Under IPS Global Settings , click the Configure IPS Settings button. |
|
|
In the IPS Config View window, under IPS Exclusion List , select the Enable IPS Exclusion List checkbox. |
|
|
Click the Add button and add the SonicWALL CDP IP address to the list. |
|
|
Click OK in the Add dialog box and Config View window, then click Apply on the Intrusion Prevention page. |
|
|
Navigate to the Security Services > Anti-Spyware page. |
|
|
Under Anti-Spyware Global Settings , click the Configure Anti-Spyware Settings button. |
|
|
In the Anti-Spyware Config View window, under Anti-Spyware Exclusion List , select the Enable Anti-Spyware Exclusion List checkbox. |
|
|
Click the Add button and add the SonicWALL CDP IP address to the list. |
|
|
Click OK in the Add dialog box and Config View window, then click Apply on the Anti-Spyware page. |
Technical Frequently Asked Questions
This section contains a list of technical FAQs documented by SonicWALL technical support engineers to address common deployment questions. Table 1 lists the technical FAQs in this section.
|
|
Technical FAQs |
Q: How do I backup mapped drives?
A : SonicWALL CDP cannot backup mapped drives. Agent User Interface software must be installed on the computer where the data for backup resides. If you want to backup data stored on a server that has a mapped drive, you will still need to have the CDP Agent User Interface software installed and configured on the server.
Q: How do I back up SQL database in mixed mode?
A : To back up the SQL data base in mixed mode, the SQL server must be configured for mixed mode authentication. In addition, the SQL account must be part of SQL system administrators, and must have DBO access to the master database and all other application databases that are marked for backup. These settings can be configured using SQL Web Management Interface.
To configure the SQL server for mixed mode authentication, perform the following steps:
|
|
Launch SQL Server Web Management Interface . |
|
|
Right click on the SQL server instance and choose Properties . This will launch the SQL server properties screen. |
|
|
Click the Security tab. |
To set the SQL account as part of SQL system administrators, perform the following steps:
|
|
Expand Security tab under SQL server instance. |
|
|
Click on Logins . |
|
|
Click the Server Roles tab. |
|
|
Select System Administrators . |
To verify that the SQL account has DBO access to master database and all other application databases that are marked for backup, perform the following steps:
|
|
Click on Logins . |
|
|
Click the Database tab. |
|
|
Verify that the account has db_owner selected for all databases intended for backup. |
Command Line Interface Reference
This section describes each SonicWALL CDP Command Line Interface (CLI) command. There are two types of commands: executables and system variables. Typing in a system variable by itself will return the current value of the variable. To update a variable, type it in followed with a proper value. Some executable commands take an argument, but most do not.
bmr
SNWLCLI> bmr [{useradd <username> <passwd> <quota> | userdel <username> | passwdchange <username> <newpasswd> | quotachange <username> <newquota>}]
With no arguments, displays list of Bare Metal Recovery accounts. With arguments, changes the list.
< username >: User account name to be added or deleted, or for which to change the password or quota
Type : System Variable
Defaults : none
Related Commands : none
date
SNWLCLI> date
This variable controls the date on the appliance.
Arguments : none
Type : System Variable
Defaults : none
Related Commands : time
dig
SNWLCLI> dig [@global-server ] [domain ] [q-type ] [q-class ] {q-opt } {global-d-opt } host [@local-server ] {local-d-opt } [ host [@local-server ] {local-d-opt }]
This is the standard dig command from the bind-tools package. Use this command to troubleshoot DNS related issues, such as:
Type : Executable
Defaults :
dns
SNWLCLI> dns [--nameserver <ip >]... [--search <domain >]...
This variable controls the DNS configuration settings on an appliance. Called with no arguments it will return the current configuration.
< ip >: IP address to be assigned to the server
Type : System Variable
Defaults : q-class
drives
SNWLCLI> drives
This function outputs a list of drives registered with the system. Three types of drives are:
Arguments : none
Type : System Variable
Defaults : none
Related Commands : time
exit
SNWLCLI> exit
This function will exit out of the CLI.
Arguments : none
Type : Executable
Defaults : none
fetchurl
SNWLCLI> fetchurl [-q ] <URL >
This function sends an HTTP request and dumps it to standard output.
< URL >: The URL being requested.
Type : Executable
Defaults : none
get
SNWLCLI> get <arg> [arg ]
This function will retrieve configuration parameters.
Arguments : [arg ]: Valid arguments that can be retrieved: ntp, ntpservers, syslogservers, tz
Type : Executable
Defaults : none
gms
SNWLCLI> gms <interval > [<server>…]
This variable stores the interval time between SonicWALL GMS heartbeat messages. Heartbeat messages allow SonicWALL GMS to monitor the SonicWALL CDP appliance.
< interval >: time in seconds between SonicWALL GMS heartbeat messages, set to 0 to disable
Type : System Variable
Defaults : none
help
SNWLCLI> help <command >
This function will print help messages describing available commands from the CLI. Calling it with no arguments will print out a list of available commands. It can take a command name as an argument and will print out more detailed explanation of the given command.
< command >: name of a valid CLI command
Type : Executable
Defaults : all available commands
hostname
SNWLCLI> hostname < fqdn >
This function will display or set current host name. Calling it with no argument will display the current hostname.
< fqdn >: fully qualified domain name
Type : Executable
Defaults : snwl.example.com
interface
SNWLCLI> interface <ifname <ip / bits | ip netmask >>
This variable controls the configuration of interfaces. With no arguments, it will return the configuration of all available interfaces. Passing it an interface name as an argument will return all data related to the given interface. Passing it an interface name and an IP address will overwrite the current configuration of the interface.
< ifname >: name of interface to be configured
Type : System Variable
Defaults : current configuration
Example :
SNWLCLI> interface eth0 192.168.168.169/24
Example Use Case: Authentication Reset
Problem : You have lost the password and IP address for your SonicWALL CDP appliance.
Solution : First, reset the password to the default, and then determine the IP address of the SonicWALL CDP appliance. Connect a USB keyboard and monitor to your SonicWALL CDP appliance and perform the following steps:
|
|
Reboot the SonicWALL CDP appliance, and interrupt the boot process by tapping the ESC key on the keyboard as the boot process progresses, until you are in the GRUB bootloader screen. You will see a variety of options. Select the Authentication Reset option. |
Your SonicWALL CDP will appear to partially reboot, and will perform an additional full reboot once more. Your username/password is reset to admin and the generic password, password .
The SNWLCLI> prompt is displayed.
SNWLCLI> interface eth0
iostat
SNWLCLI> iostat [options...] [<interval >[<count >]]
This is the standard input/output statistics utility.
[options]: see manual for details
Type : Executable
Defaults : none
ntp
SNWLCLI> ntp <on |off > [<default servers | <server > [<server >]...>]
This variable controls the NTP (Network Time Protocol) on an appliance. With no arguments, it will print out the current NTP configuration. In order to change NTP configuration, pass “on” or “off” as a first argument followed by a list of NTP servers to use. Use this command to synchronize the time with a NTP server.
< on >: Enables NTP using currently configured NTP servers
Type : System Variable
Defaults : Current configuration
ping
SNWLCLI> ping [-c COUNT ] [-s SIZE ] [-q ] host
This function is the standard ping function. Use this control to test connectivity. It also tests the appliance’s DNS lookup values.
host : target of ping
Type : Executable
Defaults : Sent SIZE data bytes in packets = 56
quit
SNWLCLI> quit
Arguments : none
Type : Executable
Defaults : none
raidadd
SNWLCLI> raidadd
This function adds a new drive to the RAID array.
Arguments : none
Type : Executable
Defaults : none
Related Commands : raidinfo , raidrebuild , raidremove , raidstatus , raidverify
raidinfo
SNWLCLI> raidinfo
This function outputs information about the RAID devices in the box.
Arguments : none
Type : Executable
Defaults : none
Related Commands: raidadd , raidrebuild , raidremove , raidstatus ,raidverify
raidrebuild
SNWLCLI> raidrebuild <controller> <array> [--drive <drive>]
This function will rebuild a drive within the raid array. With no arguments, it will display the rebuild status and scheduled jobs. With <controller > and <array > arguments, it rebuilds the array using an optional specified drive or the first available spare drive. Scheduling rebuilding operations is recommended as rebuilding an array can take a long time. SonicWALL recommends allowing a full night for the rebuilding process.
< controller >, <array >: rebuilds using an optional specified drive or a first available spare
Type : Executable
Defaults : none
Related Commands : raidadd , raidinfo, raidremove , raidstatus ,raidverify
Problem : A SonicWALL CDP appliance has a degraded RAID array and displays the following information:
SNWLCLI> raidinfo
Solution : Rebuild the RAID drive in the array with valid arguments, by performing the following steps:
|
|
In the CLI, execute raidremove 2 0 , where the controller number is 2 and the drive port is 0. |
This command should not generate any verbose output.
The status of port 0 should change to NOT-PRESENT.
In the status output under Array, you will see two entries: 0 and 1:
|
|
Execute raidrebuild 2 0 – drive 0 , to rebuild array 0. |
You will see the following or similar output:
|
|
Run raidinfo to check status after starting the rebuild. |
The status of the array will show as REBUILDING.
raidremove
SNWLCLI> raidremove <controller>, <port>
This function removes a defective drive from the RAID array. It takes the name of the drive to be removed as an argument.
Type : Executable
Defaults : none
Related Commands: raidadd , raidinfo, raidrebuild , raidstatus ,raidverify
raidstatus
SNWLCLI> raidstatus
This function prints out information about the status of the RAID arrays.
Arguments : none
Type : Executable
Defaults : none
Related Commands : raidadd , raidinfo, raidrebuild , raidremove , raidverify
raidverify
SNWLCLI> raidverify [{--start |--stop } c <controller>.a <array>=<m:h:D|now >|--remove <job>]
This function will verify the RAID array. With no arguments, it will display the verification status and scheduled jobs. Scheduling verifying operations is recommended as they can take a long time. SonicWALL recommends allowing a full night for RAID verification.
< m:h:D > : schedule is expressed as either "now" or m:h:D where m is the minute, h is the hour, and D is the day of week 0-6 where 0 is Sunday, and * in any field means "every time"
Type : Executable
Defaults : displays verification status and scheduled jobs
Related Commands: raidadd , raidinfo, raidrebuild , raidrebuild , raidstatus
reboot
SNWLCLI> reboot
This function will reboot the appliance.
Arguments : none
Type : Executable
Defaults : none
reset
SNWLCLI> reset
This function will reset the appliance to factory defaults.
Arguments : none
Type : Executable
Defaults : none
restart
SNWLCLI> restart <appservices | postgresql | stunnel | webui>
This function restarts running services. It takes a service name as an argument.
Type : Executable
Defaults : none
Related Commands: stop , restart
route
SNWLCLI> route < --add <target > --destination <destination > | --remove <index >>
This function acts like a system variable. With no argument, it will display routes. It can add routes if provided with an interface name or a gateway IP, or remove an existing route. Use this command to troubleshoot routing problems.
< target >: an IP address, net as IP/CIDR, or ‘default’ to be added as a target to the new route
Type : Executable
Defaults : Current routes
Problem : You want to replace the gateway IP for your network, and add a route for it.
Solution : Execute the following command, where the new gateway IP address is 10.10.100.1:
SNWLCLI> route --add 0.0.0.0/0 --destination 10.10.100.1
snmp
SNWLCLI> snmp <on | off>
This variable holds the SNMP status. The current value will be displayed if the command is used without an argument.
Type : System Variable
Defaults : Current configuration
sshd
SNWLCLI> sshd <on | off>
This variable holds the sshd status. The current value will be displayed if the command is used without the argument.
Type : System Variable
Defaults : on
start
SNWLCLI> start < appservices | postgresq | stunnel | webui >
This function starts services. It takes a service name as an argument. The list of services is application-specific.
< service >: service to start
Type : Executable
Defaults : none
Related Commands : stop , restart
stop
SNWLCLI> stop < appservices | postgresq | stunnel | webui >
This function stops running services. It takes a service name as an argument. The list of services is application-specific.
< service >: service to stop
Type : Executable
Defaults : none
Related Commands : start , restart
telnet
SNWLCLI> telnet <host > [<port >]
This functions just like the interactive network communication program with the same name. It takes a host and a port as arguments. Use this tool to establish connectivity issues with a SMTP server. It is also useful to check if outbound SMTP rules on a firewall are well configured
< host >: hostname of telnet target
Type : Executable
Defaults : none
time
SNWLCLI> time [<YYYY/MM/DD hh:mm >][TZ <timezone >]
This function controls the date, time, and the time zone.
< YYYY>: year
Type : System Variable
Defaults : Current configuration
tsr
SNWLCLI> tsr
This function outputs an internal system state report. It does not take any arguments.
Arguments : none
Type : Executable
Defaults : none
tzlist
SNWLCLI> tzlist
This function outputs a list of all available time zones.
Arguments : none
Type : Executable
Defaults : none
version
SNWLCLI> version
This function displays the firmware and application version.
Arguments : none
Type : Executable
Defaults : none
Glossary
Active Directory : A centralized directory service system produced by Microsoft that automates network management of user data, security and resources, and enables interoperation with other directories. Active Directory is designed especially for distributed networking environments.
Advanced Encryption Standard (AES) : A recent U.S. government encryption standard designed as the replacement for the aging Data Encryption Standard (DES).
Agent : A server, laptop or PC to be backed up using SonicWALL CDP.
Agent Service : A SonicWALL CDP software installed automatically on agents with Agent User Interface software. Agent Service communicates with the SonicWALL CDP appliance.
Agent User Interface : A SonicWALL CDP software installed on agents. Agent User Interface is a user interface for users of SonicWALL CDP agents that allows data backup and recovery configuration, as administered by the SonicWALL CDP Web Management Interface.
Backup Task : A defined File Set and Schedule are combined into a Backup Task for execution. Without a Backup Task, no backups will occur.
CDP Backup Method : One method of configuring file and folder backups on agents. The CDP method corresponds to the method used in the SonicWALL CDP 5.1 and earlier releases. Files are backed up individually rather than as a File Set, with new revisions created continuously as changes occur, up to a set limit of revisions.
Data De-duplication : The process used by SonicWALL CDP to back up only the blocks of data that have changed since the last scheduled backup. Metadata is used to map the changes between different revisions so that any revision can be restored correctly.
Domain Name System/Service (DNS) : An Internet service that translates domain names into IP addresses. Because domain names are alphabetic, they're easier to remember. The internet however, is really based on IP addresses. Every time you use a domain, therefore, a DNS service must translate the name into the corresponding IP addresses.
Downstream CDP appliance : A local CDP appliance on your LAN.
Dynamic Host Configuration Protocol (DHCP) : A Protocol for assigning dynamic IP addresses to devices on a network. With dynamic addressing, a device can have a different IP address every time it connects to the network. In some systems, the device’s IP address can even change while it is still connected. DHCP also supports a mix of static and dynamic IP addresses.
Dynamic addressing simplifies network administration because the software keeps track of IP addresses rather than requiring an administrator to manage the task. This means that a new computer can be added to a network without the hassle of manually assigning it a unique IP address. Many Internet Service Providers (ISPs) use dynamic IP addressing for dial-up users.
Web Management Interface : A SonicWALL CDP software installed on the SonicWALL CDP administrator’s computer.
File Allocation Table (FAT) : A table that the operating system uses to locate files on a disk. Due to fragmentation a file may be divided into many sections that are scattered around the disk. The FAT keeps track of all the pieces.
FileSet Backup Method : One method of configuring file and folder backups on agents. The FileSet method is new in the SonicWALL CDP 6.0 release. Files are backed up as a set of files for best synchronization, with new revisions created according to a configured schedule. Data de-duplication is used to back up only the blocks of data that have changed between scheduled intervals. The defined File Set and Schedule are combined into a Backup Task for execution.
High Availability : The capability of a mission-critical device, such as a SonicWALL security gateway, to automatically failover to a backup device in the event of a hardware failure on the primary unit.
Hyper Text Transfer Protocol (HTTP) : The underlying protocol used by the World Wide Web. HTTP defines how messages are formatted and transmitted, and what actions Web servers and browsers should take in response to various commands.
IP address (Internet Protocol) : An Identifier for a computer device on a TCP/IP network. Networks using the TCP/IP protocol route message based on the IP address of the destination. The format of an IP address is a 32-bit numeric address written as four numbers separated by periods. Each number can be zero to 255. For example, 1.160.10.240 could be an IP address.
Local Area Network (LAN) : A computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected to other LANs over any distance using telephone lines and radio waves. A systems of LANs connected in this way is called a wide-area network (WAN).
Master Boot Record (MBR) : A small program that is executed when a computer boots up. Typically, the MBR resides on the first sector of the hard disk. The program begins the boot process by looking up the partition table to determine which partition to use for booting. It then transfers program control to the boot sector of that partition, which continues the boot process.
Policy : A set of rules administered from the SonicWALL CDP Web Management Interface. Policies are assigned directly to agents and define backup rights, quota, and other SonicWALL CDP capabilities.
Quota : The maximum amount of data a SonicWALL CDP agent can back up to the SonicWALL CDP appliance. The quota can be managed according to the number of files, the size of data on the appliance disk, or the size of the files being backed up. The two sizes can differ due to the data de-duplication feature.
Redundant Array of Independent Disks (RAID) : A failover method used to protect against data loss in the event of disk failure.
Static IP address : An IP address that is unique and unchanging. Unlike dynamic IP addresses, a static IP address remains the same when you make a new Internet connection.
Upstream CDP appliance : An offsite CDP appliance on your WAN that is used for secure backup and recovery.
User Datagram Protocol (UDP) : A connectionless protocol that sends and receive datagrams over an internet protocol (IP) network.
Universal Serial Bus (USB) : An external bus standard that supports data transfer rates of 12Mbps. A single USB port can be used to connect up to 127 peripheral devices, such as mice, modems, and keyboard. USB also supports Plug-and-Play installation and hot plugging.
Related Documents
This section contains related documentation specific to SonicWALL CDP solutions.
User Guides
All online documentation for SonicWALL user’s guides is available on the SonicWALL Support Web site at: http://www.sonicwall.com/us/support.html .
Contributors
Susan Weigand has over seven years of network security documentation experience. Prior to becoming a SonicWALL Senior Technical Writer, she worked for over ten years as a UNIX developer, and spent three years as a QA engineer at Cisco Systems and Symantec. At Symantec, Susan authored the Symantec Network Security 7100 Series Implementation Guide and contributed to other endpoint security and network security documents. She has taken a turn as the lead author on every SonicWALL product line over the past four years, preparing both administrator and user guides. Susan has also authored over 20 technical guides on network security topics and secure remote access solutions, including application firewall and control, high availability solutions, packet capture, switching, layer 2 bypass, single sign-on, custom reporting, application backup and restore, and Citrix access solutions. Susan holds two B.A. degrees in Computer Science and History, both with honors, and a Certificate in Internet Programming from the University of California at Santa Cruz.
Jean-Marc Catalaa , SonicWALL Curriculum Developer, holds a B.S. in Electrical Engineering from San Jose State University. Jean-Marc has written numerous technical documents and developed curriculum based on topics including multi-processor architecture, networking and wireless communications. He has taught over 40 classes about wireless communication in English, Spanish, Portuguese and Italian, adjusting training style for worldwide audiences and emphasizing hands-on learning.
Patrick Lydon has over five years of experience as a SonicWALL Technical Writer. He has authored over 20 technical guides on UTM, secure remote access solutions, Virtual Access Points, wireless site surveying, and RF monitoring. Patrick has also received an International Photography Award for Fine Art Portraiture . Patrick holds a B.A. degree in Design Studies with concentration in Graphic Design from San Jose State University.
Angela Mendoza is a Technical Writer with SonicWALL. She has a B.A. in English Literature, with an emphasis in Creative Writing, and a minor in Music from San Jose State University. Angela has earned distinction with several 2008 Phelan Awards in the genres of Best Short Story and Best Metrical Poetry from San Jose State University.
Dave Parry is SonicWALL’s Director of Platform Usability. Dave is one of SonicWALL's lead feature developers and is also the keeper of nearly a decade of SonicWALL institutional knowledge. Dave has designed and deployed networks for more than 100 companies worldwide, including a number of SonicWALL's most advanced and complicated customer networks. He has authored over one hundred SonicOS technotes for the SonicWALL Knowledge Base. Dave has also been instrumental in network troubleshooting and design, interoperability testing, lab maintenance, and performance testing. Dave designed and maintains the SonicWALL Live Demo site: http://livedemo.sonicwall.com/
Khai Tran has more than ten years of experience in networking documentation and works in San Jose, California, as technical documentation manager for SonicWALL. He leads SonicWALL’s technical documentation teams, which have received numerous 5-star reviews in 2008 from the industry’s leading publications and reviewers. Khai was a lead author of Cisco IOS NetFlow Services Integrated Solutions Guide, and a contributing author to Cisco IOS Switching Services Configuration Guide. He has also authored enterprise and service provider network solution guides for Boeing Aerospace and Electronic Arts. He holds a B.A. degree in English Modern Literature from U.C. Santa Cruz, a certificate in Technical Communications, and a Bilingual Teaching Credential from San Jose State University.