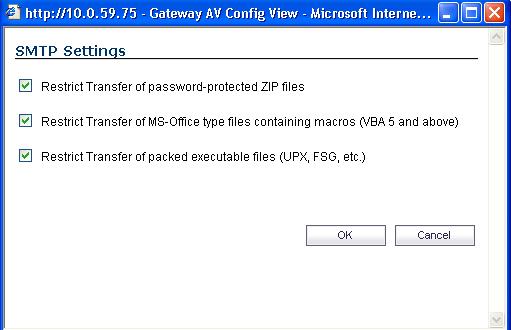
For each protocol you can restrict the transfer of files with specific attributes by clicking on the Settings button under the protocol in the Gateway Anti-Virus Global Settings section.
|
•
|
Restrict Transfer of password-protected Zip files - Disables the transfer of password protected ZIP files over any enabled protocol. This option only functions on protocols (e.g. HTTP, FTP, SMTP) that are enabled for inspection.
|
|
•
|
Restrict Transfer of MS-Office type files containing macros (VBA 5 and above) - Disables the transfers of any MS Office 97 and above files that contain VBA macros.
|
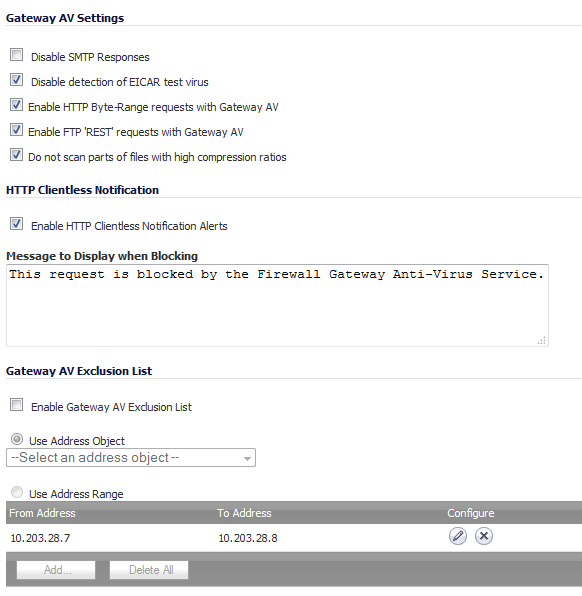
Clicking the Configure Gateway AV Settings button at the bottom of the Gateway Anti-Virus Global Settings section displays the Gateway AV Config View window, which allows you to configure clientless notification alerts and create a Dell SonicWALL GAV exclusion list.
If you want to suppress the sending of e-mail messages (SMTP) to clients from Dell SonicWALL GAV when a virus is detected in an e-mail or attachment, check the Disable SMTP Responses checkbox.
Optionally, you can configure the timeout for the HTTP Clientless Notification on the Security Services > Summary page under the Security Services Summary heading.