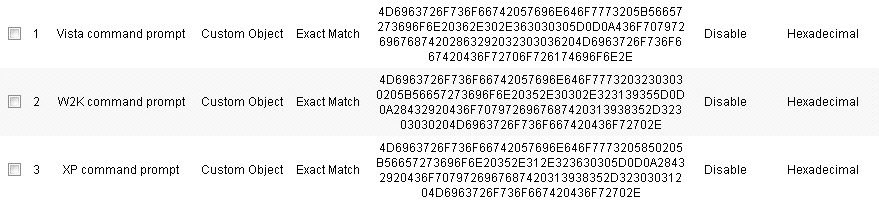
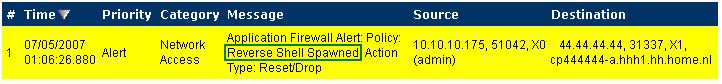
The reverse shell exploit is an attack that you can prevent by using Application Control’s custom signature capability (See Custom Signature ). A reverse shell exploit could be used by an attacker if he or she is successful in gaining access to your system by means of a Zero-day exploit. A Zero-day exploit refers to an attack whose signature is not yet recognized by security software.
The netcat tool offers – among other features – the ability to bind a program’s output to an outbound or a listening connection. The following usage examples show how to setup a listening “Command Prompt Daemon” or how to connect to a remote endpoint and provide an interactive command prompt:
A Windows prompt will be available to hosts connecting to port 23 (the -l option stands for listen mode as opposed to the default, implicit, connect mode).
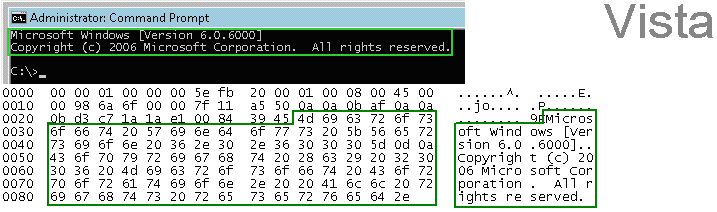
To capture the data, launch Wireshark and click Capture > Interfaces to open a capture dialog. Start a capture on the interface with the netcat traffic. As soon as the capture begins, run the netcat command and then stop the capture.
The hexadecimal data can be exported to a text file for trimming off the packet header, unneeded or variable parts and spaces. The relevant portion here is “Microsoft… reserved.” You can use the Wireshark hexadecimal payload export capability for this. For information about Wireshark, see Wireshark .
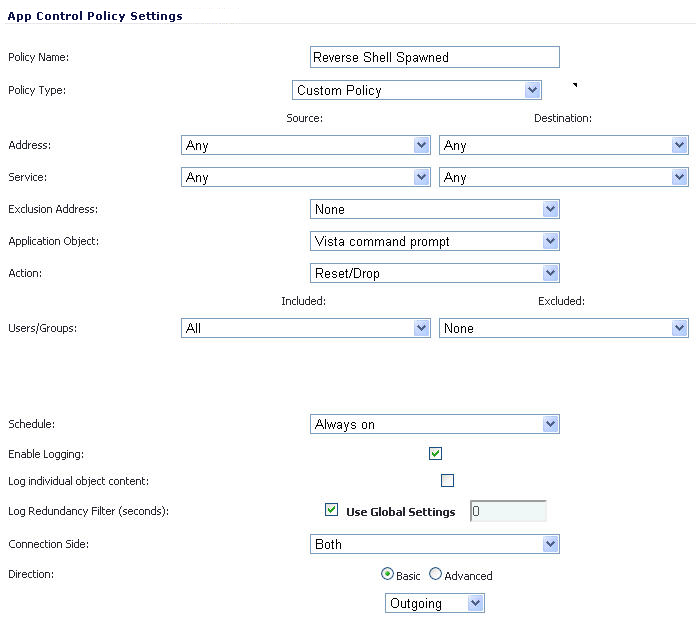
After creating the match objects, you can define a policy that uses them. The image below shows the other policy settings. This example as shown is specific for reverse shells in both the Policy Name and the Direction settings. As mentioned, it may also be tailored for a wider scope with the Direction setting changed to Both and a more generic name.