|
•
|
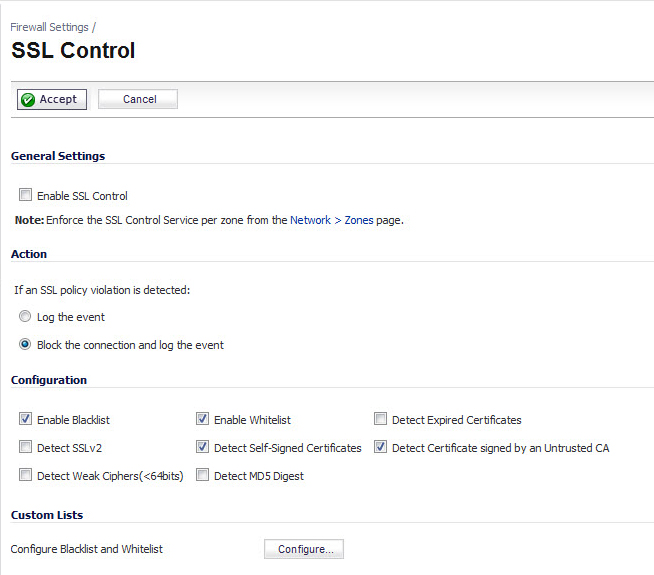
Enable SSL Control – The global setting for SSL Control. This must be enabled for SSL Control applied to zones to be effective.
|
|
•
|
Log the event – If an SSL policy violation, as defined within the Configuration section below, is detected, the event will be logged, but the SSL connection will be allowed to continue.
|
|
•
|
Block the connection and log the event – In the event of a policy violation, the connection will be blocked and the event will be logged.
|
|
•
|
Enable Blacklist – Controls detection of the entries in the blacklist, as configured in the Configure Lists section below.
|
|
•
|
Enable Whitelist – Controls detection of the entries in the whitelist, as configured in the Configure Lists section below. Whitelisted entries will take precedence over all other SSL control settings.
|
|
•
|
Detect Expired Certificates – Controls detection of certificates whose start date is before the current system time, or whose end date is beyond the current system time. Date validation depends on the firewall’s System Time. Make sure your System Time is set correctly, preferably synchronized with NTP, on the System > Time page.
|
|
•
|
Detect SSLv2 – Controls detection of SSLv2 exchanges. SSLv2 is known to be susceptible to cipher downgrade attacks because it does not perform integrity checking on the handshake. Best practices recommend using SSLv3 or TLS in its place.
|
|
•
|
Detect Self-signed certificates – Controls the detection of certificates where both the issuer and the subject have the same common name.
|
|
•
|
Detect Certificates signed by an Untrusted CA – Controls the detection of certificates where the issuer’s certificate is not in the firewall’s System > Certificates trusted store.
|
|
•
|
Detect Weak Ciphers (<64 bits) – Controls the detection of SSL sessions negotiated with symmetric ciphers less than 64 bits, commonly indicating export cipher usage.
|
|
•
|
Detect MD5 Digest – Controls the detection of certificates that were created using an MD5 Hash.
|
|
•
|
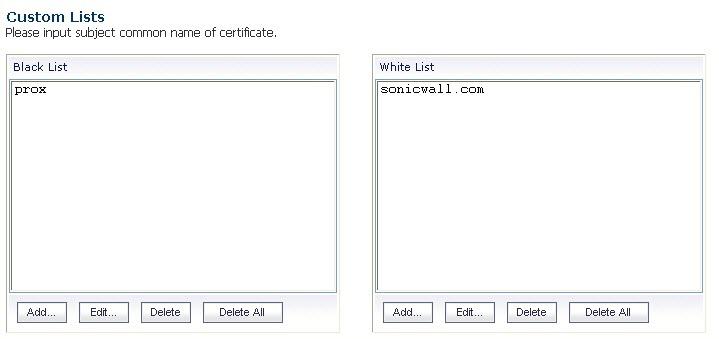
Configure Blacklist and Whitelist – Allows the administrator to define strings for matching common names in SSL certificates. Entries are case-insensitive, and will be used in pattern-matching fashion, for example:
|
|
https://www.sonicwall.com, https://csm.demo.sonicwall.com, https://mysonicwall.com, https://supersonicwall.computers.org, https://67.115.118.87 1
|
||
|
https://proxify.org, https://www.proxify.org, https://megaproxy.com, https://1070652204 2
|
https://www.freeproxy.ru 3
|
To configure the Whitelist and Blacklist, click the Configure button to bring up the following window.