For information on activating Network Anti-Virus Service, see Activating the Gateway Anti-Virus, Anti-Spyware, and IPS License .
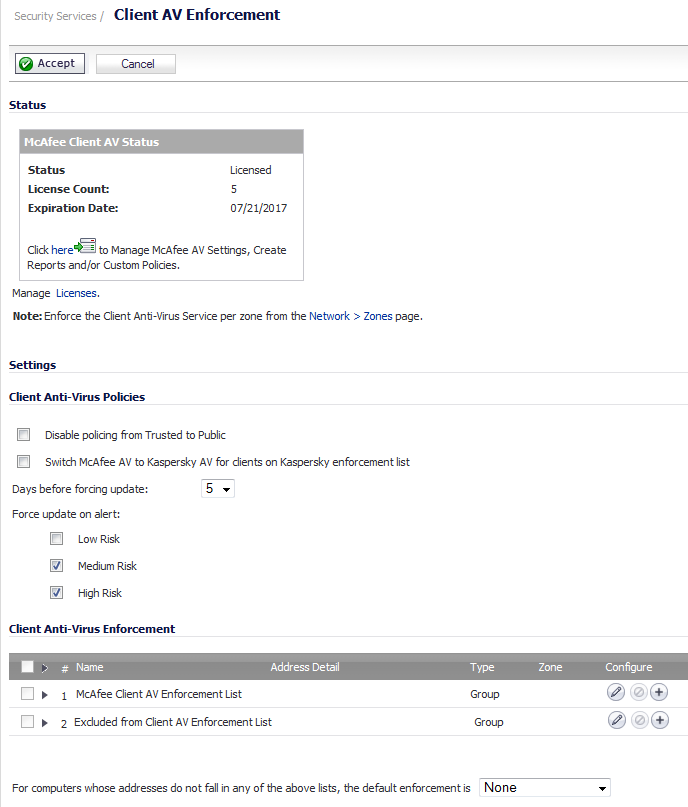
The following features are available in the Client Anti-Virus Policies section:
|
•
|
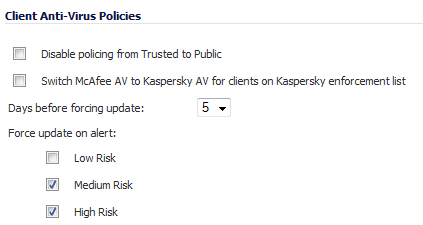
Disable policing from Trusted to Public - Cleared, this option enforces anti-virus policies on computers located on Trusted zones. Choosing this option allows computers on a trusted zone (such as a LAN) to access computers on public zones (such as DMZ), even if anti-virus software is not installed on the LAN computers.
|
|
•
|
Switch McAfee AV to Kaspersky AV for clients on Kaspersky enforcement list - When selected, uses Kaspersky AV for clients on the Kaspersky enforcement list instead of McAfee AV.
|
|
•
|
Days before forcing update - This feature defines the maximum number of days of access to the Internet before the SonicWALL requires the latest virus date files to be downloaded. Select from 0 to 5 days; 5 is the default.
|
|
•
|
Force update on alert - Dell SonicWALL broadcasts virus alerts to all SonicWALL appliances with an Anti-Virus subscription. Three levels of alerts are available, and you may select more than one. When an alert is received with this option selected, users are upgraded to the latest version of VirusScan ASaP before they can access the Internet. This option overrides the Maximum number of days allowed before forcing update selection. In addition, every virus alert is logged, and an alert message is sent to the administrator.
|
|
•
|
Low Risk - A virus that is not reported in the field and is considered unlikely to be found in the field in the future has a low risk. Even if such a virus includes a very serious or unforeseeable damage payload, its risk is still low.
|
|
•
|
Medium Risk - If a virus is found in the field, and if it uses a less common infection mechanism, it is considered to be medium risk. If its prevalence stays low and its payload is not serious, it can be downgraded to a low risk. Similarly it can be upgraded to high risk if the virus becomes more and more widespread.
|
|
•
|
High Risk - To be assigned a high risk rating, it is necessary that a virus is reported frequently in the field. Additionally, the payload must have the ability to cause at least some serious damage. If it causes very serious or unforeseeable damage, high risk may be assigned even with a lower level of prevalence.
|
|
•
|
Enforce Anti-Virus policies for all computers - Selecting this option forces computers to install VirusScan ASaP in order to access the Internet or the DMZ. This is the default configuration.
|
|
•
|
Include specified address range in the Anti-Virus enforcement - Choosing this option allows the administrator to define ranges of IP addresses to receive Anti-Virus enforcement. If you select this option, specify a range of IP addresses to be enforced. Any computer requiring enforcement needs a static IP address within the specified range of IP addresses. Up to 64 IP address ranges can be entered for enforcement. Click Add to display the Add AV Range Entry window and then enter the IP address range.
|
|
•
|
Exclude specified address range in the Anti-Virus enforcement - Selecting this option allows the administrator to define ranges of IP addresses that are exempt from Anti-Virus enforcement. If you select this option, specify the range of IP addresses that are exempt. Any computer requiring unrestricted Internet access needs a static IP address within the specified range of IP addresses. Up to 64 IP address ranges can be entered. Click Add to display the Add AV Range Entry window and then enter the IP address range.
|