|
•
|
No Single Point of Failure in the Core Network: In an Active/Active Clustering Full-Mesh deployment, there is no single point of failure in the entire core network, not just for the firewalls. An alternative path for a traffic flow is always available in case there are simultaneous failures of switch, router, firewall on a path, thus providing the highest levels of availability.
|
|
•
|
Port Redundancy: Active/Active Clustering Full-Mesh utilizes port redundancy in addition to HA redundancy within each Cluster Node, and node level redundancy within the cluster. With port redundancy, a backup link will take over in a transparent manner if the primary port fails. This prevents the need for device level failover.
|
Redundant ports can be used along with Active/Active Clustering. If one port should have a fault, the traffic is seamlessly handled through the redundant port without causing an HA or Active/Active failover. A Redundant Port field in the Network > Interfaces > Edit Interface page becomes available when Active/Active Clustering is enabled.
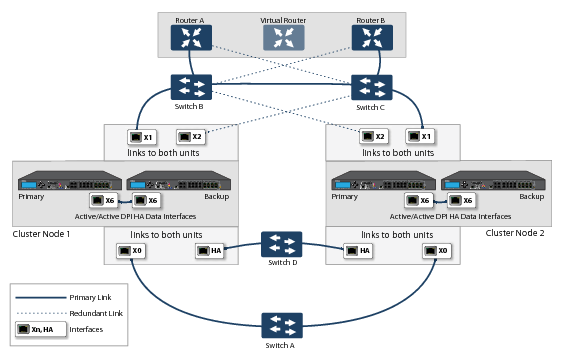
Figure 38. WAN side redundancy
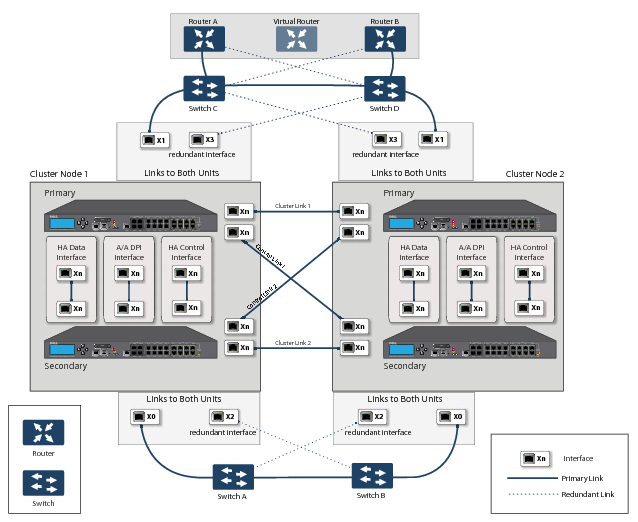
For more information about Full Mesh deployments, see the Active/Active Clustering Full Mesh Deployment Technote.
Figure 39. Active/Active four-unit cluster full mesh
|
a
|
|
a
|
|
2
|
On the High Availability > Settings page:
|
|
g
|
Click Submit.
|
|
3
|
On the Network > Interfaces page:
|
|
4
|
On the High Availability > Monitoring page, add the monitoring/management IP addresses either on X0 or X1 for each unit in the cluster.
|
|
6
|
|
1
|
Device Failures: Traffic should continue to flow through both Cluster Nodes in each of the following device failures:
|
|
2
|
Link Failures: Traffic should continue to flow in each of the following link failures:
|
|
a
|
|
b
|
|
c
|