|
•
|
Traffic legitimacy - Stateful inspection of every VoIP signaling and media packet traversing the firewall ensures all traffic is legitimate. Packets that exploit implementation flaws, causing effects such as buffer overflows in the target device, are the weapons of choice for many attackers. Dell SonicWALL network security appliances detect and discard malformed and invalid packets before they reach their intended target.
|
|
•
|
Application-layer protection for VoIP protocols - Full protection from application-level VoIP exploits through SonicWALL Intrusion Prevention Service (IPS). IPS integrates a configurable, high performance scanning engine with a dynamically updated and provisioned database of attack and vulnerability signatures to protect networks against sophisticated Trojans and polymorphic threats. SonicWALL extends its IPS signature database with a family of VoIP-specific signatures designed to prevent malicious traffic from reaching protected VoIP phones and servers.
|
|
•
|
DoS and DDoS attack protection - Prevention of DoS and DDoS attacks, such as the SYN Flood, Ping of Death, and LAND (IP) attack, which are designed to disable a network or service.
|
|
•
|
Stateful monitoring - Stateful monitoring ensures that packets, even though appearing valid in themselves, are appropriate for the current state of their associated VoIP connection.
|
|
•
|
Encrypted VoIP Device Support - SonicWALL supports VoIP devices capable of using encryption to protect the media exchange within a VoIP conversation or secure VoIP devices that do not support encrypted media using IPsec VPNs to protect VoIP calls.
|
|
•
|
Application-Layer Protection - SonicWALL delivers full protection from application-level VoIP exploits through SonicWALL Intrusion Prevention Service (IPS). SonicWALL IPS is built on a configurable, high performance Deep Packet Inspection engine that provides extended protection of key network services including VoIP, Windows services, and DNS. The extensible signature language used in SonicWALL’s Deep Packet Inspection engine also provides proactive defense against newly discovered application and protocol vulnerabilities. Signature granularity allows SonicWALL IPS to detect and prevent attacks based on a global, attack group, or per-signature basis to provide maximum flexibility and control false positives.
|
|
•
|
VoIP over Wireless LAN (WLAN) - SonicWALL extends complete VoIP security to attached wireless networks with its Distributed Wireless Solution. All of the security features provided to VoIP devices attached to a wired network behind a SonicWALL are also provided to VoIP devices using a wireless network.
|
|
•
|
Bandwidth Management (BWM) and Quality-of-Service (QoS) - Bandwidth management (both ingress and egress) can be used to ensure that bandwidth remains available for time-sensitive VoIP traffic. BWM is integrated into SonicWALL Quality of Service (QoS) features to provide predictability that is vital for certain types of applications.
|
|
•
|
WAN redundancy and load balancing - WAN redundancy and load balancing allows for an interface to act as a secondary WAN port. This secondary WAN port can be used in a simple active/passive setup, where traffic is only routed through it if the primary WAN port is down or unavailable. Load balancing can be performed by splitting the routing of traffic based on destination.
|
|
•
|
High availability - High availability is provided by SonicOS high availability, which ensures reliable, continuous connectivity in the event of a system failure.
|
|
•
|
Plug-and-protect support for VoIP devices - With SonicOS, VoIP device adds, changes, and removals are handled automatically, ensuring that no VoIP device is left unprotected. Using advanced monitoring and tracking technology, a VoIP device is automatically protected as soon as it is plugged into the network behind a firewall.
|
|
•
|
Full syntax validation of all VoIP signaling packets - Received signaling packets are fully parsed within SonicOS to ensure they comply with the syntax defined within their associated standard. By performing syntax validation, the firewall can ensure that malformed packets are not permitted to pass through and adversely affect their intended target.
|
|
•
|
Support for dynamic setup and tracking of media streams - SonicOS tracks each VoIP call from the first signaling packet requesting a call setup, to the point where the call ends. Only based on the successful call progress are additional ports opened (for additional signaling and media exchange) between the calling and called party.
|
|
•
|
Validation of headers for all media packets - SonicOS examines and monitors the headers within media packets to allow detection and discarding of out-of-sequence and retransmitted packets (beyond window). Also, by ensuring that a valid header exists, invalid media packets are detected and discarded. By tracking the media streams as well as the signaling, SonicWALL provides protection for the entire VoIP session.
|
|
•
|
Configurable inactivity timeouts for signaling and media - In order to ensure that dropped VoIP connections do not stay open indefinitely, SonicOS monitors the usage of signaling and media streams associated with a VoIP session. Streams that are idle for more than the configured timeout are shut down to prevent potential security holes.
|
|
•
|
SonicOS allows the administrator to control incoming calls - By requiring that all incoming calls are authorized and authenticated by the H.323 Gatekeeper or SIP Proxy, SonicOS can block unauthorized and spam calls. This allows the administrator to be sure that the VoIP network is being used only for those calls authorized by the company.
|
|
•
|
Comprehensive monitoring and reporting - For all supported VoIP protocols, SonicOS offers extensive monitoring and troubleshooting tools:
|
|
•
|
|
•
|
|
•
|
|
•
|
SonicOS supports media streams from any CODEC - Media streams carry audio and video signals that have been processed by a hardware/software CODEC (COder/DECoder) within the VoIP device. CODECs use coding and compression techniques to reduce the amount of data required to represent audio/video signals. Some examples of CODECs are:
|
•
|
|
•
|
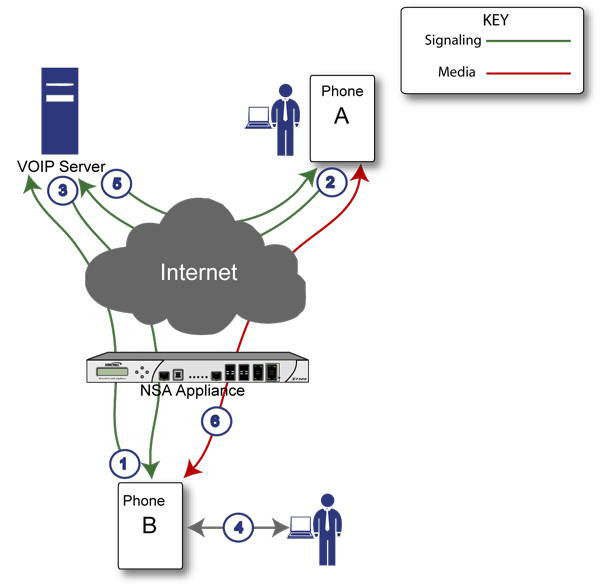
Figure 26. Incoming calls sequence of events
|
1
|
Phone B registers with VoIP server - The firewall builds a database of the accessible IP phones behind it by monitoring the outgoing VoIP registration requests. SonicOS translates between phone B’s private IP address and the firewall’s public IP address used in registration messages. The VoIP server is unaware that phone B is behind a firewall and has a private IP address—it associates phone B with the firewall’s public IP address.
|
|
2
|
Phone A initiates a call to phone B - Phone A initiates a call to phone B using a phone number or alias. When sending this information to the VoIP server, it also provides details about the media types and formats it can support as well as the corresponding IP addresses and ports.
|
|
3
|
VoIP Server validates the call request and sends the request to phone B - The VoIP server sends the call request to the firewall’s public IP address. When it reaches the firewall, SonicOS validates the source and content of the request. The firewall then determines phone B’s private IP address.
|
|
4
|
Phone B rings and is answered - When phone B is answered, it returns information to the VoIP server for the media types and formats it supports as well as the corresponding IP addresses and ports. SonicOS translates this private IP information to use the firewall’s public IP address for messages to the VoIP server.
|
|
5
|
VoIP server returns phone B media IP information to phone A - Phone A now has enough information to begin exchanging media with Phone B. Phone A does not know that Phone B is behind a firewall, as it was given the public address of the firewall by the VoIP Server.
|
|
6
|
Phone A and phone B exchange audio/video/data through the VoIP server - Using the internal database, SonicOS ensures that media comes from only Phone A and is only using the specific media streams permitted by Phone B.
|
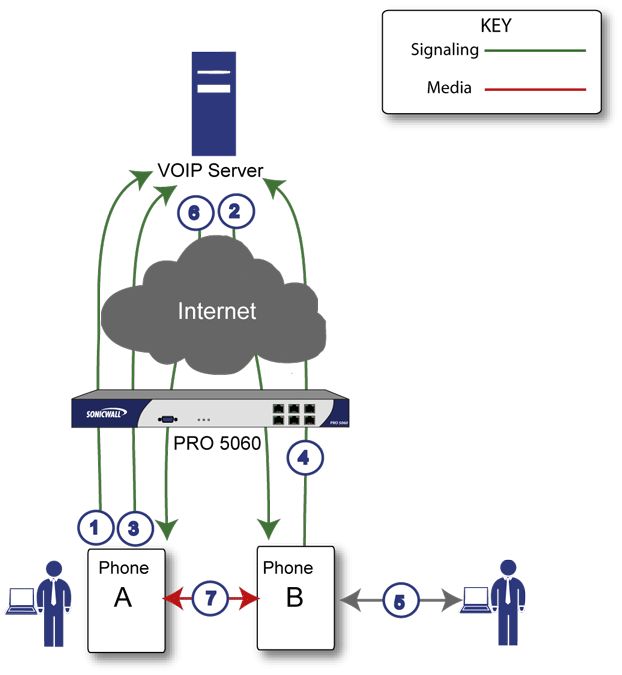
Figure 27. Local VoIP calls sequence of events
|
1
|
Phones A and B register with VoIP server - The firewall builds a database of the accessible IP phones behind it by monitoring the outgoing VoIP registration requests. SonicOS translates between the phones’ private IP addresses and the firewall’s public IP address. The VoIP server is unaware that the phones are behind a firewall. It associates the same IP address for both phones, but different port numbers.
|
|
2
|
Phone A initiates a call to phone B by sending a request to the VoIP server - Even though they are behind the same firewall, phone A does not know Phone B’s IP address. Phone A initiates a call to phone B using a phone number or alias.
|
|
3
|
VoIP Server validates the call request and sends the request to phone B - The VoIP server sends the call request to the firewall’s public IP address.The firewall then determines phone B’s private IP address.
|
|
4
|
Phone B rings and is answered - When phone B is answered, the firewall translate its private IP information to use the firewall’s public IP address for messages to the VoIP server.
|
|
5
|
VoIP Server returns phone B media IP information to phone A - Both the called and calling party information within the messages are translated by SonicOS back to the private addresses and ports for phone A and phone B.
|
|
6
|
Phone A and phone B directly exchange audio/video/data - The firewall routes traffic directly between the two phones over the LAN. Directly connecting the two phones reduces the bandwidth requirements for transmitting data to the VoIP server and eliminates the need for the firewall to perform address translation.
|