|
1
|
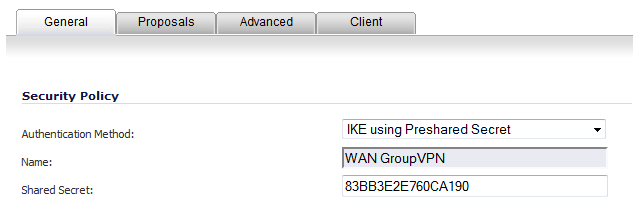
Navigate to VPN > Settings.
|
|
2
|
|
3
|
In the General tab, IKE using Preshared Secret is the default setting for Authentication Method. A Shared Secret is generated automatically by the SonicOS 5.9 Administration Guide security appliance in the Shared Secret field, or you can generate your own shared secret. Shared Secrets must be minimum of four characters.
|
|
4
|
Click the Proposals tab to continue the configuration process.
|
|
5
|
In the IKE (Phase 1) Proposal section, use the following settings:
|
|
•
|
Select the DH Group from the DH Group drop-down menu.
|
|
•
|
|
•
|
Select the desired authentication method from the Authentication drop-down menu.
|
|
•
|
Enter a value in the Life Time (seconds) field. The default setting of 28800 forces the tunnel to renegotiate and exchange keys every 8 hours.
|
|
6
|
In the IPsec (Phase 2) Proposal section, select the following settings:
|
|
•
|
Select the desired protocol from the Protocol drop-down menu.
|
|
•
|
|
•
|
Select the desired authentication method from the Authentication drop-down menu.
|
|
•
|
Select Enable Perfect Forward Secrecy if you want an additional Diffie-Hellman key exchange as an added layer of security. The DH Group drop-down menu displays.
|
|
•
|
|
•
|
Enter a value in the Life Time (seconds) field. The default setting of 28800 forces the tunnel to renegotiate and exchange keys every 8 hours.
|
|
7
|
Click the Advanced tab.
|
|
•
|
Disable IPsec Anti-Replay - Disables Anti-Replay, which is a form of partial sequence integrity that detects arrival of duplicate IP datagrams (within a constrained window).
|
|
•
|
Enable Windows Networking (NetBIOS) broadcast - Allows access to remote network resources by browsing the Windows® Network Neighborhood.
|
|
•
|
Enable Multicast - Enables IP multicasting traffic, such as streaming audio (including VoIP) and video applications, to pass through the VPN tunnel.
|
|
•
|
Accept Multiple Proposals for Clients - Allows L2TP, iOS, and Windows clients to connect to the SonicOS L2TP server at the same time.
|
|
•
|
Enable IKE Mode Configuration - Allows SonicOS to assign internal IP address, DNS Server, or WINS Server to third-party clients such as iOS devices or Avaya IP phones.
|
|
•
|
Management via this SA: - If using the VPN policy to manage the SonicWall security appliance, select the management method, either HTTP, HTTPS, SSH, or SNMP.
|
|
•
|
Default Gateway - Allows you to specify the IP address of the default network route for incoming IPsec packets for this VPN policy.
|
|
•
|
Require Authentication of VPN Clients via XAUTH - Requires that all inbound traffic on this VPN tunnel is from an authenticated user. Unauthenticated traffic is not allowed on the VPN tunnel. The Trusted users group is selected by default. You can select another user group or Everyone from User Group for XAUTH users or create a new group.
|
|
•
|
Allow Unauthenticated VPN Client Access - Allows you to enable unauthenticated VPN client access. If you uncheck Require Authentication of VPN Clients via XAUTH, the Allow Unauthenticated VPN Client Access menu is activated. Select an Address Object or Address Group from the drop-down menu of predefined options, or select Create new address object or Create new address group to create a new one.
|
|
9
|
Click the Client tab, select any of the following settings you want to apply to your GroupVPN policy.
|
|
•
|
Cache XAUTH User Name and Password on Client - Allows the Global VPN Client to cache the user name and password.
|
|
•
|
Never - Global VPN Client is not allowed to cache the username and password. The user will be prompted for a username and password when the connection is enabled, and also every time there is an IKE Phase 1 rekey.
|
|
•
|
Single Session - Global VPN Client user prompted for username and password each time the connection is enabled and will be valid until the connection is disabled. The username and password is used through IKE Phase 1 rekey.
|
|
•
|
Always - Global VPN Client user prompted for username and password only once when connection is enabled. When prompted, the user will be given the option of caching the username and password.
|
|
•
|
Virtual Adapter Settings - The use of the Virtual Adapter by the Global VPN Client (GVC) is dependent upon a DHCP server, either the internal SonicOS or a specified external DHCP server, to allocate addresses to the Virtual Adapter. In instances where predictable addressing was a requirement, it is necessary to obtain the MAC address of the Virtual Adapter and to create a DHCP lease reservation. To reduce the administrative burden of providing predictable Virtual Adapter addressing, you can configure the GroupVPN to accept static addressing of the Virtual Adapter's IP configuration. This feature requires the use of GVC version 3.0 or later.
|
|
•
|
None - A Virtual Adapter will not be used by this GroupVPN connection.
|
|
•
|
DHCP Lease - The Virtual Adapter will obtain its IP configuration from the DHCP Server only, as configured in the VPN > DHCP over VPN page.
|
|
•
|
DHCP Lease or Manual Configuration - When the GVC connects to the SonicWall, the policy from the SonicWall instructs the GVC to use a Virtual Adapter, but the DHCP messages are suppressed if the Virtual Adapter has been manually configured. The configured value is recorded by the SonicWall so that it can proxy ARP for the manually assigned IP address. By design, there are currently no limitations on IP address assignments for the Virtual Adapter. Only duplicate static addresses are not permitted.
|
|
•
|
Allow Connections to - Client network traffic matching destination networks of each gateway is sent through the VPN tunnel of that specific gateway.
|
|
•
|
This Gateway Only - Allows a single connection to be enabled at a time. Traffic that matches the destination networks as specified in the policy of the gateway is sent through the VPN tunnel. If this option is selected along with Set Default Route as this Gateway, then the Internet traffic is also sent through the VPN tunnel. If this option is selected without selecting Set Default Route as this Gateway, then the Internet traffic is blocked.
|
|
•
|
All Secured Gateways - Allows one or more connections to be enabled at the same time. Traffic matching the destination networks of each gateway is sent through the VPN tunnel of that specific gateway. If this option is selected along with Set Default Route as this Gateway, then Internet traffic is also sent through the VPN tunnel. If this option is selected without Set Default Route as this Gateway, then the Internet traffic is blocked. Only one of the multiple gateways can have Set Default Route as this Gateway enabled.
|
|
•
|
Split Tunnels - Allows the VPN user to have both local Internet connectivity and VPN connectivity.
|
|
•
|
Set Default Route as this Gateway - Enable this check box if all remote VPN connections access the Internet through this VPN tunnel. You can only configure one VPN policy to use this setting.
|
|
•
|
Use Default Key for Simple Client Provisioning - uses Aggressive mode for the initial exchange with the gateway and VPN clients uses a default Preshared Key for authentication.
|
|
10
|
Click OK.
|