PANEL_editInterface
This section is divided into:
• Configuring the Static Interfaces
• Configuring Interfaces in Transparent Mode
• Configuring Wireless Interfaces
• Configuring the WLAN Interface (SonicWALL TZ series wireless appliances)
• Configuring the NSA Expansion Pack Module Interface (NSA 2400MX and 250M only)
• Configuring Link Aggregation (SonicOS 5.9 or higher)
• Port Redundancy (SonicOS 5.9 or higher)
• Configuring the U0/U1/M0 External 3G/4G/Modem Interface
• Configuring SonicWALL PortShield Interfaces (TZ series, NSA 240, and NSA 2400MX)
• Configuring VLAN Subinterfaces (SonicWALL NSA series appliances)
• Configuring Layer 2 Bridge Mode
• Configuring IPS Sniffer Mode (SonicWALL NSA series appliances)
Configuring the Static Interfaces
For general information on interfaces, see Network > Interfaces.
Static means that you assign a fixed IP address to the interface. To configure a Static interface, perform the following:
1. Click on the Configure icon ![]() in the Configure column for the Interface you want to configure. The Edit Interface window is displayed.
in the Configure column for the Interface you want to configure. The Edit Interface window is displayed.
• You can configure X0 through X8, depending on the number of interfaces on your appliance.
• If you want to create a new zone, select Create new zone. The Add Zone window is displayed. See Adding and Configuring Zone for instructions on adding a zone.
2. Select a zone to assign to the interface. You can select LAN, WAN, DMZ, WLAN, or a custom zone.
3. Select Static IP Mode from the Mode / IP Assignment menu.
4. Enter the IP address and subnet mask of the zone in the IP Address and Subnet Mask fields.
Note You cannot enter an IP address that is in the same subnet as another zone.
5. Enter any optional comment text in the Comment field. This text is displayed in the Comment column of the Interface table.
6. If you want to enable remote management of the SonicWALL security appliance from this interface, select the supported management protocol(s): HTTP, HTTPS, SSH, Ping, SNMP, and/or SSH.
To allow access to the WAN interface for management from another zone on the same appliance, access rules must be created. See Allowing WAN Primary IP Access from the LAN Zone for more information.
7. If you want to allow selected users with limited management rights to log in to the security appliance, select HTTP and/or HTTPS in User Login.
8. Click OK.
Note The administrator password is required to regenerate encryption keys after changing the SonicWALL security appliance’s address.
Configuring Advanced Settings for the Interface
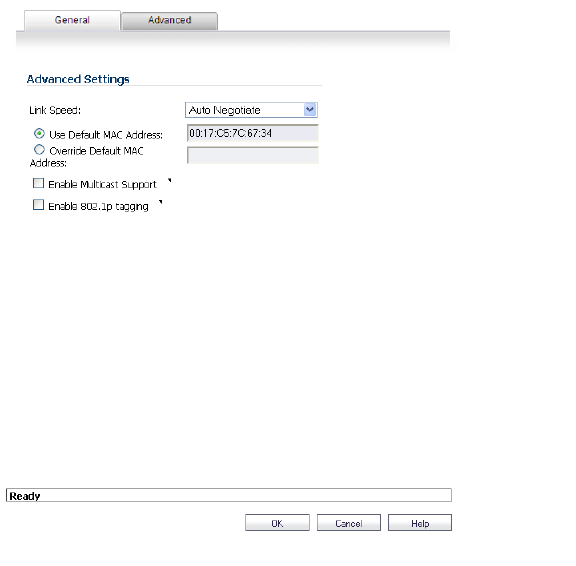
If you need to force an Ethernet speed, duplex and/or MAC address, click the Advanced tab.
Advanced Settings
The Advanced Settings section allows you to manage the Ethernet settings of links connected to the SonicWALL.
• Auto Negotiate—is selected by default as the Link Speed because the Ethernet links automatically negotiate the speed and duplex mode of the Ethernet connection. If you want to specify the forced Ethernet speed and duplex, select one of the following options from the Link Speed menu:
– 1 Gbps - Full Duplex
– 100 Mbps - Full Duplex
– 100 Mbps - Half Duplex
– 10 Mbps - Full Duplex
– 10 Mbps - Half Duplex
CAUTION If you select a specific Ethernet speed and duplex, you must force the connection speed and duplex from the Ethernet card to the SonicWALL security appliance as well.
• Use Default MAC Address—select this checkbox to use the default MAC address.
• Override Default MAC Address—overrides the default MAC address for the Interface, enter the desired MAC address in the field.
• Enable flow reporting—enables flow reporting for flows created on this interface.
• Enable Multicast Support—allows multicast reception on this interface.
• Enable 802.1p tagging (SonicWALL NSA series appliances)—select this checkbox to tag information passing through this interface with 802.1p priority information for Quality of Service (QoS) management. Packets sent through this interface are tagged with VLAN id=0 and carry 802.1p priority information. In order to make use of this priority information, devices connected to this interface should support priority frames. QoS management is controlled by access rules on the Firewall > Access Rules page. For information on QoS and bandwidth management, see Firewall Settings > QoS Mapping.
• Management Traffic Only—
Expert Mode Settings
Enter description here
• Use Routed Mode - Add NAT Policy to prevent outbound/inbound translation—
• Set NAT Police’s outbound/inbound interface to:—
Bandwidth Management
Enter description here
• Enable Interface Egress Bandwidth Limitation—
– Maximum Interface Egress Bandwidth (kbps):—
• Enable Interface Ingress Bandwidth Limitation—
– Maximum Interface Ingress Bandwidth (kbps):—
Note Change the bandwidth management setting to Advanced, refer to the Firewall Settings > BWM page.
Configuring Interfaces in Transparent Mode
Transparent Mode enables the SonicWALL security appliance to bridge the WAN subnet onto an internal interface. To configure an interface for transparent mode, complete the following steps:
1. Click on the Configure icon in the Configure column for Unassigned Interface you want to configure. The Edit Interface window is displayed.
2. Select an interface.
• If you select a configurable interface, select LAN or DMZ for Zone.
• If you want to create a new zone for the configurable interface, select Create a new zone. The Add Zone window is displayed. See Network > Zones, for instructions on adding a zone.
3. Select Transparent IP Mode from the Mode / IP Assignment menu.
From the Transparent Range menu, select an address object that contains the range of IP addresses you want to have access through this interface. The address range must be within the WAN zone and must not include the WAN interface IP address. If you do not have an address object configured that meets your needs, perform the following:
1. In the Transparent Range menu, select Create New Address Object.
2. In the Add Address Object window, enter a name for the address range.
3. For Zone Assignment, select WAN.
4. For Type, select:
– Select Host if you want only one network device to connect to this interface.
– Select Range to specify a range of IP addresses by entering beginning and ending value of the range.
– Select Network to specify a subnet by entering the beginning value and the subnet mask. The subnet must be within the WAN address range and cannot include the WAN interface IP address.
5. Enter the IP address of the host, the beginning and ending address of the range, or the IP address and subnet mask of the network.
6. Click OK to create the address object and return to the Edit Interface window.
See Network > Address Objects for more information.
7. Enter any optional comment text in the Comment field. This text is displayed in the Comment column of the Interface table.
8. If you want to enable remote management of the SonicWALL security appliance from this interface, select the supported management protocol(s): HTTP, HTTPS, SSH, Ping, SNMP, and/or SSH.
To allow access to the WAN interface for management from another zone on the same appliance, access rules must be created. See Allowing WAN Primary IP Access from the LAN Zone for more information.
9. If you want to allow selected users with limited management rights to log directly into the security appliance through this interface, select HTTP and/or HTTPS in User Login.
10. Click OK.
Note The administrator password is required to regenerate encryption keys after changing the SonicWALL security appliance’s address.
Configuring Advanced Settings for the Interface
If you need to force an Ethernet speed, duplex and/or MAC address, click the Advanced tab.
Advanced Settings
The Advanced Settings section allows you to manage the Ethernet settings of links connected to the SonicWALL.
• Auto Negotiate—is selected by default as the Link Speed because the Ethernet links automatically negotiate the speed and duplex mode of the Ethernet connection. If you want to specify the forced Ethernet speed and duplex, select one of the following options from the Link Speed menu:
– 1 Gbps - Full Duplex
– 100 Mbps - Full Duplex
– 100 Mbps - Half Duplex
– 10 Mbps - Full Duplex
– 10 Mbps - Half Duplex
CAUTION If you select a specific Ethernet speed and duplex, you must force the connection speed and duplex from the Ethernet card to the SonicWALL security appliance as well.
• Use Default MAC Address—select this checkbox to use the default MAC address.
• Override Default MAC Address—overrides the default MAC address for the Interface, enter the desired MAC address in the field.
• Enable flow reporting—enables flow reporting for flows created on this interface.
• Enable Multicast Support—allows multicast reception on this interface.
• Enable 802.1p tagging (SonicWALL NSA series appliances)—select this checkbox to tag information passing through this interface with 802.1p priority information for Quality of Service (QoS) management. Packets sent through this interface are tagged with VLAN id=0 and carry 802.1p priority information. In order to make use of this priority information, devices connected to this interface should support priority frames. QoS management is controlled by access rules on the Firewall > Access Rules page. For information on QoS and bandwidth management, see Firewall Settings > QoS Mapping.
• Management Traffic Only—
• Enable Gratuitous ARP Forwarding Towards WAN—gratuitous ARP packets received on this interface will be forwarded towards the WAN with the source MAC address as the hardware MAC address of the WAN interface.
• Enable Automatic Gratuitous ARP Generation Towards WAN—Whenever a new entry is added into the ARP table for a new machine on this interface, a gratuitous ARP packet will be generated towards the WAN interface with the source MAC address as the hardware MAC address of the WAN interface.
Bandwidth Management
Enter description here
• Enable Interface Egress Bandwidth Limitation—
– Maximum Interface Egress Bandwidth (kbps):—
• Enable Interface Ingress Bandwidth Limitation—
– Maximum Interface Ingress Bandwidth (kbps):—
Note Change the bandwidth management setting to Advanced, refer to the Firewall Settings > BWM page.
Configuring Wireless Interfaces
A Wireless interface is an interface that has been assigned to a Wireless zone and is used to support SonicWALL SonicPoint secure access points.
1. Click on the Configure icon ![]() in the Configure column for the Interface you want to configure. The Edit Interface window is displayed.
in the Configure column for the Interface you want to configure. The Edit Interface window is displayed.
2. In the Zone list, select WLAN or a custom Wireless zone.
3. Enter the IP address and subnet mask of the zone in the Mode / IP Address and Subnet Mask fields.
Note The upper limit of the subnet mask is determined by the number of SonicPoints you select in the SonicPoint Limit field. If you are configuring several interfaces or subinterfaces as Wireless interfaces, you may want to use a smaller subnet (higher) to limit the number of potential DHCP leases available on the interface. Otherwise, if you use a class C subnet (subnet mask of 255.255.255.0) for each Wireless interface you may exceed the limit of DHCP leases available on the security appliance.
4. In the SonicPoint Limit field, select the maximum number of SonicPoints allowed on this interface.
• This value determines the highest subnet mask you can enter in the Subnet Mask field. The following table shows the subnet mask limit for each SonicPoint Limit selection and the number of DHCP leases available on the interface if you enter the maximum allowed subnet mask.
• Available Client IPs assumes 1 IP for the SonicWALL gateway interface, in addition to the presence of the maximum number of SonicPoints allowed on this interface, each consuming an IP address.
|
Note The above table depicts the maximum subnet mask sizes allowed. You can still use class-full subnetting (class A, class B, or class C) or any variable length subnet mask that you wish on WLAN interfaces. You are encouraged to use a smaller subnet mask (e.g. 24-bit class C - 255.255.255.0 - 254 total usable IPs), thus allocating more IP addressing space to clients if you have the need to support larger numbers of wireless clients.
5. Enter any optional comment text in the Comment field. This text is displayed in the Comment column of the Interface table.
6. If you want to enable remote management of the SonicWALL security appliance from this interface, select the supported management protocol(s): HTTP, HTTPS, SSH, Ping, SNMP, and/or SSH.
To allow access to the WAN interface for management from another zone on the same appliance, access rules must be created. See Allowing WAN Primary IP Access from the LAN Zone for more information.
7. If you want to allow selected users with limited management rights to log in to the security appliance, select HTTP and/or HTTPS in User Login.
8. Click OK.
Configuring Advanced Settings for the Interface
If you need to force an Ethernet speed, duplex and/or MAC address, click the Advanced tab.
Advanced Settings
The Advanced Settings section allows you to manage the Ethernet settings of links connected to the SonicWALL.
• Auto Negotiate—is selected by default as the Link Speed because the Ethernet links automatically negotiate the speed and duplex mode of the Ethernet connection. If you want to specify the forced Ethernet speed and duplex, select one of the following options from the Link Speed menu:
– 1 Gbps - Full Duplex
– 100 Mbps - Full Duplex
– 100 Mbps - Half Duplex
– 10 Mbps - Full Duplex
– 10 Mbps - Half Duplex
CAUTION If you select a specific Ethernet speed and duplex, you must force the connection speed and duplex from the Ethernet card to the SonicWALL security appliance as well.
• Use Default MAC Address—select this checkbox to use the default MAC address.
• Override Default MAC Address—overrides the default MAC address for the Interface, enter the desired MAC address in the field.
• Enable flow reporting—enables flow reporting for flows created on this interface.
• Enable Multicast Support—allows multicast reception on this interface.
• Enable 802.1p tagging (SonicWALL NSA series appliances)—select this checkbox to tag information passing through this interface with 802.1p priority information for Quality of Service (QoS) management. Packets sent through this interface are tagged with VLAN id=0 and carry 802.1p priority information. In order to make use of this priority information, devices connected to this interface should support priority frames. QoS management is controlled by access rules on the Firewall > Access Rules page. For information on QoS and bandwidth management, see Firewall Settings > QoS Mapping.
• Management Traffic Only—
Expert Mode Settings
Enter description here
• Use Routed Mode - Add NAT Policy to prevent outbound/inbound translation—
• Set NAT Police’s outbound/inbound interface to:—
Bandwidth Management
Enter description here
• Enable Interface Egress Bandwidth Limitation—
– Maximum Interface Egress Bandwidth (kbps):—
• Enable Interface Ingress Bandwidth Limitation—
– Maximum Interface Ingress Bandwidth (kbps):—
Note Change the bandwidth management setting to Advanced, refer to the Firewall Settings > BWM page.
Configuring the WLAN Interface (SonicWALL TZ series wireless appliances)
The WLAN interface is only available on the SonicWALL TZ series wireless. You can only configure the WLAN interface with a static IP address.
1. Click on the Edit ![]() icon in the Configure column for Unassigned Interface you want to configure. The Edit Interface window is displayed.
icon in the Configure column for Unassigned Interface you want to configure. The Edit Interface window is displayed.
2. Select the WLAN interface. If you want to create a new zone for the interface, select Create a new zone. The Add Zone window is displayed. See Chapter 11 for instructions on adding a zone.
3. Select one of the following WLAN Network Addressing Mode from the Mode / IP Assignment menu. Depending on the option you choose from the IP Assignment menu, complete the corresponding fields that are displayed after selecting the option.
• Static IP Mode—the IP address for the interface is manually entered
• Layer 2 Bridge Mode—an interface placed in this mode becomes the Secondary Bridge Interface to the Primary Bridge Interface to which it is paired. The resulting Bridge-Pair will then behave like a two-port learning bridge with full L2 transparency, and all IP traffic that passes through will be subjected to full stateful failover and deep packet inspection
• PortShield Switch Mode—this architecture enables you to configure some or all of the LAN ports into separate security contexts, providing protection not only from the WAN and DMZ, but between devices inside your network as well. In effect, each context has its own wire-speed PortShield that enjoys the protection of a dedicated, deep packet inspection firewall.
4. Enter the IP address and subnet mask of the Zone in the IP Address and Subnet Mask fields.
5. Enter any optional comment text in the Comment field. This text is displayed in the Comment column of the Interface table.
6. If you want to enable remote management of the SonicWALL security appliance from this interface, select the supported management protocol(s): HTTP, HTTPS, Ping, and/or SNMP.
7. If you want to allow selected users with limited management rights, select HTTP and/or HTTPS in User Login.
8. Click OK.
Note The administrator password is required to regenerate encryption keys after changing the SonicWALL security appliance’s address.
Configuring Advanced Settings for the Interface
Check the Enable Multicast Support checkbox to allow multicast reception on this interface.
Configuring the WAN interface enables Internet connect connectivity. You can configure up to two WAN interfaces on the SonicWALL security appliance.
1. Click on the Edit ![]() icon in the Configure column for the Interface you want to configure. The Edit Interface window is displayed.
icon in the Configure column for the Interface you want to configure. The Edit Interface window is displayed.
2. If you’re configuring an Unassigned Interface, select WAN from the Zone menu. If you selected the Default WAN Interface, WAN is already selected in the Zone menu.
Select one of the following WAN Network Addressing Mode from the Mode / IP Assignment menu. Depending on the option you choose from the IP Assignment menu, complete the corresponding fields that are displayed after selecting the option.
• Static - configures the SonicWALL for a network that uses static IP addresses.
• DHCP - configures the SonicWALL to request IP settings from a DHCP server on the Internet. NAT with DHCP Client is a typical network addressing mode for cable and DSL customers.
• PPPoE - uses Point to Point Protocol over Ethernet (PPPoE) to connect to the Internet. If desktop software and a username and password is required by your ISP, select NAT with PPPoE. This protocol is typically found when using a DSL modem.
• PPTP - uses PPTP (Point to Point Tunneling Protocol) to connect to a remote server. It supports older Microsoft Windows implementations requiring tunneling connectivity.
• L2TP - uses IPsec to connect a L2TP (Layer 2 Tunneling Protocol) server and encrypts all data transmitted from the client to the server. However, it does not encrypt network traffic to other destinations.
• Wire Mode (2-Port Wire) - is a deployment option where the SonicWALL appliance can be deployed as a “Bump in the Wire”. It provides a least-intrusive way to deploy the appliance in a network. Wire Mode is very well suited for deploying behind a pre-existing Stateful Packet Inspection (SPI) Firewall.Wire Mode is a simplified form of Layer 2 Bridge Mode. A Wire Mode interface does not take any IP address and it is typically configured as a bridge between a pair of interfaces. None of the packets received on a Wire Mode interface are destined to the firewall, but are only bridged to the other interface
• Tap Mode (1-Port Tap) - can be configured between a pair of interfaces. All traffic received is bridged to the paired interface; in addition, the firewall does SPI and DPI processing of traffic. There is full Application Visibility, but no Application Control in Tap Mode
Note For Windows clients, L2TP is supported by Windows 2000 and Windows XP. If you are running other versions of Windows, you must use PPTP as your tunneling protocol.
4. If you want to enable remote management of the SonicWALL security appliance from this interface, select the supported management protocol(s): HTTP, HTTPS, SSH, Ping, SNMP, and/or SSH. You can also select HTTP for management traffic. However, bear in mind that HTTP traffic is less secure than HTTPS.
To allow access to the WAN interface for management from another zone on the same appliance, access rules must be created. See Allowing WAN Primary IP Access from the LAN Zone for more information.
5. If you want to allow selected users with limited management rights to log directly into the security appliance from this interface, select HTTP and/or HTTPS in User Login.
6. Check Add rule to enable redirect from HTTP to HTTPS, if you want an HTTP connection automatically redirected to a secure HTTPS connection to the SonicWALL security appliance management interface.
7. After completing the WAN configuration for your Network Addressing Mode, click OK.
Configuring the Advanced Settings for the WAN Interface
If you need to force an Ethernet speed, duplex and/or MAC address, click the Advanced tab.
Advanced Settings
The Advanced Settings section allows you to manage the Ethernet settings of links connected to the SonicWALL.
• Auto Negotiate—is selected by default as the Link Speed because the Ethernet links automatically negotiate the speed and duplex mode of the Ethernet connection. If you want to specify the forced Ethernet speed and duplex, select one of the following options from the Link Speed menu:
– 1 Gbps - Full Duplex
– 100 Mbps - Full Duplex
– 100 Mbps - Half Duplex
– 10 Mbps - Full Duplex
– 10 Mbps - Half Duplex
CAUTION If you select a specific Ethernet speed and duplex, you must force the connection speed and duplex from the Ethernet card to the SonicWALL security appliance as well.
• Use Default MAC Address—select this checkbox to use the default MAC address.
• Override Default MAC Address—overrides the default MAC address for the Interface, enter the desired MAC address in the field.
• Enable flow reporting—enables flow reporting for flows created on this interface.
• Enable Multicast Support—allows multicast reception on this interface.
• Enable 802.1p tagging (SonicWALL NSA series appliances)—select this checkbox to tag information passing through this interface with 802.1p priority information for Quality of Service (QoS) management. Packets sent through this interface are tagged with VLAN id=0 and carry 802.1p priority information. In order to make use of this priority information, devices connected to this interface should support priority frames. QoS management is controlled by access rules on the Firewall > Access Rules page. For information on QoS and bandwidth management, see Firewall Settings > QoS Mapping.
• Management Traffic Only—
• Interface MTU—Specifies the largest packet size that the interface can forward without fragmenting the packet.
• Fragment non-VPN outbound packets larger than this Interface’s MTU—Specifies all non-VPN outbound packets larger than this Interface’s MTU be fragmented. Specifying the fragmenting of VPN outbound packets is set in the VPN > Advanced page.
– Ignore Don’t Fragment (DF) Bit—Overrides DF bits in packets.
• Suppress ICMP Fragmentation Needed message generation—blocks notification that this interface can receive fragmented packets.
Bandwidth Management
Bandwidth Management
Enter description here
• Enable Interface Egress Bandwidth Limitation—
– Maximum Interface Egress Bandwidth (kbps):—
• Enable Interface Ingress Bandwidth Limitation—
– Maximum Interface Ingress Bandwidth (kbps):—
For information on Bandwidth Management (BWM), see .
Configuring the NSA Expansion Pack Module Interface (NSA 2400MX and 250M only)
The SonicWALL NSA 2400MX and NSA 250M security appliances support the following optional NSA Expansion Pack modules:
• 1-Port ADSL (RJ-11) Annex A module
• 1-Port ADSL (RJ-45) Annex B module
• 1-Port T1/E1 module
• 2-Port LAN Bypass module
• 2-Port SFP module
• 4-Port Gigabit Ethernet module (SonicWALL NSA 2400MX only)
These interfaces are listed in the Interface Settings table as the Mx interfaces.
CAUTION Before attempting to insert and configure the module, you must power off the appliance. Once the appliance has been powered down, remove the rear module plate cover and insert the expansion module.Tighten the screws to secure the module, then power on the appliance.
Log into the SonicWALL management interface. You can now begin configuring the desired expansion module. The following sections describe how to configure the
• Configuring the ADSL Expansion Module
• Configuring the T1/E1 Module
• Configuring the LAN Bypass Module
• Configuring the 2 Port SFP or 4 Port Gigabit Ethernet Modules
Configuring the ADSL Expansion Module
ADSL is an acronym for Asymmetric Digital Subscriber Line (or Loop). The line is asymmetric because, when connected to the ISP, the upstream and downstream speeds of transmission are different. The DSL technology allows non-voice services (data) to be provided on regular single copper wire-pair POTS connections (such as your home phone line). It allows voice calls and data to pass through simultaneously by using higher band frequencies for data transmission.
The SonicWALL ADSL module cards support only one subscriber ADSL line (one port). Two types of ADSL module cards are supported:
• 1 Port ADSL (RJ-11) Annex A – ADSL over plain old telephone service (POTS) with a downstream rate of 12.0 Mbit/s and an upstream rate of 1.3 Mbit/s.
• 1 Port ADSL (RJ-45) Annex B – ADSL over an Integrated Services Digital Network (ISDN) with a downstream rate of 12.0 Mbit/s and an ups.tream rate of 1.8 Mbit/s.
The following ADSL standards are supported
|
The ADSL module card uses 2 LEDs to indicate connectivity status. The upper green LED is the ADSL link. Its status is as follows:
• OFf - No link
• ON - ADSL link is active
The lower green LED shows the system and ADSL module activity.
• If it is OFF, there is no activity.
• If it displays a slow blink rate, it signifies activity on system management interface.
• If it displays a fast blink rate, there is data activity on ADSL line.
The ADSL module card is detected on boot, and assigned an interface name of M0 or M1. The interface name is based to it based on the expansion slot hosting the module card. You will see the assigned entry when you log into the Network Interfaces page.
The ADSL interface never unassigned. When plugged in, it is always present in the WAN zone and zone assignment cannot be modified by the administrator
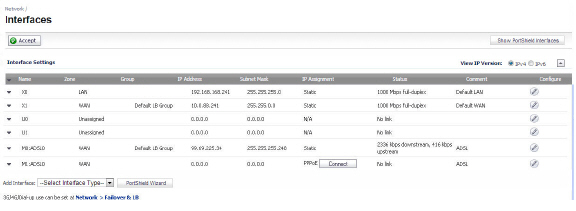
Click on the Configure ![]() icon to the right of the interface entry. You will see a menu with three tabs: General, Advanced, and DSL Settings. The DSL Settings tab allows you to configure ISP-specific settings for the ADSL connection.
icon to the right of the interface entry. You will see a menu with three tabs: General, Advanced, and DSL Settings. The DSL Settings tab allows you to configure ISP-specific settings for the ADSL connection.
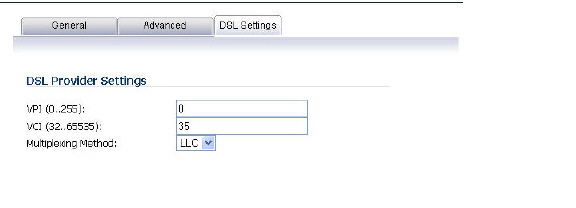
It displays the configurable DSL fields:
• Virtual Path Identifier (VPI)
• Virtual Channel Identifier (VCI)
• Multiplexing Method (LLC or VC)
The values for these parameters should match the settings on the ISP DSLAM, and are provided by the ISP. These values vary from one ISP to another, and from country to country.
The SNWL default uses the most common values in the USA. The VPI and VCI settings are used to create the Permanent Virtual Circuit (PVC) from the NSA2400MX to the ISP DSLAM.
When finished configuring these ISP settings, click OK.
The Ethernet-specific settings on the Advanced tab, even if set, do not apply to the ADSL module. The Link Speed field in the Advanced tab has a fixed "N/A" selection, since it does not apply to ADSL. The ADSL link speed can't be customized but is predetermined by the DSL Provider.
The standard WAN ethernet settings are not affected by the presence of the ADSL module.
When the ADSL module is first plugged in, it should be added to the WAN Load Balancing default group so that the ADSL module can be used to handle default route traffic. Go to the Failover and LB screen and click the Configure ![]() icon to edit the settings.
icon to edit the settings.
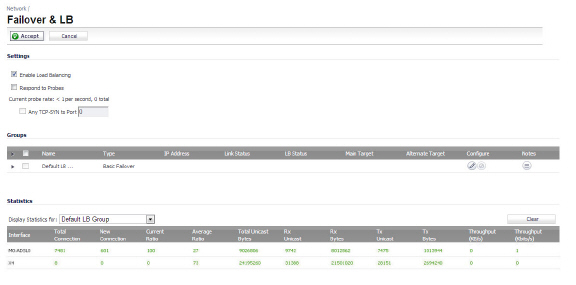
On the General menu, add the ADSL interface to the Load Balancing group. If the default primary WAN, X1, is unused or unconfigured, it can be removed for a cleaner interface configuration.
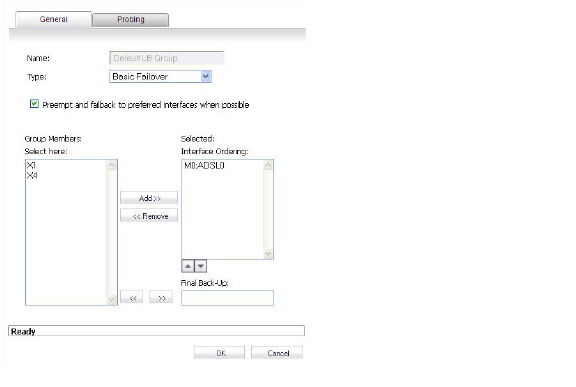
When done, click OK, and the ADSL module will be added to the group.
The 1-port T1/E1 Module provides the connection of a T1 or E1 (digitally multiplexed telecommunications carrier system) circuit to a SonicWALL appliance using an RJ-45 jack.
The SonicWALL T1/E1 module fully supports Point-to-Point Protocol (PPP) and Cisco HDLC encapsulation, and can connect to Cisco routers and HP ProCurve devices.
Note Only one T1/E1 module can be configured on each appliance.
To configure the T1/E1 Module, perform the following tasks:
1. Click on the Edit ![]() icon in the Configure column for the Interface of the expansion module you want to configure. The Edit Interface window is displayed.
icon in the Configure column for the Interface of the expansion module you want to configure. The Edit Interface window is displayed.
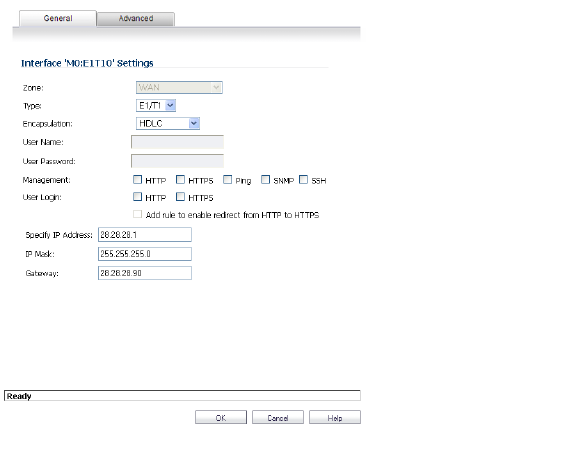
The General tab allows you to set up the type of encapsulation: PPP or HDLC, as well as the management interface type and level of user security login. The Zone setting is disabled.
2. Select the desired type of encapsulation: PPP, HDLC, or Cisco HDLC. If you select a type of encapsulation other than PPP, you will need to assign the IP address and netmask.
3. If HDLC or Cisco HDLC is selected, assign the IP address and subnet mask for the network mask assigned to the subnet.These are auto-filled for you, but you can change them if desired.
If you want to enable remote management of the SonicWALL security appliance from this interface, select the supported management protocol(s): HTTP, HTTPS, SSH, Ping, SNMP, and/or SSH. You can also select HTTP for management traffic. However, bear in mind that HTTP traffic is less secure than HTTPS. You can also set the level of security (HTTP or HTTPS) at this time.
4. Click on the Advanced Tab.
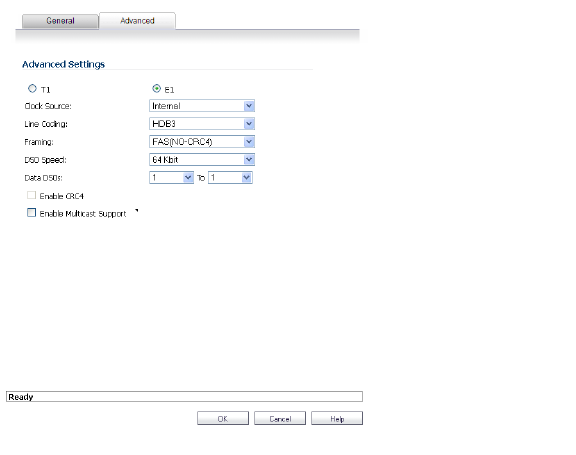
You will see two radio buttons, one for T1 and one for E1. Only one button should be selected at a time. Different Line Coding, Framing and Encapsulation configuration choices are offered, depending on the button.
5. Select the Clock Source: Internal or External. This selection is the same for both T1 and E1.
6. Select the Line Coding option:
• When T1 is selected the choices are: B8ZS, AMI
• When E1 is selected the choices are: HDB3, AMI
7. Select the Framing configuration:
• When T1 is selected the choices are: D4 (SF), ESF
• When E1 is selected the choices are: FAS, MFAS
8. Select the DSO speed: 56 KB or 64KB (default).
If desired, you can specify the Data DSO range.
• For T1, the range is 1 to 24 (default)
• For E1, the range is 1 to 31
Each number can be individually set. For example, “5 to 15”, “1 to 1”, 1 to 20” are valid settings.
9. Line Build Out is available with T1. The options are: 0.0 dB, -7.5 dB, -15 dB, -22.5 dB.
CRC is configured with an enable/disable check-box. When T1 is selected, the check-box is labeled CRC6, when E1 is selected the check-box is labeled CRC4.
You can also choose to enable multicast.
10. When finished with configuration, click OK.
The T1/E1 module interface will be added to the pool of available WAN interfaces
Configuring the LAN Bypass Module
This module allows you to perform a physical bypass of the firewall when the interface is bridged to another interface with LAN bypass capability. This allows network traffic to continue flowing if an unrecoverable firewall error occurs.
1. Click on the Edit ![]() icon in the Configure column for the Interface of the expansion module you want to configure. The Edit Interface window is displayed. The Bypass option is only displayed if an interface capable of performing the bridge is present.
icon in the Configure column for the Interface of the expansion module you want to configure. The Edit Interface window is displayed. The Bypass option is only displayed if an interface capable of performing the bridge is present.
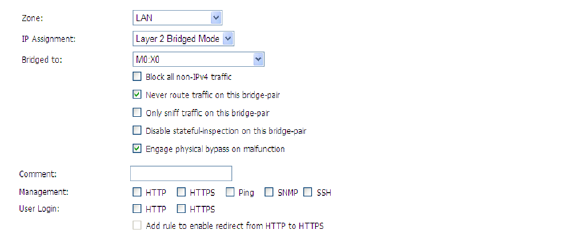
2. The window shows the LAN interface, and has a checkbox “Engage Physical ByPass on Malfunction” to enable the physical bypass feature. This is only displayed when the interface is bridged to another interface capable of performing the LAN bypass. Enabling this checkbox means that the packets between the bridged pairs will not fail, even if the firmware or NSA appliance fails.
If the checkbox is not enabled, the ports will behave like normal Ethernet ports.
3. Click OK to configure the interface.
Configuring the 2 Port SFP or 4 Port Gigabit Ethernet Modules
1. Click on the Edit ![]() icon in the Configure column for the Interface of the expansion module you want to configure. The Edit Interface window is displayed.
icon in the Configure column for the Interface of the expansion module you want to configure. The Edit Interface window is displayed.
2. If you’re configuring an Unassigned Interface, you can select any zone from the Zone menu. LAN is already selected in the Zone menu.
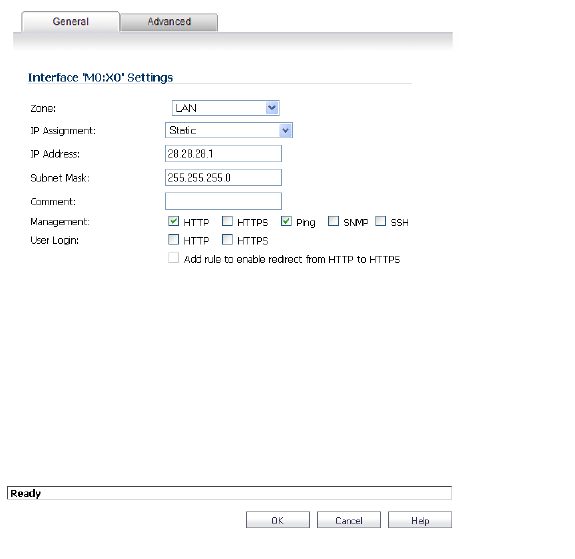
Select one of the following LAN Network Addressing Modes from the IP Assignment menu.
• Static - configures the interface for a network that uses static IP addresses.
• Transparent - configures the interface to use interfaces as the top level of the management hierarchy and span multiple interfaces.
Depending on the option you choose from the IP Assignment menu, complete the corresponding fields that are displayed after selecting the option.
3. Assign the IP address and subnet mask for the network mask assigned to the subnet.These are auto-filled for you, but you can change them if desired.
4. If you want to enable remote management of the SonicWALL security appliance from this interface, select the supported management protocol(s): HTTP, HTTPS, SSH, Ping, SNMP, and/or SSH. You can also select HTTP for management traffic. However, bear in mind that HTTP traffic is less secure than HTTPS. You can also use a checkbox to add a rule to redirect from HTTP to HTTPS to enforce security on the interface.
5. Click OK to configure the interface.
Configuring the Advanced Settings for the Module Interface
The Advanced tab includes settings for forcing an Ethernet speed and duplex, overriding the Default MAC address, enabling multicast support on the interface, and enabling 802.1p tagging. Packets sent out with 802.1p tagging are tagged VLAN id=0 and carry 802,1p priority information. Devices connected to this interface need to support priority frames.
Configuring Additional Interfaces
6. Each expansion module interface must be individually configured. These initially appear as unassigned interfaces.
7. Click on the Edit ![]() icon in the Configure column for the Interface you want to configure.
icon in the Configure column for the Interface you want to configure.
For each interface, on the General tab of the Edit Interface window, select LAN from the Zone menu. Fill in the desired IP assignment. The subnet will be assigned for you. Add the desired management options and click Okay. Then configure the Advanced settings.
Configuring Link Aggregation (SonicOS 5.9 or higher)
Link Aggregation groups up to four Ethernet interfaces together forming a single logical link to support greater throughput than a single physical interface could support, this is referred to as a Link Aggregation Group (LAG). This provides the ability to send multi-gigabit traffic between two Ethernet domains. All ports in an aggregate link must be connected to the same switch. The firewall uses a round-robin algorithm for load balancing traffic across the interfaces in a Link Aggregation Group. Link Aggregation also provides a measure of redundancy, in that if one interface in the LAG goes down, the other interfaces remain connected.
Link Aggregation is referred to using different terminology by different vendors, including Port Channel, Ether Channel, Trunk, and Port Grouping.
Link Aggregation failover
SonicWALL provides multiple methods for protecting against loss of connectivity in the case of a link failure, including High Availability (HA), Load Balancing Groups (LB Groups), and now Link Aggregation. If all three of these features are configured on a firewall, the following order of precedence is followed in the case of a link failure:
• High Availability
• Link Aggregation
• Load Balancing Groups
HA takes precedence over Link Aggregation. Because each link in the LAG carries an equal share of the load, the loss of a link on the Active firewall will force a failover to the Idle firewall (if all of its links remain connected). Physical monitoring needs to be configured only on the primary aggregate port.
When Link Aggregation is used with a LB Group, Link Aggregation takes precedence. LB will take over only if all the ports in the aggregate link are down.
Link Aggregation Limitations
• Currently only static addressing is supported for Link Aggregation
• Link Aggregation is supported on Dell SonicWALL E-Class appliances only.
• The Link Aggregation Control Protocol (LACP) is currently not supported
Link Aggregation Configuration
To configure Link Aggregation, perform the following tasks:
1. On the Network > Interfaces page, click the configure icon for the interface that is to be designated the master of the Link Aggregation Group. The Edit Interface window displays.
2. Click on the Advanced tab.
3. In the Redundant/Aggregate Ports pull-down menu, select Link Aggregation.
4. The Aggregate Port option is displayed with a checkbox for each of the currently unassigned interfaces on the firewall. Select up to three other interfaces to assign to the LAG.
Note After an interface is assigned to a Link Aggregation Group, its configuration is governed by the Link Aggregation master interface and it cannot be configured independently. In the Interface Settings table, the interface's zone is displayed as "Aggregate Port" and the configuration icon is removed.
5. Set the Link Speed for the interface to Auto-Negotiate.
6. Click OK.
Note Link Aggregation requires a matching configuration on the Switch. The switch's method of load balancing will very depending on the vendor. Consult the documentation for the switch for information on configuring Link Aggregation. Remember that it may be referred to as Port Channel, Ether Channel, Trunk, or Port Grouping.
Port Redundancy (SonicOS 5.9 or higher)
Port Redundancy provides a simple method for configuring a redundant port for a physical Ethernet port. This is a valuable feature, particularly in high-end deployments, to protect against switch failures being a single point of failure.
When the primary interface is active, it processes all traffic to and from the interface. If the primary interface goes down, the secondary interface takes over all outgoing and incoming traffic. The secondary interface assumes the MAC address of the primary interface and sends the appropriate gratuitous ARP on a failover event. When the primary interface comes up again, it resumes responsibility for all traffic handling duties from the secondary interface.
In a typical Port Redundancy configuration, the primary and secondary interfaces are connected to different switches. This provides for a failover path in case the primary switch goes down. Both switches must be on the same Ethernet domain. Port Redundancy can also be configured with both interfaces connected to the same switch.
Note Port Redundancy is supported on Dell SonicWALL E-Class appliances only.
Port Redundancy Failover
SonicWALL provides multiple methods for protecting against loss of connectivity in the case of a link failure, including High Availability (HA), Load Balancing Groups (LB Groups), and now Port Redundancy. If all three of these features are configured on a firewall, the following order of precedence is followed in the case of a link failure:
• Port Redundancy
• HA
• LB Group
When Port Redundancy is used with HA, Port Redundancy takes precedence. Typically an interface failover will cause an HA failover to occur, but if a redundant port is available for that interface, then an interface failover will occur but not an HA failover. If both the primary and secondary redundant ports go down, then an HA failover will occur (assuming the secondary firewall has the corresponding port active).
When Port Redundancy is used with a LB Group, Port Redundancy again takes precedence. Any single port (primary or secondary) failures are handled by Port Redundancy just like with HA. When both the ports are down then LB kicks in and tries to find an alternate interface.
Port Redundancy Configuration
To configure Port Redundancy, perform the following tasks:
1. On the Network > Interfaces page, click the configure icon for the interface that is to be designated the master of the Link Aggregation Group. The Edit Interface window displays.
2. Click on the Advanced tab.
3. In the Redundant/Aggregate Ports pull-down menu, select Port Redundancy.
4. The Redundant Port pull-down menu is displayed, with all of the currently unassigned interfaces available. Select one of the interfaces.
Note After an interface is selected as a Redundant Port, its configuration is governed by the primary interface and it can not be configured independently. In the Interface Settings table, the interface's zone is displayed as "Redundant Port" and the configuration icon is removed.
5. Set the Link Speed for the interface to Auto-Negotiate.
6. Click OK.
Routed Mode provides an alternative for NAT for routing traffic between separate public IP address ranges. Consider the following topology where the firewall is routing traffic across two public IP address ranges:
• 10.50.26.0/24
• 172.16.6.0/24
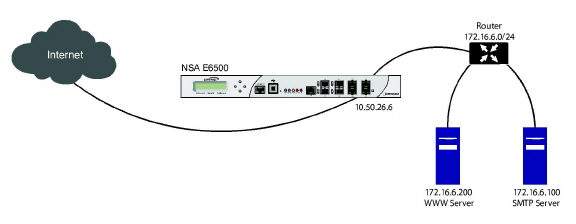
By enabling Routed Mode on the interface for the 172.16.6.0 network, NAT translations will be automatically disabled for the interface, and all inbound and outbound traffic will be routed to the WAN interface configured for the 10.50.26.0 network.
To configure Routed Mode, perform the following steps:
1. Navigate to the Network > Interfaces page.
2. Click on the configure icon for the appropriate interface. The Edit Interface window displays.
3. Click on the Advanced tab.
Under the Expert Mode Settings heading, select the Use Routed Mode - Add NAT Policy to prevent outbound\inbound translation checkbox to enable Routed Mode for the interface.
5. In the Set NAT Policy's outbound\inbound interface to pulldown menu, select the WAN interface that is to be used to route traffic for the interface.
6. Click OK.
The firewall then creates “no-NAT” policies for both the configured interface and the selected WAN interface. These policies override any more general M21 NAT policies that may be configured for the interfaces.