 For complete information on SonicWALL’s implementation of IPv6, see the Appendix C: IPv6 Appendix
For complete information on SonicWALL’s implementation of IPv6, see the Appendix C: IPv6 Appendix For complete information on SonicWALL’s implementation of IPv6, see the Appendix C: IPv6 Appendix
For complete information on SonicWALL’s implementation of IPv6, see the Appendix C: IPv6 Appendix
The IPv6 DNS Name Lookup tool will lookup the IPv6 address for a domain name. Or, if you enter an IPv6 address, it will lookup the domain name for that address.
When performing IPv6 DNS Lookup or IPv6 Reverse Name Lookup, you must enter the DNS server address. Either an IPv6 or IPv4 address can be used.
To use the IPv6 DNS Name Lookup tool, perform the following steps:
1. Enter either an IPv4 DNS server address in the DNS Server(V4) field or an IPv6 DNS server address in the DNS Server(V6) field.
2. In the Reverse Lookup the IP Address field, enter either the domain name that you want to know the IPv6 address for or the IPv6 address that you want to know the domain name for.
3. Click Go.
The appliance will return the matching pair of IPv6 address and domain name.
Find Network Path indicates if an IP host is located on the LAN or WAN ports. This can diagnose a network configuration problem on the SonicWALL security appliance. For example, if the SonicWALL security appliance indicates that a computer on the Internet is located on the LAN, then the network or Intranet settings may be misconfigured.
Find Network Path can be used to determine if a target device is located behind a network router and the Ethernet address of the target device. It also displays the gateway the device is using and helps isolate configuration problems.
The Ping test bounces a packet off a machine on the Internet and returns it to the sender. This test shows if the SonicWALL security appliance is able to contact the remote host. If users on the LAN are having problems accessing services on the Internet, try pinging the DNS server, or another machine at the ISP location. If the test is unsuccessful, try pinging devices outside the ISP. If you can ping devices outside of the ISP, then the problem lies with the ISP connection.
1. Select Ping from the Diagnostic Tool menu.
Enter the IP address or host name of the target device and click Go.
3. In the Interface pulldown menu, select which WAN interface you want to test the ping from. Selecting ANY allows the appliance to choose among all interfaces—including those not listed in the pulldown menu.
4. If the test is successful, the SonicWALL security appliance returns a message saying the IP address is alive and the time to return in milliseconds (ms).
Ping for IPv6
For complete information on SonicWALL’s implementation of IPv6, see the Appendix C: IPv6 Appendix.
The ping tool includes a new Prefer IPv6 networking option.
When pinging a domain name, it uses the first IP address that is returned and shows the actual pinging address. If both an IPv4 and IPv6 address are returned, by default, the firewall pings the IPv4 address.
If the Prefer IPv6 networking option is enabled, the firewall will ping the IPv6 address.
The Core 0 Process Monitor shows the individual system processes on core 0, their CPU utilization, and their system time. The Core 0 process monitor is only available on the multi-core NSA E-Class appliances.
The Real-Time Black List Lookup tool allows you to test SMTP IP addresses, RBL services, or DNS servers. Enter an IP address in the IP Address field, a FQDN for the RBL in the RBL Domain field and DNS server information in the DNS Server field. Click Go.
The Reverse Name Resolution tool is similar to the DNS name lookup tool, except that it looks up a server name, given an IP address.
Enter an IP address in the Reverse Lookup the IP Address field, and it checks all DNS servers configured for your security appliance to resolve the IP address into a server name.
For complete information on SonicWALL’s implementation of IPv6, see the Appendix C: IPv6 Appendix.
The IPv6 Reverse Name Resolution tool will lookup the server name for a given IPv6 address. To use the tool, perform the following steps:
1. Enter either an IPv4 DNS server address in the DNS Server(V4) field or an IPv6 DNS server address in the DNS Server(V6) field.
2. Enter the IPv6 address that you want to know the server name for in the Reverse Lookup the IP Address field.
3. Click Go.
The appliance will return the server name for the IPv6 address.
The Connection Limit TopX tool lists the top 10 connections by the source and destination IP addresses. Before you can use this tool, you must enable source IP limiting and/or destination IP limiting for your appliance. Navigate to the Firewall > Access Rules page and enable connection limiting on the desired access rules.
Check GEO Location and BOTNET Server Lookup
The Geo-IP and Botnet Filtering feature allows administrators to block connections to or from a geographic location based on IP address, and to or from Botnet command and control servers. Additional functionality for this feature is available on the Security Services > Geo-IP and Botnet Filter page. For full details, see Security Services > Geo-IP and Botnet Filter.
The MX Lookup and Banner Check tool allows you to look up a domain or IP address. Your configured DNS servers are displayed in the DNS Server 1/2/3 fields, but are not editable. After you type a domain name, such as “google.com” into the Lookup name or IP field and click Go, the output is displayed under Result. The results include the domain name or IP address that you entered, the DNS server from your list that was used, the resolved email server domain name and/or IP address, and the banner received from the domain server or a message that the connection was refused. The contents of the banner depends on the server you are looking up.
Trace Route is a diagnostic utility to assist in diagnosing and troubleshooting router connections on the Internet. By using Internet Connect Message Protocol (ICMP) echo packets similar to Ping packets, Trace Route can test interconnectivity with routers and other hosts that are farther and farther along the network path until the connection fails or until the remote host responds.
1. Select Trace Route from the Diagnostic Tool menu.
Type the IP address or domain name of the destination host in the TraceRoute this host or IP addres field.
3. In the Interface pulldown menu, select which interface you want to test the trace route from. Selecting ANY allows the appliance to choose among all interfaces—including those not listed in the pulldown menu.
4. Click Go.
A second window is displayed with each hop to the destination host. By following the route, you can diagnose where the connection fails between the SonicWALL security appliance and the destination.
TraceRoute for IPv6
For complete information on SonicWALL’s implementation of IPv6, see the Appendix C: IPv6 Appendix.
The TraceRoute tool includes a new Prefer IPv6 networking option.
When testing interconnectivity with routers and other hosts, it uses the first IP address that is returned and shows the actual TraceRoute address. If both an IPv4 and IPv6 address are returned, by default, the firewall will TraceRoute the IPv4 address.
If the Prefer IPv6 networking option is enabled, the firewall will TraceRoute the IPv6 address.
PMTU Discovery is a diagnostic tool that determines the maximum transmission unit (MTU) on the network path between the SonicWALL security appliance and a remote host. It is used to avoid IP fragmentation of traffic between the two hosts.
For IPv4 packets, Path MTU Discovery works by setting the "Don't Fragment" (DF) option bit in the IP headers of outgoing packets. When the DF option bit is set for a packet, and the packet traverses a device with an MTU smaller than the packet size, the device drops the packet and sends back an ICMP Fragmentation Needed message containing its MTU, allowing the source host to reduce its Path MTU appropriately. The process repeats until the MTU is small enough to traverse the entire path without fragmentation. IPv6 functions similarly, but the DF option bit is not required. IPv6 devices automatically send an ICMPv6 Packet Too Big message if the packet exceeds the devices MTU size.
By determining the MTU size on a network path and configuring the MTU for your SonicWALL security appliance below the path MTU size, you avoid the potential delay caused by negotiation of the MTU size and other MTU-related network issues.
To configure Path MTU Discovery, perform the following tasks:
1. On the System > Diagnostics page, select PMTU Discovery for the Diagnostic Tool.
2. In the Path MTU Discovery to this host or IP address, enter the IP address or host name that you want to measure the Path MTU for. This can be either an IPv4 or IPv6 address.
3. Optionally, in the Interface pulldown menu, you can select one of the configured WAN interfaces on the appliance to check the Path MTU for that interface. When the Interface pulldown menu is set to ANY, the appliance chooses among all of its interfaces.
4. Click Go. The Path MTU Discovery results are displayed in a pop-up window.
Note If you do not see this window, check that your browser allows pop-ups for the SonicWALL GUI.
The following example shows the Path MTU Discovery for the route between 192.168.168.168 and 58.63.236.236. The smallest MTU is 1492 bytes between 9.9.9.8 and 0.103.48.1.
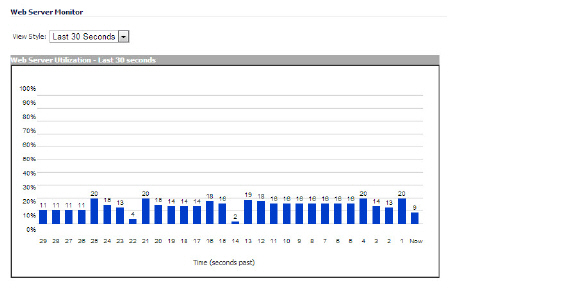
The Web Server Monitor tool displays the CPU utilization of the Web server over several periods of time. The time frame of the Web Server Monitor can be changed by selecting one of the following options in the View Style pulldown menu: last 30 seconds, last 30 minutes, last 24 hours, or last 30 days.
The User Monitor tool displays details on all user connections to the SonicWALL security appliance.
The following options can be configured to modify the User Monitor display:
• View Style – Select whether to display the Last 30 Minutes, the Last 24 Hours, or the Last 30 Days.
• Vertical Axis – Select whether the scale of the vertial axis should be set for 10, 100, or 1000 users.
• Show – Select whether to show All Users, All Non-Guest Users, Users Authenticated by Single-Sign-On, Remote Users via SSL VPN, Remote Users with GVC/L2TP Client, Users Authenticated by Web Login, or Guest Users.