Both Link Aggregation and Port Redundancy are configured on the
Advanced
tab of the Edit
Interface
window in the SonicOS UI.
|
|
•
|
“
Link Aggregation
”
- Groups multiple Ethernet interfaces together forming a single logical link to support greater throughput than a single physical interface could support. This provides the ability to send multi-gigabit traffic between two Ethernet domains.
|
|
|
•
|
“
Port Redundancy
”
- Configures a single redundant port for any physical interface that can be connected to a second switch to prevent a loss of connectivity in the event that either the primary interface or primary switch fail.
|
Link Aggregation is used to increase the available bandwidth between the firewall and a switch
by aggregating up to four interfaces into a single aggregate link, referred to as a Link Aggregation Group (LAG). All ports in an aggregate link must be connected to the same switch. The firewall uses a round-robin algorithm for load balancing traffic across the interfaces in a Link Aggregation Group. Link Aggregation also provides a measure of redundancy, in that if one interface in the LAG goes down, the other interfaces remain connected.
Link Aggregation is referred to using different terminology by different vendors, including Port
Channel, Ether Channel, Trunk, and Port Grouping.
SonicWALL provides multiple methods for protecting against loss of connectivity in the case of
a link failure, including High Availability (HA), Load Balancing Groups (LB Groups), and now Link Aggregation. If all three of these features are configured on a firewall, the following order of precedence is followed in the case of a link failure:
HA takes precedence over Link Aggregation. Because each link in the LAG carries an equal
share of the load, the loss of a link on the Active firewall will force a failover to the Idle firewall (if all of its links remain connected). Physical monitoring needs to be configured only on the primary aggregate port.
When Link Aggregation is used with a LB Group, Link Aggregation takes precedence. LB will
take over only if all the ports in the aggregate link are down.
To configure Link Aggregation, perform the following tasks:
|
1.
|
On the
Network > Interfaces
page, click the configure
icon for the interface that is to be designated the master of the Link Aggregation Group. The Edit Interface window displays.
|
|
3.
|
In the
Redundant/Aggregate Ports
pulldown menu, select Link Aggregation
.
|
|
4.
|
The
Aggregate Port
option is displayed with a checkbox for each of the currently unassigned interfaces on the firewall. Select up to three other interfaces to assign to the LAG.
|
|
5.
|
Set the
Link Speed
for the interface to Auto-Negotiate
.
|
Port Redundancy provides a simple method for configuring a redundant port for a physical
Ethernet port. This is a valuable feature, particularly in high-end deployments, to protect against switch failures being a single point of failure.
When the primary interface is active, it processes all traffic to and from the interface. If the
primary interface goes down, the backup interface takes over all outgoing and incoming traffic. The backup interface assumes the MAC address of the primary interface and sends the appropriate gratuitous ARP on a failover event. When the primary interface comes up again, it resumes responsibility for all traffic handling duties from the backup interface.
In a typical Port Redundancy configuration, the primary and backup interfaces are connected
to different switches. This provides for a failover path in case the primary switch goes down. Both switches must be on the same Ethernet domain. Port Redundancy can also be configured with both interfaces connected to the same switch.
SonicWALL provides multiple methods for protecting against loss of connectivity in the case of
a link failure, including High Availability (HA), Load Balancing Groups (LB Groups), and now Port Redundancy. If all three of these features are configured on a firewall, the following order of precedence is followed in the case of a link failure:
When Port Redundancy is used with HA, Port Redundancy takes precedence. Typically an
interface failover will cause an HA failover to occur, but if a redundant port is available for that interface, then an interface failover will occur but not an HA failover. If both the primary and backup redundant ports go down, then an HA failover will occur (assuming the backup firewall has the corresponding port active).
When Port Redundancy is used with a LB Group, Port Redundancy again takes precedence.
Any single port (primary or backup) failures are handled by Port Redundancy just like with HA. When both the ports are down then LB kicks in and tries to find an alternate interface.
To configure Port Redundancy, perform the following tasks:
|
1.
|
On the
Network > Interfaces
page, click the configure
icon for the interface that is to be designated the master of the Link Aggregation Group. The Edit Interface window displays.
|
|
3.
|
In the
Redundant/Aggregate Ports
pulldown menu, select Port Redundancy
.
|
|
4.
|
The
Redundant Port
pulldown menu is displayed, with all of the currently unassigned interfaces available. Select one of the interfaces.
|
|
5.
|
Set the
Link Speed
for the interface to Auto-Negotiate
.
|
Routed Mode provides an alternative for NAT for routing traffic between separate public IP
address ranges. Consider the following topology where the firewall is routing traffic across two public IP address ranges:
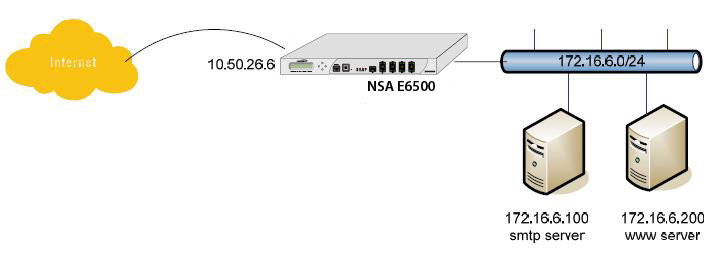
By enabling Routed Mode on the interface for the 172.16.6.0 network
, all inbound and outbound traffic will be routed to the WAN interface configured for the 10.50.26.0 network.
To configure Routed Mode, perform the following steps:
|
1.
|
Click on the
configure
icon for the appropriate interface. The Edit Interface window displays.
|
|
3.
|
Under the
Expert Mode Settings
heading, select the Use Routed Mode - Add NAT Policy
to prevent outbound\inbound translation
checkbox to enable Routed Mode for the interface.
|
|
4.
|
In the
Set NAT Policy's outbound\inbound interface to
pulldown menu, select the WAN interface that is to be used to route traffic for the interface.
|
The firewall then creates
two “No-NAT” policies for both the configured interface and the selected WAN interface. These policies override any more general Many to One NAT policies that may be configured for the interfaces.
