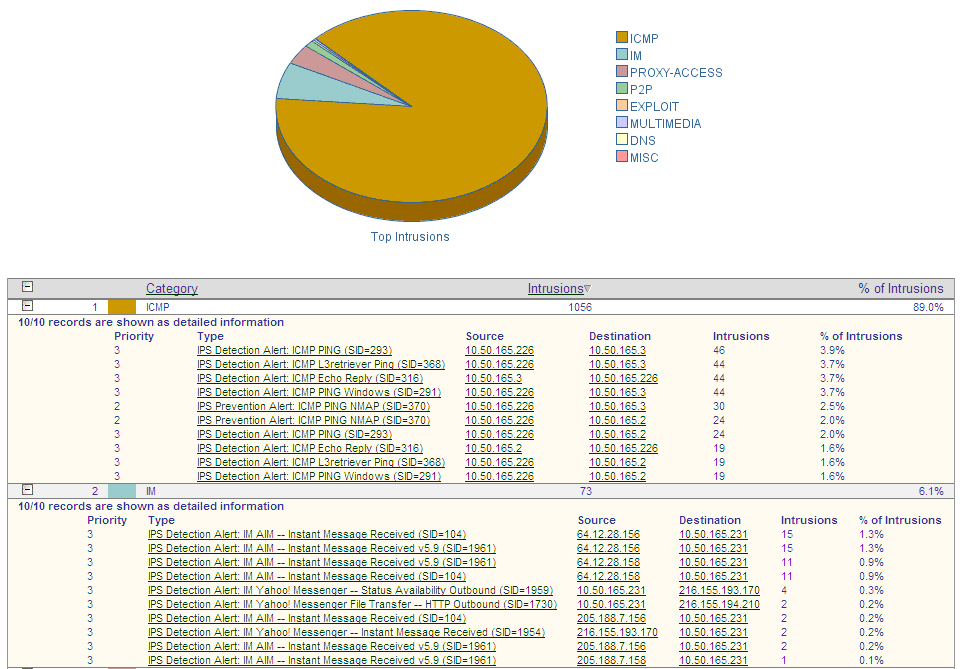
The SonicWALL security appliance maintains an Event log for tracking potential security
threats. This log can be viewed in the Log > View
page, or it can be automatically sent to an e-mail address for convenience and archiving. The log is displayed in a table and can be sorted by column.
The SonicWALL security appliance can alert you of important events, such as an attack to the
SonicWALL security appliance. Alerts are immediately e-mailed, either to an e-mail address or to an e-mail pager. Each log entry contains the date and time of the event and a brief message describing the event.
The log is displayed in a table and is sortable by column. The log table columns include:
|
|
•
|
Time
- the date and time of the event.
|
|
|
•
|
Priority
- the level of priority associated with your log event.
Syslog uses eight categories to characterize messages – in descending order of severity, the categories include:
|
Specify a priority level on a SonicWALL security appliance on the
Log
> Categories
page to log messages for that priority level, plus all messages tagged with a higher severity. For example, select ‘error’ as the priority level to log all messages tagged as ‘error,’ as well as any messages tagged with ‘critical,’ ‘alert,’ and ‘emergency.’ Select ‘debug’ to log all messages.
|
|
•
|
Category
- the type of traffic, such as Network Access
or Authenticated Access
.
|
|
|
•
|
Message
- provides description of the event.
|
|
|
•
|
Source
- displays source network and IP address.
|
|
|
•
|
Destination
- displays the destination network and IP address.
|
|
|
•
|
Notes
- provides additional information about the event.
|
|
|
•
|
Rule
- notes Network Access Rule affected by event.
|
The
Log View
table provides easy pagination for viewing large numbers of log events. You can navigate these log events by using the navigation control bar located at the top right of the Log
View
table. Navigation control bar includes four buttons. The far left button displays the first page of the table. The far right button displays the last page. The inside left and right arrow buttons moved the previous or next page respectively.
You can sort the entries in the table by clicking on the column header. The entries are sorted
by ascending or descending order. The arrow to the right of the column entry indicates the sorting status. A down arrow means ascending order. An up arrow indicates a descending order.
To update log messages, clicking the
Refresh
button near the top right corner of the page.
To delete the contents of the log, click the
Clear Log
button near the top right corner of the page.
To export the contents of the log to a defined destination, click the
Export Log
button below the filter table.You can export log content to two formats:
|
|
•
|
Comma-separated value
(CSV
) format
--Used for importing into Excel or other presentation development applications.
|
If you have configured the SonicWALL security appliance to e-mail log files, clicking
E-mail Log
near the top right corner of the page sends the current log files to the e-mail address specified in the Log > Automation > E-mail
section.
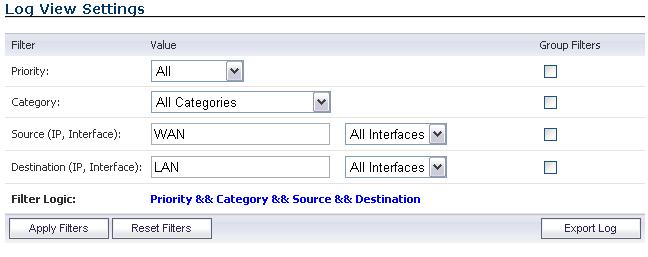
You can filter the results to display only event logs matching certain criteria. You can filter by
Priority
, Category
, Source
(IP
or Interface
), and Destination
(IP
or Interface
).
Source interface
AND
Destination interface
|
Step 3
|
Check the
Group Filters
box next to any two or more criteria to combine them with a logical OR
.
|
For example, if you enter values for
Source IP
, Destination IP
, and Protocol
, and check Group Filters
next to Source IP
and Destination IP
, the search string will look for connections matching:
(
Source IP
OR
Destination IP
) AND
Protocol
|
Step 4
|
Click
Apply Filter
to apply the filter immediately to the Log View Settings
table. Click Reset
Filters
to clear the filter and display the unfiltered results again.
|
The following example filters for log events resulting from traffic from the WAN to the LAN:
For a complete reference guide of log event messages, refer to the
SonicOS Log Events Reference Guide
.
SonicWALL UTM appliances have configurable deep-packet classification capabilities that
intersect with forensic and content-management products. While the SonicWALL can reliably detect and prevent any ‘interesting-content’ events, it can only provide a record of the occurrence, but not the actual data of the event.
Of equal importance are diagnostic applications where the interesting-content is traffic that is
being unpredictably handled or inexplicably dropped.
Although the SonicWALL can achieve interesting-content using our Enhanced packet capture
diagnostic tool, data-recorders are application-specific appliances designed to record all the packets on a network. They are highly optimized for this task, and can record network traffic without dropping a single packet.
While data-recorders are good at recording data, they lack the sort of deep-packet inspection
intelligence afforded by IPS/GAV/ASPY/AF. Consider the minimal requirements of effective data analysis:
Together, a UTM device (a SonicWALL appliance) and data-recorder (a Solera Networks
appliance) satisfy the requirements to offer outstanding forensic and data-leakage capabilities.
The Solera appliance can search its data-repository, while also allowing the administrator to
define “interesting-content” events on the SonicWALL. The level of logging detail and frequency of the logging can be configured by the administrator. Nearly all events include Source IP, Source Port, Destination IP, Destination Port, and Time. SonicOS Enhanced has an extensive set of log events, including:
|
|
•
|
User-events
—Administrative access, single sign-on activity, user logins, content filtering details
|
The following is an example of the process of distributed event detection and replay:
The client and NPCS must be able to reach one another. Usually, this means the client and the
NPCS will be in the same physical location, both connected to the SonicWALL appliance. In any case, the client will be able to directly reach the NPCS, or will be able to reach the NPCS through the SonicWALL. Administrators in a remote location will require some method of VPN connectivity to the internal network. Access from a centralized GMS console will have similar requirements.
SonicOS currently allocates 32K to a rolling log buffer. When the log becomes full, it can be
emailed to a defined recipient and flushed, or it can simply be flushed. Emailing provides a simple version of logging persistence, while GMS provides a more reliable and scalable method.
By offering the administrator the option to deliver logs as either plain-text or HTML, the
administrator has an easy method to review and replay events logged.
To provide the ability to identify and view events across an entire enterprise, a GMS update will
be required. Device-specific interesting-content events at the GMS console appear in Reports
> Log Viewer Search
page, but are also found throughout the various reports, such as Top Intrusions Over Time.