Users_usersSettingsView
Configuring Settings on Users > Settings
On this page, you can configure the authentication method required, global user settings, and an acceptable user policy that is displayed to users when logging onto your network.
Configuration instructions for the settings on this page are provided in the following sections:
In the Authentication method for login drop-down list, select the type of user account management your network uses:
• Select Local Users to configure users in the local database in the SonicWALL appliance using the Users > Local Users and Users > Local Groups pages.
For information about using the local database for authentication, see Using Local Users and Groups for Authentication.
For detailed configuration instructions, see the following sections:
• Select RADIUS if you have more than 1,000 users or want to add an extra layer of security for authenticating the user to the SonicWALL. If you select RADIUS for user authentication, users must log into the SonicWALL using HTTPS in order to encrypt the password sent to the SonicWALL. If a user attempts to log into the SonicWALL using HTTP, the browser is automatically redirected to HTTPS.
For information about using a RADIUS database for authentication, see Using RADIUS for Authentication.
For detailed configuration instructions, see Configuring RADIUS Authentication
• Select RADIUS + Local Users if you want to use both RADIUS and the SonicWALL local user database for authentication.
• Select LDAP if you use a Lightweight Directory Access Protocol (LDAP) server, Microsoft Active Directory (AD) server, or Novell eDirectory to maintain all your user account data.
For information about using an LDAP database for authentication, see Using LDAP / Active Directory / eDirectory Authentication.
For detailed configuration instructions, see Configuring LDAP Integration in SonicOS Enhanced
• Select LDAP + Local Users if you want to use both LDAP and the SonicWALL local user database for authentication.
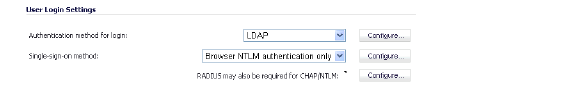
In the Single-sign-on method drop-down list, select one of the following:
• Select SonicWALL SSO Agent if you are using Active Directory for authentication and the SonicWALL SSO Agent is installed on a computer in the same domain.
• Select SonicWALL SSO Agent if you are using Terminal Services and the SonicWALL Terminal Services Agent (TSA) is installed on a terminal server in the same domain.
• Select Browser NTLM authentication only if you want to authenticate Web users without using the SonicWALL SSO Agent or TSA. Users are identified as soon as they send HTTP traffic. NTLM requires RADIUS to be configured (in addition to LDAP, if using LDAP), for access to MSCHAP authentication. If LDAP is selected above, a separate Configure button for RADIUS appears here when NTLM is selected.

• Select None if not using SSO.
For detailed SSO configuration instructions, see Configuring Single Sign-On.
For Browser NTLM authentication configuration, see Configuring Your SonicWALL Appliance for Browser NTLM Authentication.
In the Show user authentication page for field, enter the number of minutes that a user has to log in before the login page times out. If it times out, a message displays saying they must click before attempting to log in again.
Select Case-sensitive user names to enable matching based on capitalization of user account names.
Select Enforce login uniqueness to prevent the same user name from being used to log into the network from more than one location at a time. This setting applies to both local users and RADIUS/LDAP users. However the login uniqueness setting does not apply to the default administrator with the username admin.
Select Redirect users from HTTPS to HTTP on completion of login if you want users to be connected to the network through your SonicWALL appliance via HTTP after logging in via HTTPS. If you have a large number of users logging in via HTTPS, you may want to redirect them to HTTP, because HTTPS consumes more system resources than HTTP. If you deselect this option, you will see a warning dialog.
Select Allow HTTP login with RADIUS CHAP mode to have a CHAP challenge be issued when a RADIUS user attempts to log in using HTTP. This allows for a secure connection without using HTTPS, preventing the browser from sending the password in clear text over HTTP. Be sure to check that the RADIUS server supports this option.
Note Administrators who log in using this method will be restricted in the management operations they can perform (because some operations require the appliance to know the administrator's password, which is not the case for this authentication method).
Select either Plain text or HTML for One-time password Email format, depending on your preference if you are using One-Time Password authentication.
The settings listed below apply to all users when authenticated through the SonicWALL.
• Inactivity timeout (minutes): users can be logged out of the SonicWALL after a preconfigured inactivity time. Enter the number of minutes in this field. The default value is 5 minutes.
• Enable login session limit: you can limit the time a user is logged into the SonicWALL by selecting the check box and typing the amount of time, in minutes, in the Login session limit (minutes) field. The default value is 30 minutes.
• Show user login status window: causes a status window to display with a Log Out button during the user’s session. The user can click the Log Out button to log out of their session.
The User Login Status window displays the number of minutes the user has left in the login session. The user can set the remaining time to a smaller number of minutes by entering the number and clicking the Update button.
If the user is a member of the SonicWALL Administrators or Limited Administrators user group, the User Login Status window has a Manage button the user can click to automatically log into the SonicWALL appliance’s management interface. See Disabling the User Login Status Popup for information about disabling the User Login Status window for administrative users. See Configuring Local Groupsfor group configuration procedures.
• User's login status window sends heartbeat every (seconds): Sets the frequency of the heartbeat signal used to detect whether the user still has a valid connection
• Enable disconnected user detection: Causes the SonicWALL to detect when a user’s connection is no longer valid and end the session.
• Timeout on heartbeat from user's login status window (minutes): Sets the time needed without a reply from the heartbeat before ending the user session.
Allow these HTTP URLs to bypass users authentication access rules: Define a list of URLs users can connect to without authenticating. To add a URL to the list:
Step 1 Click Add below the URL list.
Step 2 In the Enter URL window, enter the top level URL you are adding, for example, www.sonicwall.com. All sub directories of that URL are included, such as www.sonicwall.com/us/Support.html. Click on OK to add the URL to the list.
For wildcard matching, prefix with '*.' and/or suffix with '...', e.g.: *.windowsupdate.com...
To allow access to a file on any host, prefix with '*/', e.g.: */wpad.dat.
Auto-Configuration of URLs to Bypass User Authentication
You can use the Auto-Configure utility to temporarily allow traffic from a single specified IP address to bypass authentication. The destinations that traffic accesses are then recorded and used to allow that traffic to bypass user authentication. Typically this is used to allow traffic such as anti-virus updates and Windows updates. To auto-configure the URL bypass list, perform the following steps:
Step 1 On the Users > Settings page, under the Other Global User Settings heading, click the Auto-configure button.
Step 2 Enter the IP address that you want to allow traffic from and click Start.
Step 3 Run the traffic that needs to bypass authentication. Traffic that would otherwise be blocked by firewall rules needing authentication will be allowed through and the destinations recorded. As traffic is detected, the destionatin addresses will be recorded in the window.
Step 4 To convert a specific address to a more generic wildcard, select the address and click Convert to wildcard.
Step 5 To convert a specific address to a more generic class B (16-bit) or class C (24-bit) network, select the address, click either Class B or Class C and click Convert to network(s).
Tip Windows Updates access some destinations via HTTPS, and those can only be tracked by IP address. However, the actual IP addresses accessed each time may vary and so rather than trying to set up a bypass for each such IP address, it may be better to use the Convert to network(s) option to set it up to allow bypass for HTTPS to all IP addresses in that network.
Step 6 When you have detected all of the necessary addresses click Stop and click Save Selected.
Tip You may want to run updates multiple times in case the destinations that are accessed may vary.
An acceptable use policy (AUP) is a policy that users must agree to follow in order to access a network or the Internet. It is common practice for many businesses and educational facilities to require that employees or students agree to an acceptable use policy before accessing the network or Internet through the SonicWALL.
The Acceptable Use Policy section allows you to create the AUP message window for users. You can use HTML formatting in the body of your message. Clicking the Example Template button creates a preformatted HTML template for your AUP window.
• Display on login from - Select the network interface(s) you want to display the Acceptable Use Policy page when users login. You can choose Trusted Zones, WAN Zone, Public Zones, Wireless Zones, and VPN Zone in any combination.
• Window size (pixels) - Allows you to specify the size of the AUP window defined in pixels. Checking the Enable scroll bars on the window allows the user to scroll through the AUP window contents.
• Enable scroll bars on window - Turns on the scroll bars if your content will exceed the display size of the window.
Acceptable use policy page content - Enter your Acceptable Use Policy text in the text box. You can include HTML formatting. The page that is displayed to the user includes an I Accept button or Cancel button for user confirmation.
Click the Example Template button to populate the content with the default AUP template, which you can modify:
<font face=arial size=3>
<center><b><i>Welcome to the SonicWALL</center></b></i>
<font size=2>
<table width="100%" border="1">
<tr><td>
<font size=2>
<br><br><br>
<center>Enter your usage policy terms here.
<br><br><br>
</td></tr>
</table>
Click "I Accept" only if you wish to accept these terms and continue,
or otherwise select "Cancel".
Click the Preview button to display your AUP message as it will appear for the user.
SonicOS now provides the ability to customize the text of the login authentication pages that are presented to users. Administrators can translate the login-related pages with their own wording and apply the changes so that they take effect without rebooting.
Although the entire SonicOS interface is available in different languages, sometimes the administrator does not want to change the entire UI language to a specific local language.
However, if the firewall requires authentication before users can access other networks, or enables external access services (e.g. VPN, SSL-VPN), those login related pages usually should be localized to make them more usable for typical users.
The Customizable Login Page feature provides the following functionality:
• Keeps the style of original login by default
• Allows administrators to customize login related pages
• Allows administrators to use the default login related pages as templates
• Allows administrators to save customized pages into system preferences
• Allows administrators to preview their changes before saving to preferences
• Presents customized login related pages to typical users
The following login-related pages can be customized:
• Admin Preempt
• Login Authentication
• Logged Out
• Login Full
• Login Disallowed
• Login Lockour
• Login Status
• Guest Login Status
• Policy Access Barred
• Policy Access Down
• Policy Access Unavailable
• Policy Login Redirect
• Policy SSO Probe Failure
• User Password Update
• User Login Message
To customize one of these pages, perform the following steps:
1. On the Users > Settings page, scroll down to the Customize Login Pages section.
2. Select the page to be customized from the Select Login Page pulldown menu.
3. Scroll to the bottom of the page and click Default to load the default content for the page.
4. Edit the content of the page.
Note The "var strXXX =" lines in the template pages are customized JavaScript Strings. You can change them into your preferring wonrding. Modifications should follow the JavaScript syntax. You can also edit the wording in the HTML section.
5. Click Preview to preview how the customized page will look.
6. When you are finished editing the page, click Apply.
Leave the Login Page Contents field blank and apply the change to revert the default page to users.
Caution Be careful to verify the HTML of your custom login page before deploying it, because HTML errors may cause the login page to not function properly.
An alternative login page is always available for the administrator, in case a customized login page has any issues. To access the alternate login page, manually input the URL:
https://(device_ip)/defauth.html
directly into the address line of browser (case sensitive). The default login page without any customization is then displayed, allowing you to login as normal and reset your customized login related pages.