High_Availability
High Availability (HA) allows two identical firewalls running SonicOS to be configured to provide a reliable, continuous connection to the public Internet. This section provides conceptual information and describes how to configure High Availability (HA) in SonicOS. This section contains the following main sections:
• Stateful Synchronization Overview
• Active/Active DPI HA Overview
• Active/Standby and Active/Active DPI Prerequisites
• High Availability > Settings
• High Availability > Advanced
• High Availability > Monitoring
The following sections provide overviews of Dell SonicWALL’s implementation of HA:
– Benefits of Active/Standby HA
– How Does Active/Standby HA Work?
• Stateful Synchronization Overview
– Benefits of Stateful Synchronization
– How Does Stateful Synchronization Work?
• Active/Active DPI HA Overview
– Benefits of Active/Active DPI HA
• Active/Standby and Active/Active DPI Prerequisites
• Physically Connecting Your Appliances
• Registering and Associating Appliances on MySonicWALL
• Licensing High Availability Features
High Availability has four operation modes.
• Active/Standby
• Active/Active DPI
• Active/Active Clustering
• Active/Active DPI Clustering
The four HA operation modes can be selected on the High Availability > Settings page, under the General tab, from the pull-down menu:
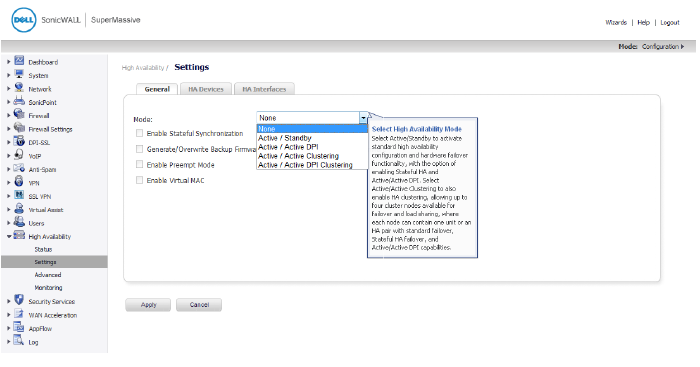
Active/Standby—Active/Standby mode provides basic high availability with the configuration of two identical firewalls as a High Availability Pair. The Active unit handles all traffic, while the Standby unit shares its configuration settings and can take over at any time to provide continuous network connectivity if the Active unit stops working. By default, Active/Standby mode is stateless, meaning that network connections and VPN tunnels must be re-established after a failover. To avoid this, Stateful Synchronization can be licensed and enabled with Active/Standby mode. In this Stateful HA mode, the dynamic state is continuously synchronized between the Active and Standby units. When the Active unit encounters a fault condition, stateful failover occurs as the Standby firewall takes over the Active role with no interruptions to the existing network connections.
Note Stateful HA is supported on the NSA 2600 only with the purchase of a SonicOS Expanded License or a High Availability License. Licenses can be purchased on www.mysonicwall.com.
Active/Active DPI—The Active/Active Deep Packet Inspection (DPI) mode can be used along with the Active/Standby mode. When Active/Active DPI mode is enabled, the processor intensive DPI services, such as Intrusion Prevention (IPS), Gateway Anti-Virus (GAV), and Anti-Spyware are processed on the standby firewall, while other services, such as firewall, NAT, and other types of traffic are processed on the Active firewall concurrently.
Note Active/Active DPI is not supported on the NSA 2600, NSA 3600, or NSA 4600.
Active/Active Clustering—In this mode, multiple firewalls are grouped together as cluster nodes, with multiple Active units processing traffic (as multiple gateways), doing DPI and sharing the network load. Each cluster node consists of two units acting as a Stateful HA pair. Active/Active Clustering provides Stateful Failover support in addition to load-sharing. Optionally, each cluster node can also consist of a single unit, in which case Stateful Failover and Active/Active DPI are not available.
Note Active/Active Clustering is supported by default on the SM 9000 series. Active/Active Clustering is supported on NSA 5600 and NSA 6600 only with the purchase of a SonicOS Expanded License. Licenses can be purchased on www.mysonicwall.com.
Active/Active DPI Clustering—This mode allows for the configuration of up to four HA cluster nodes for failover and load sharing, where the nodes load balance the application of DPI security services to network traffic. This mode can be enabled for additional performance gain, utilizing the standby units in each cluster node.
• Primary - Describes the principal hardware unit itself. The Primary identifier is a manual designation, and is not subject to conditional changes. Under normal operating conditions, the Primary hardware unit operates in an Active role.
• Secondary - Describes the subordinate hardware unit itself. The Secondary identifier is a relational designation, and is assumed by a unit when paired with a Primary unit. Under normal operating conditions, the Secondary unit operates in Standby mode. Upon failure of the Primary unit, the Secondary unit will assume the Active role.
• Active - Describes the operative condition of a hardware unit. The Active identifier is a logical role that can be assumed by either a Primary or Secondary hardware unit.
• Standby - Describes the passive condition of a hardware unit. The Standby identifier is a logical role that can be assumed by either a Primary or Secondary hardware unit. The Standby unit assumes the Active role in the event of determinable failure of the Active unit.
• Failover - Describes the actual process in which the Standby unit assumes the Active role following a qualified failure of the Active unit. Qualification of failure is achieved by various configurable physical and logical monitoring facilities described throughout the Task List section.
• Preempt - Applies to a post-failover condition in which the Primary unit has failed, and the Secondary unit has assumed the Active role. Enabling Preempt will cause the Primary unit to seize the Active role from the Secondary after the Primary has been restored to a verified operational state.
Crash Detection
The HA feature has a thorough self-diagnostic mechanism for both the Active and Standby firewalls. The failover to the standby unit occurs when critical services are affected, physical (or logical) link failure is detected on monitored interfaces, or when the SonicWALL loses power.
The self-checking mechanism is managed by software diagnostics, which check the complete system integrity of the SonicWALL device. The diagnostics check internal system status, system process status, and network connectivity. There is a weighting mechanism on both sides to decide which side has better connectivity, used to avoid potential failover looping.
Critical internal system processes such as NAT, VPN, and DHCP (among others) are checked in real time. The failing service is isolated as early as possible, and the failover mechanism repairs it automatically.
The Virtual MAC address allows the High Availability pair to share the same MAC address, which dramatically reduces convergence time following a failover. Convergence time is the amount of time it takes for the devices in a network to adapt their routing tables to the changes introduced by high availability.
Without Virtual MAC enabled, the Active and Standby appliances each have their own MAC addresses. Because the appliances are using the same IP address, when a failover occurs, it breaks the mapping between the IP address and MAC address in the ARP cache of all clients and network resources. The Secondary appliance must issue an ARP request, announcing the new MAC address/IP address pair. Until this ARP request propagates through the network, traffic intended for the Primary appliance’s MAC address can be lost.
The Virtual MAC address greatly simplifies this process by using the same MAC address for both the Primary and Secondary appliances. When a failover occurs, all routes to and from the Primary appliance are still valid for the Secondary appliance. All clients and remote sites continue to use the same Virtual MAC address and IP address without interruption.
By default, this Virtual MAC address is provided by the SonicWALL firmware and is different from the physical MAC address of either the Primary or Secondary appliances. This eliminates the possibility of configuration errors and ensures the uniqueness of the Virtual MAC address, which prevents possible conflicts. Optionally, you can manually configure the Virtual MAC address on the High Availability > Monitoring page.
The Virtual MAC setting is available even if Stateful High Availability is not licensed. When Virtual MAC is enabled, it is always used even if Stateful Synchronization is not enabled.
On the High Availability > Monitoring page, you can configure both physical and logical interface monitoring. By enabling physical interface monitoring, you enable link detection for the designated HA interfaces. The link is sensed at the physical layer to determine link viability. Logical monitoring involves configuring the SonicWALL to monitor a reliable device on one or more of the connected networks. Failure to periodically communicate with the device by the Active unit in the HA Pair will trigger a failover to the Standby unit. If neither unit in the HA Pair can connect to the device, no action will be taken.
The Primary and Secondary IP addresses configured on the High Availability > Monitoring page can be configured on LAN or WAN interfaces, and are used for multiple purposes:
• As independent management addresses for each unit (supported on all physical interfaces)
• To allow synchronization of licenses between the Standby unit and the SonicWALL licensing server
• As the source IP addresses for the probe pings sent out during logical monitoring
Configuring unique management IP addresses for both units in the HA Pair allows you to log in to each unit independently for management purposes. Note that non-management traffic is ignored if it is sent to one of these IP addresses. The Primary and Secondary firewalls’ unique LAN IP addresses cannot act as an active gateway; all systems connected to the internal LAN will need to use the virtual LAN IP address as their gateway.
If WAN monitoring IP addresses are configured, then X0 monitoring IP addresses are not required. If WAN monitoring IP addresses are not configured, then X0 monitoring IP addresses are required, since in such a scenario the Standby unit uses the X0 monitoring IP address to connect to the licensing server with all traffic routed via the Active unit.
The management IP address of the Secondary/Standby unit is used to allow license synchronization with the Dell SonicWALL licensing server, which handles licensing on a per-appliance basis (not per-HA Pair). Even if the Secondary unit was already registered on MySonicWALL before creating the HA association, you must use the link on the System > Licenses page to connect to the Dell SonicWALL server while accessing the Secondary appliance through its management IP address.
When using logical monitoring, the HA Pair will ping the specified Logical Probe IP address target from the Primary as well as from the Secondary unit. The IP address set in the Primary IP Address or Secondary IP Address field is used as the source IP address for the ping. If both units can successfully ping the target, no failover occurs. If both cannot successfully ping the target, no failover occurs, as SonicOS will assume that the problem is with the target, and not the appliances. But, if one appliance can ping the target but the other cannot, the HA Pair will failover to the unit that can ping the target.
The configuration tasks on the High Availability > Monitoring page are performed on the Primary unit and then are automatically synchronized to the Secondary.
HA allows two identical firewalls running SonicOS to be configured to provide a reliable, continuous connection to the public Internet. One firewall is configured as the Primary unit, and an identical firewall is configured as the Secondary unit. In the event of the failure of the Primary firewall, the Secondary firewall takes over to secure a reliable connection between the protected network and the Internet. Two appliances configured in this way are also known as a High Availability Pair (HA Pair).
HA provides a way to share licenses between two firewalls when one is acting as a high availability system for the other. To use this feature, you must register the appliances on MySonicWALL as Associated Products. Both appliances must be the same SonicWALL model.
Active/Standby HA provides the following benefits:
• Increased network reliability – In a High Availability configuration, the Secondary appliance assumes all network responsibilities when the Primary unit fails, ensuring a reliable connection between the protected network and the Internet.
• Cost-effectiveness – High Availability is a cost-effective option for deployments that provide high availability by using redundant firewalls. You do not need to purchase a second set of licenses for the Secondary unit in a High Availability Pair.
• Virtual MAC for reduced convergence time after failover – The Virtual MAC address setting allows the HA Pair to share the same MAC address, which dramatically reduces convergence time following a failover. Convergence time is the amount of time it takes for the devices in a network to adapt their routing tables to the changes introduced by high availability. By default, the Virtual MAC address is provided by the SonicWALL firmware and is different from the physical MAC address of either the Primary or Secondary appliances.
How Does Active/Standby HA Work?
HA requires one SonicWALL device configured as the Primary SonicWALL, and an identical SonicWALL device configured as the Secondary SonicWALL. During normal operation, the Primary SonicWALL is in an Active state and the Secondary SonicWALL in an Standby state. If the Primary device loses connectivity, the Secondary SonicWALL transitions to Active mode and assumes the configuration and role of Primary, including the interface IP addresses of the configured interfaces.
Basic Active/Standby HA provides stateless high availability. After a failover to the Secondary appliance, all the pre-existing network connections must be re-established, including the VPN tunnels that must be re-negotiated. Stateful Synchronization can be licensed and enabled separately. For more information, see Stateful Synchronization Overview.
The failover applies to loss of functionality or network-layer connectivity on the Primary SonicWALL. The failover to the Secondary SonicWALL occurs when critical services are affected, physical (or logical) link failure is detected on monitored interfaces, or when the Primary SonicWALL loses power. The Primary and Secondary SonicWALL devices are currently only capable of performing Active/Standby High Availability or Active/Active DPI – complete Active/Active high availability is not supported at present.
There are two types of settings synchronization for all configuration settings: incremental and complete. If the timestamps are in sync and a change is made on the Active unit, an incremental synchronization is pushed to the Standby unit. If the timestamps are out of sync and the Standby unit is available, a complete synchronization is pushed to the Standby unit. When incremental synchronization fails, a complete synchronization is automatically attempted.
Stateful Synchronization Overview
This section provides an introduction to the Stateful Synchronization feature. Stateful Synchronization provides dramatically improved failover performance. When enabled, the network connections and VPN tunnel information is continuously synchronized between the two units so that the Secondary can seamlessly assume all network responsibilities if the Primary appliance fails, with no interruptions to existing network connections.
This section contains the following subsections:
• Benefits of Stateful Synchronization
• How Does Stateful Synchronization Work?
Benefits of Stateful Synchronization
Stateful Synchronization provides the following benefits:
• Improved reliability - By synchronizing most critical network connection information, Stateful Synchronization prevents down time and dropped connections in case of appliance failure.
• Faster failover performance - By maintaining continuous synchronization between the Primary and Secondary appliances, Stateful Synchronization enables the Secondary appliance to take over in case of a failure with virtually no down time or loss of network connections.
• Minimal impact on CPU performance - Typically less than 1% usage.
• Minimal impact on bandwidth - Transmission of synchronization data is throttled so as not interfere with other data.
How Does Stateful Synchronization Work?
Stateful Synchronization is not load-balancing. It is an active-standby configuration where the Primary appliance handles all traffic. When Stateful Synchronization is enabled, the Primary appliance actively communicates with the Secondary to update most network connection information. As the Primary appliance creates and updates network connection information (VPN tunnels, active users, connection cache entries, etc.), it immediately informs the Secondary appliance. This ensures that the Secondary appliance is always ready to transition to the Active state without dropping any connections.
The synchronization traffic is throttled to ensure that it does not interfere with regular network traffic. All configuration changes are performed on the Primary appliance and automatically propagated to the Secondary appliance. The High Availability pair uses the same LAN and WAN IP addresses—regardless of which appliance is currently Active.
When using SonicWALL Global Management System (GMS) to manage the appliances, GMS logs into the shared WAN IP address. In case of a failover, GMS administration continues seamlessly, and GMS administrators currently logged into the appliance will not be logged out, however Get and Post commands may result in a timeout with no reply returned.
The following table lists the information that is synchronized and information that is not currently synchronized by Stateful Synchronization.
|
Stateful Synchronization Example
In case of a failover, the following sequence of events occurs:
1. A PC user connects to the network, and the Primary firewall creates a session for the user.
2. The Primary appliance synchronizes with the Secondary appliance. The Secondary now has all of the user’s session information.
3. The administrator restarts the Primary unit.
4. The Secondary unit detects the restart of the Primary unit and switches from Standby to Active.
5. The Secondary appliance begins to send gratuitous ARP messages to the LAN and WAN switches using the same Virtual MAC address and IP address as the Primary appliance. No routing updates are necessary for downstream or upstream network devices.
6. When the PC user attempts to access a Web page, the Secondary appliance has all of the user’s session information and is able to continue the user’s session without interruption.
With Active/Active DPI enabled on a Stateful HA pair, the Deep Packet Inspection services are processed on the standby firewall of an HA pair concurrently with the processing of firewall, NAT, and other modules on the active firewall. The following DPI services are affected:
• Intrusion Prevention Service (IPS)
• Gateway Anti-Virus (GAV)
• Gateway Anti-Spyware
• Application Control
To use the Active/Active DPI feature, the administrator must configure an additional interface as the Active/Active DPI Interface. For example, if you choose to make X5 the Active/Active DPI Interface, you must physically connect X5 on the active unit to X5 on the standby unit in the HA pair. Certain packet flows on the active unit are selected and offloaded to the standby unit on the Active/Active DPI Interface. DPI is performed on the standby unit and then the results are returned to the active unit over the same interface. The remaining processing is performed on the active unit.
Benefits of Active/Active DPI HA
Active/Active DPI taps into the unused CPU cycles available in the standby unit, but the traffic still arrives and leaves through the active unit. The standby unit only sees the network traffic offloaded by the active unit, and processing of all modules other than DPI services is restricted to the active unit.
Active/Standby and Active/Active DPI Prerequisites
This section lists the supported platforms, provides recommendations and requirements for physically connecting the units, and describes how to register, associate, and license the units for High Availability.
Active/Active DPI is supported only on the following Dell SonicWALL models:
• SuperMassive 9600
• SuperMassive 9400
• SuperMassive 9200
• NSA 6600
• NSA 5600
Note Active/Active DPI is supported on the NSA 5600 and NSA 6600 with the purchase of an expanded license.
Active/Active DPI is not supported on the following Dell SonicWALL models:
• NSA 4600
• NSA 3600
• NSA 2600
Physically Connecting Your Appliances
High Availability requires additional physical connections among the affected Dell SonicWALL appliances.For all modes, you need connections for HA Control and HA Data. Active/Active DPI requires an additional connection.
In any High Availability deployment, you must physically connect the LAN and WAN ports of all units to the appropriate switches.
It is important that the X0 interfaces from all units be connected to the same broadcast domain. Otherwise, traffic failover will not work. Also, X0 is the default redundant HA port; in case the normal HA Control link fails, X0 is used to communicate heartbeats between units. Without X0 in the same broadcast domain, both units would become active if the HA Control link fails.
A WAN connection to the Internet is useful for registering your appliances on MySonicWALL and for synchronizing licensing information. Unless live communication with SonicWALL's licensing server is not permitted due to network policy, the WAN (X1) interface should be connected before registration and licensing are performed.
Dell SonicWALL network security appliances requires the following interface link speeds for each designated HA interface:
• HA Control Interface—Can be a 1GB or 10GB interface. 1GB is recommended.
Note Link Aggregation and Port Redundancy are not supported for the HA Control Interface.
• HA Data Interface—Can be a 1GB or 10GB interface. 10GB is recommended.
The HA Control Interface and the HA Data Interface can share the same single interface.
If they share a single interface, 10GB is recommended.
• Active/Active DPI Interface—Can be a 1GB or 10GB interface.
Connecting the Active/Active DPI Interfaces for Active/Active DPI
For Active/Active DPI, you must physically connect at least one additional interface, called the Active/Active DPI Interface, between the two appliances in each HA pair, or Cluster Node. The connected interfaces must be the same number on both appliances, and must initially appear as unused, unassigned interfaces in the Network > Interfaces page. For example, you could connect X5 on the Primary unit to X5 on the Secondary if X5 is an unassigned interface. After enabling Active/Active DPI, the connected interface will have a Zone assignment of HA Data-Link.
Certain packet flows on the active unit are selected and offloaded to the standby unit on the Active/Active DPI Interface. DPI is performed on the standby unit and then the results are returned to the active unit over the same interface.
Optionally, for port redundancy with Active/Active DPI, you can physically connect a second Active/Active DPI Interface between the two appliances in each HA pair. This interface will take over transferring data between the two units during Active/Active DPI processing if the first Active/Active DPI Interface has a fault.
To connect the Active/Active DPI Interfaces for Active/Active DPI:
1. Decide which interface to use for the additional connection between the appliances in the HA pair. The same interface must be selected on each appliance.
2. In the SonicOS management interface, navigate to the Network > Interfaces page and ensure that the Zone is Unassigned for the intended Active/Active DPI Interface.
3. Using a standard Ethernet cable, connect the two interfaces directly to each other.
4. Optionally, for port redundancy with Active/Active DPI, physically connect a second Active/Active DPI Interface between the two appliances in each HA pair.
Registering and Associating Appliances on MySonicWALL
To use High Availability, you must register both appliances and associate them for HA on MySonicWALL. When you click the link for a registered appliance in your MySonicWALL page, the Service Management page displays for that appliance. At the bottom of the Service Management page, you can click the HA Secondary link under Associated Products. Then follow the instructions to select and associate the other unit for your HA Pair.
After the appliances are associated as an HA pair, they can share licenses. In addition to High Availability licenses, this includes the SonicOS license, the Support subscription, and the security services licenses. The only licenses that are not shareable are for consulting services, such as the SonicWALL GMS Preventive Maintenance Service.
It is not required that the Primary and Secondary appliances have the same security services enabled. The security services settings will be automatically updated as part of the initial synchronization of settings. License synchronization is used so that the Secondary appliance can maintain the same level of network protection provided before the failover.
MySonicWALL provides several methods of associating the two appliances. You can start by registering a new appliance, and then choosing an already-registered unit to associate it with. Or, you can associate two units that are both already registered. You can also start the process by selecting a registered unit and adding a new appliance with which to associate it.
Note Even if you first register your appliances on MySonicWALL, you must individually register both the Primary and the Secondary appliances from the SonicOS management interface while logged into the individual management IP address of each appliance. This allows the Secondary unit to synchronize with the Dell SonicWALL license server and share licenses with the associated Primary appliance. When Internet access is restricted, you can manually apply the shared licenses to both appliances.
For information about configuring and using the individual management IP address of each appliance, see About High Availability Monitoring with Active/Clustering and High Availability > Monitoring.
Licensing High Availability Features
Active/Active Clustering, Stateful High Availability, and Active/Active DPI licenses are included on registered firewalls. So, you do not need to purchase any additional licenses to use these High Availability features.
Note Active/Active Clustering and Stateful High Availability licenses must be activated on each appliance, either by registering the unit on MySonicWALL from the SonicOS management interface, or by applying the license keyset to each unit if Internet access is not available.
You can view system licenses on the System > Licenses page of the management interface. This page also provides a way to log into MySonicWALL.
When the firewalls in the Active/Active cluster have Internet access, each appliance in the cluster must be individually registered from the SonicOS management interface while the administrator is logged into the individual management IP address of each appliance. This allows the Secondary units to synchronize with the SonicWALL licensing server and share licenses with the associated Primary appliances in each HA pair.
There is also a way to synchronize licenses for an HA pair whose appliances do not have Internet access. When live communication with SonicWALL's licensing server is not permitted due to network policy, you can use license keysets to manually apply security services licenses to your appliances. When you register a firewall on MySonicWALL, a license keyset is generated for the appliance. If you add a new security service license, the keyset is updated. However, until you apply the licenses to the appliance, it cannot perform the licensed services.
Note In a High Availability deployment without Internet connectivity, you must apply the license keyset to both of the appliances in the HA pair.
The following table shows the HA licenses that are included with the purchase of the Dell SonicWALL network security appliance. Some platforms require additional licensing to use the Stateful Synchronization or Active/Active DPI features. SonicOS Expanded licenses or High Availability licenses can be purchased on MySonicWALL or from a Dell SonicWALL reseller.
|
You can use one of the following procedures to apply licenses to an appliance:
• Activating Licenses from the SonicOS User Interface
• Copying the License Keyset from MySonicWALL
Activating Licenses from the SonicOS User Interface
Follow the procedure in this section to activate licenses from within the SonicOS user interface. Perform the procedure for each of the appliances in a High Availability Pair while logged into its individual LAN management IP address.
See High Availability > Monitoring for information about configuring the individual IP addresses.
1. Log in to the SonicOS user interface using the individual LAN management IP address for the appliance.
2. On the System > Licenses page, under Manage Security Services Online, click the link for To Activate, Upgrade or Renew services, click here.
3. In the Licenses > License Management page, type your MySonicWALL user name and password into the text boxes.
4. Click Submit.
5. On the Systems > Licenses page under Manage Security Services Online, verify the services listed in the Security Services Summary table.
6. Repeat this procedure for the other appliance in the HA pair.
Copying the License Keyset from MySonicWALL
You can follow the procedure in this section to view the license keyset on MySonicWALL and copy it to the firewall. Perform the procedure for each of the appliances in a High Availability Pair while logged into its individual LAN management IP address.
See High Availability > Monitoring for information about configuring the individual IP addresses.
1. Login to your MySonicWALL account at https://www.mysonicwall.com.
2. In the left navigation pane, click My Products.
3. On the My Products page, under Registered Products, scroll down to find the appliance to which you want to copy the license keyset. Click the product name or serial number.
4. On the Service Management page, click View License Keyset.
5. On the License Keyset page, use your mouse to highlight all the characters in the text box.
6. To copy the license keyset to the clipboard, press Ctrl+C.
7. Log in to the SonicOS user interface by using the individual LAN management IP address.
8. On the Systems > Licenses page under Manual Upgrade, press Ctrl+V to paste the license keyset into the Or enter keyset text box.
9. Click Submit.
10. Repeat this procedure for the other appliance in the HA pair.
The following sections describe the High Availability > Status page:
• Active/Standby High Availability Status
• Active/Active High Availability Status
Active/Standby High Availability Status
The High Availability Status table on the High Availability > Status page displays the current status of the HA Pair. If the Primary SonicWALL is Active, the first line in the table indicates that the Primary SonicWALL is currently Active.
It is also possible to check the status of the Secondary SonicWALL by logging into the unique LAN IP address of the Secondary SonicWALL. If the Primary SonicWALL is operating normally, the status indicates that the Secondary SonicWALL is currently Standby. If the Secondary has taken over for the Primary, the status table indicates that the Secondary is currently Active.
In the event of a failure in the Primary SonicWALL, you can access the management interface of the Secondary SonicWALL at the Primary SonicWALL virtual LAN IP address or at the Secondary SonicWALL LAN IP address. When the Primary SonicWALL restarts after a failure, it is accessible using the unique IP address created on the High Availability > Monitoring page. If preempt mode is enabled, the Primary SonicWALL becomes the Active firewall and the Secondary firewall returns to Standby status.
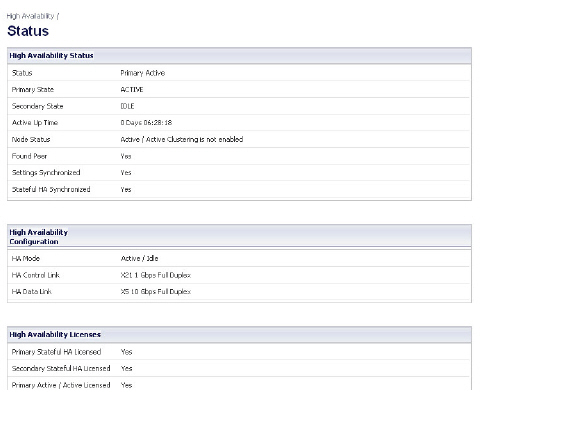
The table displays the following information:
High Availability Status
• Status – Indicates the HA state of the Primary firewall. The possible values are:
– Primary Active – Indicates that the Primary HA appliance is in the ACTIVE state.
– Primary Standby – Indicates that this appliance is in the standby state.
– Primary Disabled – Indicates that High Availability has not been enabled in the management interface of this appliance.
– Primary not in a steady state – Indicates that HA is enabled and the appliance is neither in the ACTIVE nor the standby state.
• Primary State - Indicates the current state of the Primary appliance as a member of an HA Pair. The Primary State field is displayed on both the Primary and the Secondary appliances. The possible values are:
– ACTIVE – Indicates that the Primary unit is handling all the network traffic except management/monitoring/licensing traffic destined to the standby unit.
– standby – Indicates that the Primary unit is passive and is ready to take over on a failover.
– ELECTION – Indicates that the Primary and Secondary units are negotiating which should be the ACTIVE unit.
– SYNC – Indicates that the Primary unit is synchronizing settings or firmware to the Secondary.
– ERROR – Indicates that the Primary unit has reached an error condition.
– REBOOT – Indicates that the Primary unit is rebooting.
– NONE – When viewed on the Primary unit, NONE indicates that HA is not enabled on the Primary. When viewed on the Secondary unit, NONE indicates that the Secondary unit is not receiving heartbeats from the Primary unit.
• Secondary State - Indicates the current state of the Secondary appliance as a member of an HA Pair. The Secondary State field is displayed on both the Primary and the Secondary appliances. The possible values are:
– ACTIVE – Indicates that the Secondary unit is handling all the network traffic except management/monitoring/licensing traffic destined to the standby unit.
– standby – Indicates that the Secondary unit is passive and is ready to take over on a failover.
– ELECTION – Indicates that the Secondary and Primary units are negotiating which should be the ACTIVE unit.
– SYNC – Indicates that the Secondary unit is synchronizing settings or firmware to the Primary.
– ERROR – Indicates that the Secondary unit has reached an error condition.
– REBOOT – Indicates that the Secondary unit is rebooting.
– NONE – When viewed on the Secondary unit, NONE indicates that HA is not enabled on the Secondary. When viewed on the Primary unit, NONE indicates that the Primary unit is not receiving heartbeats from the Secondary unit.
• Active Up Time - Indicates how long the current Active firewall has been Active, since it last became Active. This line only displays when High Availability is enabled. If failure of the Primary SonicWALL occurs, the Secondary SonicWALL assumes the Primary SonicWALL LAN and WAN IP addresses. There are three main methods to check the status of the High Availability Pair: the High Availability Status window, Email Alerts and View Log. These methods are described in the following sections.
• Node Status - Indicates if Active / Active Clustering is enabled or is not enabled.
• Found Peer - Indicates if the Primary unit has discovered the Secondary unit. Possible values are Yes and No.
• Settings Synchronized - Indicates if HA settings are synchronized between the Primary and Secondary units. Possible values are Yes and No.
• Stateful HA Synchronized - Indicates if stateful synchronization settings are synchronized between the Primary and Secondary units. Possible values are Yes and No.
High Availability Configuration
• HA Mode - One method to determine which SonicWALL is Active is to check the HA Settings Status indicator on the High Availability > Settings page. If the Primary SonicWALL is Active, the first line in the page indicates that the Primary SonicWALL is currently Active. It is also possible to check the status of the Secondary SonicWALL by logging into the LAN IP address of the Secondary SonicWALL. If the Primary SonicWALL is operating normally, the status indicates that the Secondary SonicWALL is currently Standby. If the Secondary has taken over for the Primary, the status indicates that the Secondary is currently Active. In the event of a failure in the Primary SonicWALL, you can access the management interface of the Secondary SonicWALL at the Primary SonicWALL LAN IP address or at the Secondary SonicWALL LAN IP address. When the Primary SonicWALL restarts after a failure, it is accessible using the third IP address created during configuration. If preempt mode is enabled, the Primary SonicWALL becomes the Active firewall and the Secondary firewall returns to Standby status.
• HA Control Link – Indicates the port, speed, and duplex settings of the HA link, such as HA 1000 Mbps full-duplex, when two firewalls are connected over their specified HA interfaces. When High Availability is not enabled, the field displays Disabled.
• HA Data Link – Indicates the port, speed, and duplex settings of the HA link, such as HA 1000 Mbps full-duplex, when two firewalls are connected over their specified HA interfaces. When High Availability is not enabled, the field displays Disabled.
High Availability Licenses
• Primary Stateful HA Licensed - Indicates if the Primary appliance has a stateful HA license. Possible values are Yes or No.
• Secondary Stateful HA Licensed - Indicates if the Secondary appliance has a stateful HA license. Possible values are Yes or No. Note that the Stateful HA license is shared with the Primary, but that you must access mysonicwall.com while logged into the LAN management IP address of the Secondary unit in order to synchronize with the SonicWALL licensing server.
• Primary Active / Active Licensed - Indicates if the Primary appliance has a Active / Active license. Possible values are Yes or No.
Active/Active High Availability Status
The High Availability > Status page provides status for the entire Active/Active cluster and for each Cluster Node in the deployment. The status for the Active/Active cluster is displayed in the upper table, and status for the each Cluster Node is displayed in the lower table.
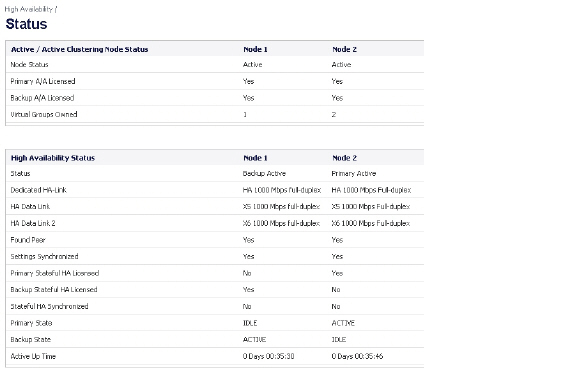
For additional information on High Availability status and verifying the configuration, see Verifying Active/Active Clustering Configuration