Firewall_advRuleOptions
This section provides network administrators advanced firewall settings for configuring detection prevention, dynamic ports, source routed packets, connection selection, and access rule options. To configure advanced access rule options, select Firewall Settings > Advanced under Firewall.
The Firewall Settings > Advanced page includes the following firewall configuration option groups:
• IP and UDP Checksum Enforcement
• Enable Stealth Mode - By default, the security appliance responds to incoming connection requests as either “blocked” or “open.” If you enable Stealth Mode, your security appliance does not respond to blocked inbound connection requests. Stealth Mode makes your security appliance essentially invisible to hackers.
• Randomize IP ID - Select Randomize IP ID to prevent hackers using various detection tools from detecting the presence of a security appliance. IP packets are given random IP IDs, which makes it more difficult for hackers to “fingerprint” the security appliance.
• Decrement IP TTL for forwarded traffic - Time-to-live (TTL) is a value in an IP packet that tells a network router whether or not the packet has been in the network too long and should be discarded. Select this option to decrease the TTL value for packets that have been forwarded and therefore have already been in the network for some time.
– Never generate ICMP Time-Exceeded packets - The firewall generates Time-Exceeded packets to report when it has dropped a packet because its TTL value has decreased to zero. Select this option if you do not want the firewall to generate these reporting packets.
• Enable FTP Transformations for TCP port(s) in Service Object - Select from the service group pull-down menu to enable FTP transformations for a particular service object. By default, service group FTP (All) is selected.
FTP operates on TCP ports 20 and 21 where port 21 is the Control Port and 20 is Data Port. When using non-standard ports (for example, 2020, 2121), however, Dell SonicWALL drops the packets by default as it is not able to identify it as FTP traffic. The Enable FTP Transformations for TCP port(s) in Service Object option allows you to select a Service Object to specify a custom control port for FTP traffic.
To illustrate how this feature works, consider the following example of an FTP server behind the Dell SonicWALL listening on port 2121:
a. On the Network > Address Objects page, create an Address Object for the private IP address of the FTP server with the following values:
: •: Name: FTP Server Private
: •: Zone: LAN
: •: Type: Host
: •: IP Address: 192.168.168.2
b. On the Network > Services page, create a custom Service for the FTP Server with the following values:
: •: Name: FTP Custom Port Control
: •: Protocol: TCP(6)
: •: Port Range: 2121 - 2121
c. On the Network > NAT Policies page, create the following NAT Policy:
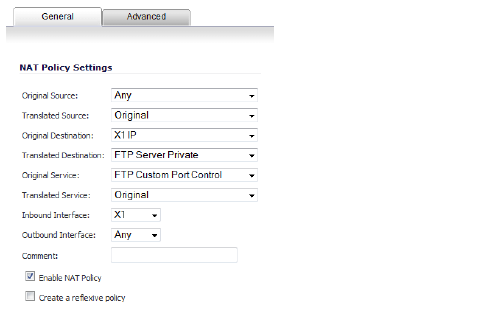
d. On the Firewall > Access Rules page, create the following Access Rule:
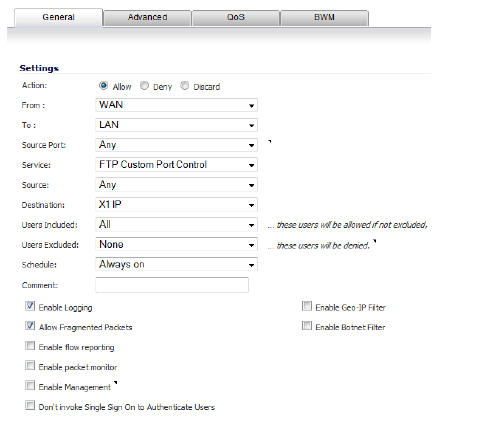
e. Lastly, on the Firewall Settings > Advanced page, from the Enable FTP Transformations for TCP port(s) in Service Object drop-down menu, select the FTP Custom Port Control Service Object.
Note For more information on configuring service groups and service objects, refer to Network > Services.
• Enable support for Oracle (SQLNet) - Select this option if you have Oracle9i or earlier applications on your network. For Oracle10g or later applications, it is recommended that this option not be selected.
For Oracle9i and earlier applications, the data channel port is different from the control connection port. When this option is enabled, a SQLNet control connection is scanned for a data channel being negotiated. When a negotiation is found, a connection entry for the data channel is created dynamically, with NAT applied if necessary. Within SonicOS, the SQLNet and data channel are associated with each other and treated as a session.
For Oracle10g and later applications, the two ports are the same, so the data channel port does not need to be tracked separately; thus, the option does not need to be enabled.
• Enable RTSP Transformations - Select this option to support on-demand delivery of real-time data, such as audio and video. RTSP (Real Time Streaming Protocol) is an application-level protocol for control over delivery of data with real-time properties.
• Drop Source Routed IP Packets - (Enabled by default.) Clear this checkbox if you are testing traffic between two specific hosts and you are using source routing.
IP Source Routing is a standard option in IP that allows the sender of a packet to specify some or all of the routers that should be used to get the packet to its destination.
This IP option is typically blocked from use as it can be used by an eavesdropper to receive packets by inserting an option to send packets from A to B via router C. The routing table should control the path that a packet takes, so that it is not overridden by the sender or a downstream router.
The Connections section provides the ability to fine-tune the firewall to prioritize for either optimal throughput or an increased number of simultaneous connections that are inspected by Deep-Packet Inspection (DPI) services. There is no change in the level of security protection provided by either of the DPI Connections settings below.
• Maximum SPI Connections (DPI services disabled) - This option does not provide SonicWALL DPI Security Services protection and optimizes the firewall for maximum number of connections with only stateful packet inspection enabled. This option should be used by networks that require only stateful packet inspection, which is not recommended for most Dell SonicWALL network security appliance deployments.
• Maximum DPI Connections (DPI services enabled) - This is the default and recommended setting for most Dell SonicWALL network security appliance deployments.
• DPI Connections (DPI services enabled with additional performance optimization) - This option is intended for performance critical deployments. This option trades off the number of maximum DPI connections for an increased firewall DPI inspection throughput.
Note When changing any Connections setting, the Dell SonicWALL security appliance must be restarted for the change to be implemented.
The maximum number of connections also depends on whether App Flow is enabled and if an external collector is configured, as well as the physical capabilities of the particular model of Dell SonicWALL security appliance. Mousing over the question mark ![]() icon next to the Connections heading displays a pop-up table of the maximum number of connections for your specific Dell SonicWALL security appliance for the various configuration permutations. The table entry for your current configuration is indicated in the table, as shown in the example below.
icon next to the Connections heading displays a pop-up table of the maximum number of connections for your specific Dell SonicWALL security appliance for the various configuration permutations. The table entry for your current configuration is indicated in the table, as shown in the example below.
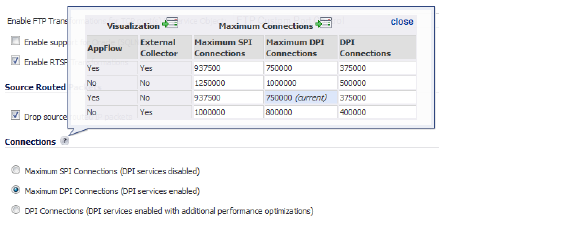
• Force inbound and outbound FTP data connections to use default port 20 - The default configuration allows FTP connections from port 20 but remaps outbound traffic to a port such as 1024. If the check box is selected, any FTP data connection through the security appliance must come from port 20 or the connection is dropped. The event is then logged as a log event on the security appliance.
• Apply firewall rules for intra-LAN traffic to/from the same interface - Applies firewall rules that is received on a LAN interface and that is destined for the same LAN interface. Typically, this only necessary when secondary LAN subnets are configured.
IP and UDP Checksum Enforcement
• Enable IP header checksum enforcement - Select this to enforce IP header checksums. Packets with incorrect checksums in the IP header are dropped. This option is disabled by default.
• Enable UDP checksum enforcement - Select this to enforce UDP packet checksums. Packets with incorrect checksums are dropped. This option is disabled by default.
• Enable Jumbo Frame support – Enabling this option increases throughput and reduces the number of Ethernet frames to be processed. Throughput increase may not be seen in some cases. However, there will be some improvement in throughput if the packets traversing are really jumbo size.
Note Jumbo frame packets are 9000 kilobytes in size and increase memory requirements by a factor of 4. Interface MTUs must be changed to 9000 bytes after enabling jumbo frame support as described in Configuring Advanced Settings for a WAN Interface.
The NSA 2600 does not support Jumbo frames.
• Drop IPv6 Routing Header type 0 packets – Select this to prevent a potential DoS attack that exploits IPv6 Routing Header type 0 (RH0) packets. When this setting is enabled, RH0 packets are dropped unless their destination is the Dell SonicWALL security appliance and their Segments Left value is 0. Segments Left specifies the number of route segments remaining before reaching the final destination. Enabled by default. For more information, see http://tools.ietf.org/html/rfc5095.
• Decrement IPv6 hop limit for forwarded traffic – Similar to Ipv4 TTL, when selected, the packet is dropped when the hop limit has been decremented to 0. Disabled by default.
• Drop and log network packets whose source or destination address is reserved by RFC – Select this option to reject and log network packets that have a source or destination address defined as an address reserved for future definition and use as specified in RFC 4921 for IPv6. Disabled by default.
• Never generate IPv6 ICMP Time-Exceeded packets – By default, the SonicWALL appliance generates IPv6 ICMP Time-Exceeded Packets that report when the appliance drops packets due to the hop limit decrementing to 0. Select this option to disable this function; the SonicWALL appliance will not generate these packets.
• Never generate IPv6 ICMP destination unreachable packets – By default, the SonicWALL appliance generates IPv6 ICMP destination unreachable packets. Select this option to disable this function; the SonicWALL appliance will not generate these packets.
• Never generate IPv6 ICMP redirect packets – By default, the SonicWALL appliance generates redirect packets. Select this option to disable this function; the SonicWALL appliance will not generate redirect packets.
• Never generate IPv6 ICMP parameter problem packets – By default, the SonicWALL appliance generates IPv6 ICMP parameter problem packets. Select this option to disable this function; the SonicWALL appliance will not generate these packets.
• Enable IPv6 Extension Header Validation – Select this option if you want the SonicWALL appliance to check the validity of IPv6 extension headers. By default, this option is disabled.
• Enable NetBIOS name query response for ISATAP – Select this option if you want the SonicWALL appliance to generate a NetBIOS name in response to an ISATAP query. By default, this option is disabled.
– Resolved name ISATAP is valid for (seconds) – If you enabled generation of a NetBIOS name, you can specify the time, in seconds, that the name remains valid. The default value is 900 seconds (15 minutes).