 in the Configure column in the Address Objects table. The Edit Address Object window is displayed, which has the same settings as the Add Address Object window (see Adding an Address Object).
in the Configure column in the Address Objects table. The Edit Address Object window is displayed, which has the same settings as the Add Address Object window (see Adding an Address Object).Network_netObjView
Address Objects are one of four object classes (Address, User, Service, and Schedule) in SonicOS. These Address Objects allow for entities to be defined one time, and to be re-used in multiple referential instances throughout the SonicOS interface. For example, take an internal Web-Server with an IP address of 67.115.118.80. Rather than repeatedly typing in the IP address when constructing Access Rules or NAT Policies, Address Objects allow you to create a single entity called “My Web Server” as a Host Address Object with an IP address of 67.115.118.80. This Address Object, “My Web Server” can then be easily and efficiently selected from a drop-down menu in any configuration screen that employs Address Objects as a defining criterion.
Topics:
• Creating and Managing Address Objects
• Editing or Deleting an Address Object
• Creating Group Address Objects
• Working with Dynamic Addresses
Since there are multiple types of network address expressions, there are currently the following Address Objects types:
• Host – Host Address Objects define a single host by its IP address. The netmask for a Host Address Object will automatically be set to 32-bit (255.255.255.255) to identify it as a single host. For example, “My Web Server” with an IP address of “67.115.118.110” and a default netmask of “255.255.255.255”
• Range – Range Address Objects define a range of contiguous IP addresses. No netmask is associated with Range Address Objects, but internal logic generally treats each member of the specified range as a 32-bit masked Host object. For example “My Public Servers” with an IP address starting value of “67.115.118.66” and an ending value of “67.115.118.90”. All 25 individual host addresses in this range would be comprised by this Range Address Object.
• Network – Network Address Objects are like Range objects in that they comprise multiple hosts, but rather than being bound by specified upper and lower range delimiters, the boundaries are defined by a valid netmask. Network Address Objects must be defined by the network’s address and a corresponding netmask. For example “My Public Network” with a Network Value of “67.115.118.64” and a netmask of “255.255.255.224” would comprise addresses from 67.115.118.64 through to 67.115.118.95. As a general rule, the first address in a network (the network address) and the last address in a network (the broadcast address) are unusable.
• MAC Address – MAC Address Objects allow for the identification of a host by its hardware address or MAC (Media Access Control) address. MAC addresses are uniquely assigned to every piece of wired or wireless networking device by their hardware manufacturers, and are intended to be immutable. MAC addresses are 48-bit values that are expressed in 6 byte hex-notation. For example “My Access Point” with a MAC address of “00:06:01:AB:02:CD”. MAC addresses are resolved to an IP address by referring to the ARP cache on the security appliance MAC address objects are used by various components of Wireless configurations throughout SonicOS.
• FQDN Address – FQDN address objects allow for the identification of a host by its Fully Qualified Domain Names (FQDN), such as 'www.sonicwall.com'. FQDNs are be resolved to their IP address (or IP addresses) using the DNS server configured on the security appliance. Wildcard entries are supported through the gleaning of responses to queries sent to the sanctioned DNS servers.
SonicOS has the ability to group Address Objects into Address Object Groups. Groups of Address Objects can be defined to introduce further referential efficiencies. Groups can comprise any combination of Host, Range, or Network Address Objects. MAC address Objects should be grouped separately, although they can safely be added to Groups of IP-based Address Objects, where they will be ignored when their reference is contextually irrelevant (e.g. in a NAT Policy). For example “My Public Group” can contain Host Address Object “My Web Server” and Range Address Object “My Public Servers”, effectively representing IP addresses 67.115.118.66 to 67.115.118.90 and IP address 67.115.118.110.
Overview of the Network > Address Objects Page
The Network > Address Objects page comprises two tabs:
• Address Objects
• Address Groups
Although the two tabs are similar with similar functions, there are some differences between them.
Topics:
Each tab contains these common functions and each table contains the same column headings.
The bottom of each table displays the number of entries in the table.
Topics;
• Search – Enter a search string to display only those entries containing the string. The search string is case insensitive.
• Print icon – If your system has a printer, the printer icon becomes active. Click on the icon to print the contents of the table.
• Refresh icon – Click on the icon to refresh the table display.
• Select radio buttons – View all or a subset of the entries by selecting one of the radio buttons:
– All Types - Displays all configured Address Objects or Address Groups.
– Default - Displays those Address Objects or Address Groups configured by default on the firewall.
– Custom - Displays only Address Objects or Address Groups with custom properties.
• Load All button – Click on this button to load all Address Objects or Address Groups.
• Checkbox – Click to select a custom entry.
Note Default Address Objects and Default Address Groups cannot be deleted.
• # – The number of the entry in the table. This number changes depending on whether the column is sorted by ascending or descending order.
• Name – The unique name of the Address Object or Address Group entry. If an Address Group entry is expanded, this column will show:
– The unique name of each member of the Address Group.
– No Entries if the Address Group does not contain members.
• Details – Shows the Address Object details. For an Address Group entry, this column is blank; an expanded entry, however, shows the details of the members of the group.
• Type – Shows the Address Object type, such as Host, Network, Range, or FQDN. For an Address Group, the type is Group; an expanded entry shows the type of each member.
• IP Version – Shows the IP version of the Address Object or Address Group member: IPv4 or IPv6.
• Zone – Shows the assigned zone, any, of the Address Object or Address Group member.
• Class – Shows whether the Address Object or Address Group is default (system defined) or custom (user defined).
• Comments – Mouse over the Comment icon to display a pop-up window with details about the entry:
– Address Object – Displays this information:
: •: Name of the Address Object
: •: Referenced By: – What references the Address Object and the number of times it has been referenced. If the Address Object has not be referenced, this section will state No Listing.
: •: Groups (Member of): – List of groups to which the Address Object belongs. If the Address Object does not belong to a group, this section will state No Listing.
– Address Group – Displays this information:
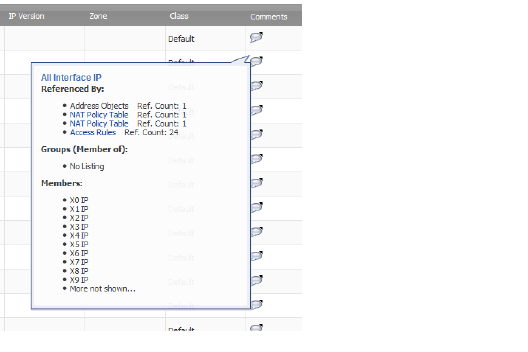
: •: Name of the Address Group
: •: Referenced By: – What references the Address Group and the number of times it has been referenced. If the Address Group has not be referenced, this section will state No Listing.
: •: Groups (Member of): – List of groups to which the Address Group belongs. If the Address Group does not belong to a group, this section will state No Listing.
: •: Members: – List of Address Objects that belong to this group. If the Address Group does not contain members, this section will state No Listing.
– Configure — Displays Edit and Delete icons for individual entries. Only custom Address Objects and Address Groups can be deleted; only custom entries and some default entries can be edited. If an entry cannot be edited or deleted, the icon(s) will be dimmed.
The Address Objects and Address Groups tabs display tables for easy viewing of address objects and address groups.
You can sort the entries in the table by clicking on the column header. The entries are sorted by ascending or descending order. The arrow to the right of the column entry indicates the sorting status. A down arrow means ascending order. An up arrow indicates a descending order.
Creating and Managing Address Objects
The Network > Address Objects page allows you to create and manage your Address Objects and Address Groups.
Note An Address Object must be defined before configuring NAT Policies, Access Rules, and Services.
Note The Default Address Objects Default Address Objects entries cannot be deleted and most cannot be modified. Therefore, the Delete icons are dimmed for Default Address Objects and the Edit icons are dimmed for those that cannot be edited.
1. Click the Add… button under the Address Objects table to display the Add Address Object window.
2. Enter a friendly, unique name for the Network Object in the Name field.
3. Select the zone to assign to the Address Object from the Zone Assignment menu.
4. Select one of the following from the Type menu:
• Host, enter the IP address in the IP Address field.
• Range, enter the starting and ending IP addresses in the Starting IP Address and Ending IP Address fields.
• Network, enter the network IP address and netmask/prefix length in the Network and Netmask/Prefix Length fields.
• MAC, enter the MAC address in the Network field and, optionally, select the Multi-honed host checkbox.
• FQDN, enter the domain name for the individual site or range of sites (with a wildcard) in the FQDN Hostname field.
5. Click Add.
Editing or Deleting an Address Object
Note Only custom Address Objects and certain default Address Objects can be edited. Only custom Address Objects can be deleted.
Editing Address Objects
To edit an Address Object, click the edit icon  in the Configure column in the Address Objects table. The Edit Address Object window is displayed, which has the same settings as the Add Address Object window (see Adding an Address Object).
in the Configure column in the Address Objects table. The Edit Address Object window is displayed, which has the same settings as the Add Address Object window (see Adding an Address Object).
Deleting Custom Address Objects
To delete a custom Address Object, click the Delete icon ![]() in the Configure column for the Address Object you want to delete. A dialog box is displayed asking you to confirm the deletion. Click OK to delete the Address Object. To delete multiple active Address Objects, select them and click the Delete button.
in the Configure column for the Address Object you want to delete. A dialog box is displayed asking you to confirm the deletion. Click OK to delete the Address Object. To delete multiple active Address Objects, select them and click the Delete button.
To delete all custom Address Objects, click the Delete All button.
Purging FQDN Address Objects
To purge one or multiple custom FQDN Address Objects, select them and then click the Purge button. To purge all FQDN Address Objects, click the Purge All button.
Creating Group Address Objects
As more and more Address Objects are added to the firewall, you can simplify managing the addresses and access policies by creating groups of addresses. Changes made to the group are applied to each address in the group. To add a Group of Address Objects, complete the following steps:
1. Click the Address Groups tab on the Network > Address Objects page.
2. Click Add Group… to display the Add Address Object Group window.
3. Create a friendly, unique name for the group in the Name field.
4. Select an Address Objects from the list and then click the right arrow. The selected item is added to the group. Clicking while pressing the Ctrl key allows you to select multiple objects.
5. Click OK.
Tip To remove an address or subnet from the group, select the IP address or subnet in the right column and click the left arrow. The selected item moves from the right column to the left column.
Editing or Deleting Address Groups
Note Only custom and some Address Groups can be edited; only custom Address Groups can be deleted.
Editing Address Groups
To edit a group, click the Edit icon  in the Configure column of the Address Groups table. The Edit Address Object Group window is displayed. This window is the same as the Add Address Object Group window; see Creating Group Address Objects.
in the Configure column of the Address Groups table. The Edit Address Object Group window is displayed. This window is the same as the Add Address Object Group window; see Creating Group Address Objects.
Deleting Address Groups
To delete a custom Address Group, click on the Delete icon ![]() in the Configure column to delete an individual Address Group. A dialog box is displayed asking you to confirm the deletion. Click OK to delete the Address Group.
in the Configure column to delete an individual Address Group. A dialog box is displayed asking you to confirm the deletion. Click OK to delete the Address Group.
To delete multiple active custom Address Groups, select them and click the Delete button.
To delete all custom Address Groups, click the Delete All button.
Working with Dynamic Addresses
From its inception, SonicOS has used Address Objects (AOs) to represent IP addresses in most areas throughout the user interface. Address Objects come in the following varieties:
• Host – An individual IP address, netmask and zone association.
• MAC (original) – Media Access Control, or the unique hardware address of an Ethernet host. MAC AOs are used for:
– Identifying SonicPoints
– Allowing hosts to bypass Guest Services authentication
– Authorizing the BSSID (Basic Service Set Identifier, or WLAN MAC) of wireless access points detected during wireless scans.
MAC AOs were originally not allowable targets in other areas of the management interface, such as Access Rules, so historically they could not be used to control a host’s access by its hardware address.
• Range – A starting and ending IP address, inclusive of all addresses in between.
• Group – A collection of Address Objects of any assortment of types. Groups may contain other Groups, Host, MAC, Range, or FQDN Address Objects.
SonicOS redefined the operation of MAC AOs, and supports Fully Qualified Domain Name (FQDN) AOs:
• MAC – SonicOS resolves MAC AOs to an IP address by referring to the ARP cache on the firewall.
• FQDN – Fully Qualified Domain Names, such as ‘www.reallybadWebsite.com’, will be resolved to their IP address (or IP addresses) using the DNS server configured on the firewall. Wildcard entries are supported through the gleaning of responses to queries sent to the sanctioned DNS servers.
While more effort is involved in creating an Address Object than in simply entering an IP address, AOs were implemented to complement the management scheme of SonicOS, providing the following characteristics:
• Zone Association – When defined, Host, MAC, and FQDN AOs require an explicit zone designation. In most areas of the interface (such as Access Rules) this is only used referentially. The functional application are the contextually accurate populations of Address Object drop-down lists, and the area of “VPN Access” definitions assigned to Users and Groups; when AOs are used to define VPN Access, the Access Rule auto-creation process refers to the AO’s zone to determine the correct intersection of VPN [zone] for rule placement. In other words, if the “192.168.168.200 Host” Host AO, belonging to the LAN zone was added to “VPN Access” for the “Trusted Users” User Group, the auto-created Access Rule would be assigned to the VPN LAN zone.
• Management and Handling – The versatilely typed family of Address Objects can be easily used throughout the SonicOS interface, allowing for handles (e.g. from Access Rules) to be quickly defined and managed. The ability to simply add or remove members from Address Object Groups effectively enables modifications of referencing rules and policies without requiring direct manipulation.
• Reusability – Objects only need to be defined once, and can then be easily referenced as many times as needed.
Key Features of Dynamic Address Objects
The term Dynamic Address Object (DAO) describes the underlying framework enabling MAC and FQDN AOs. By transforming AOs from static to dynamic structures Firewall > Access Rules can automatically respond to changes in the network.
|
Enforcing the Use of Sanctioned Servers on the Network
Although not a requirement, it is recommended to enforce the use of authorized or sanctioned servers on the network. This practice can help to reduce illicit network activity, and will also serve to ensure the reliability of the FQDN wildcard resolution process. In general, it is good practice to define the endpoints of known protocol communications when possible. For example:
• Create Address Object Groups of sanctioned servers (e.g. SMTP, DNS, etc.)
• Create Access Rules in the relevant zones allowing only authorized SMTP servers on your network to communicate outbound SMTP; block all other outbound SMTP traffic to prevent intentional or unintentional outbound spamming.
• Create Access Rules in the relevant zones allowing authorized DNS servers on your network to communicate with all destination hosts using DNS protocols (TCP/UDP 53). Be sure to have this rule in place if you have DNS servers on your network, and you will be configuring the restrictive DNS rule that follows.
• Create Access Rules in the relevant zones allowing Firewalled Hosts to only communicate DNS (TCP/UDP 53) with sanctioned DNS servers; block all other DNS access to prevent communications with unauthorized DNS servers.
• Unsanctioned access attempts will then be viewable in the logs.
Using MAC and FQDN Dynamic Address Objects
MAC and FQDN DAOs provide extensive Access Rule construction flexibility. MAC and FQDN AOs are configured in the same fashion as static Address Objects, that is from the Network > Address Objects page. Once created, their status can be viewed by a mouse-over of their appearance, and log events will record their addition and deletion.
Dynamic Address Objects lend themselves to many applications. The following are just a few examples of how they may be used. Future versions of SonicOS may expand their versatility even further.
Blocking All Protocol Access to a Domain using FQDN DAOs
There might be instances where you wish to block all protocol access to a particular destination IP because of non-standard ports of operations, unknown protocol use, or intentional traffic obscuration through encryption, tunneling, or both. An example would be a user who has set up an HTTPS proxy server (or other method of port-forwarding/tunneling on “trusted” ports like 53, 80, 443, as well as nonstandard ports, like 5734, 23221, and 63466) on his DSL or cable modem home network for the purpose of obscuring his traffic by tunneling it through his home network. The lack of port predictability is usually further complicated by the dynamic addressing of these networks, making the IP address equally unpredictable.
Since these scenarios generally employ dynamic DNS (DDNS) registrations for the purpose of allowing users to locate the home network, FQDN AOs can be put to aggressive use to block access to all hosts within a DDNS registrar.
Note A DDNS target is used in this example for illustration. Non-DDNS target domains can be used just as well.
Assumptions
• The firewall is configured to use DNS server 10.50.165.3, 10.50.128.53.
• The firewall is providing DHCP leases to all firewalled users. All hosts on the network use the configured DNS servers above for resolution.
– DNS communications to unsanctioned DNS servers can optionally be blocked with Access Rules, as described in the ‘Enforcing the use of sanctioned servers on the network’ section.
• The DSL home user is registering the hostname moosifer.dyndns.org with the DDNS provider DynDNS. For this session, the ISP assigned the DSL connection the address 71.35.249.153.
– A wildcard FQDN AO is used for illustration because other hostnames could easily be registered for the same IP address. Entries for other DDNS providers could also be added, as needed.
Step 1 – Create the FQDN Address Object
• From Network > Address Objects, select Add and create the following Address Object:
• When first created, this entry will resolve only to the address for dyndns.org, e.g. 63.208.196.110.
Step 2 – Create the Firewall Access Rule
• From the Firewall > Access Rules page, LAN->WAN zone intersection, Add an Access Rule as follows:
Note Rather than specifying ‘LAN Subnets’ as the source, a more specific source could be specified, as appropriate, so that only certain hosts are denied access to the targets.
• When a host behind the firewall attempts to resolve moosifer.dyndns.org using a sanctioned DNS server, the IP address(es) returned in the query response will be dynamically added to the FQDN AO.
• Any protocol access to target hosts within that FQDN will be blocked, and the access attempt will be logged:
Using an Internal DNS Server for FQDN-based Access Rules
It is common for dynamically configured (DHCP) network environments to work in combination with internal DNS servers for the purposes of dynamically registering internal hosts – a common example of this is Microsoft’s DHCP and DNS services. Hosts on such networks can easily be configured to dynamically update DNS records on an appropriately configured DNS server (for example, see the Microsoft Knowledgebase article “How to configure DNS dynamic updates in Windows Server 2003” at http://support.microsoft.com/kb/816592/en-us).
The following illustrates a packet dissection of a typical DNS dynamic update process, showing the dynamically configured host 10.50.165.249 registering its full hostname bohuymuth.moosifer.com with the (DHCP provided) DNS server 10.50.165.3:
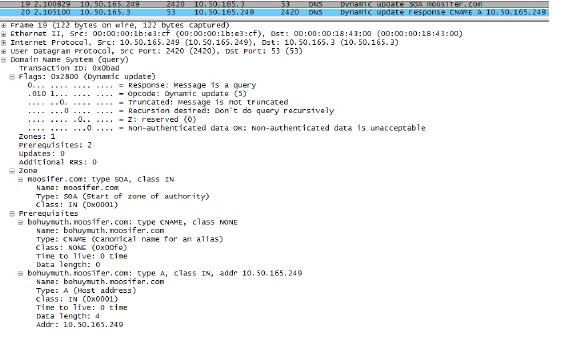
In such environments, it could prove useful to employ FQDN AOs to control access by hostname. This would be most applicable in networks where hostnames are known, such as where hostname lists are maintained, or where a predictable naming convention is used.
Controlling a Dynamic Host’s Network Access by MAC Address
Since DHCP is far more common than static addressing in most networks, it is sometimes difficult to predict the IP address of dynamically configured hosts, particularly in the absence of dynamic DNS updates or reliable hostnames. In these situations, it is possible to use MAC Address Objects to control a host’s access by its relatively immutable MAC (hardware) address.
Like most other methods of access control, this can be employed either inclusively, for example, to deny access to/for a specific host or group of hosts, or exclusively, where only a specific host or group of hosts are granted access, and all other are denied. In this example, we will illustrate the latter.
Assuming you had a set of DHCP-enabled wireless clients running a proprietary operating system which precluded any type of user-level authentication, and that you wanted to only allow these clients to access an application-specific server (e.g. 10.50.165.2) on your LAN. The WLAN segment is using WPA-PSK for security, and this set of clients should only have access to the 10.50.165.2 server, but to no other LAN resources. All other wireless clients should not be able to access the 10.50.165.2 server, but should have unrestricted access everywhere else.
Step 1 – Create the MAC Address Objects
• From Network > Address Objects, select Add and create the following Address Object (multi-homing optional, as needed):
Once created, if the hosts are present in the firewall’s ARP cache, they will be resolved immediately, otherwise they will appear in an unresolved state in the Address Objects table until they are activated and are discovered through ARP:
Create an Address Object Group comprising the Handheld devices:
Step 2 – Create the Firewall Access Rules
• To create access rules, navigate to the Firewall > Access Rules page, click on the All Rules radio button, and scroll to the bottom of the page and click the Add button.
• Create the following four access rules:
|
Note The ‘MediaMoose Services’ service is used to represent the specific application used by the handheld devices. The declaration of a specific service is optional, as needed.
Bandwidth Managing Access to an Entire Domain
Streaming media is one of the most profligate consumers of network bandwidth. But trying to control access, or manage bandwidth allotted to these sites is difficult because most sites that serve streaming media tend to do so off of large server farms. Moreover, these sites frequently re-encode the media and deliver it over HTTP, making it even more difficult to classify and isolate. Manual management of lists of servers is a difficult task, but wildcard FQDN Address Objects can be used to simplify this effort.
Step 1 – Create the FQDN Address Object
• From Network > Address Objects, select Add and create the following Address Object:
Upon initial creation, youtube.com will resolve to IP addresses 208.65.153.240, 208.65.153.241, 208.65.153.242, but after an internal host begins to resolve hosts for all of the elements within the youtube.com domain, the learned host entries will be added, such as the entry for the v87.youtube.com server (208.65.154.84).
Step 2 – Create the Firewall Access Rule
• From the Firewall > Access Rules page, LAN->WAN zone intersection, add an Access Rule as follows:
Note If you do not see the Bandwidth tab, you can enable bandwidth management by declaring the bandwidth on your WAN interfaces.
Note The BWM icon will appear within the Access Rule table indicating that BWM is active, and providing statistics. Access to all *.youtube.com hosts, using any protocol, will now be cumulatively limited to 2% of your total available bandwidth for all user sessions.