 For complete information on the SonicOS implementation of IPv6, see IPv6.
For complete information on the SonicOS implementation of IPv6, see IPv6.Network_netDns
The Domain Name System (DNS) is a distributed, hierarchical system that provides a method for identifying hosts on the Internet using alphanumeric names called fully qualified domain names (FQDNs) instead of using difficult to remember numeric IP addresses. The Network > DNS page allows you to manually configure your DNS settings, if necessary.
The options on the Network > DNS page change depending on whether you specify IPv6 or IPv4:
In the DNS Settings section, select Specify DNS Servers Manually and enter the IP address(es) into the DNS Server fields. Click Accept to save your changes. To use the DNS Settings configured for the WAN zone, select Inherit DNS Settings Dynamically from the WAN Zone. Click Accept to save your changes.
 For complete information on the SonicOS implementation of IPv6, see IPv6.
For complete information on the SonicOS implementation of IPv6, see IPv6.
Simply click the IPv6 option in the View IP Version radio button at the top left of the Network > DNS page.
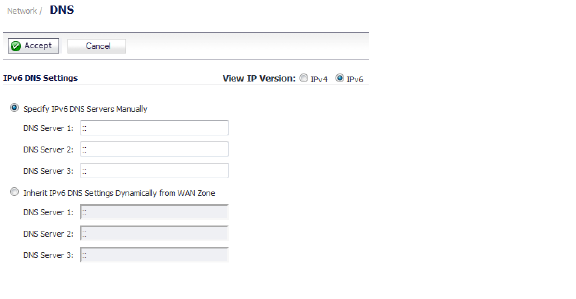
In the IPv6 DNS Settings section, select one of the following:
• Specify IPv6 DNS Servers Manually and enter the IP address(es) into the DNS Server fields.
• To use the DNS Settings configured for the WAN zone, select Inherit IPv6 DNS Settings Dynamically from WAN Zone and enter the IP address(es) into the DNS Server fields.
Click Accept to save your changes.
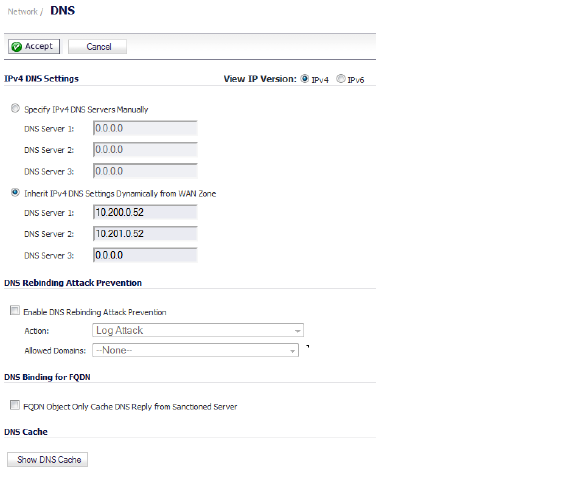
The IPv4 page has these sections:
• DNS Rebinding Attack Prevention
In the IPv4 DNS Settings section, select one of the following:
• Specify IPv4 DNS Servers Manually and enter the IP address(es) into the DNS Server fields.
• To use the DNS Settings configured for the WAN zone, select Inherit IPv4 DNS Settings Dynamically from WAN Zone and enter the IP address(es) into the DNS Server fields.
Click Accept to save your changes.
DNS Rebinding Attack Prevention
DNS rebinding is a DNS-based attack on code embedded in web pages. Normally requests from code embedded in web pages (JavaScript, Java and Flash) are bound to the web-site they are originating from (see Same Origin Policy). A DNS rebinding attack can be used to improve the ability of JavaScript based malware to penetrate private networks, and subvert the browser's same-origin policy.
DNS rebinding attackers register a domain which is delegated to a DNS server they control. The server is configured to respond with a very short TTL parameter which prevents the result from being cached. The first response contains IP address of the server hosting the malicious code. Any subsequent requests contain IP addresses from private (RFC 1918) network, presumably behind a firewall, being target of the attacker. Because both are fully valid DNS responses, they authorize the sandbox script to access hosts in a private network. By iterating addresses in these short-term but still valid DNS replies the script is able to scan the network and perform other malicious activities.
1. Select the Enable DNS Rebinding Attack Prevention checkbox.
2. From the Action pull-down menu, select an action to perform when a DNS rebinding attack is detected:
• Log Attack
• Log Attack & Return a Query Refused Reply
• Log Attack & Drop DNS Reply
3. From the Allowed Domains pull-down menu, select an allowed domain FQDN Address Object or FQDN Address Object Group containing allowed domain-names (such as, *.sonicwall.com) for which locally connected/routed subnets should be considered legal responses.
You can also create new FQDN address objects or FQDN address object groups by selecting Create new FQDN Address Object… or FQDN Address Object Group….
To enable DNS binding for FQDN, select the FQDN Object Only Cache DNS Reply from Sanctioned Server checkbox.
To show the contents of the general DNS cache, click the Show DNS Cache button. A pop-up window displays the following cache contents:
• What
• DNS Name
• IP Address
• TTL (secs)