Policies_SecurityServices_ClientAVEnforcement_Snwls
Configuring SonicWALL Network Anti-Virus
SonicWALL Network Anti-Virus is a distributed, gateway-enforced solution that ensures always-on, always-updated anti-virus software for every client on your network. The SonicWALL constantly monitors the version of the virus definition file and automatically triggers download and installation of new virus definition files to each user’s computer. In addition, the SonicWALL restricts each user’s access to the Internet until they are protected, therefore acting as an automatic enforcer of the company’s virus protection policy.
This new approach ensures the most current version of the virus definition file is installed and active on each PC on the network, preventing a rogue user from disabling the virus protection and potentially exposing the entire organization to an outbreak. And most importantly, SonicWALL Network Anti-Virus offloads the costly and time-consuming burden of maintaining and updating anti-virus software across the entire network.
SonicWALL Network Anti-Virus also includes Network Anti-Virus Email Filter to selectively manage inbound Email attachments as they pass through the SonicWALL to control the flow of executable files, scripts, and applications into your network.
Configuring Anti-Virus Settings
Global Management System (Dell SonicWALL GMS) offers anti-virus protection on a subscription-basis through a partnership with McAfee.
This section describes how to configure Anti-Virus settings for SonicWALL appliances.
Note SonicWALL appliances are entitled to a one-month anti-virus trial subscription. To enable the trial subscription, refer to the Upgrading Licenses.
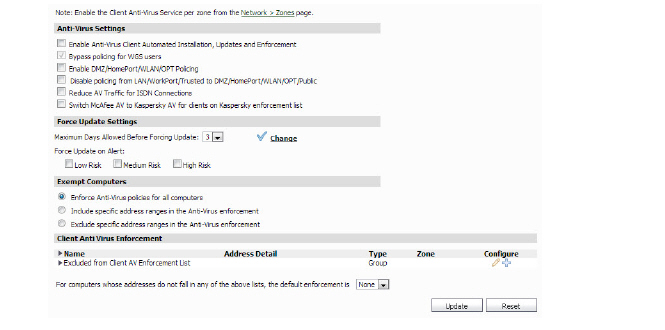
Anti-Virus Settings
To configure Anti-Virus settings for one or more SonicWALL appliances, follow these steps:
1. Select the global icon, a group, or a SonicWALL appliance.
2. Expand the Security Services tree and click Client AV Enforcement. The Client AV Enforcement page appears.
3. To enable the Client Anti-Virus Service, navigate to the Network > Zones page. Once the service is enabled, proceed to the next steps to configure the settings.
4. Select the Enable Anti-Virus Client Automated Installation, Updates and Enforcement check box.
5. Clicking the Disable policing from Trusted to Public option allows computers on a trusted zone (such as a LAN) to access computers on public zones (such as DMZ), even if anti-virus software is not installed on the LAN computers. Unchecked, the Disable policing from Trusted to Public option enforces anti-virus policies on computers located on Trusted zones.
6. To bypass policing to Wireless Guest Services users, click the Bypass policing for WGS users checkbox. This checkbox is only applicable to SonicOS Standard and is greyed out unless the Enable DMZ/OPT Policing checkbox is selected.
7. To enforce Anti-Virus protection on the DMZ port or HomePort (if available), select the Enable DMZ/HomePort/WLAN/OPT Policing check box.
8. To disable policing from the LAN to the DMZ, select the Disable policing from LAN/WorkPort/Trusted to DMZ/HomePort/WLAN/OPT check box.
9. To configure the SonicWALL appliance(s) to only check for updates once a day, select the Reduce AV Traffic for ISDN connections check box. This is useful for low bandwidth connections or connections that are not “always on.”
Force Update Settings
Dell SonicWALL GMS automatically downloads the latest virus definition files. To configure the maximum number of days that can pass before Dell SonicWALL GMS downloads the latest files, select the number of days from the Maximum Days Allowed Before Forcing Update list box.
Significant virus events can occur without warning (e.g., Melissa, ILOVEYOU, and others). When these occur, Dell SonicWALL GMS can be configured to block network traffic until the latest virus definition files are downloaded. To configure this feature, determine which types of events will require updating. Then, select the Low Risk, Medium Risk, or High Risk check boxes.
Force update on alert - SonicWALL, Inc. broadcasts virus alerts to all SonicWALL appliances with an Anti-Virus subscription. Three levels of alerts are available, and you may select more than one. When an alert is received with this option selected, users are upgraded to the latest version of VirusScan ASaP before they can access the Internet. This option overrides the Maximum number of days allowed before forcing update selection. In addition, every virus alert is logged, and an alert message is sent to the administrator.
• Low Risk - A virus that is not reported in the field and is considered unlikely to be found in the field in the future has a low risk. Even if such a virus includes a very serious or unforeseeable damage payload, its risk is still low.
• Medium Risk - If a virus is found in the field, and if it uses a less common infection mechanism, it is considered to be medium risk. If its prevalence stays low and its payload is not serious, it can be downgraded to a low risk. Similarly it can be upgraded to high risk if the virus becomes more and more widespread.
• High Risk - To be assigned a high risk rating, it is necessary that a virus is reported frequently in the field. Additionally, the payload must have the ability to cause at least some serious damage. If it causes very serious or unforeseeable damage, high risk may be assigned even with a lower level of prevalence.
Exempt Computers
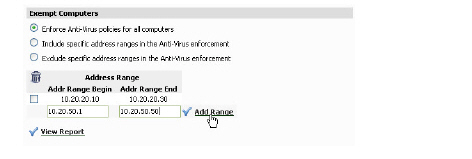
The Exempt Computers section allows the GMS administrator to specify address ranges which should be explicitly included or excluded in Anti-Virus enforcement.
1. Select the Enforce Anti-Virus policies for all computers radio button to enforce Anti-Virus policies across your entire network. Selecting this option forces computers to install VirusScan ASaP in order to access the Internet or the DMZ. This is the default configuration
2. Select the Include specific address ranges in the Anti-Virus enforcement radio button to force a specified range of addresses to adhere to Anti-Virus enforcement. Choosing this option allows the administrator to define ranges of IP addresses to receive Anti-Virus enforcement. If you select this option, specify a range of IP addresses to be enforced. Any computer requiring enforcement needs a static IP address within the specified range of IP addresses. Up to 64 IP address ranges can be entered for enforcement.
3. Select the Exclude specific address ranges in the Anti-Virus enforcement radio button to exempt a specified range of addresses from Anti-Virus enforcement. Selecting this option allows the administrator to define ranges of IP addresses that are exempt from Anti-Virus enforcement. If you select this option, specify the range of IP addresses are exempt. Any computer requiring unrestricted Internet access needs a static IP address within the specified range of IP addresses. Up to 64 IP address ranges can be entered.
Client Anti Virus Enforcement
The Client Anti Virus Enforcement list provides the options to exclude address objects from the Client AV Enforcement list.
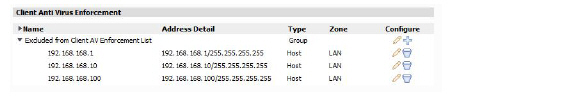
You can edit these address objects and groups by clicking the Edit icon, or add address objects by clicking the Add icon for the desired list.
Select the default enforcement type for computers whose addresses did not fail any of the client anti-virus enforcement from the drop-down list.